Troubleshoot user access issues for different environments
Multiple factors affect user access to environments. Administrators can use the Run diagnostics command to assess user access to an environment, and get details and mitigation suggestions as to why a user can or can't access the environment.
To access an environment, a user must meet the following criteria:
- Be enabled for sign-in in Microsoft Entra ID.
- Have a valid license that has a Dynamics 365 or Microsoft Power Platform recognized service plan, or the environment must have active per-app plans.
- Be a member of the environment's Microsoft Entra group (if one has been associated with the environment).
- Have at least one Dataverse security role assigned directly to them or to a group team they're a member of.
A user's level of access within the environment and to the resources (apps and data) in the environment is determined by the privileges defined in the security roles assigned to that user. Their access mode being Administrative or Read-Write also determines their level of access within an environment.
User diagnostics
Use the following steps to run user access diagnostics on a user in an environment.
In the Power Platform admin center, select an environment.
Select Settings > Users + permissions > Users.
Select a user.
Select Run diagnostics.
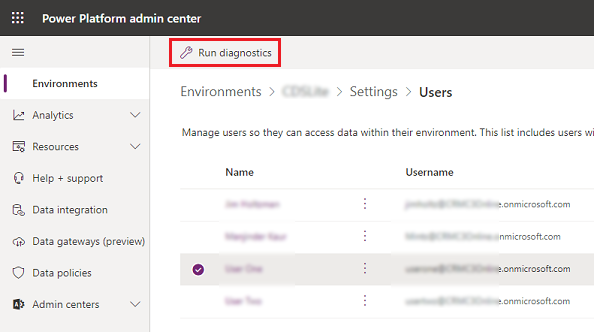
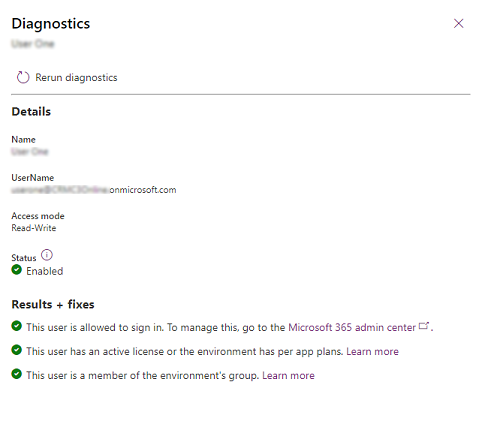
Review the details for the user, and take any needed corrective actions.
Note
The action of running or rerunning diagnostics will force the user information in Microsoft Entra ID to synchronize to the environment's Dataverse database to provide up-to-date status on the user's properties. If the diagnostic run doesn't eliminate the root cause of a user access issue, please provide the results of the diagnostic run in the support ticket you create; this will greatly help Microsoft Support engineers to resolve your issue faster.
Access issues
The following issues are documented below. If you don't see your issue:
- See if you can get your question answered here: https://powerusers.microsoft.com/t5/Power-Apps-Community/ct-p/PowerApps1.
- Create a support request.
Diagnostic tool for user permissions in the Power Platform admin center
Several factors influence user access in an environment. To help administrators with diagnosing user access to an environment and reasons for access or no access, the new “Run diagnostics” feature in the Power Platform admin center provides basic access diagnostics for individual users in the environment. The feature helps to detect potential causes to user sign-in and other issues and suggests potential mitigations. See User diagnostics.
Dataverse security roles to users
When an error screen stating the user has no roles is encountered, a system administrator needs to assign roles to the user. Roles can be assigned directly to the user, or to a group team that the user is a part of. For information on how to assign Dataverse security roles to a user, see: Assign a security role to a user.
Troubleshoot record visibility issues
See How access to a record is determined.
Troubleshoot license and membership issues
- Verify if a license has been assigned to the user and assign one if not already. See: Add a license to a user account.
- Once a license is assigned, it may take some time for the license change to sync to the environment. To trigger a sync for this user, the system administrator for the environment can readd the user to the environment. See: Add users to an environment that has a Dataverse database.
Troubleshoot access issues
- As a system administrator of the environment, verify that the environment is associated with any Microsoft Entra group. See: Associate a security group with an environment.
- Ensure the user with the access issue is a member of the group associated with the environment. See: Create a security group and add members to the security group.
- Once user membership in the environment’s group is updated, it may take some time for the change to sync to the environment. To trigger a sync for this user, the system administrator for the environment can readd the user to the environment. See: Add users to an environment that has a Dataverse database.
Troubleshoot permission issues
You don't have sufficient permissions to access customer engagement apps (Dynamics 365 Sales, Dynamics 365 Customer Service, Dynamics 365 Field Service, Dynamics 365 Marketing, and Dynamics 365 Project Service Automation). A system administrator needs to complete the following steps.
In the Power Platform admin center, select an environment.
Select Settings > Users + permissions > Users.
Open the user record.
Select More Commands (
 ) > Manage Roles.
) > Manage Roles.Make note of the role assigned to the user. If appropriate, select a different security role. Close the Manage User Roles dialog box.
Select Security > Security Roles.
Select the security role from step 4.
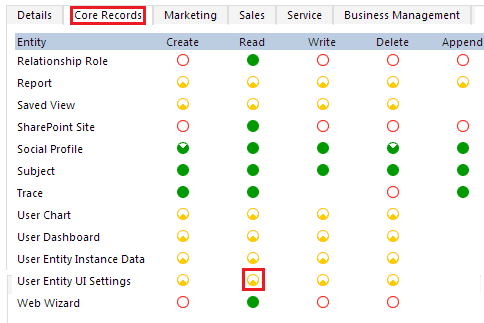
Select Core Records.
Confirm that the Read permission for User Entity UI Settings is set to the User level (a yellow circle with a wedge-shaped segment).
If the security role is missing this permission, the system administrator will need to change this setting by clicking or tapping on it.
Troubleshoot unaccounted user issues
In some cases, users aren't automatically provisioned into environments.
If a user meets all access requirements but is still missing from an environment, the user may fall into one of the following cases:
Users with only Office licenses (with Dataverse plan enabled) won't be pre-provisioned into environments.
Owners of Microsoft Entra groups that are associated with environments won't be pre-provisioned.
Members of Microsoft Entra groups that are part of a Group Team created for the Microsoft Entra group won't be pre-provisioned.
Users won't be pre-provisioned into Microsoft Dataverse for Teams environments.
Although these users aren't pre-provisioned, they can be added to environments through on-demand sync. See the section below for ways to add or refresh users on demand.
Troubleshoot on demand user management
As mentioned above, there are cases where users aren't provisioned automatically. Additionally, there may be delays in reflecting the users' latest status in environments. In such cases, adding or refreshing specific users on demand can be helpful.
There are multiple ways to do this:
Just-in-time (JIT) user provisioning: When users access an environment URL, access requirements are checked at the time of sign-in and qualified users are added to the environment.
User impersonation call: Impersonation call triggers a JIT sync for the user. See How to impersonate a user.
Add users in the Power Platform admin center: Admins can add or refresh users. See Add users to an environment.
PowerShell cmdlets: See PowerShell support for Power Apps.
Connectors: See Power Platform for Admins.
Power Automate template: See Force Sync Microsoft Entra Group members to specified CDS instance.
Known issue
The check for the presence of security roles assigned to a user only checks for roles directly assigned to the user and can't currently check for roles inherited through group team memberships.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for