Run Transact-SQL statements using secure enclaves
Applies to:
SQL Server 2019 (15.x) and later - Windows only
Azure SQL Database
Always Encrypted with secure enclaves allows some Transact-SQL (T-SQL) statements to perform confidential computations on encrypted database columns in a server-side secure enclave.
Statements using secure enclaves
The following types of T-SQL statement utilize secure enclaves.
DDL statements using secure enclaves
The following types of Data Definition Language (DDL) statements require secure enclaves.
- ALTER TABLE column_definition (Transact-SQL) statements that trigger in-place cryptographic operations using enclave-enabled keys. For more information, see Configure column encryption in-place using Always Encrypted with secure enclaves.
- CREATE INDEX (Transact-SQL) and ALTER INDEX (Transact-SQL) statements that create or alter indexes on enclave-enabled columns using randomized encryption. For more information, see Create and use indexes on columns using Always Encrypted with secure enclaves.
DML statements using secure enclaves
The following Data Manipulation Language (DML) statements or queries against enclave-enabled columns using randomized encryption require secure enclaves:
- Queries that use one or more of the following Transact-SQL operators supported inside secure enclaves:
- Comparison Operators
- BETWEEN (Transact-SQL)
- IN (Transact-SQL)
- LIKE (Transact-SQL)
- DISTINCT
- Joins - SQL Server 2019 (15.x) supports only nested loop joins. SQL Server 2022 (16.x) and Azure SQL Database supports nested loop, hash, and merge joins
- SELECT - ORDER BY Clause (Transact-SQL). Supported in SQL Server 2022 (16.x) and Azure SQL Database. Not supported in SQL Server 2019 (15.x)
- SELECT - GROUP BY Clause (Transact-SQL). Supported in SQL Server 2022 (16.x) and Azure SQL Database. Not supported in SQL Server 2019 (15.x)
- Queries that insert, update, or delete rows, which in turn triggers inserting and/or removing an index key to/from an index on an enclave-enabled column. For more information, see Create and use indexes on columns using Always Encrypted with secure enclaves
Note
Operations on indexes and confidential DML queries using enclaves are only supported on enclave-enabled columns that use randomized encryption. Deterministic encryption is not supported.
The compatibility level of the database should be set to SQL Server 2022 (160) or higher.
In Azure SQL Database and in SQL Server 2022 (16.x), confidential queries using enclaves on a character string column (char, nchar) require the column uses a binary-code point (_BIN2) collation or a UTF-8 collation. In SQL Server 2019 (15.x), a_BIN2 collation is required.
DBCC commands using secure enclaves
DBCC (Transact-SQL) administrative commands that involve checking the integrity of indexes might also require secure enclaves if the database contains indexes on enclave-enabled columns using randomized encryption. For example, DBCC CHECKDB (Transact-SQL) and DBCC CHECKTABLE (Transact-SQL).
Prerequisites for running statements using secure enclaves
Your environment needs to meet the following requirements to support executing statements that use a secure enclave.
Your SQL Server instance or your database server in Azure SQL Database must be correctly configured to support enclaves and attestation, if applicable/required. For more information, see Set up the secure enclave and attestation.
When you're connecting to your database from an application or a tool (such as SQL Server Management Studio), make sure to:
Use a client driver version or a tool version that supports Always Encrypted with secure enclaves.
- See Develop applications using Always Encrypted with secure enclaves for information about client drivers supporting Always Encrypted with secure enclaves.
- See the following sections for information about tools supporting Always Encrypted with secure enclaves.
Enable Always Encrypted for the database connection.
Specify an attestation protocol, which determines whether your application or tool must attest the enclave before submitting enclave queries, and which attestation service it should use. Most tools and drivers support the following attestation protocols:
- Microsoft Azure Attestation - enforces attestation using Microsoft Azure Attestation.
- Host Guardian Service - enforces attestation using Host Guardian Service.
- None - allows using enclaves without attestation.
The below table specifies attestation protocols valid for particular SQL products and enclave technologies:
Product Enclave technology Supported attestation protocols SQL Server 2019 (15.x) and later VBS enclaves Host Guardian Service, None Azure SQL Database SGX enclaves (in DC-series databases) Microsoft Azure Attestation Azure SQL Database VBS enclaves None
Specify an attestation URL that is valid for your environment if you're using attestation.
- If you're using SQL Server and Host Guardian Service (HGS), see Determine and share the HGS attestation URL.
- If you're using Azure SQL Database with Intel SGX enclaves and Microsoft Azure Attestation, see Determine the attestation URL for your attestation policy.
Prerequisites for running T-SQL statements using enclaves in SSMS
Download the latest version of SQL Server Management Studio (SSMS).
