Step 5. Protect information
Because ransomware attackers will also look at your on-premises data located on file, database, and other types of servers, one of the best ways to protect that data is to migrate it to your Microsoft 365 tenant. Once there, it can be protected by built-in mitigation and recovery features such as versioning, recycle bin, and Files Restore.
To provide additional protection of sensitive information in your Microsoft 365 tenant:
- Locate your sensitive information.
- Implement strict permissions and eliminating broad access (for example, prevent too many users having write, edit, and delete capabilities).
- Protect your sensitive information.
Note
For detailed deployment guidance for information protection in a Microsoft 365 tenant, see Deploy information protection for data privacy regulations. Although intended for data privacy regulations, much of the guidance also applies to ransomware protection.
Locate your sensitive information
The first task is to identify the types and locations of sensitive information in your tenant, which can include the following types:
- Sensitive
- Proprietary or intellectual property
- Regulated, such regional regulations that specify protection of personally identifying information (PII)
- IT recovery plans
For each type of sensitive information, determine the following:
The use of the information to your organization
A relative measure of its monetary value if it were held for ransom (such as high, medium, low)
Its current location, such as a OneDrive or SharePoint folder or collaboration venue such as a Microsoft Teams team
The current permissions, which consist of:
The user accounts who have access
The actions that are allowed to each account that has access
Implement strict permissions for locations with sensitive information
Implementing strict permissions within your Microsoft 365 tenant uses the principle of least privilege for locations and communications venues, which in Microsoft 365 are typically OneDrive folders, SharePoint sites and folders, and teams.
While it is easier to create file storage locations or teams with broad access (such as the default of everyone in your organization), for sensitive information, the user accounts that are permitted and the actions that are allowed must be confined to the minimum set required to meet collaboration and business requirements.
Once a ransomware attacker has infiltrated your tenant, they try to escalate their privileges by compromising the credentials of user accounts with wider scopes of permissions across your tenant, such as administrator role accounts or user accounts that have access to sensitive information.
Based on this typical attacker behavior, there are two levels of difficulty for the attacker:
- Low: An attacker can use a low-permission account and discover your sensitive information because of broad access throughout your tenant.
- Higher: An attacker can't use a low-permission account and discover your sensitive information because of strict permissions. They must escalate their permissions by determining and then compromising the credentials of an account that has access to a location with sensitive information, but then may only be able to do a limited set of actions.
For sensitive information, you must make the level of difficulty as high as you can.
You can ensure strict permissions in your tenant with these steps:
- From the effort to locate your sensitive information, review the permissions for the locations of sensitive information.
- Implement strict permissions for the sensitive information while meeting collaboration and business requirements and inform the users that are affected.
- Perform change management for your users so that future locations for sensitive information are created and maintained with strict permissions.
- Audit and monitor the locations for sensitive information to ensure that broad permissions aren't being granted.
See Set up secure file sharing and collaboration with Microsoft Teams for detailed guidance. An example of a communication and collaboration venue with strict permissions for sensitive information is a team with security isolation.
Protect your sensitive information
To protect your sensitive information in case a ransomware attacker obtains access to it:
Use controlled folder access to make it more difficult for unauthorized applications to modify the data in controlled folders.
Use Microsoft Purview Information Protection and sensitivity labels and apply them to sensitive information. Sensitivity labels can be configured for additional encryption and permissions with defined user accounts and allowed actions. A file labeled with this type of sensitivity label that is exfiltrated from your tenant will only be useable to a user account defined in the label.
Use Microsoft Purview Data Loss Prevention (DLP) to detect, warn, and block risky, inadvertent, or inappropriate sharing of data containing personal or confidential information based on sensitivity labels, both internally and externally.
Use Microsoft Defender for Cloud Apps to block downloads of sensitive information such as files. You can also use Defender for Cloud Apps anomaly detection policies to detect a high rate of file uploads or file deletion activities.
Impact on users and change management
Administrative changes to broad permissions can lead to users being denied access or being unable to execute some actions.
Additionally, for the protection of sensitive information in your Microsoft 365 tenant, train your users to:
- Create communication and collaboration venues with strict permissions (the minimum set of user accounts for access and the minimum allowed actions for each account).
