Reinstate admin privileges for a customer's Azure CSP subscriptions
Appropriate roles: Global admin | Admin agent
As a Cloud Solution Provider (CSP) program partner, your customers often rely on you to manage their Azure usage and their systems. You must have admin privileges to help them. If you don't already have admin privileges, you can work with your customer to reinstate them.
Admin privileges for Azure in the CSP program
Some admin privileges are granted automatically when you establish a reseller relationship with a customer. Others must be granted to you by a customer.
There are two levels of admin privileges for Azure in CSP:
Tenant-level admin privileges (that is, delegated admin privileges) give you access to your customers' tenants. This delegated access allows you to perform administrative functions, such as adding and managing users, resetting passwords, and managing user licenses.
You get tenant-level admin privileges when you establish CSP reseller relationships with customers.
Subscription-level admin privileges give you complete access to your customers' Azure CSP subscriptions. This access allows you to provision and manage their Azure resources.
You get subscription-level admin privileges when creating Azure CSP subscriptions for your customers.
Reinstate your CSP admin privileges: your actions
You and your customer each have actions to perform to reinstate your CSP admin privileges. This section describes the actions for you to take.
To reinstate your CSP admin privileges, use the following steps:
Sign in to Partner Center and select Customers.
On the Customer List, select Request a reseller relationship.
For the Delegated Admin Privileges check box:
- Leave the check box selected to establish the relationship with delegated administrator privileges.
- Clear the check box to establish the relationship without delegated administrator privileges.
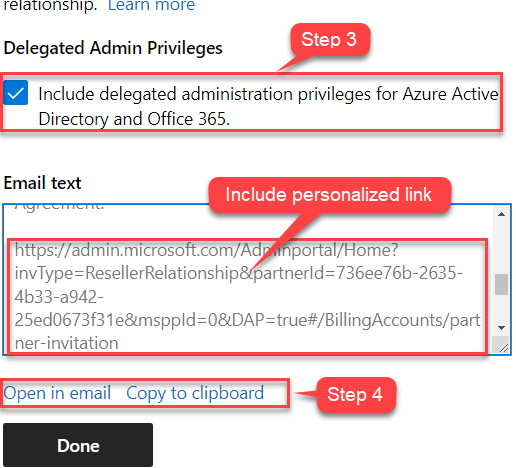
Review the draft email invitation.
- Select Open in email to open the draft invitation in your default email application.
- Select Copy to clipboard to copy and paste the invitation into an email message.
Important
You can edit the text in the draft email message, but be sure to include the personalized link because it links the customer directly to your account.
Select Done.
Send the email invitation to your customer.
Note
To be able to accept the request, the person in your customer's organization must be a Global admin of your customer's tenant.
Your customer selects the link they received in the email. The link takes them to Microsoft Admin Center where they can accept your invitation.
After the customer accepts your invitation, they'll appear on your Customers page in Partner Center, and you'll be able to provision and manage the service for the customer from there.
After your customer approves the reseller relationship invitation using the link provided, connect to the partner tenant to get the
object IDof the AdminAgents group.Connect-AzAccount -Tenant "Partner tenant" # Get Object ID of AdminAgents group Get-AzADGroup -DisplayName AdminAgentsEnsure that your customer has:
- The role of owner or user access administrator
- Permissions to create role assignments at the subscription level
Reinstate your CSP admin privileges: customer actions
This section describes the customer's actions to reinstate your CSP admin privileges.
To complete reinstating your CSP admin privileges, your customer uses PowerShell or the Azure CLI to perform the following steps:
Your customer uses PowerShell to update the
Az.Resourcesmodule.Update-Module Az.ResourcesYour customer connects to the tenant in which the CSP subscription exists.
Connect-AzAccount -TenantID "<Customer tenant>"az login --tenant <Customer tenant>Your customer connects to the subscription.
This step is applicable only if the user has role assignment permissions over multiple subscriptions in the tenant.
Set-AzContext -SubscriptionID "<CSP Subscription ID>"az account set --subscription <CSP Subscription ID>Your customer creates the role assignment.
New-AzRoleAssignment -ObjectID "<Object ID of the AdminAgents group from step 7 of your actions section>" -RoleDefinitionName "Owner" -Scope "/subscriptions/<CSP subscription ID>" -ObjectType "ForeignGroup"az role assignment create --role "Owner" --assignee-object-id <Object ID of the AdminAgents group from step 4> --scope "/subscriptions/<CSP Subscription Id>" --assignee-principal-type "ForeignGroup"
Instead of granting owner permissions at the subscription level, they can be granted at the resource group or resource level:
At the resource group level
New-AzRoleAssignment -ObjectID "<Object ID of the AdminAgents group from step 4>" -RoleDefinitionName Owner -Scope "/subscriptions/<SubscriptionID of CSP subscription>/resourceGroups/<Resource group name>" -ObjectType "ForeignGroup"az role assignment create --role "Owner" --assignee-object-id <Object ID of the AdminAgents group from step 4> --scope "/subscriptions/<CSP Subscription Id>/resourceGroups/<Resource group name>" --assignee-principal-type "ForeignGroup"At the resource level
New-AzRoleAssignment -ObjectID "<Object ID of the AdminAgents group from step 4>" -RoleDefinitionName Owner -Scope "<Resource URI>" -ObjectType "ForeignGroup"az role assignment create --role "Owner" --assignee-object-id <Object ID of the AdminAgents group from step 4> --scope "<Resource URI>" --assignee-principal-type "ForeignGroup"
Troubleshooting the customer steps
If your customer is unable to complete the preceding steps, suggest the following command and provide the resulting newRoleAssignment.log file to Microsoft for further analysis:
New-AzRoleAssignment -ObjectId <principal ID> -RoleDefinitionName "Owner" -Scope "/subscriptions/<customer subscription>" -ObjectType "ForeignGroup" -Debug > newRoleAssignment.log
Reinstate your CSP admin privileges: PowerShell catchall procedure
If the steps in the preceding sections don't work, or if you get errors when attempting them, try the following "catchall" procedure to reinstate admin rights for your customer:
Install-Module -Name Az.Resources -Force -Verbose
Import-Module -Name Az.Resources -Verbose -MinimumVersion 4.1.1
Connect-AzAccount -Tenant <customer tenant>
Set-AzContext -SubscriptionId <customer subscriptions>
New-AzRoleAssignment -ObjectId <principal ID> -RoleDefinitionName "Owner" -Scope "/subscriptions/<customer subscription>" -ObjectType "ForeignGroup"
If the "catchall" procedure fails at Import-Module, try the following steps:
- If the import fails because the module is in use, restart the PowerShell session by closing and reopening all windows.
- Check the version of
Az.ResourceswithGet-Module Az.Resources -ListAvailable.- If version 4.1.1 isn't in the available list, you must use
Update-Module Az.Resources -Force.
- If version 4.1.1 isn't in the available list, you must use
- If an error states that
Az.Accountsmust be a specific version, update that module as well, replacingAz.ResourceswithAz.Accounts. You must then restart the PowerShell session.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for