Make sure you run your statements from a query window that uses a connection that has Always Encrypted and attestation parameters correctly configured.
In the Connect to Server dialog, specify your server name, select an authentication method, and specify your credentials.
Select Options >> and select the Connection Properties tab. Specify your database name.
Select the Always Encrypted tab.
Select Enable Always Encrypted (column encryption).
Select Enable secure enclaves.
Set Protocol to:
- Host Guardian Service if you're using SQL Server.
- Microsoft Azure Attestation if you're using Azure SQL Database with Intel SGX enclaves.
- None if you're using Azure SQL Database with VBS enclaves.
Specify your enclave attestation URL. Not applicable when the Protocol is set to None. For example,
https://hgs.bastion.local/Attestationorhttps://contososqlattestation.uks.attest.azure.net/attest/SgxEnclave.
Select Connect.
If you're prompted to enable Parameterization for Always Encrypted queries, select Enable.
For more information, see Enabling and disabling Always Encrypted for a database connection.
Prerequisites for running T-SQL statements using enclaves in Azure Data Studio
The minimum recommended version 1.23 or higher is recommended. Make sure you run your statements from a query window that uses a connection that has Always Encrypted enabled and both the correct attestation protocol and the attestation URL configured.
In the Connection dialog, select Advanced....
To enable Always Encrypted for the connection, set the Always Encrypted field to Enabled.
To enable secure enclaves, set the Secure enclaves field to Enabled.
Specify the attestation protocol and the attestation URL.
- If you're using SQL Server set Attestation Protocol to Host Guardian Service and enter your Host Guardian Service attestation URL in the Enclave Attestation URL field.
- If you're using a DC-series database with Intel SGX in Azure SQL Database, set Attestation Protocol to Azure Attestation and enter the attestation URL, referencing your policy in Microsoft Azure Attestation in the Enclave Attestation URL field.
- If you're using a database with VBS enclaves enabled in Azure SQL Database, set Attestation Protocol to None.
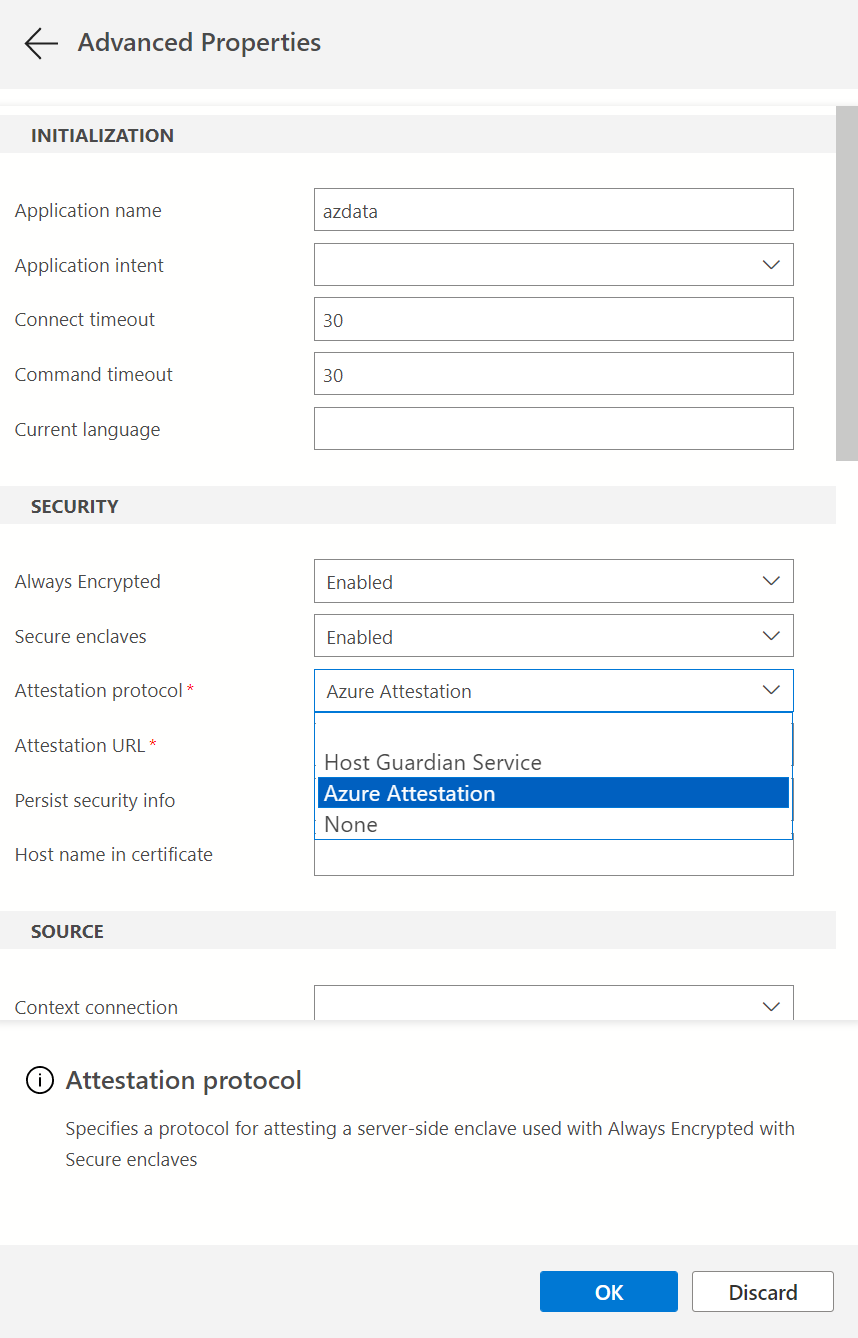
Select OK to close Advanced Properties.
