Create or edit an activity log, service health, or resource health alert rule
This article shows you how to create or edit an activity log, service health, or resource health alert rule. To learn more about alerts, see the alerts overview.
You create an alert rule by combining the resources to be monitored, the monitoring data from the resource, and the conditions that you want to trigger the alert. You can then define action groups and alert processing rules to determine what happens when an alert is triggered.
Alerts triggered by these alert rules contain a payload that uses the common alert schema.
Accessing the alert rule wizard in the Azure portal
There are several ways that you can create or edit a new alert rule.
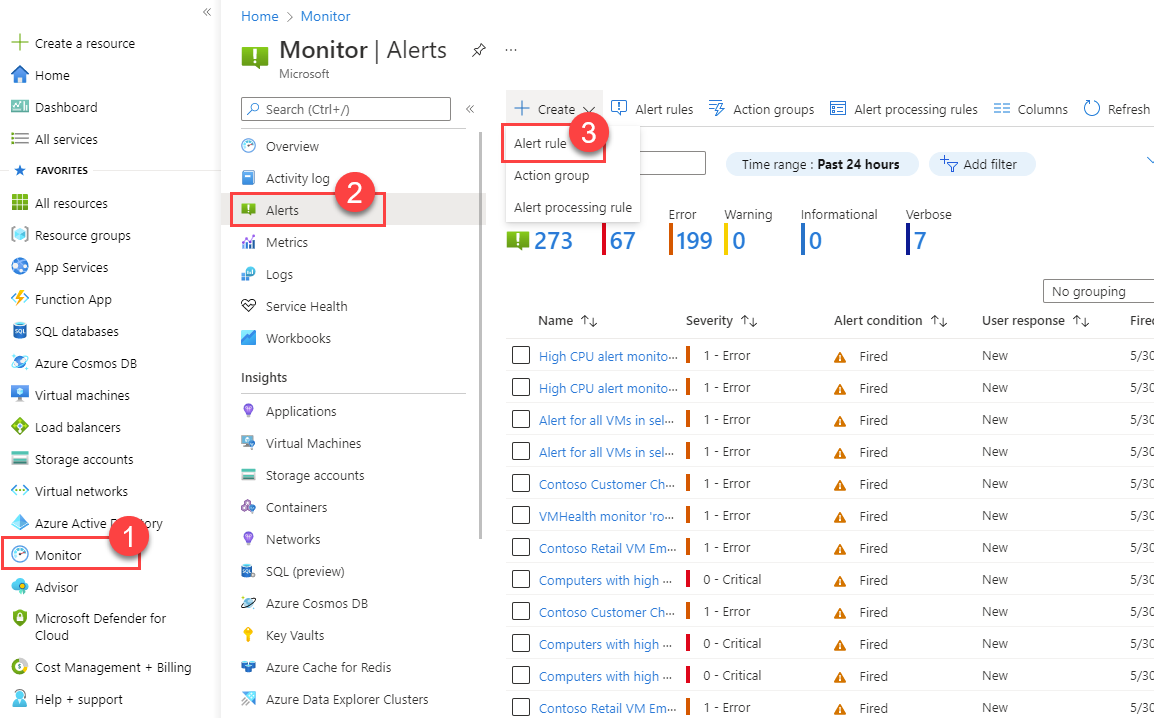
Create or edit an alert rule from the portal home page
In the portal, select Monitor > Alerts.
Open the + Create menu, and select Alert rule.
