The Cable GuyNetwork Policy Server
Joseph Davies
This column is based on a prerelease version of Windows Server 2008. All information herein is subject to change.
The Network Policy Server (NPS) service in Windows Server 2008 is the replacement for the Internet Authentication Service (IAS) in Windows Server 2003. NPS allows a computer running Windows Server 2008 to act as a Remote Authentication Dial-In User Service (RADIUS) server and proxy. RADIUS is an Internet Engineering Task
Force (IETF) protocol specified in RFCs 2865 and 2866 that provides centralized authentication, authorization, and accounting (AAA) for network access devices such as wireless access points. RADIUS servers perform AAA for network access devices. RADIUS proxies forward RADIUS messages between RADIUS clients (network access devices) and RADIUS servers.
NPS includes many enhancements to facilitate deployment of authenticated network access, to provide extensibility for third-party components, and to support the latest networking technologies and platforms. The new NPS snap-in is shown in Figure 1.
Figure 1** The new NPS snap-in **(Click the image for a larger view)
Network Policy Server Features
In this column, I will discuss NPS features that were not included in previous versions of Windows®. I'll begin with how Network Access Protection (NAP) helps enforce health requirements for your network, then touch on management, configuration, IPv6 support, and other elements. I'll also describe the features of the new NPS snap-in.
Network Access Protection NAP, supported in Windows Server® 2008, Windows Vista and Windows XP with Service Pack 3 is a set of new technologies that can help you enforce compliance with computer health requirements, allowing you to better protect your intranet. Your health policies can specify, for example, that a firewall must be installed and enabled and that the latest operating system updates must be installed on all clients connecting to your network. With NAP, you can create customized policies to certify computer health before allowing network access or communication, automatically update computers to ensure ongoing compliance, and confine noncompliant computers to a restricted network until they do comply. For more information, see microsoft.com/nap.
In a NAP deployment, the NPS server is a NAP health policy server that evaluates the health of NAP clients on behalf of NAP enforcement points—such as health registration authorities (HRAs), 802.1X access points, virtual private network (VPN) servers, and Dynamic Host Configuration Protocol (DHCP) servers. The NPS server also determines whether the clients should be granted full or limited access to the intranet. Network policies, health policies, and NAP settings determine the health evaluation behavior for NPS.
EAPHost and EAP Policy Support NPS supports EAPHost, the new architecture for Extensible Authentication Protocol (EAP) authentication methods. This new architecture allows EAP method vendors to easily develop and install new EAP methods for 802.1X or point-to-point protocol (PPP)-based authentication on both client computers and NPS servers.
EAPHost will support the installation and use of all the EAP methods listed on the EAP Registry at www.iana.org/assignments/eap-numbers, as well as other popular authentication methods such as Cisco Systems Lightweight EAP (LEAP). EAPHost allows multiple implementations of an EAP method to coexist. For example, you can install and select both the Microsoft version of Protected EAP (PEAP) and the Cisco Systems version.
For EAP method vendors, EAPHost supports EAP methods already developed for Windows XP and Windows Server 2003, plus an easier way of developing new EAP methods for Windows Vista® and Windows Server 2008. After installation, you can configure the required EAP methods for a given network access scenario in a network policy. A network policy for NPS is the same as a remote access policy for IAS.
For more information about EAPHost architecture, see technetmagazine.com/issues/2007/05/CableGuy.
Configuration Stored in XML IAS stored its configuration information in a Jet database. NPS now stores configuration information in XML format, which makes it easier to export the configuration of one NPS server and import it on another. Exporting and importing configuration files is one way to synchronize the settings of multiple NPS servers in a fault-tolerant configuration. You can export the NPS configuration with the netsh nps export command and import it with the netsh nps import command.
Common Engineering Criteria Compliance NPS has been updated to support deployment in environments that must meet Microsoft® Common Engineering Criteria (CEC). For more information, see microsoft.com/windowsserversystem/cer/allcriteria.mspx.
