Configure user authentication in Microsoft Copilot Studio
Important
Power Virtual Agents capabilities and features are now part of Microsoft Copilot Studio following significant investments in generative AI and enhanced integrations across Microsoft Copilot.
Some articles and screenshots may refer to Power Virtual Agents while we update documentation and training content.
Authentication allows users to sign in, giving your copilot access to a restricted resource or information. Users can sign in with Microsoft Entra ID, or with any OAuth2 identity provider such as Google or Facebook.
Note
In Microsoft Teams, you can configure a Microsoft Copilot Studio copilot to provide authentication capabilities, so that users can sign in with a Microsoft Entra ID or any OAuth2 identity provider, such as a Microsoft or Facebook account.
You can add user authentication to your copilot when you edit a topic.
Microsoft Copilot Studio supports the following authentication providers:
- Azure Active Directory v1
- Microsoft Entra ID
- Any identity provider that complies with the OAuth2 standard
Important
Changes to the authentication configuration will only take effect after you publish your copilot. Make sure to plan ahead before you make authentication changes to your copilot.
Choose an authentication option
Microsoft Copilot Studio supports several authentication options. Choose the one that meets your needs.
To change your copilot's authentication settings, in the navigation menu under Settings, go to the Security tab and select the Authentication card.
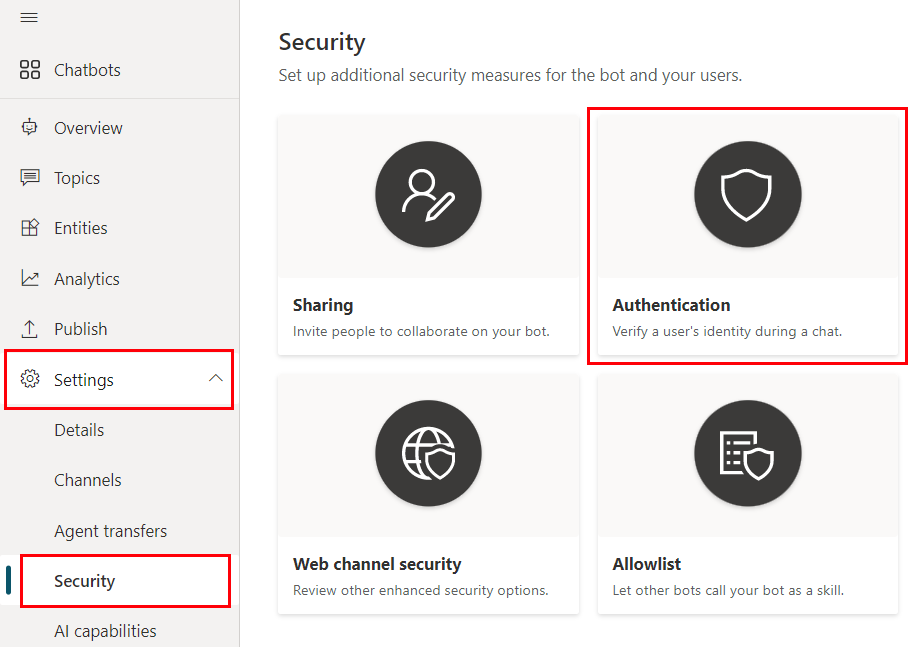
The following authentication options are available:
- No authentication
- Only for Teams and Power Apps
- Manual (for any channel including Teams)

No Authentication
No authentication means your copilot doesn't require your users to sign in when interacting with the copilot. An unauthenticated configuration means your copilot can only access public information and resources.
Caution
Selecting the No authentication option will allow anyone who has the link to chat and interact with your bot or copilot.
We recommend you apply authentication, especially if you are using your bot or copilot within your organization or for specific users, along with other security and governance controls.
Only for Teams and Power Apps
Important
When the Only for Teams and Power Apps option is selected, all channels except the Teams channel will be disabled.
Additionally, the Only for Teams and Power Apps option is not available if your copilot is integrated with Dynamics 365 Customer Service.
Teams and Power Apps authentication is enabled by default for copilots and copilots that you create in Microsoft Copilot Studio.
This configuration automatically sets up Microsoft Entra ID authentication for Teams without the need for any manual configuration. Since Teams authentication itself identifies the user, users aren't prompted to sign in while they're in Teams, unless your copilot needs expanded scope.
