Getting Started with the Offline Assessment for SharePoint Server - Unified
The SharePoint assessment provides you with an assessment of your SharePoint Server farm to diagnose potential issues with the following SharePoint environments:
- SharePoint hosted on-premises
- SharePoint hosted on Azure Infrastructure as a Service (IaaS)
The service supports a single SharePoint 2013, SharePoint 2016 or SharePoint 2019 farm, with up to 30 servers (including SQL Servers) and up to 50,000 webs running on Windows Server 2012 R2 or later.
The recommendations cover areas such as change control, monitoring, disaster recovery, service level agreements, configuration items and the proper function of the major components that make up SharePoint, such as SharePoint configuration settings, dependencies on SQL and IIS, and so on.
This assessment is designed to provide you with specific actionable guidance grouped in Focus Areas to mitigate risks to your SharePoint Server farm and your organization.
SharePoint Assessment Focus Points
The SharePoint Assessment focuses on several key pillars, including:
- SharePoint Configuration
- SharePoint Topology
- SharePoint Health Analyzer
- SharePoint Data Integrity
- Event Log Analysis
- Operational Excellence
How to prepare for your Offline Assessment for SharePoint Server
A Tools Machine is required to connect to each of the servers in your SharePoint environment. The Tools Machine retrieves information through communicating over Remote Procedure Call (RPC), Server Message Block (SMB), Lightweight Directory Access Protocol (LDAP) and the Distributed Component Object Model (DCOM). Once the data is collected and the operational interview is completed, the Offline Assessment Tool will analyze the data locally.
The prerequisites below are required for a successful data collection.
Prerequisites
1. Hardware and Software
Server-class or high-end workstation computer equipped with the following:
Minimum single 2Ghz processor — Recommended dual-core/multi-core 2Ghz or higher processors.
Minimum 4 GB RAM—Recommended 12 GB RAM.
Minimum 5GB of free disk space.
High End Workstation: Windows 11, Windows 10 Server: Windows Server 2022, Windows Server 2019, Windows Server 2016
Can be a 32-bit or 64-bit operating system.
At least a 1024x768 screen resolution (higher preferred).
Microsoft 365 Apps for enterprise (Word, Excel and PowerPoint) for report creation.
Must be a member of the same domain as the SharePoint farm that is being analyzed.
Microsoft® .NET Framework 4.8 — https://dotnet.microsoft.com/en-us/download/dotnet-framework/net48
NOTE: If the SharePoint Server has a higher version of .NET installed than 4.8 than the version installed on the Tools Machine must be equal to or higher than installed on the Target SharePoint Server.
Windows PowerShell 4.0 or higher
- PowerShell 4.0 is part of the Windows Management Framework 4.0
- Windows PowerShell System Requirements
- The execution policy for PowerShell should be set to RemoteSigned on both the Tools Machine and all the servers (SharePoint and SQL)
- The execution policy settings can be verified using “Get-ExecutionPolicy –list” in a PowerShell command window
Networked “Documents” or redirected “Documents” folders are not supported. A Local “Documents” folder on the data collection machine is required.
IIS Management Tools (IIS 7 Administration components)
Firewall exception for Remote Administration (RPC) – Dynamic Port Ranges
2. Accounts Rights
A domain account with the following:
- Member of the local Administrators group on all servers in the SharePoint environment (SharePoint and SQL servers)
- Full Control on all Service Applications
- Member of the “SysAdmin” group on SQL instances hosting SharePoint databases
- Unrestricted network access from the Tools Machine to all servers (SharePoint and SQL servers)
- Member of the SharePoint Farm Administrators group
Ability to run PowerShell scripts on the machine running the Offline Assessment Tool. The Windows PowerShell execution policy must be set to RemoteSigned or a policy that provides an equivalent ability to run local scripts. For more information, see about_Execution_Policies.
Warning
Do not use the “Run As” feature to start the assessment software as the discovery process and collectors might fail. The account starting the Offline Assessment Tool must log on to the local machine.
3. Download the assessment software
The software for the assessment (Offline Assessment Tool) can be downloaded from the Services Hub. Work with your Services Admin, CSAM, or Support Account Coordinator for access to the Services Hub.
Note
As this is an offline assessment no Azure Subscription and Log Analytics Workspace is required.
4. Network and Remote Access
To ensure a complete data collection we recommend to temporarily allow unrestricted network access from the Tools Machine to all servers (SharePoint and SQL) during the assessment. This means access through any firewalls and router ACLs that might be limiting traffic to any of the servers. This includes remote access to:
- DCOM
- Remote Registry service
- Windows Management Instrumentation (WMI) services
- Default administrative shares (C$, D$, IPC$).
We understand that unrestricted network access may raise security concerns, these requirements are needed as each environment has been configured differently (e.g. port ranges might have been changed for specific protocols. Following instructions below you can attempt to open the firewall for specific ports and protocols for your environment.
Note
Microsoft does not provide any support or assistance when using the steps below.
Ports and Protocol access requirements:
Ensure that the Tools Machine has the following:
- Complete TCP/UDP access, including RPC access to all servers (SharePoint and SQL).
