ToolboxNew Products for IT Professionals
Greg Steen
The opinions expressed in this column are solely those of the author and do not necessarily reflect the opinions of Microsoft. All prices were confirmed at the time of writing, and are subject to change.
Create Disk Images
Clonezilla-Live
clonezilla.org/clonezilla-live
At some point, most IT professionals find themselves needing to clone a hard drive to switch from a failing disk, upgrade to a larger disk or create a "point-in-time" archive of a system (for instance, for legal and informational purposes after an employee has been terminated). Clonezilla is a free open-source collaborative project that can help you create disk images. Clonezilla-Live puts the imaging utility in a downloadable, ready-to-go "live" format that you can burn to disk, install to a machine or launch from a PXE boot and just begin using. The project site offers prepackaged versions for all those use cases, too. The live OS is a Debian Linux modification with Clonezilla wired in.
At its heart. Clonezilla is a command-line utility. So the user interface is a little rough, but it's lightweight because it doesn't have to load an XWindows extension such as KDE and Gnome to run. While the main Clonezilla project can clone many computers simultaneously, the live-media edition is tailored toward cloning individual machines or drives.
There are two main modes of operation. The first clones or restores a disk or partition via image file; the second does a device-to-device clone or restoration. For the first method, in addition to local storage, the Clonezilla supports networked file storage via SSH, SAMBA or NFS so that you can keep your images in a remote location. For the second method, you can similarly mount remote partitions in addition to local devices. From that point, you pick your operation—either restoration or creation—and begin your disk imaging.
Clonezilla offers many advanced options for those who need more customization with their images. You can also get to the Debian shell to run your own command-line operations, if you wish. The project Web site offers numerous helpful walkthroughs, instructions and screen shots that can help get the application to do what you need it to do.
So the next time you need to image a drive, you may want to consider the free Clonezilla-Live project.
Price: Free.
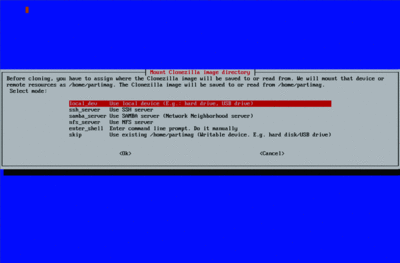
Clonezilla-Live (Click the image for a larger view)
Identify Unknown Files
TrIDNet File Identifi er
Have you or your users ever encountered a file that couldn't be opened by Windows because it didn't know what type of file it was without a file extension? One way you can detect the file type is with the TrIDNet file identifier.
TrIDNet is a .Net GUI wrapper to the TrIDEngine; both were written by Marco Pontello. This free, easy-to-use utility requires no installer—you can just drop it onto your portable administration tools, USB key or network share so that it's available when you need it on any desktop in your organization. Simply browse to the file in question; the utility compares what it reads in the unknown file to a definition library of more than 3,700 file-type descriptors, looking for a match.
The descriptor files are XML documents, so you can easily tweak them or add your own. TrIDNet keeps the list of definitions in memory as you use the application, so it doesn't have to load them all for each file you scan. Once the scan is complete, the UI displays the results in a data grid, showing match candidates for the file type and the percentage likelihood of that match. In addition, you'll also see the extension of the matches so that you can change the file name, which lets Windows once again recognize the file and lets the standard opener open it.
Also listed are the file-type description and the points of comparison used for the match. Double-clicking on a result provides more detail. Here, you'll again see the file type and extension as well as a link to the definition file that recognized the file type (in case you want to verify the match yourself by reading the matching rules). You'll also see a URL of a reference to the type (if available), any remarks noted in the definition file and contact details for the author of that definition file.
If you ever get stuck with unknown file, the free TrIDNet File Identifier utility may help you out.
Price: Free
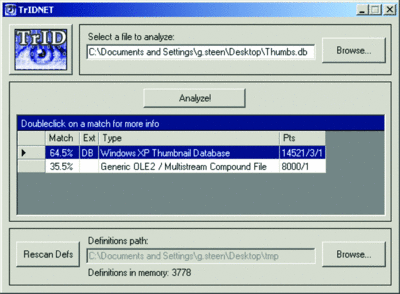
TrIDNet File Identifier (Click the image for a larger view)
Protect Sensitive Data
TrueCrypt 6.2
In today's mobile world, securing your critical data is more important than ever. One option for securing sensitive information is to password-protect and perhaps encrypt each file—but that's usually not the most efficient approach.
Another option is the latest release of TrueCrypt, which gives you both logical file container and physical volume encryption on the fly. TrueCrypt is a user-supported, free and open-source tool that works with Windows XP, Mac OS X and various flavors of Linux, as well as Vista.
Once you've installed the application, launch the TrueCrypt Volume Creation Wizard to create your encrypted partition, drive, volume or file container. Then choose whether you want to create a normal volume or a hidden one--which, in effect, creates a container within the container for extra "plausible deniability" should you be forced to reveal the password of the external volume.
