How to set up certificate-based authentication across forests without trust for a web server
This article describes how to set up a web server to use smart cards for cross-forest certificate-based authentication when the user forests and the resource forest do not trust one another.
Applies to: Windows Server 2016
Original KB number: 4509680
Environment configuration
Consider an environment that uses the following configuration:
- A user forest that is named
Contoso.com. - A resource forest that is named
Fabrikam.com. The forest hasTailspintoys.comadded as an alternate User Principal Name (UPN). - There is no trust between the two forests.
- User smart cards use certificates that have Subject Alternative Name (SAN) entries of the format
user@tailspintoys.com. - An IIS web server that is configured for Active Directory Certificate Based Authentication.
Configure Active Directory and the web server as described in the following procedures.
Configure Active Directory
To configure the resource forest to authenticate smart cards, follow these steps:
Make sure that a Kerberos Authentication Certificate that has a KDC Authentication extended key usage (EKU) has been issued to the domain controllers.
Make sure that the Issuing CA certificate of the user's certificate is installed in the Enterprise NTAUTH store.
To publish the Issuing CA certificate in the domain, run the following command at a command prompt:
certutil -dspublish -f <filename> NTAUTHCAIn this command, <filename> represents the name of the CA certificate file, which has a .cer extension.
Users must have accounts that use the alternate UPN of the resource forest.

To configure the user forest, follow these steps:
Make sure that you have Smart Card Logon and Client Authentication EKU defined in the certificate.
Make sure that the SAN of the certificate uses the UPN of the user.

Make sure that you install the Issuing CA Certificate of the user certificate in the Enterprise NTAUTH store.
Note
If you want to set up delegation on the front end server or want to skip using the UPN in the SAN attribute of the certificate (AltSecID route), see the More information section.
Configure the web server
To configure the IIS Web server in the resource forest, follow these steps:
Install the IIS Web server role, and select the Client Certificate Mapping Authentication Security feature.

On the IIS Web server, enable Active Directory Client Certificate Authentication.
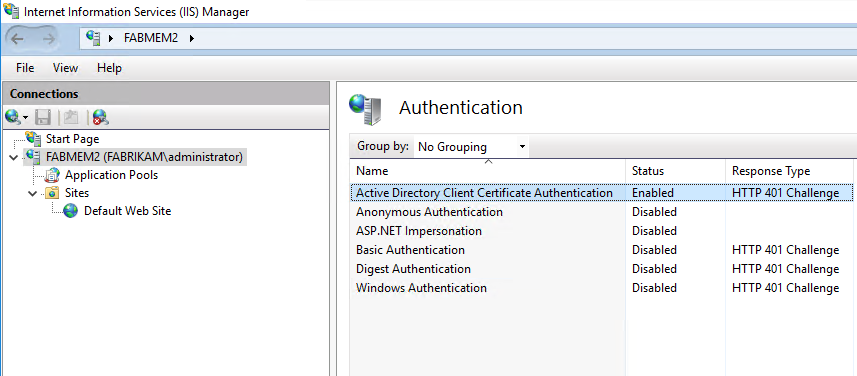
On your website, configure SSL Settings to Require SSL and then under Client certificates, select Require.
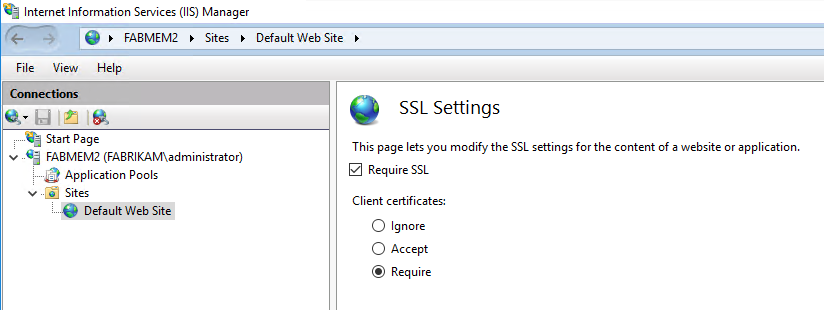
Make sure that no other authentication type is enabled on the website. We don't recommend enabling Certificate Based Authentication with any other authentication type because the DS Mapper service, which is responsible for mapping the user's presented certificate to the user account in Active Directory, is designed to only work with the Active Directory Client Certificate Authentication type. If you enable Anonymous Authentication, you may experience unexpected outcomes.

More information
If you want to set up delegation on this resource web server to query a backend server, such as a database server or a CA, you may also configure constrained delegation by using a custom service account. Additionally, you must set up the web server for constrained delegation (S4U2Self) or protocol transition. For more information, see How to configure Kerberos Constrained Delegation for Web Enrollment proxy pages.
If you want to skip the UPN in the SAN attribute of the user smart card certificate, you have to either explicitly map by using AltSecID attributes, or use name hints.
Note
We do not recommend this approach to configuring smart card certificates.
If you publish the SAN attribute as the intended UPN in the user's certificate, you should not enable AltSecID.
To check the NTAuth store on the web server, open a Command Prompt window and run the following command:
Certutil -viewstore -enterprise NTAUTH
References
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for