- Access over ports 135 and 139 or 445.
- Windows Remote Management (WinRM) uses Ports 5985 for HTTP. Communication between the Tools Machine and the SharePoint server that is targeted (see section 6 for the target server) for the data collection on port 5985 must be enabled as PowerShell commands will be executed remotely via this port.
- The ports configured for the SQL instance(s).
Configure the server firewall to have Remote Event Log Management enabled.
The Offline Assessment Tool might not be unable to collect event log information from a Windows Server if the Remote Event Log Management has not been enabled. When Remote Management is enabled, the following services must be started on all servers (SharePoint and SQL):
- WMI
- Remote Registry service
- Server service
- Workstation service
- File and Printer Sharing service
- Automatic Updates service
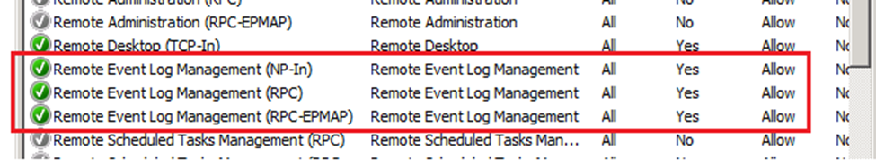
Connectivity Testing
You can perform the below tests to verify if you are able to connect to all servers in the SharePoint farm (SharePoint and SQL).
- Event Log: Use eventvwr.msc to verify if you are able to connect to the event viewers on all the servers. If the remote connection is unsuccessful you may need to enable the Windows built-in firewall to allow “Remote Event Log Management”.
- Registry: Use regedit.exe to test remote registry connectivity to all servers (File > Connect Network Registry).
- File: Connect to the C$ and Admin$ shares on all servers to verify file access.
4. Additional requirements for Windows Server 2016 or later:
A. Log into the chosen data collection machine to identify its current IP address using IPConfig.exe from the command prompt. An example output is as follows:
C:\>ipconfig
Windows IP Configuration
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::X:X:X:X%13
IPv4 Address. . . . . . . . . . . : X.X.X.X
Subnet Mask . . . . . . . . . . . : X.X.X.X
Default Gateway . . . . . . . . . : X.X.X.X
- Make a note of the IPv4 address of your machine. The final step in the configuration will use this address to ensure only the data collection machine can communicate with the Windows Update Agent on the SharePoint server farm.
B. Create, configure, and link a group policy object to the SharePoint Servers OU in the domain of the servers.
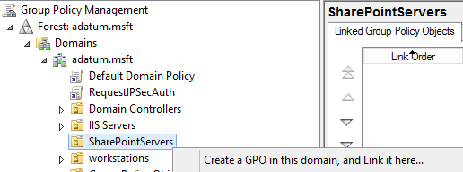
Create a new GPO
Make sure the GPO applies to the SharePoint Servers organizational unit.
Note: If other servers outside the scope are present in the OU, then security group filtering can be used to restrict the application of group policy to only the SharePoint Servers.
- Within the GPO open: Computer Configuration\Policies\Windows Settings\Security Settings\Windows Firewall with Advanced Security\ Windows Firewall with Advanced Security.
- Right-click Inbound Rules and then click New Rule.
- The rule you create will be merged with the rules that already enabled on the SharePoint Servers’ through local policy and/or other group policy objects that have inbound rules defined.
- On the New Inbound Rule Wizard, on the Rule Type page click Custom, and then click Next.
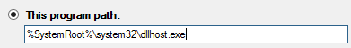
- On the Program tab, choose This Program Path and insert the following path without the quotes:
- “%SystemRoot%\system32\dllhost.exe” as shown in the below graphic and choose next.
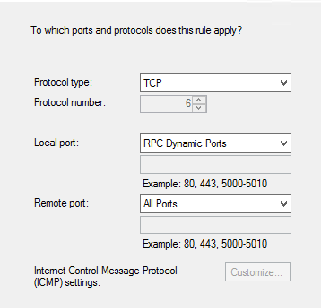
On the Protocol and Ports Page Select “TCP” for the Protocol Type and “RPC Dynamic Ports” for Local Ports and select next as shown in the following graphic.
- On the scope page, select These IP Addresses under “which remote IP addresses does this rule apply to”, then click Add. Insert the IP address of the data collection machine identified in the first step. Click OK, then Next on the scope page.
- Choose Allow the Connection on the Action page and select Next.
- Leave the default profiles checked on the Profile page, then on the Name page, give the rule a name that describes what it allows, similar to “Allow Inbound to WUA from x.x.x.x” and finish the rule creation wizard to commit the rule to the firewall policy.
- Once the rule applies, it can be confirmed as active through Windows Firewall with Advanced Security MMC (WF.MSC) monitoring navigation node or by interrogating the output of the following PowerShell command “Get-NetFirewallRule -Enabled true -policystore ActiveStore” and confirming the created rule shows up.
