Manage agent registry options
This section describes registry options that you can set to control the runtime processing behavior of the Microsoft Entra provisioning agent.
Configure LDAP connection timeout
When performing LDAP operations on configured Active Directory domain controllers, by default, the provisioning agent uses the default connection timeout value of 30 seconds. If your domain controller takes more time to respond, then you may see the following error message in the agent log file:
System.DirectoryServices.Protocols.LdapException: The operation was aborted because the client side timeout limit was exceeded.
LDAP search operations can take longer if the search attribute is not indexed. As a first step, if you get the above error, first check if the search/lookup attribute is indexed. If the search attributes are indexed and the error persists, you can increase the LDAP connection timeout using the following steps:
- Log on as Administrator on the Windows server running the Microsoft Entra provisioning agent.
- Use the Run menu item to open the registry editor (regedit.exe)
- Locate the key folder HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Azure AD Connect Agents\Azure AD Connect Provisioning Agent
- Right-click and select "New -> String Value"
- Provide the name:
LdapConnectionTimeoutInMilliseconds - Double-click on the Value Name and enter the value data as
60000milliseconds.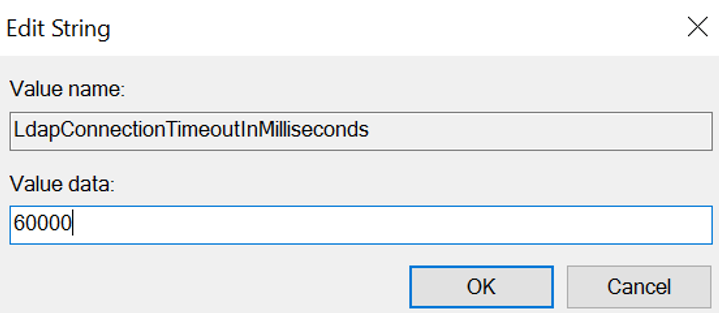
- Restart the Microsoft Entra Connect Provisioning Service from the Services console.
- If you have deployed multiple provisioning agents, apply this registry change to all agents for consistency.
Configure referral chasing
By default, the Microsoft Entra provisioning agent does not chase referrals. You may want to enable referral chasing, to support certain HR inbound provisioning scenarios such as:
- Checking uniqueness of UPN across multiple domains
- Resolving cross-domain manager references
Use the following steps to turn on referral chasing:
- Log on as Administrator on the Windows server running the Microsoft Entra provisioning agent.
- Use the Run menu item to open the registry editor (regedit.exe)
- Locate the key folder HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Azure AD Connect Agents\Azure AD Connect Provisioning Agent
- Right-click and select "New -> String Value"
- Provide the name:
ReferralChasingOptions - Double-click on the Value Name and enter the value data as
96. This value corresponds to the constant value forReferralChasingOptions.Alland specifies that both subtree and base-level referrals will be followed by the agent.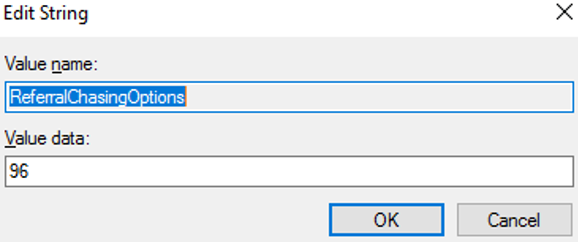
- Restart the Microsoft Entra Connect Provisioning Service from the Services console.
- If you have deployed multiple provisioning agents, apply this registry change to all agents for consistency.
Note
You can confirm the registry options have been set by enabling verbose logging. The logs emitted during agent startup will display the config values picked from the registry.
Next steps
Phản hồi
Sắp ra mắt: Trong năm 2024, chúng tôi sẽ dần gỡ bỏ Sự cố với GitHub dưới dạng cơ chế phản hồi cho nội dung và thay thế bằng hệ thống phản hồi mới. Để biết thêm thông tin, hãy xem: https://aka.ms/ContentUserFeedback.
Gửi và xem ý kiến phản hồi dành cho