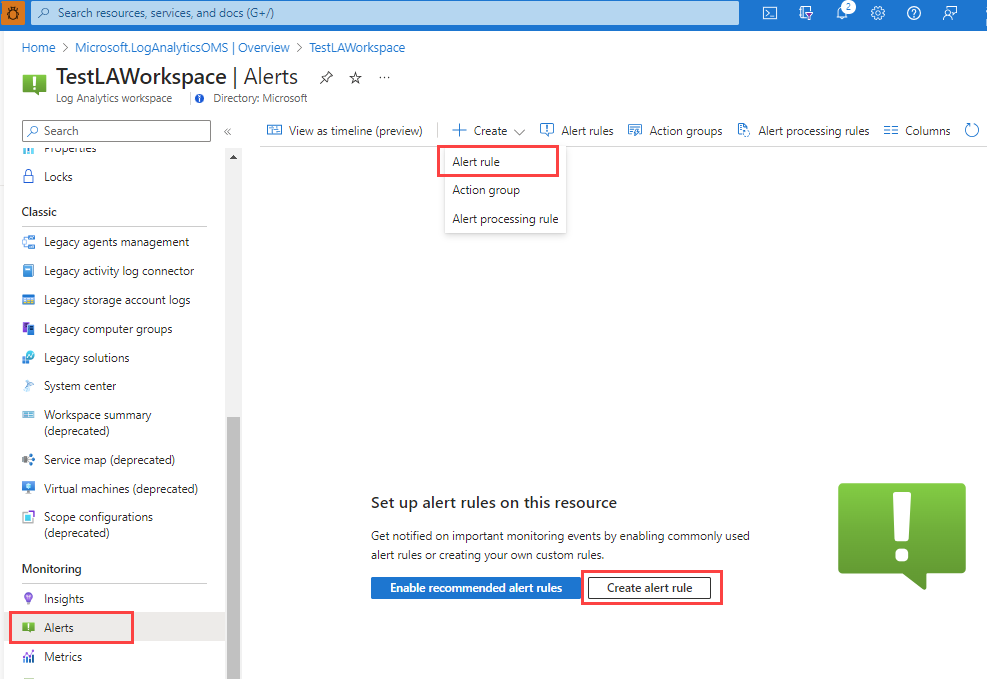
Create or edit an alert rule from a specific resource
In the portal, navigate to the resource.
Select Alerts from the left pane, and then select + Create > Alert rule.
Edit an existing alert rule
In the portal, either from the home page or from a specific resource, select Alerts from the left pane.
Select Alert rules.
Select the alert rule you want to edit, and then select Edit.
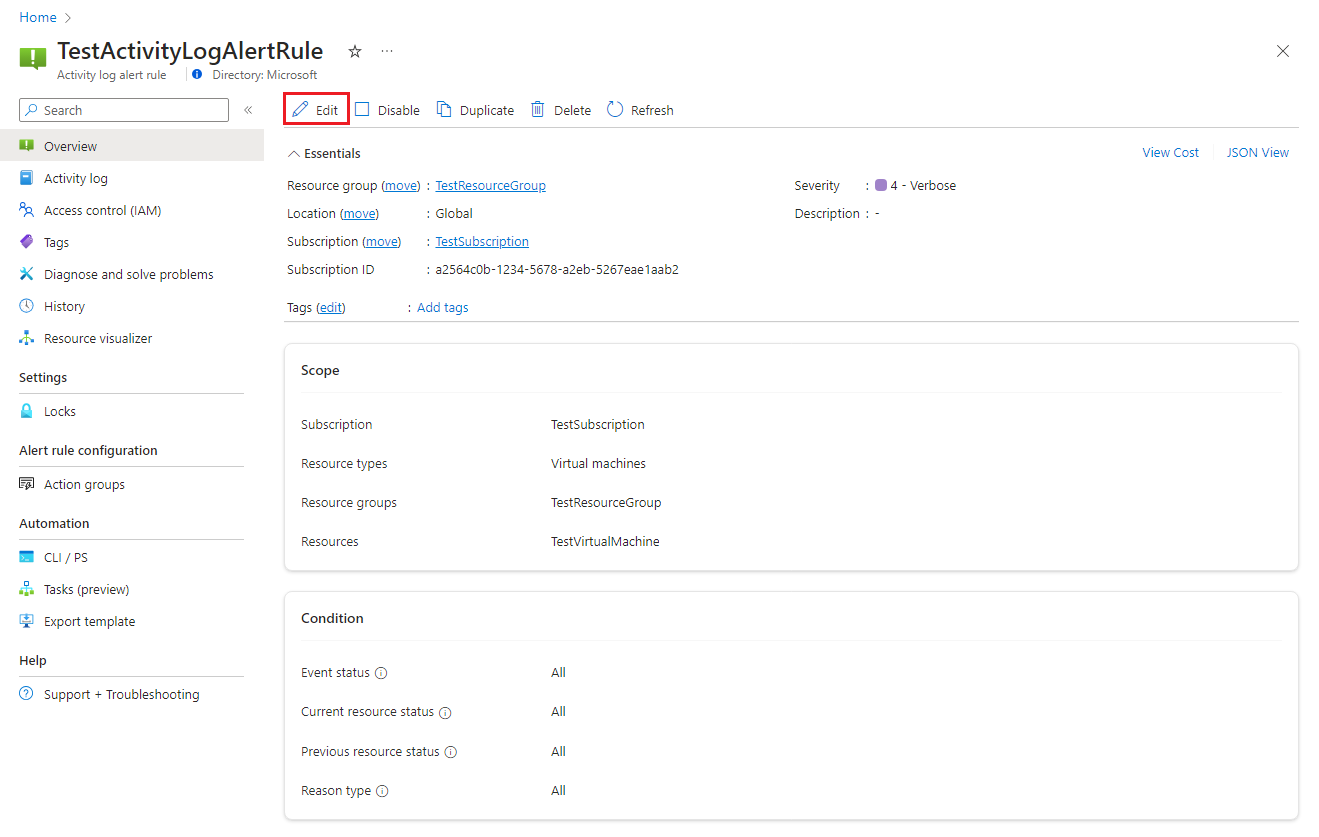