For more information, see Enabling and disabling Always Encrypted for a database connection.
If you plan to run parameterized DML queries, you also need to enable Parameterization for Always Encrypted.
Examples
This section includes examples of DML queries using enclaves.
The examples use the below schema.
CREATE SCHEMA [HR];
GO
CREATE TABLE [HR].[Jobs](
[JobID] [int] IDENTITY(1,1) PRIMARY KEY,
[JobTitle] [nvarchar](50) NOT NULL,
[MinSalary] [money] ENCRYPTED WITH (COLUMN_ENCRYPTION_KEY = [CEK1], ENCRYPTION_TYPE = Randomized, ALGORITHM = 'AEAD_AES_256_CBC_HMAC_SHA_256') NOT NULL,
[MaxSalary] [money] ENCRYPTED WITH (COLUMN_ENCRYPTION_KEY = [CEK1], ENCRYPTION_TYPE = Randomized, ALGORITHM = 'AEAD_AES_256_CBC_HMAC_SHA_256') NOT NULL
);
GO
CREATE TABLE [HR].[Employees](
[EmployeeID] [int] IDENTITY(1,1) PRIMARY KEY,
[SSN] [char](11) ENCRYPTED WITH (COLUMN_ENCRYPTION_KEY = [CEK1], ENCRYPTION_TYPE = Randomized, ALGORITHM = 'AEAD_AES_256_CBC_HMAC_SHA_256') NOT NULL,
[FirstName] [nvarchar](50) NOT NULL,
[LastName] [nvarchar](50) NOT NULL,
[Salary] [money] ENCRYPTED WITH (COLUMN_ENCRYPTION_KEY = [CEK1], ENCRYPTION_TYPE = Randomized, ALGORITHM = 'AEAD_AES_256_CBC_HMAC_SHA_256') NOT NULL,
[JobID] [int] NULL,
FOREIGN KEY (JobID) REFERENCES [HR].[Jobs] (JobID)
);
GO
Exact match search
The below query performs an exact match search on the encrypted SSN string column.
DECLARE @SSN char(11) = '795-73-9838';
SELECT * FROM [HR].[Employees] WHERE [SSN] = @SSN;
GO
Pattern matching search
The below query performs a pattern matching search on the encrypted SSN string column, searching for employees with the specified last for digits of a social security number.
DECLARE @SSN char(11) = '795-73-9838';
SELECT * FROM [HR].[Employees] WHERE [SSN] = @SSN;
GO
Range comparison
The below query performs a range comparison on the encrypted Salary column, searching for employees with salaries within the specified range.
DECLARE @MinSalary money = 40000;
DECLARE @MaxSalary money = 45000;
SELECT * FROM [HR].[Employees] WHERE [Salary] > @MinSalary AND [Salary] < @MaxSalary;
GO
Joins
The below query performs a join between Employees and Jobs tables using the encrypted Salary column. The query retrieves employees with salaries outside of a salary range for employee's job.
SELECT * FROM [HR].[Employees] e
JOIN [HR].[Jobs] j
ON e.[JobID] = j.[JobID] AND e.[Salary] > j.[MaxSalary] OR e.[Salary] < j.[MinSalary];
GO
Sorting
The below query sorts employee records based on the encrypted Salary column, retrieving 10 employees with the highest salaries.
Note
Sorting encrypted columns is supported in SQL Server 2022 (16.x) and Azure SQL Database, but not in SQL Server 2019 (15.x).
SELECT TOP(10) * FROM [HR].[Employees]
ORDER BY [Salary] DESC;
GO
Next steps
See also
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for