Toolbox New Products for IT Pros
Greg Steen
The opinions expressed in this column are solely those of the author and do not necessarily reflect the opinions of Microsoft. All prices were confirmed at the time of writing, and are subject to change.
Secure Sensitive Information
Encrypt Only What You Need
Encryption is a great way to protect your sensitive information, and there are a number of utilities and tools out there to help you do so. One such tool is Microsoft's own BitLocker technology, which seamlessly encrypts an entire volume on your Windows system.
But sometimes you need to encrypt just a single file to protect your sensitive information or transport a file in a protected manner. If so, you may want to take a look at AxCrypt. AxCrypt is free, open-source file-encryption software that allows you to easily encrypt, decrypt and compress individual files on your computer.
The tool integrates with Windows Explorer, giving you right-click access for encrypting and decrypting your files. Because the file extension is registered with Windows, double-clicking the file will pop up the passphrase or key file dialog, so opening and editing your encrypted items won't slow down your day-to-day operations.
When you save your file, AxCrypt automatically re-encrypts the modifications, providing a near seamless workflow. If you don't want to use the Windows Explorer interface, the utility also has a complete command-line interface. AxCrypt supports files greater than 4GB, so you could, for example, encrypt .ZIP files of protected content as well. In addition to creating the custom extension encrypted files, AxCrypt can also wrap the encrypted file in an executable for easy repurposing and sharing of the encrypted data.
A note about names: Although AxCrypt's default is to give the encrypted file the same filename as the original (with a different extension), you can use the "Rename" functionality to protect the content; the utility will assign a completely anonymous name. When you decrypt that file, the original filename will be preserved.
To secure your data, AxCrypt uses AES encryption with 128-bit keys. It also uses iterative key wrapping as a countermeasure against brute force attacks. You can either protect your file with a passphrase or a key file. If you use a passphrase, the strength of the encryption is dependent upon the complexity of your passphrase. Key files are more secure; the downside is that you have to protect access to those key files. AxCrypt has a built-in random key file generator which wisely recommends that you keep your key file on removable media, and print out a backup rather than storing it on a fileserver (remember, you won't be able to access that encrypted data without it).
AxCrypt has an integrated "Shred and Delete" function, to ensure that the bits of an extracted file are completely wiped from your system as added protection. As a further security measure, AxCrypt does not place any keys or data into your paging file while it encrypts. And since the project is open source, you can download the source code to get a sense of AxCrypt's architecture.
AxCrypt is open source and free to use, so the next time you are looking for a file encryption tool, why not take a look?
Price: Free.
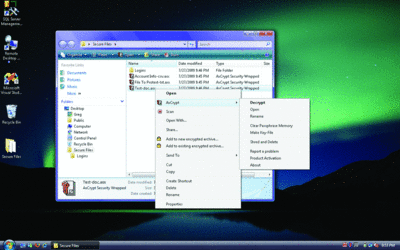
AxCrypt (Click the image for a larger view)
Remote Connection
Make the Switch with KaVoom! KVM
kavoom.biz/k/prod_overview.html
Remote Desktop is a great way to connect to your Windows machines remotely. But there are times when you are either unable to use Remote Desktop, or the version of Windows you are connecting to doesn't support it. For those occasions when you need to "be there without really being there" and can't use Remote Desktop, you might want to consider a software-based keyboard, video, mouse (KVM) switch. One such switch is KaVoom! KVM from KaVoom Software Inc.
Software KVM switches differ from hardware-based KVMs in at least two significant ways: first, they require a client to be installed on each machine; second, they need to be networked together. After installing the KaVoom! KVM on each machine you'll be connecting to and from, you will need to configure the primary (the display) and secondary (slave) machines. You can set it up so all machines are both primary and secondary, if needed.
The application runs in your taskbar. As a default, KaVoom! displays an "always-on-top" switch in the lower right of the display to provide one-click switching between configured hosts. Adding a host is easy: Simply right-click on the tray icon and select "Setup." Here, too, you can hide the switch UI if it becomes distracting.