After choosing the target file location, partition or drive, pick an encryption and hash algorithm for your container. TrueCrypt supports AES-256, Serpent and Twofish encryption algorithms and numerous combinations of the three. Here, you should balance the performance you'll need against the security you'll get from your choice. Fortunately, the application gives you a description, history and certification of each algorithm and even a benchmark performance run of each for your current system, if you so desire. You can choose RIPEMD-160, SHA-512 or Whirlpool for your hash algorithm; here, too, you can see a description of what each provides.
To keep your data portable, TrueCrypt can also encrypt an entire USB flash drive. But it might be more useful to create a file container on the flash drive while leaving enough room for the TrueCrypt application itself. Then, from the Tools menu, choose Traveler Disk Setup. This wizard copies the application to the device. You can also choose to have it create an autorun.ini file that will either start TrueCrypt or auto-mount your file container. You'll need administrator privileges on the machine that you wish to use the Traveler Disk.
Because the TrueCrypt volumes act as physical disk devices, you can also change the file-system type, defragment, run applications from and run utilities such as Chkdsk against your containers. The volumes are also cross-platform, meaning that you can, for example, create a container on a Linux box and open it on your Windows machine at home. If you've used TrueCrypt before, you'll appreciate the addition of read-ahead buffering for the I/O pipeline; this improves read performance, especially when using a solid-state drive. You may also notice that auto-mounting encrypted drives takes much less time.
If you're looking for a seasoned, portable and versatile physical-partition, disk or logical volume encryption tool, give TrueCrypt a test drive.
Price: Free.
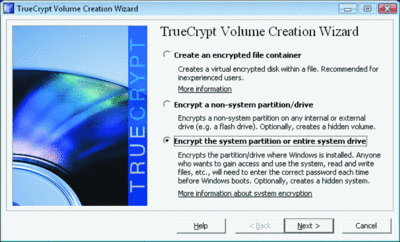
TrueCrypt 6.2 (Click the image for a larger view)
Keep An Eye On Disk Space
NetWrix Disk Space Monitor—Free Edition
netwrix.com/disk_space_monitor_freeware.html
Like other administrators, you want to know when your system's available disk space is running out well before your end-users do—and before your servers start to throw errors and lock up.
One tool that can help you keep an eye on available storage space is NetWrix Disk Space Monitor—Free Edition. Once you've installed the utility, launch the Configurator to set up your monitoring details. Here you can specify the list of servers you wish to monitor and the percentage free-space threshold at which you want to be notified. Unfortunately, you can't tailor the percentage to each server, but a general guideline for all your servers will probably be sufficient. As you add each server, you'll be prompted for credentials that the application can use to connect to the remote machines to verify the available disk space. You may want to set up a dedicated account for this purpose.
Next, set the schedule for when you want the checks to occur. I've found that timing the checks during low-usage periods, such as in the early morning after backups, is usually a good idea. The check is saved as a Scheduled Task, so you can also tweak or manually run the application via the Scheduled Task interface. Notification of low disk space is sent via e-mail, so you'll also need to specify the SMTP relay that you want to have the application send its notification messages through. (The e-mail contains a log file of the checks and indications of which servers are running low on space, all within the body of the e-mail for quick reading.) Once you click Apply, your preferences are saved and the application will run on your schedule.
You probably want to consider the product's commercial version if you need real-time instead of scheduled checks, notification of disk-space events or the ability to import server lists from a file, or if you want phone or e-mail support. The commercial version is licensed according to the number of servers you wish to manage.
Price: Free.
The opinions expressed in this column are solely those of the author and do not necessarily reflect the opinions of Microsoft. Prices were confirmed at the time of writing, and are subject to change.
Greg Steen is a technology professional, entrepreneur and enthusiast. He is always on the hunt for new tools to help make operations, QA and development easier for IT professionals.
Price: Free.
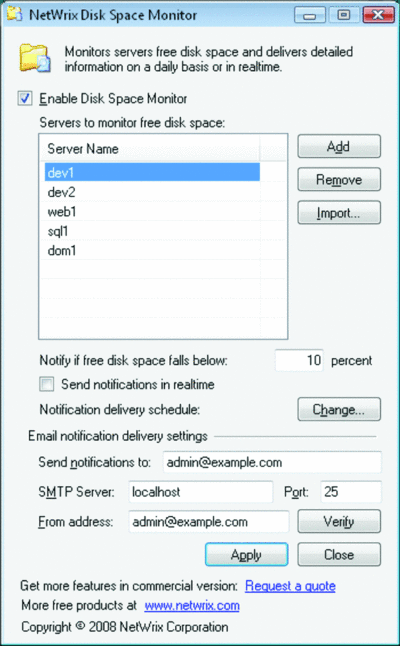
NetWrix Disk Space Monitor (Click the image for a larger view)
If you have a favorite tool or utility you would like to see featured here, please write to the author at tntools@microsoft.com.
Greg Steen is a technology professional, entrepreneur, and enthusiast. He is always on the hunt for new tools to help make operations, QA, and development easier for the IT professional.