你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
在 Windows 计算机上安装 Log Analytics 代理
本文提供有关如何使用以下方法在 Windows 计算机上安装 Log Analytics 代理的信息:
- 使用安装向导或命令行手动进行安装。
- Azure 自动化 Desired State Configuration (DSC)。
本文所述的安装方法通常用于本地或其他云中的虚拟机。 有关可用于 Azure 虚拟机的更高效选项,请参阅安装选项。
重要
旧版 Log Analytics 代理将于 2024 年 8 月弃用。 在此日期之后,Microsoft 将不再为 Log Analytics 代理提供任何支持。 请在 2024 年 8 月之前迁移到 Azure Monitor 代理,这样才能继续引入数据。
注意
安装 Log Analytics 代理通常不需要重启计算机。
要求
支持的操作系统
有关 Log Analytics 代理支持的 Windows 版本的列表,请参阅 Azure Monitor 代理概述。
SHA-2 代码签名支持要求
Windows 代理于 2020 年 8 月 17 日开始以独占方式使用 SHA-2 签名。 此更改将影响使用旧版 OS 上的 Log Analytics 代理作为任何 Azure 服务(如 Azure Monitor、Azure 自动化、Azure 更新管理、Azure 更改跟踪、Microsoft Defender for Cloud、Microsoft Sentinel、Windows Defender Advanced Threat Protection)一部分的客户。
除非你在旧版 OS 版本(如 Windows 7、Windows Server 2008 R2 和 Windows Server 2008)上运行代理,否则更改不需要任何客户操作。 在 2020 年 8 月 17 日之前,在旧版 OS 版本上运行的客户必须在其计算机上执行以下操作,否则其代理会停止将数据发送到其 Log Analytics 工作区:
为 OS 安装最新服务器包。 必需的服务包版本包括:
- Windows 7 SP1
- Windows Server 2008 SP2
- Windows Server 2008 R2 SP1
要为 OS 安装 SHA-2 签名 Windows 更新,请参阅适用于 Windows 和 WSUS 的 2019 SHA-2 代码签名支持要求。
更新到 Windows 代理的最新版本(版本 10.20.18067)。
我们建议你将代理配置为使用 TLS 1.2。
网络要求
有关 Windows 代理的网络要求,请参阅 Log Analytics 代理概述。
将代理配置为使用 TLS 1.2
TLS 1.2 协议可确保在 Windows 代理与 Log Analytics 服务之间进行通信的传输中数据的安全性。 如果要在默认情况下未启用 TLS 1.2 的操作系统上安装,则应使用以下步骤配置 TLS 1.2。
查找以下注册表子项:HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols。
在“Protocols”下为 TLS 1.2 创建一个子项:HKLM\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2。
在你之前创建的 TLS 1.2 协议版本子项下创建一个 Client 子项。 例如,HKLM\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client。
在 HKLM\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client 下创建以下 DWORD 值:
- Enabled [值 = 1]
- DisabledByDefault [值 = 0]
将 .NET Framework 4.6 或更高版本配置为安全加密,因为默认情况下禁用此功能。 强加密使用更安全的网络协议(例如 TLS 1.2)并且会阻止不安全的协议。
- 查找以下注册表子项:HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319。
- 在此子项下创建值为 1的 DWORD 值 SchUseStrongCrypto。
- 查找以下注册表子项:HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319。
- 在此子项下创建值为 1的 DWORD 值 SchUseStrongCrypto。
- 重启系统以使设置生效。
工作区 ID 和密钥
无论使用何种安装方法,都需要有该代理将要连接到的 Log Analytics 工作区的工作区 ID 和密钥。 请从 Azure 门户中的“Log Analytics 工作区”菜单中选择该工作区。 然后在“设置”部分中选择“代理”。
注意