Only the Teams channel is available if you select this option. If you need other channels but still want authentication for your copilot (such as when using generative AI features, choose Manual authentication.
If you select the Only for Teams and Power Apps option, the following variables are available in the authoring canvas:
UserIDUserDisplayName
For more information about these variables and how to use them, see Add user authentication to a Microsoft Copilot Studio copilot.
AuthToken and IsLoggedIn variables aren't available with this option. If you need an authentication token, use the Manual option.
If you change from Manual to Only for Teams and Power Apps authentication, and your topics contain the variables AuthToken or IsLoggedIn, they're displayed as Unknown variables after the change. Make sure to correct any topics with errors before you publish your copilot.
Manual (for any channel including Teams)
You can configure any Microsoft Entra ID v1, Microsoft Entra ID, or OAuth2-compatible identity provider with this option. The following variables are available in the authoring canvas after you configure manual authentication:
UserIDUserDisplayNameAuthTokenIsLoggedIn
For more information about these variables and how to use them, see Add user authentication to a Microsoft Copilot Studio copilot.
Once the configuration is saved, make sure to publish your copilot so the changes take effect.
Note
Authentication changes only take effect after the copilot is published.
Required user sign in and copilot sharing
Require users to sign in determines whether a user needs to sign in before talking with the copilot. We highly recommended that you turn on this setting when your copilot needs to access sensitive or restricted information.
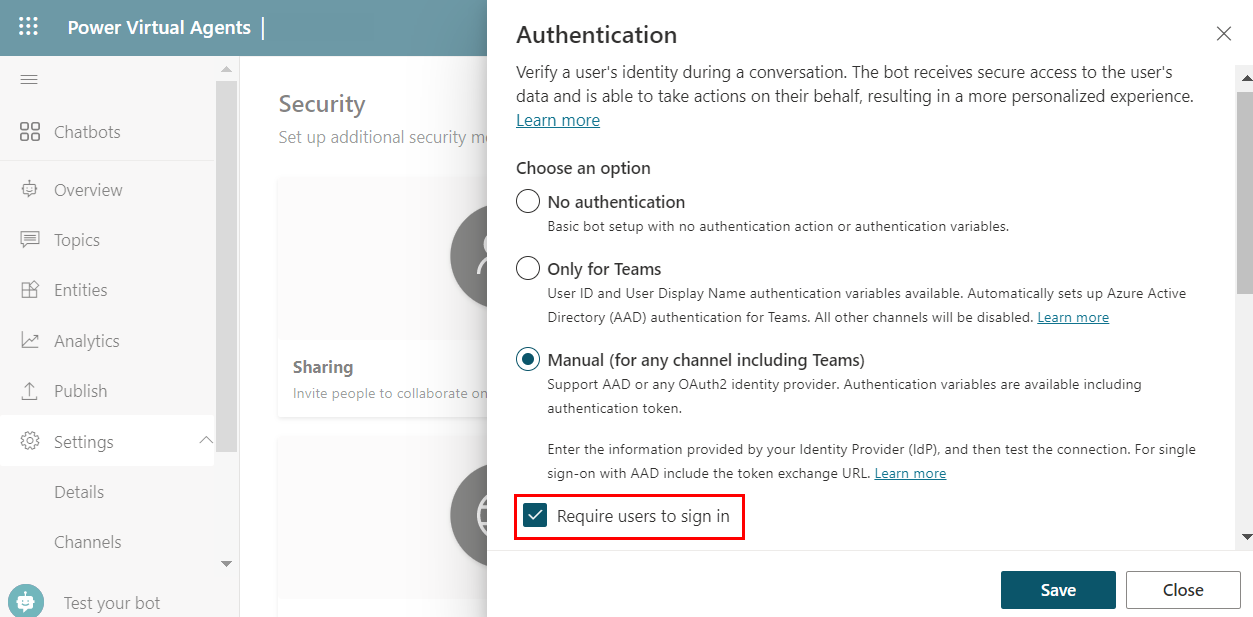
This option isn't available when the No authentication option is chosen.
If you turn off this option, your copilot won't ask users to sign in until it encounters a topic that requires them to.