Select any of the tabs for the alert rule to edit the settings.
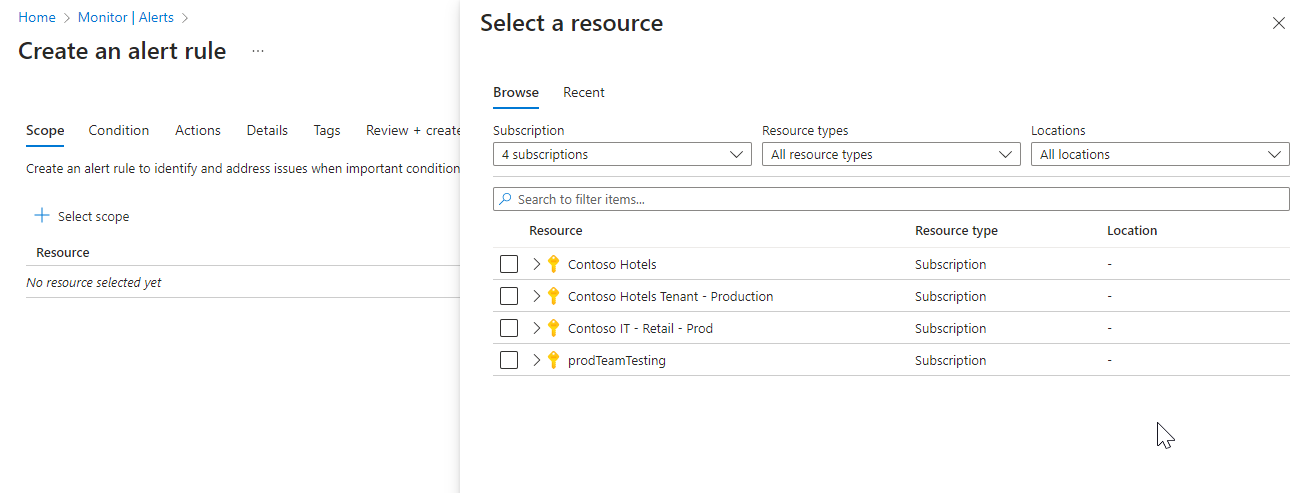
Configure the scope of the alert rule
On the Select a resource pane, set the scope for your alert rule. You can filter by subscription, resource type, or resource location.
Select Apply.
Configure the alert rule conditions
On the Condition tab, select Activity log, Resource health, or Service health, or select See all signals if you want to choose a different signal for the condition.
