什么是条件访问?
新式安全外围现在已不止于组织的网络外围,还包括用户和设备标识。 在做出访问控制决策的过程中,组织现在会使用标识驱动的信号。 Microsoft Entra 条件访问统合信号,以做出决策并强制实施组织策略。 条件访问是 Microsoft 的零信任策略引擎,在强制执行策略决策时会考虑来自各种源的信号。
最简单地讲,条件访问策略是一些 if-then 语句:如果用户想要访问某个资源,则必须完成某个操作。 例如:如果用户想要访问应用程序或服务(如 Microsoft 365),则必须执行多重身份验证才能获取访问权限。
管理员面临着两个主要目标:
- 使用户能够随时随地保持高效的工作
- 保护组织的资产
使用条件访问策略,可以在必要时应用适当的访问控制来确保组织的安全。
重要
完成第一因素身份验证后将强制执行条件访问策略。 在遇到拒绝服务 (DoS) 攻击等情景中,条件访问不应充当组织的第一道防线,但它可以使用这些事件的信号来确定访问权限。
常见信号
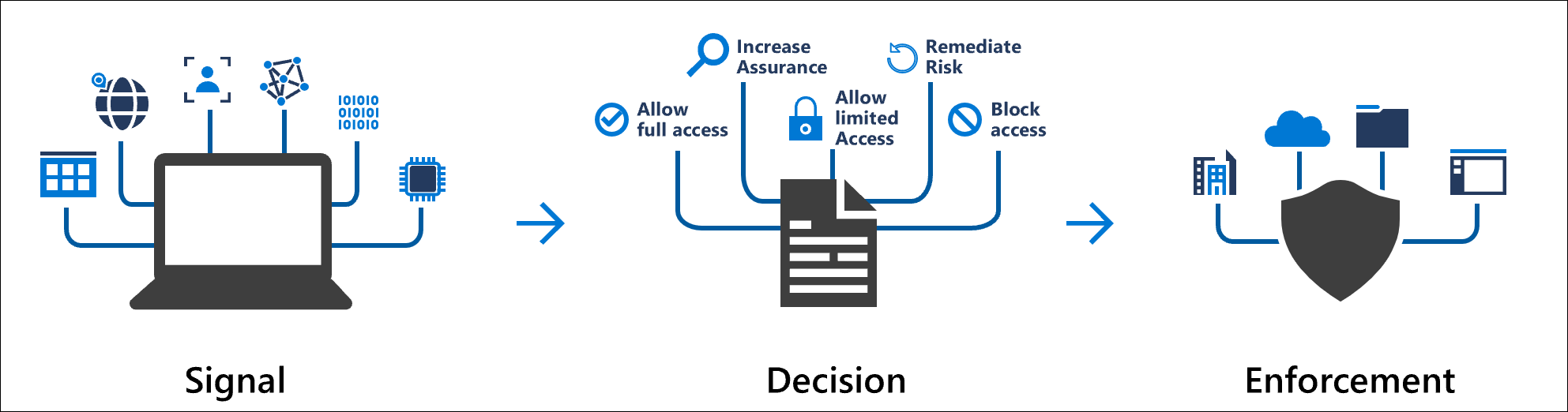
条件访问会在做出访问决策时考虑来自各种源的信号。
这些信号包括:
- 用户或组成员身份
- 策略可以针对特定的用户和组,并为管理员提供精细的访问控制。
- IP 定位信息
- 组织可以创建在做出策略决策时使用的受信任 IP 地址范围。
- 管理员可以指定整个国家/地区的 IP 范围,阻断或允许来自其范围内的流量。
- 设备
- 实施条件访问策略时,用户可以使用的装有特定平台或标有特定状态的设备。
- 使用设备的筛选器将策略目标设定为特定设备,例如特权访问工作站。
- 应用程序
- 尝试访问特定应用程序的用户可以触发不同的条件访问策略。
- 实时风险和计算风险检测
- 将信号与 Microsoft Entra ID 保护相集成可让条件访问策略识别并修正存在风险的用户和登录行为。
- Microsoft Defender for Cloud Apps
- 实时监视和控制用户应用程序访问和会话。 此集成可提高对云环境的访问和在其中执行的活动的可见性和控制。
常见决策
- 阻止访问
- 最严格的决策
- 授予访问权限
- 限制较少的决策可要求以下一个或多个选项:
- 要求多重身份验证
- 需要身份验证强度
- 要求将设备标记为合规
- 需要 Microsoft Entra 混合联接设备
- “需要已批准的客户端应用”
- 要求应用保护策略
- 要求更改密码
- 需要使用条款
- 限制较少的决策可要求以下一个或多个选项:
经常应用的策略
许多组织都存在条件访问策略可以帮助解决的常见访问问题,例如:
- 要求具有管理角色的用户执行多重身份验证
- 要求在运行 Azure 管理任务时执行多重身份验证
- 阻止用户尝试使用旧式身份验证协议登录
- 要求安全信息注册的受信任位置
- 阻止或允许来自特定位置的访问
- 阻止有风险的登录行为
- 要求在组织管理的设备上使用特定的应用程序
管理员可以从头开始创建策略,也可以借助门户中的模版策略,或使用 Microsoft Graph API。
管理员体验
具有条件访问管理员角色的管理员可以管理策略。
可在 Microsoft Entra 管理中心中的“保护”>“条件访问”下找到条件访问。
- “概述”页提供策略状态、用户、设备和应用程序的摘要,以及常规和安全警报以及建议。
- “覆盖范围”页提供过去 7 天内有和没有条件访问策略覆盖的应用程序的概要。
- “监视”页允许管理员查看可筛选的登录图,以查看策略覆盖范围中的潜在缺口。
“策略”页上的条件访问策略可以由管理员根据行动者、目标资源、条件、已应用控件、状态或日期等项进行筛选。 通过此筛选功能,管理员可以根据其配置快速查找特定策略。
许可证要求
使用此功能需要 Microsoft Entra ID P1 许可证。 要根据需要查找合适的许可证,请参阅比较 Microsoft Entra ID 的正式发布功能。
拥有 Microsoft 365 商业高级版许可证的客户也可以访问条件访问功能。
基于风险的策略需要访问标识保护,这需要 P2 许可证。
其他与条件访问策略交互的产品和功能需要适用于这些产品和功能的相应许可。
条件访问所需的许可证过期时,不会自动禁用或删除策略。 这样,客户就能够从条件访问策略迁移出来,同时防止其安全状况突然发生变化。 可以查看和删除剩余的策略,但不能再对其进行更新。
安全默认值有助于防范与标识相关的攻击,并且适用于所有客户。
零信任
此功能有助于组织将其标识与零信任体系结构的三个指导原则保持一致:
- 显式验证
- 使用最小特权
- 假定数据泄露
要详细了解零信任和其他让组织与指导原则保持一致的方式,请参阅零信任指导中心。