在初始设置期间,无法将代理配置为向多个工作区报告。 通过从控制面板或 PowerShell 更新设置,在安装后添加或删除工作区。
注意
虽然有可能重新生成 Log Analytics 工作区共享密钥,但这旨在不立即限制对当前使用这些密钥的任何代理的访问。 代理使用该密钥生成在三个月后过期的证书。 重新生成共享密钥只会阻止代理续订其证书,在证书过期之前不会继续使用这些证书。
安装代理
重要
旧版 Log Analytics 代理将于 2024 年 8 月弃用。 在此日期之后,Microsoft 将不再为 Log Analytics 代理提供任何支持。 请在 2024 年 8 月之前迁移到 Azure Monitor 代理,这样才能继续引入数据。
以下步骤在计算机上使用代理的设置向导在 Azure 和 Azure 政府云中安装并配置 Log Analytics 代理。 如果希望了解如何将代理配置为也向 System Center Operations Manager 管理组进行报告,请参阅使用代理设置向导部署 Operations Manager 代理。
- 在 Log Analytics 工作区中,从先前导航到的“Windows 服务器”页,根据 Windows 操作系统的处理器体系结构选择相应的“下载 Windows 代理”版本。
- 运行安装程序在计算机上安装该代理。
- 在“欢迎”页面上,单击“下一步”。
- 在“许可条款”页面上阅读许可协议,然后单击“我接受” 。
- 在“目标文件夹”页面上更改或保留默认安装文件夹,然后单击“下一步” 。
- 在“代理安装选项”页上,选择将代理连接到 Azure Log Analytics,单击“下一步”。
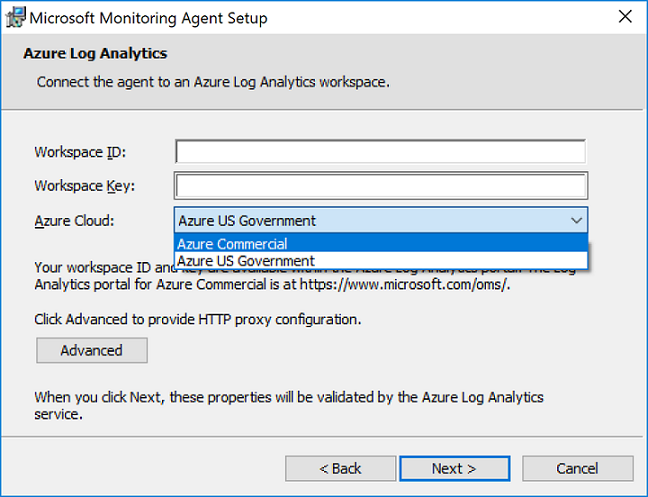
- 在“Azure Log Analytics”页面上,执行以下操作:
- 粘贴前面复制的“工作区 ID”和“工作区密钥(主密钥)”。 如果计算机应向 Azure 政府云中的 Log Analytics 工作区报告,请从“Azure 云”下拉列表中选择“Azure 美国政府版”。
- 如果计算机需要通过代理服务器来与 Log Analytics 通信,请单击“高级”并提供代理服务器的 URL 和端口号。 如果代理服务器要求身份验证,请键入用于在代理服务器上进行身份验证的用户名和密码,并单击“下一步”。
- 提供必需的配置设置后,单击“下一步”。
- 在“准备安装”页上检查所做的选择,并单击“安装”。
- 在“配置已成功完成”页上,单击“完成”。
完成后,Microsoft Monitoring Agent 将显示在“控制面板”中。 要确认其正在向 Log Analytics 报告,请参阅验证代理与 Log Analytics 的连接。
验证代理与 Azure Monitor 的连接
安装代理完成后,可以验证代理是否已成功连接并采用两种方式进行报告。
在“控制面板”的“系统和安全性”中,找到“Microsoft Monitoring Agent”项。 选择此项,代理应会在“Azure Log Analytics”选项卡上显示一条消息,指出:“Microsoft Monitoring Agent 已成功连接到 Microsoft Operations Management Suite 服务”。
还可在 Azure 门户中执行日志查询:
在 Azure 门户中,搜索并选择“监视”。
在菜单中选择“日志”。
在“日志”窗格的查询字段中输入:
Heartbeat | where Category == "Direct Agent" | where TimeGenerated > ago(30m)
在返回的搜索结果中,应可以看到计算机的检测信号记录,该记录指示计算机已连接到服务,并向其报告。
缓存信息
来自 Log Analytics 代理的数据在发送到 Azure Monitor 之前会缓存在本地计算机上的“C:\Program Files\Microsoft Monitoring Agent\Agent\Health Service State”中。 该代理会尝试每隔 20 秒上传一次。 如果操作失败,它会等待以指数级增加的一段时间,直到成功为止: 它会在第二次尝试之前等待 30 秒,在接下来的一次尝试之前等待 60 秒,在再下一次尝试之前等待 120 秒,依此类推,直到再次成功连接为止,两次重试之间的最长间隔为 8.5 小时。 此等待时间会稍微随机化,以避免所有代理同时尝试连接。 达到最大缓冲时,会丢弃最早的数据。
默认缓存大小为 50 MB,但可以在最小 5 MB 和最大 1.5 GB 之间进行配置。 缓存大小将存储在注册表项“HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HealthService\Parameters\Persistence Cache Maximum”中。 该值表示页数(每页 8 KB)。
后续步骤
- 查看管理和维护 Windows 和 Linux 的 Log Analytics 代理以了解如何重新配置、升级代理或从虚拟机中删除代理。
- 如果在安装或管理代理时遇到问题,请查看 Windows 代理疑难解答。