5. Remote PowerShell and CredSSP Configuration (Tools Machine) On the Tools Machine, launch PowerShell Prompt with the option “Run as Administrator”. And run the following commands (see important note below before running the below commands)
Enable-WSManCredSSP -Role client -DelegateComputer <SharePointServer FQDN>
(example) Enable-WSManCredSSP -Role client -DelegateComputer SPAPP01.contoso.local
Notes:
- The “SharePointServer FQDN” in the above command is the “Target Server” to which the “Tools Machine” connects to when collecting data. You must use the FQDN for the SharePoint server (e.g. SPAPP01.contoso.local). The target server is generally the SharePoint service hosting the Central Administration.
- The WinRM service needs to be running for this command to succeed.
6. Remote PowerShell and CredSSP Configuration (Target Server)
On the Target Server (see the first page and the fourth page of this document to learn about Target Server), launch PowerShell Prompt with the option “Run as Administrator”. And run the following commands (see important note below before running the following commands)
Enable-WSManCredSSP -Role server
Notes:
- SharePoint 2013, SharePoint 2016 and SharePoint 2019 farms supported only at this time. The Offline Assessment for SharePoint Server does not support SharePoint Server 2010 or earlier.
- Offline Assessment for SharePoint Server supports SharePoint farms backed by SQL servers running SQL - Server 2014 or later. Earlier versions of SQL Server are not supported.
7. Remote PowerShell and CredSSP Configuration testing
Most of the SharePoint information is gathered by executing PowerShell scripts remotely from the Tools Machine. It is particularly important for the CredSSP delegation to be configured correctly so that the PowerShell scripts can be executed remotely on the Target Server. To test the configuration run the below commands from the Tools Machine.
Executing the snippet below should output the list of all SharePoint Content databases of your SharePoint farm.
$farm = Get-Credential
$s = New-PSSession -ComputerName [FQDN of Target Server] -Authentication CredSSP -Credential $farm
Invoke-Command -Session $s -ScriptBlock { Add-PSSnapin Microsoft.SharePoint.PowerShell -ea 0 }
Invoke-Command -Session $s -ScriptBlock { Get-SPFarm }
Invoke-Command -Session $s -ScriptBlock { Get-SPContentDatabase }
Get-PSSession | Remove-PSSession
Note
- The “FQDN of Target Server” is the SharePoint server on which the CredSSP is enabled (see the first page and the fourth page of this document to learn about Target Server).
- If the above test fails, DO NOT proceed with the assessment and reach out to your CSAM for further assistance.
Data Collection Methods
Appendix: Data Collection Methods
Offline Assessment for SharePoint Server uses multiple data collection methods to collect information. This section describes the methods used to collect data from a SharePoint environment. No VB scripts are used to collect data. Data collection uses workflows and collectors. The collectors are:
- Registry Collectors
- SharePoint PowerShell Scripts
- Event Log Collector
- SQL Queries
- IIS information
- File Data Collector
- WMI
Registry Collectors:
Registry keys and values are read from the Tools Machine and all SharePoint Servers in the farm (SharePoint and SQL). They include items such as:
- SQL Alias information from HKLM\SOFTWARE\Microsoft\MSSQLServer\Client\ConnectTo
This allows the assessment to determine if the SharePoint servers are using SQL alias to connect to the SQL server that is hosting the SharePoint databases.
Operating System information from HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion
This allows to determine Operation System information such as Windows 10, Windows Server 2012 R2 or later.
SharePoint PowerShell Scripts:
Most of the SharePoint data is gathered via running the SharePoint PowerShell scripts. For example, the information pertaining to Large list views, Alternate Access mappings, SharePoint services, ULS information, SharePoint Lists information, SharePoint Search, Timer Jobs etc., are all gathered using SharePoint PowerShell scripts.
These scripts are executed remotely from the Tools Machine by connecting to the Target Machine.
Event Log Collector:
Collects event logs from all SharePoint Servers in the farm (SharePoint and SQL). The Offline Assessment Tool collects the last 7 days of Warnings and Errors from the Application and System logs.
SQL Queries:
Some of the information pertaining to the SQL databases that are hosted by the SharePoint SQL instance are gathered via SQL scripts. For example, the information related to the SQL data and log files (for example, the size and next growth size), SQL instance properties (for example, if using Integrated Security, if the instance is clustered), Index Fragmentation, Statistics information etc., are all gathered via SQL Scripts.
IIS Information:
The details of the IIS web sites and App Pool configurations are gathered using .NET code and workflows.
File Data Collector:
Enumerates files in a folder on a remote machine, and optionally retrieves those files. For example, web.config files, IIS Log files, App Host config files etc.,
Windows Management Instrumentation (WMI):
WMI is used to collect various information such as:
WIN32_Volume: Collects information on Volume Settings for each server in the SharePoint environment. The information is used for instance to determine the system volume and drive letter which allows the Offline Assessment Tool to collect information on files located on the system drive.
Win32_Process: Collect information on the processes running on each server in the SharePoint environment. The information provides insight in processes that consume a large amount of threads, memory or have a large page file usage.
Win32_LogicalDisk: Used to collect information on the logical disks. We use the information to determine the amount of free space on the disk where the database or log files are located.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for