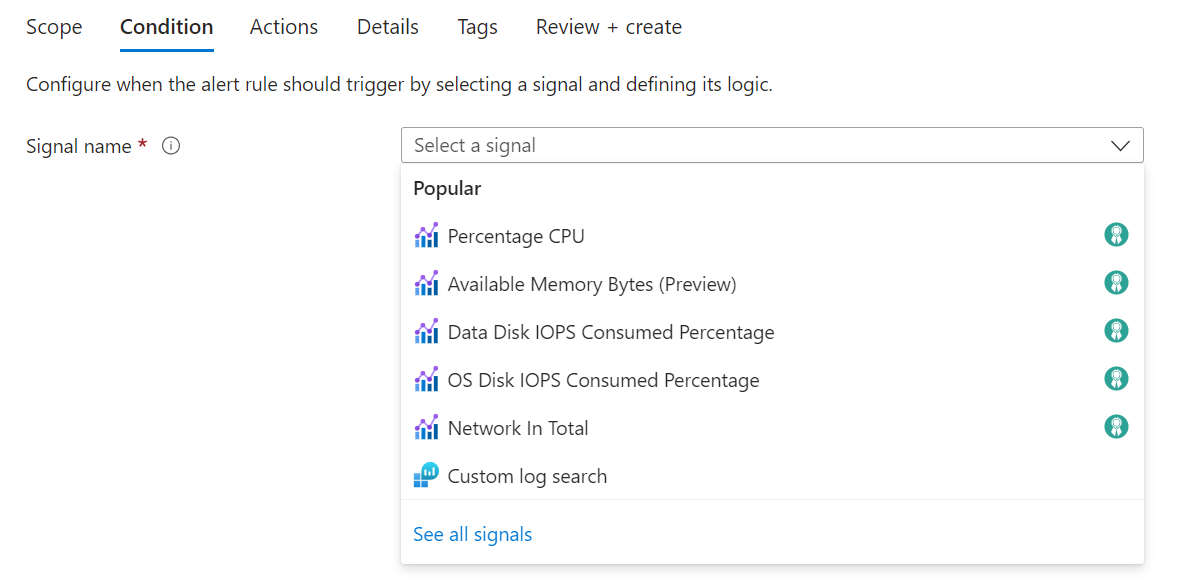
(Optional) If you chose to See all signals in the previous step, use the Select a signal pane to search for the signal name or filter the list of signals. Filter by:
- Signal type: The type of alert rule you're creating.
- Signal source: The service sending the signal.
This table describes the services available for activity log alert rules:
Signal source Description Activity log – Policy The service that provides the Policy activity log events. Activity log – Autoscale The service that provides the Autoscale activity log events. Activity log – Security The service that provides the Security activity log events. Resource health The service that provides the resource-level health status. Service health The service that provides the subscription-level health status. Select the Signal name and Apply.
On the Conditions pane, select the Chart period.
The Preview chart shows you the results of your selection.
Select values for each of these fields in the Alert logic section:
Field Description Event level Select the level of the events for this alert rule. Values are Critical, Error, Warning, Informational, Verbose, and All. Status Select the status levels for the alert. Event initiated by Select the user or service principal that initiated the event.
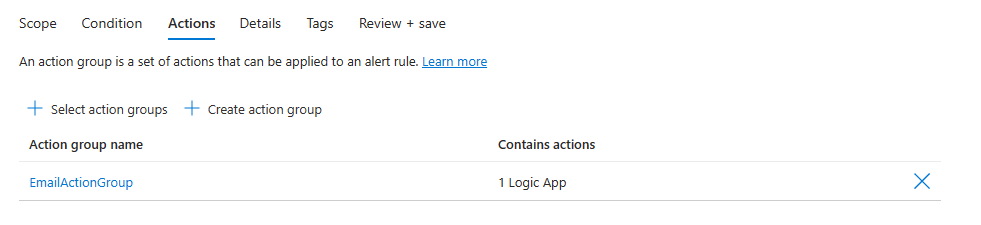
Configure the alert rule actions
On the Actions tab, select or create the required action groups.
Configure the alert rule details

Enter values for the Alert rule name and the Alert rule description.
Select Enable upon creation for the alert rule to start running as soon as you're done creating it.
-
(Optional) In the Custom properties section, if this alert rule contains action groups, you can add your own properties to include in the alert notification payload. You can use these properties in the actions called by the action group, such as by a webhook, Azure function or logic app actions.
The custom properties are specified as key:value pairs, using either static text, a dynamic value extracted from the alert payload, or a combination of both.
