Conditional access
Applies to:
Azure SQL Database
Azure SQL Managed Instance
Azure Synapse Analytics
This article explains how to configure a conditional access policy for Azure SQL Database, Azure SQL Managed Instance, and Azure Synapse Analytics in a tenant.
Microsoft Entra Conditional Access enables organizations to create policy decisions at the tenant level for access to resources. For example, this article uses a conditional access policy to require multifactor authentication for user access to any Azure SQL or Azure Synapse Analytics resources in a tenant.
Prerequisites
- Full conditional access requires, at minimum, a P1 Microsoft Entra ID tenant in the same subscription as your database or instance. Only limited multifactor authentication is available with a free Microsoft Entra ID tenant - conditional access is not supported.
- You must configure Azure SQL Database, Azure SQL Managed Instance, or a dedicated SQL pool in Azure Synapse to support Microsoft Entra authentication. For specific steps, see Configure and manage Microsoft Entra authentication.
Note
Conditional access policies only apply to users, and not to programmatic connections, such as service principals and managed identities.
Configure conditional access
You can configure a conditional access policy by using the Azure portal.
Note
When configuring conditional access for Azure SQL Managed Instance, or Azure Synapse Analytics, the cloud app target resource is Azure SQL Database, which is the Microsoft application automatically created in any Microsoft Entra tenant with Azure SQL or Azure Synapse Analytics resources.
To configure your conditional access policy, follow these steps:
Sign into the Azure portal, search for
Enterprise Applicationsand choose Enterprise Applications: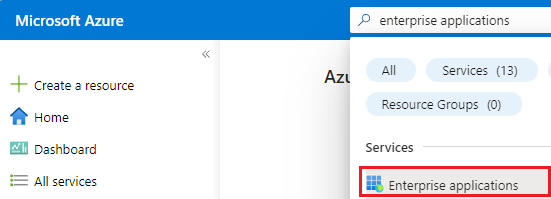
Select All applications under Manage on the Enterprise applications page, update the existing filter to
Application type == Microsoft Applicationsand then search for Azure SQL Database - even if you're configuring a policy for Azure SQL Managed Instance or Azure Synapse Analytics: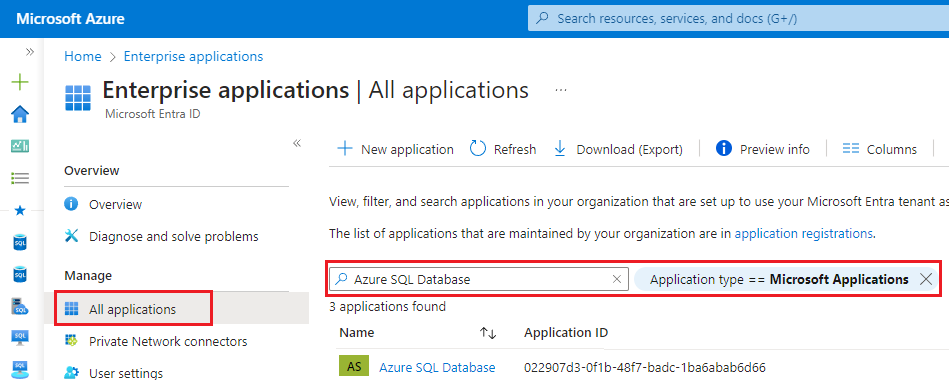
The first party application Azure SQL Database is registered in a tenant when the first Azure SQL or Azure Synapse Analytics instance is created. If you don't see Azure SQL Database, check that one of those resources is deployed in your tenant.
Select the Azure SQL Database application to navigate to the Overview page for your Azure SQL Database Enterprise Application.
Select Conditional Access under Security to open the Conditional Access page. Select + New policy to open the New Conditional Access policy page:
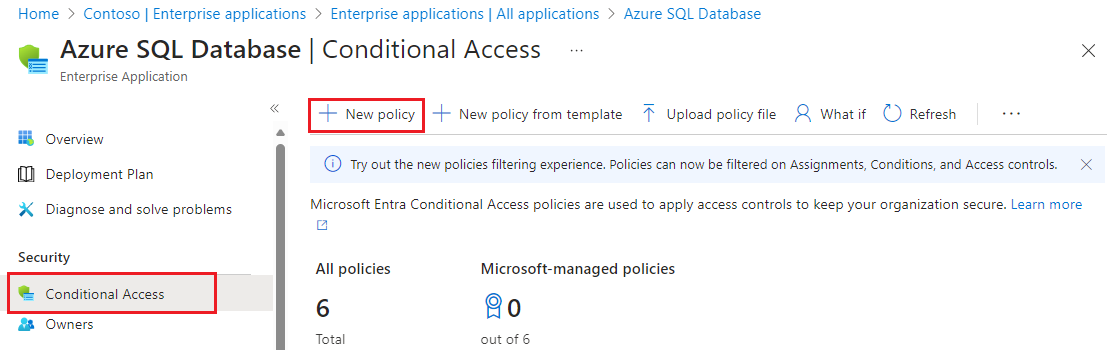
On the New Conditional Access policy page, select 1 app included under Target resources to validate that Azure SQL Database is the included application.