When you turn on this option, it creates a system topic called Require users to sign in. This topic is only relevant for the Manual authentication setting. Users are always authenticated on Teams.
The Require users to sign in topic is automatically triggered for any user who talks to the copilot without being authenticated. If the user fails to sign in, the topic redirects to the Escalate system topic.
The topic is read-only and can't be customized. To see it, select Go to the authoring canvas.
Control who can chat with the copilot in the organization
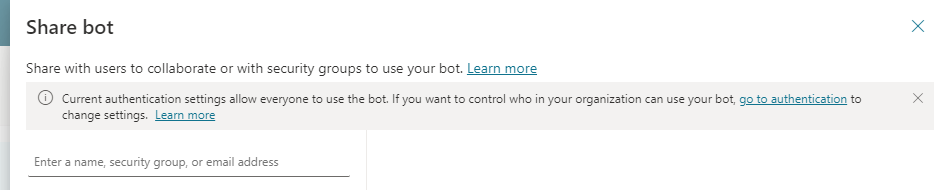
Your copilot's authentication and Require user to sign in setting in combination determines whether you can share the copilot to control who in your organization can chat with it. The authentication setting doesn't affect sharing a copilot for collaboration.
No authentication: Any user who has a link to the copilot (or can find it; for example, on your website) can chat with it. You can't control which users in your organization can chat with the copilot.
Only for Teams: The copilot works only on the Teams channel. Since the user is always signed in, the Require users to sign in setting is turned on and can't be turned off. You can use copilot sharing to control who in your organization can chat with the copilot.
Manual (for any channel including Teams):
If the service provider is either Azure Active Directory or Microsoft Entra ID, you can turn on Require users to sign in to control who in your organization can chat with the copilot using copilot sharing.
If the service provider is Generic OAuth2, you can turn Require users to sign in on or off. When it's turned on, a user who signs in can chat with the copilot. You can't control which specific users in your organization can chat with the copilot using copilot sharing.
When a copilot's authentication setting can't control who can chat with it, if you select Share on the copilot's overview page a message informs you that anyone can chat with your copilot.
Manual authentication fields
The following are all the fields you can see when you're configuring manual authentication. Which fields you see depends on your choice for service provider.
| Field name | Description |
|---|---|
| Authorization URL template | The URL template for authorization, as defined by your identity provider. For example, https://login.microsoftonline.com/common/oauth2/v2.0/authorize |
| Authorization URL query string template | The query template for authorization, as provided by your identity provider. Keys in the query string template vary, depending on the identity provider. |
| Client ID | Your client ID, obtained from the identity provider. |
| Client secret | Your client secret, obtained when you created the identity provider app registration. |
| Refresh body template | The template for the refresh body. |
| Refresh URL query string template | The refresh URL query string separator for the token URL, usually a question mark (?). |
| Refresh URL template | The URL template for refresh; for example, https://login.microsoftonline.com/common/oauth2/v2.0/token. |
| Scope list delimiter | The separator character for the scope list. Empty spaces aren't supported in this field.1 |
| Scopes | The list of scopes that you want users to have after they've signed in. Use the Scope list delimiter to separate multiple scopes.1 Only set necessary scopes and follow the least privilege access control principle. |
| Service provider | The service provider you want to use for authentication. For more information, see OAuth generic providers. |
| Tenant ID | Your Microsoft Entra ID tenant ID. Refer to Use an existing Microsoft Entra ID tenant to learn how to find your tenant ID. |
| Token body template | The template for the token body. |
| Token exchange URL (required for SSO) | This is an optional field used when you're configuring single sign-on. |
| Token URL template | The URL template for tokens, as provided by your identity provider; for example, https://login.microsoftonline.com/common/oauth2/v2.0/token. |
| Token URL query string template | The query string separator for the token URL, usually a question mark (?). |
1 You can use spaces in the Scopes field if the identity provider requires it. In that case, enter a comma (,) in Scope list delimiter, and enter spaces in the Scopes field.
Remove the authentication configuration
- In the navigation menu, under Settings, select Security. Then select the Authentication card.
- Select No authentication.
- Publish the copilot.
If authentication variables are being used in a topic, they become Unknown variables. Go to the Topics page to see which topics have errors and fix them before publishing.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for