Robust NPS Extension DLLs The NPS service can be extended through extension and authorization DLLs. In contrast with IAS, these third-party components are sandboxed in NPS so that any problems they encounter will not affect the operation or running of the NPS service.
IPv6 Support NPS supports IPv6 and deployment in native or tunneled IPv6 environments. You can configure IPv6 addresses for RADIUS clients or remote RADIUS servers and the NPS service can communicate over IPv6 for Active Directory® domain services account authentication and authorization operations.
IAS vs. NPS
If you are already familiar with the IAS snap-in for Windows Server 2003, you'll appreciate the following changes in the NPS snap-in:
- Remote access policies have become network policies and have been moved under the Policies node.
- The RADIUS Clients node has been moved under the RADIUS Clients and Servers node.
- There is no longer a Connection Request Processing node. The Connection Request Policies node has been moved under Policies and the Remote RADIUS Server Groups node has been moved under RADIUS Clients and Servers.
- Remote access policy conditions and profile settings have been reorganized on the Overview, Conditions, Constraints, and Settings tabs for the properties of a network policy.
- Connection request policy conditions and profile settings have been reorganized on the Overview, Conditions, and Settings tabs for the properties of a connection request policy.
- The Remote Access Logging folder has been renamed the Accounting node and no longer has the Local File or SQL ServerTM nodes.
Automatic Generation of Strong RADIUS Shared Secrets RADIUS shared secrets are used to verify that RADIUS messages were sent by a RADIUS client, server, or proxy configured with the same shared secret. Shared secrets are also used to encrypt some sensitive RADIUS attributes, such as passwords and encryption keys. Strong RADIUS shared secrets are a long (more than 22 characters) sequence of random letters, numbers, and punctuation.
With the NPS snap-in, you can automatically generate a strong RADIUS shared secret when you add or edit a RADIUS client. This strong shared secret can be copied to a text editor, such as Notepad, so you have the ability to configure the network access device or NAP enforcement point with the same shared secret.
Integration with Server Manager You can install NPS through the Initial Configuration Tasks and Server Manager tools. In both cases, you install NPS with the Network Policy and Access Services role. To get started, in the Initial Configuration Tasks tool under Customize This Server, click the Add Roles option. In the Server Manager tool, open Roles Summary and click Add Roles.
After NPS is installed, you can click Network Policy and Access Services under the Roles node in the console tree of Server Manager to check the status of the NPS service and to view error events encountered in the last 24 hours. When you expand the Network Policy and Access Services node in the console, you can configure NPS with the NPS snap-in.
Enhanced Netsh Support Windows Server 2003 had a limited set of commands in the netsh aaaa context to configure IAS. In Windows Server 2008, the new netsh nps context has an extensive set of commands for configuring NPS at the command line or through a script. Now, with netsh nps commands, you can configure RADIUS clients and remote RADIUS servers, network policies, logging, and for NAP, health policies, system health validators, and remediation server groups. Scripts consisting of commands in the netsh nps context provide another way for you to synchronize the settings of multiple NPS servers in a fault tolerant configuration.
Source Tags for Network Policy Isolation Network policies can be configured for a specific type of network access server or NAP enforcement point, such as a DHCP server or an HRA, which becomes a source tag that classifies the network policy. Windows Server 2008-based access servers and NAP enforcement points include this source tag in their RADIUS messages. When a RADIUS message requesting access is received, the NPS service attempts to find a matching network policy that has the same source tag as the incoming message. If there is no policy match, NPS attempts to find a matching network policy for those policies that have no source tag specified.
Using the source tag in network policy and incoming RADIUS messages isolates the different types of network policies from each other. For example, network policies for DHCP servers are not used for VPN connections.