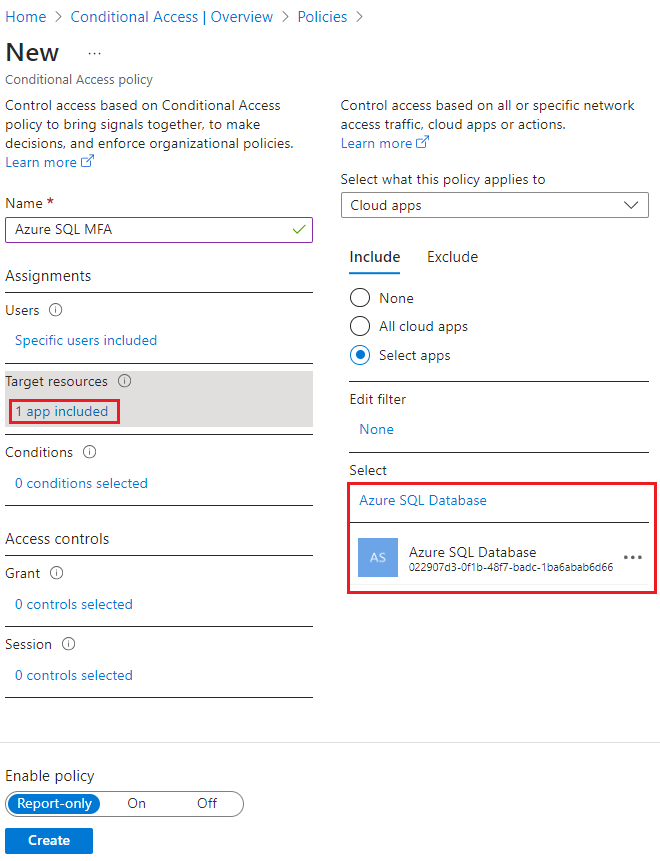
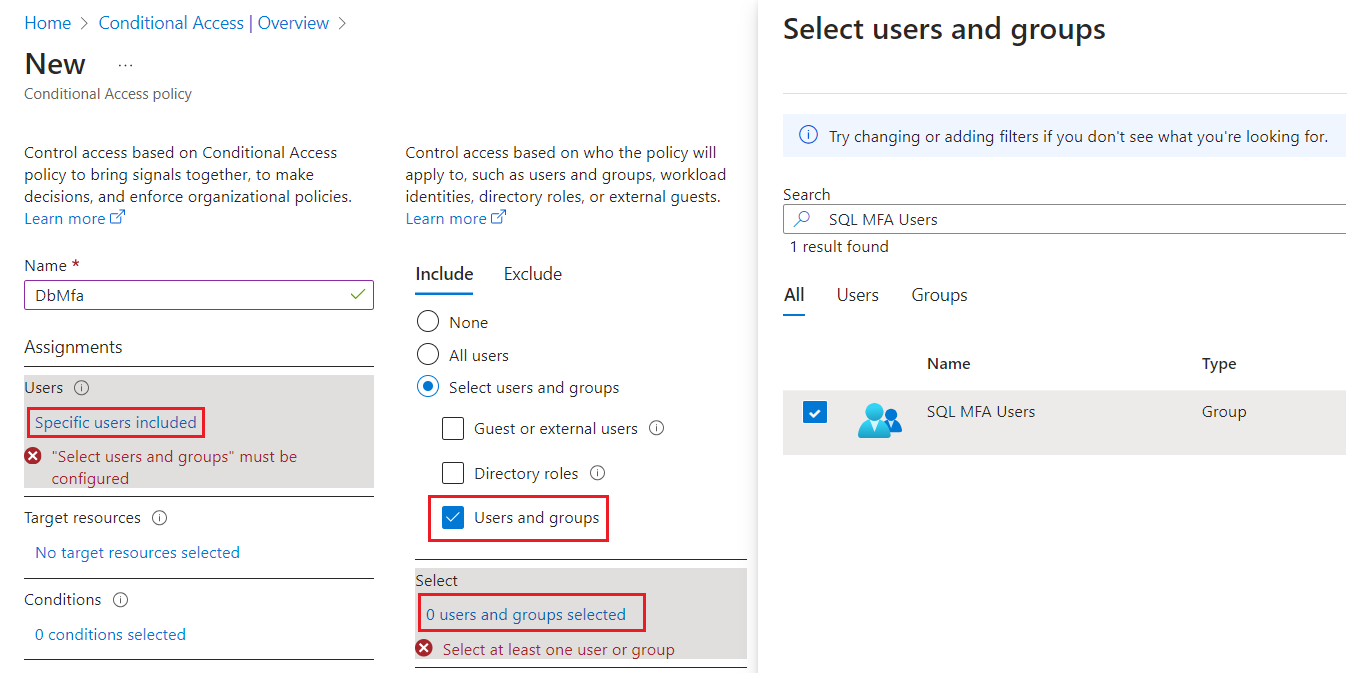
Under Assignments, select Specific users included, and then check Select users and groups under Include. Select 0 users and groups selected to open the Select users and groups page and search for the user or group you want to add. Check the box next to the group or user you want to choose, and then use Select to apply your settings and close the window.