- Apply the proper sensitivity labels to sensitive information.
- Use controlled folder access.
Resulting configuration
Here's the ransomware protection for your tenant for steps 1-5.
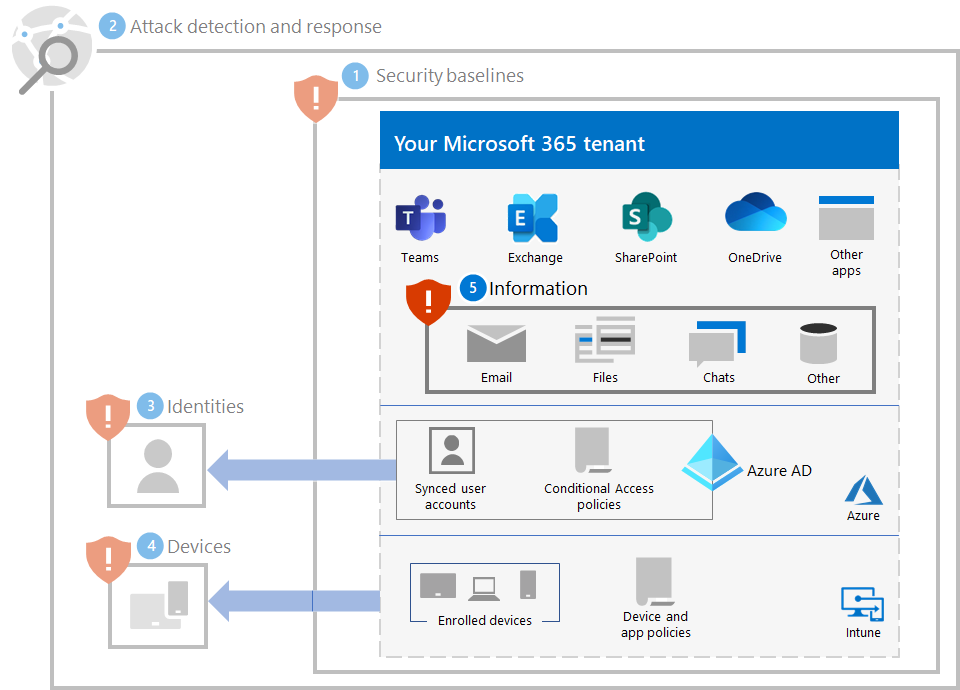
Additional ransomware resources
Key information from Microsoft:
- The growing threat of ransomware, Microsoft On the Issues blog post on July 20, 2021
- Human-operated ransomware
- Quickly deploy ransomware preventions
- 2021 Microsoft Digital Defense Report (see pages 10-19)
- Ransomware: A pervasive and ongoing threat analytics report in the Microsoft Defender portal
- Microsoft's Detection and Response Team (DART) ransomware approach and best practices and case study
Microsoft 365:
- Maximize Ransomware Resiliency with Azure and Microsoft 365
- Ransomware incident response playbooks
- Malware and ransomware protection
- Protect your Windows 10 PC from ransomware
- Handling ransomware in SharePoint Online
- Threat analytics reports for ransomware in the Microsoft Defender portal
Microsoft Defender XDR:
Microsoft Azure:
- Azure Defenses for Ransomware Attack
- Maximize Ransomware Resiliency with Azure and Microsoft 365
- Backup and restore plan to protect against ransomware
- Help protect from ransomware with Microsoft Azure Backup (26-minute video)
- Recovering from systemic identity compromise
- Advanced multistage attack detection in Microsoft Sentinel
- Fusion Detection for Ransomware in Microsoft Sentinel
Microsoft Defender for Cloud Apps:
Microsoft Security team blog posts:
3 steps to prevent and recover from ransomware (September 2021)
A guide to combatting human-operated ransomware: Part 1 (September 2021)
Key steps on how Microsoft's Detection and Response Team (DART) conducts ransomware incident investigations.
A guide to combatting human-operated ransomware: Part 2 (September 2021)
Recommendations and best practices.
-
See the Ransomware section.
Human-operated ransomware attacks: A preventable disaster (March 2020)
Includes attack chain analyses of actual attacks.
Norsk Hydro responds to ransomware attack with transparency (December 2019)
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for