Microsoft Defender for Office 365 overview
Tip
Did you know you can try the features in Microsoft Defender XDR for Office 365 Plan 2 for free? Use the 90-day Defender for Office 365 trial at the Microsoft Defender portal trials hub. Learn about who can sign up and trial terms here.
Microsoft Defender for Office 365 is a seamless integration into Microsoft 365 subscriptions that protects against threats in email, links (URLS), file attachments, and collaboration tools. This article explains the protection ladder in Microsoft 365 organizations. The protection ladder starts with Exchange Online Protection (EOP) and continues through to Defender for Office 365, which includes Defender for Office 365 Plan 1 and Defender for Office 365 Plan 2.
This article is intended for Security Operations (SecOps) personnel, admins in Microsoft 365, or decisions makers who want to learn more about Defender for Office 365.
Tip
If you're using Outlook.com, Microsoft 365 Family, or Microsoft 365 Personal, and need information about Safelinks or advanced attachment scanning, see Advanced Outlook.com security for Microsoft 365 subscribers.
If you're new to your Microsoft 365 subscription and would like to know your licenses before you begin, go the Your products page in the Microsoft 365 admin center at https://admin.microsoft.com/Adminportal/Home#/subscriptions.
All Microsoft 365 subscriptions include built-in security and protection features. The goals and available actions of these features vary. In Microsoft 365, there are three main security services (or products):
- Exchange Online Protection (EOP): Included in any subscription that includes Exchange Online mailboxes. Also available as a standalone subscription to protect on-premises email environments.
- Defender for Office 365 365 Plan 1: Included in some Microsoft 365 subscriptions with Exchange Online mailboxes that cater to small to medium-sized businesses (for example, Microsoft 365 Business Premium).
- Defender for Office 365 365 Plan 2: Included in some Microsoft 365 subscriptions with Exchange Online mailboxes that cater to enterprise organizations (for example, Microsoft 365 E5, Microsoft 365 A5, and Microsoft 365 GCC G5).
Defender for Office 365 always includes EOP. Defender for Office 365 is also available as an add-in subscription to many Microsoft 365 subscriptions with Exchange Online mailboxes.
Defender for Office 365 Plan 1 contains a subset of the features that are available in Plan 2. Defender for Office 365 Plan 2 contains many features that aren't available in Plan 1.
Tip
For information about subscriptions that contain Defender for Office 365, see the Microsoft 365 business plan comparison and the Microsoft 365 Enterprise plan comparison.
Use the following exhaustive reference to determine if Defender for Office 365 Plan 1 or Plan 2 licenses are included in a Microsoft 365 subscription: Product names and service plan identifiers for licensing.
Use the following interactive guide to see how Defender for Office 365 is able to protect your organization: Safeguard your organization with Microsoft Defender for Office 365.
Use this page to compare plans and purchase Defender for Office 365.
EOP and Defender for Office 365 can be summarized with the following descriptions:
- EOP prevents broad, volume-based, known email attacks.
- Defender for Office 365 Plan 1 protects email and collaboration features from zero-day malware, phishing, and business email compromise (BEC).
- Defender for Office 365 Plan 2 adds phishing simulations, post-breach investigation, hunting, and response, and automation.
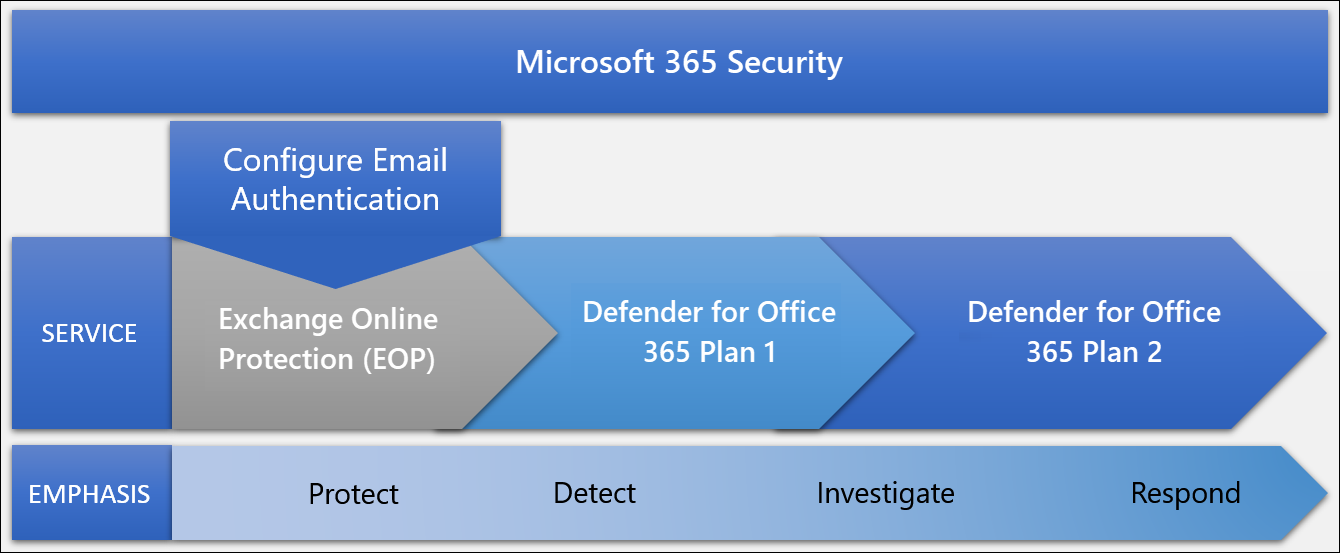
However, you can also think about the architecture of EOP and Defender for Office 365 as cumulative layers of security, where each layer has a different security emphasis. This architecture is shown in the following diagram:
EOP and Defender for Office 365 are capable of protecting, detecting, investigating, and responding to threats. But as you move up the protection ladder, the available features and automation increase.