Under Access controls, select 0 controls selected to open the Grant page. Check Grant access and then choose the policy you want to apply, such as Require multifactor authentication. Use Select to apply your access settings.
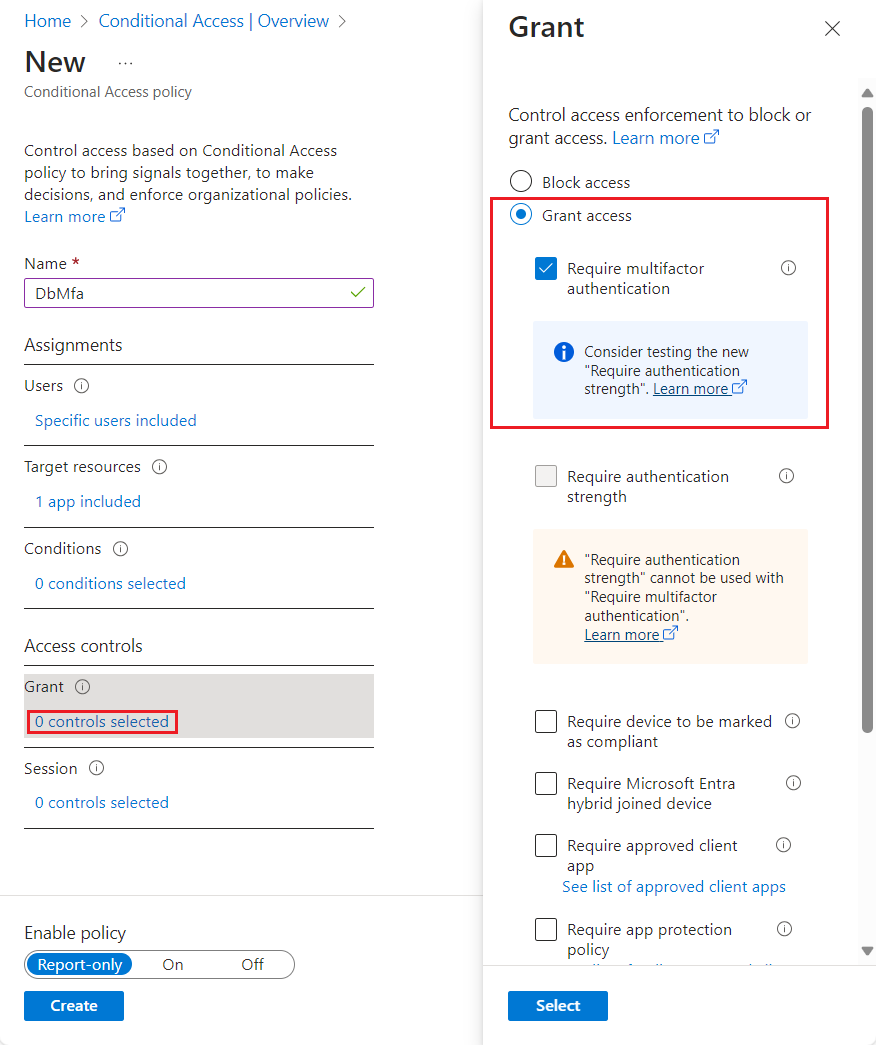
Select Create to save and apply your policy to your resource.
Once you're done, you can view your new conditional access policy on the Conditional Access page for your Azure SQL Database Enterprise Application.
Related content
For a tutorial, see Secure Azure SQL Database.
Atsiliepimai
Jau greitai: 2024 m. palaipsniui atsisakysime „GitHub“ problemų, kaip turiniui taikomo atsiliepimų mechanizmo, ir pakeisime jį nauja atsiliepimų sistema. Daugiau informacijos žr. https://aka.ms/ContentUserFeedback.
Pateikti ir peržiūrėti atsiliepimą, skirtą