Integration with Cisco Network Access Control NPS supports features to better integrate into an environment that uses Cisco hardware and Network Access Control (NAC). The features include support for the Host Credential Authorization Protocol (HCAP) and HCAP conditions, the policy expiration condition, and the extended state Network Access Protection setting in network policies.
New Network Policy Conditions Network policies in NPS have new conditions that are intended to specify computer groups, user groups, allowed EAP types, and client and access server IPv6 addresses. For HCAP support, NPS has new conditions for location groups and user groups. For NAP support, NPS has new policy conditions for identity type, health policy, NAP-capable computers, operating system, and policy expiration.
The NPS Snap-In The new NPS snap-in has been significantly enhanced so you can more easily create and manage RADIUS clients and remote RADIUS servers, network policies for common network access scenarios, health policies and NAP settings for NAP scenarios, and logging settings.
In the RADIUS Clients and Servers node, you can configure RADIUS clients (network access servers, NAP enforcement points, or other RADIUS proxies when NPS is acting as a RADIUS server) and remote RADIUS server groups (other RADIUS servers when NPS is acting as a RADIUS proxy).
In the Policies node, you can configure connection request policies (whether the NPS service will act as a RADIUS server or proxy), network policies (authorization and connection settings and constraints when the NPS service acts as a RADIUS server), and health policies (system health compliance for NAP clients). When you select a connection request policy or a network policy in the details pane, the NPS snap-in displays the policy's conditions and settings. Figure 2 shows an example of what this looks like.
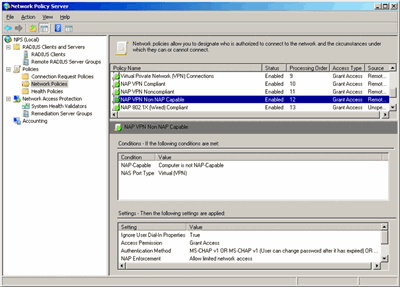
Figure 2** The NPS snap-in enhanced display **(Click the image for a larger view)
In the Network Access Protection node, the System Health Validators node allows you to configure NAP health requirements. The Remediation Server Groups node lets you configure the set of servers that restricted NAP clients can access for the VPN and DHCP NAP enforcement methods. Finally, in the Accounting node, you can configure how NPS stores accounting information.
The NPS snap-in includes an extensive set of wizards to automate the initial configuration of RADIUS clients and the policies needed for NAP enforcement methods, dial-up or VPN-based connections, and 802.1X-authenticated wireless and wired connections. For NAP enforcement methods, the NAP wizard automatically configures all of the connection request policies, network policies, and health policies.
These new wizards are available when you click the NPS node in the NPS snap-in. To configure policies and settings for NAP enforcement methods, select Network Access Protection in the Standard Configuration dropdown box, and then click Configure NAP. To configure policies and settings for VPN or dial-up network access, select RADIUS server for Dial-Up or VPN Connections in the Standard Configuration dropdown box, and then click Configure VPN or Dial-Up. In order to configure policies and settings for 802.1X-authenticated wired or wireless access, select RADIUS server for 802.1X Wireless or Wired Connections in the Standard Configuration dropdown box, and then click Configure 802.1X.
Each of these wizards guides you through the most common configuration elements for your chosen scenario. The wizards for the NAP enforcement methods are especially helpful: the NAP wizard for VPN enforcement creates a connection request policy, three network policies (for compliant NAP clients, noncompliant NAP clients, and non-NAP capable clients), and two health policies (for compliant and noncompliant NAP clients).
The new NAP wizards and other wizards for creating RADIUS clients, remote RADIUS server groups, connection request policies, and network policies make it much easier to configure NPS for a variety of network access scenarios.
Joseph Davies is a technical writer with Microsoft and has been teaching and writing about Windows networking topics since 1992. He has written eight books for Microsoft Press and is the author of the monthly online TechNet Cable Guy column.
© 2008 Microsoft Corporation and CMP Media, LLC. All rights reserved; reproduction in part or in whole without permission is prohibited.