The format for extracting a dynamic value from the alert payload is:
${<path to schema field>}. For example: ${data.essentials.monitorCondition}.Use the format of the common alert schema to specify the field in the payload, whether or not the action groups configured for the alert rule use the common schema.
Note
- The common schema overwrites custom configurations. You can't use both custom properties and the common schema.
- Custom properties are added to the payload of the alert, but they do not appear in the email template or in the alert details in the Azure portal.
- Service Health alerts do not support custom properties.
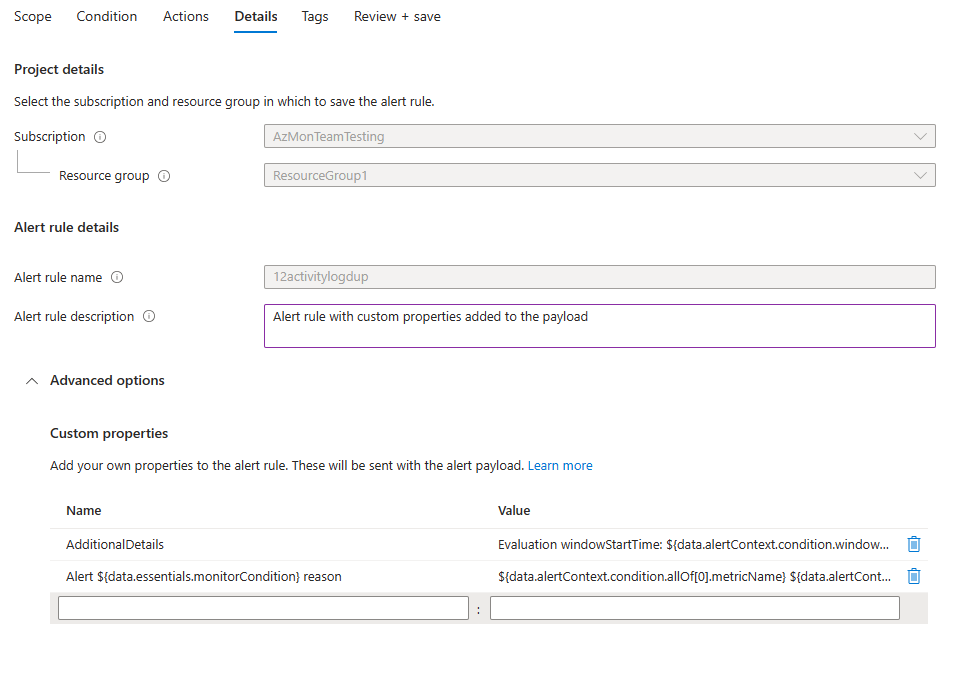
In the following examples, values in the custom properties are used to utilize data from a payload that uses the common alert schema:
Example 1
This example creates an "Additional Details" tag with data regarding the "window start time" and "window end time".
- Name: "Additional Details"
- Value: "Evaluation windowStartTime: ${data.alertContext.condition.windowStartTime}. windowEndTime: ${data.alertContext.condition.windowEndTime}"
- Result: "AdditionalDetails:Evaluation windowStartTime: 2023-04-04T14:39:24.492Z. windowEndTime: 2023-04-04T14:44:24.492Z"
Example 2 This example adds the data regarding the reason of resolving or firing the alert.
- Name: "Alert ${data.essentials.monitorCondition} reason"
- Value: "${data.alertContext.condition.allOf[0].metricName} ${data.alertContext.condition.allOf[0].operator} ${data.alertContext.condition.allOf[0].threshold} ${data.essentials.monitorCondition}. The value is ${data.alertContext.condition.allOf[0].metricValue}"
- Result: Example results could be something like:
- "Alert Resolved reason: Percentage CPU GreaterThan5 Resolved. The value is 3.585"
- “Alert Fired reason": "Percentage CPU GreaterThan5 Fired. The value is 10.585"
Configure alert rule tags
On the Tags tab, set any required tags on the alert rule resource.