Whether you're using the onmicrosoft.com domain only or custom domains for email in Microsoft 365, it's important to configure email authentication for your used and unused domains. SPF, DKIM, and DMARC records in DNS allow Microsoft 365 to more accurately protect against spoofing attacks. For more information, see Email authentication in Microsoft 365.
The Microsoft 365 security ladder from EOP to Defender for Office 365
It can be difficult to identity the advantages of Defender for Office 365 over EOP. The following subsections describe the capabilities of each product using the following security emphases:
- Preventing and detecting threats.
- Investigating threats.
- Responding to threats.
EOP capabilities
The capabilities of EOP are summarized in the following table:
| Prevent/Detect | Investigate | Respond |
|---|---|---|
|
|
* The associated protection polices are available in default policies, custom policies, and the Standard and Strict preset security policies. For help with deciding which method to use, see Determine your protection policy strategy.
For more information about EOP, see Exchange Online Protection overview.
Defender for Office 365 Plan 1 capabilities
Defender for Office 365 Plan 1 expands on the prevention and detection capabilities of EOP.
The additional features that you get in Defender for Office 365 Plan 1 on top of EOP are described in the following table:
| Prevent/Detect | Investigate | Respond |
|---|---|---|
|
|
|
* The presence of Email & collaboration > Real-time detections in the Microsoft Defender portal is a quick way to differentiate between Defender for Office 365 Plan 1 and Plan 2.
Defender for Office 365 Plan 2 capabilities
Defender for Office 365 Plan 2 expands on the investigation and response capabilities of Plan 1 and EOP, including the addition of automation.
The additional features that you get in Defender for Office 365 Plan 2 on top of Defender for Office 365 Plan 1 and EOP are described in the following table:
| Prevent/Detect | Investigate | Respond |
|---|---|---|
|
* The presence of Email & collaboration > Explorer in the Microsoft Defender portal is a quick way to differentiate between Defender for Office 365 Plan 2 and Plan 1.
Defender for Office 365 Plan 1 vs. Plan 2 cheat sheet
This quick-reference section summarizes the different capabilities between Defender for Office 365 Plan 1 and Plan 2 that aren't included in EOP.
| Defender for Office 365 Plan 1 | Defender for Office 365 Plan 2 |
|---|---|
Prevent and detect capabilities:
Investigate and respond capabilities: |
Everything in Defender for Office 365 Plan 1 capabilities --- plus --- Prevent and detect capabilities: Investigate and respond capabilities: |
- For more information, see Feature availability across Defender for Office 365 plans.
- Safe Documents is available to users with the Microsoft 365 A5 or Microsoft 365 E5 Security licenses (not included in Defender for Office 365 plans).
- If your current subscription doesn't include Defender for Office 365 Plan 2, you can try Defender for Office 365 free for 90 days. Or, contact sales to start a trial.
- Defender for Office 365 P2 customers have access to Microsoft Defender XDR integration to efficiently detect, review, and respond to incidents and alerts.
Where to go next
Get started with Microsoft Defender for Office 365
Microsoft Defender for Office 365 Security Operations Guide
Migrate from a third-party protection service or device to Microsoft Defender for Office 365
What's new in Microsoft Defender for Office 365
The Microsoft 365 Roadmap describes new features that are being added to Defender for Office 365.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for