Other configuration options include setting hot keys for switching between machines and hot keys for specific machines. You can also set friendly names for each of your connections, or reinstall the KVM software remotely if your account has permission to do so. There are no software limits on the number of machines to which you can connect.
Price: A full-featured trial of KaVoom! KVM is available; a two-computer license can be purchased for $39.95, and each additional computer costs $16.95.
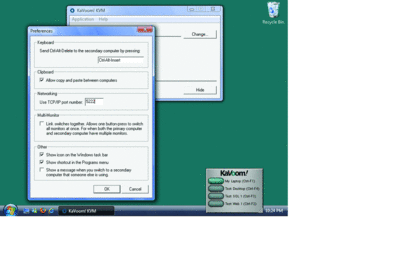
KaVoom! (Click the image for a larger view)
Book Review
Malware Forensics: Investigating and Analyzing Malicious Code
What do you do if you suspect or detect some kind of worm, botnet, rootkit or Trojan horse inside the walls of your own infrastructure? Will you be prepared to analyze it in a live setting or will you have to wait until it causes the damage it was intended to do?
One book that will get you up to speed on live analysis and malware forensics in general, for both Windows and Linux systems, is "Malware Forensics: Investigating and Analyzing Malicious Code" (Syngress, 2008) by James M. Aquilina, Eoghan Casey and Cameron H. Malin. The book alternates chapters between Windows and Linux technologies, presenting techniques and tools for Windows first and then Linux, providing a full overview of both.
The first two chapters cover malware incident response, showing how to collect and preserve volatile data (data that doesn't persist, so it must be observed and recorded either as it happens or shortly thereafter) on a live system. You'll see how to use tools such as Quser (Query User Utility), Netstat, CurrPorts and OpenPorts to help collect the information you need.
Next up is Memory Forensics, wherein the authors demonstrate how to uncover and utilize evidence with memory forensic tools for both Windows and Linux systems. Here you'll see the usage of tools such as Userdump, Process Dumper and Memfetch.
Following that is coverage of Post-Mortem Forensics. As the name implies, this post-incident information involves collecting evidence from a compromise, analyzing it, and using it to protect against future attacks. The next chapter, Legal Considerations, provides an overview of the laws in place to protect your private information—as well as the limitations of those laws. You'll also learn how to improve your chances of being able to use your collected information in court by using techniques such as hashing.
The next two chapters highlight File Identification and Profiling for Windows and Linux systems, demonstrating the anatomy of an executable file, different file signatures, file obfuscation techniques employed by malware, and how to extract embedded artifacts within those files.
The last pair of chapters expands the file coverage into Analysis of a Suspect Program, giving you guidelines for examination of a suspect program with passive and active network monitoring techniques and tools such as Process Explorer, pstree and strace.
If you're looking for a malware book based on real-world experience from real-world security experts, give this one a try. Its in-depth coverage will increase your knowledge, making you a better investigator and incident responder.
Price: $69.95 (list).

Extension Discovery
Find that File
The time it takes to discover an unknown file extension in Windows can be a real frustration for the IT pro. But it does not have to be. One quick and easy extension to your machine to help speed the process of identification is FILExt Direct.
The free utility works by changing the default action for unknown file types. When you double-click to open them, the query goes to the FILExt.com Website to determine the file type and associated program to open it with.
FILExt.com is an online repository of more than 25,000 file extensions and associated details. The information includes data like the program or extension function used to open the file type, notes about that file type describing its usage and what to do with it, MIME and file classification information, and links to useful information about those files. The FILExt.com repository is user supported, so you can also submit your own extensions as well.
Price: Free.
filext.com (Click the image for a larger view)
If you have a favorite tool or utility you would like to see featured here, please write to the author at tntools@microsoft.com.
Greg Steen is a technology professional, entrepreneur, and enthusiast. He is always on the hunt for new tools to help make operations, QA, and development easier for the IT professional.