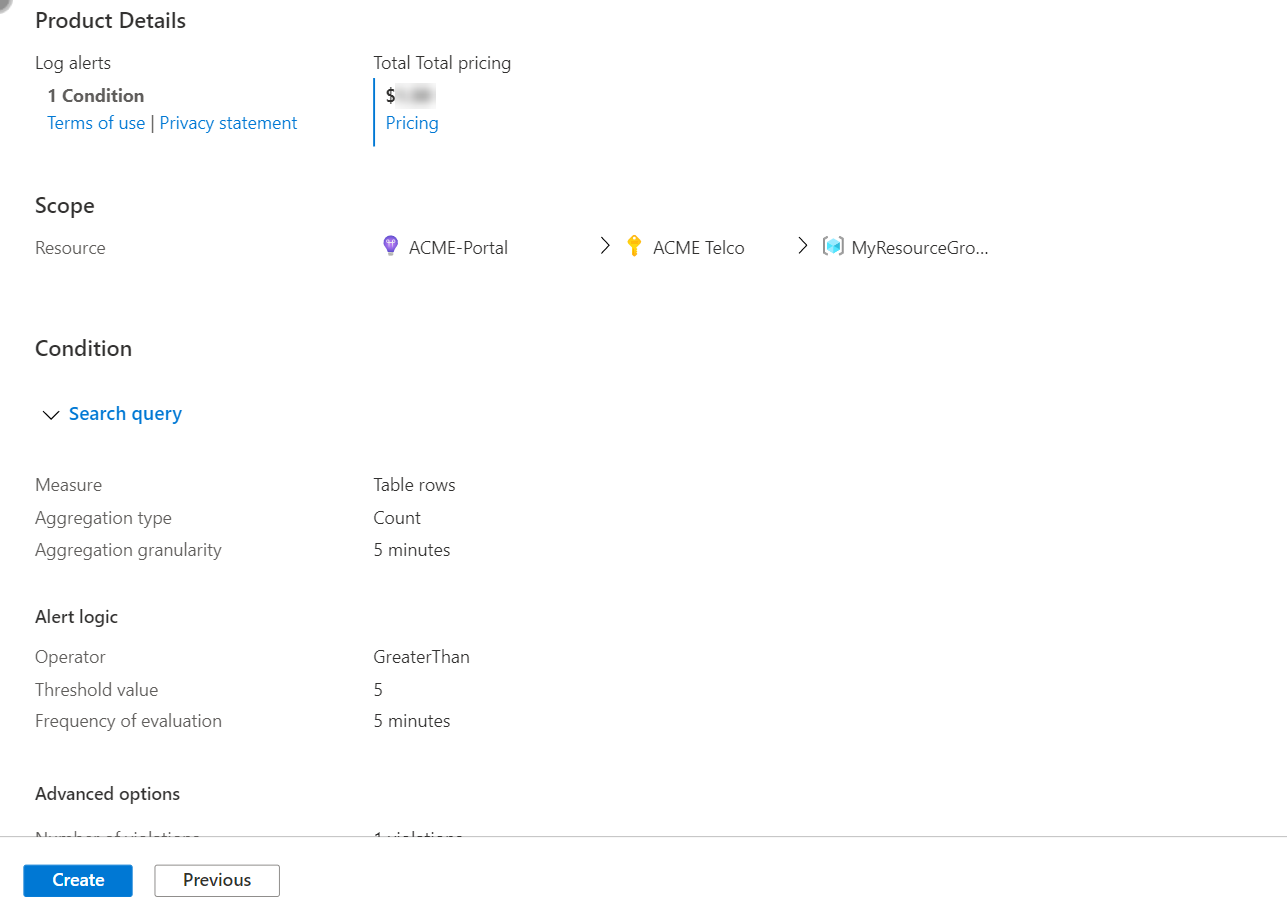
Review and create the alert rule
On the Review + create tab, the rule is validated, and lets you know about any issues.
When validation passes and you've reviewed the settings, select the Create button.
Next steps
Pripomienky
Pripravujeme: V priebehu roka 2024 postupne zrušíme službu Problémy v službe GitHub ako mechanizmus pripomienok týkajúcich sa obsahu a nahradíme ju novým systémom pripomienok. Ďalšie informácie nájdete na stránke: https://aka.ms/ContentUserFeedback.
Odoslať a zobraziť pripomienky pre