你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
使用 Microsoft Entra ID 对 Azure Batch 服务进行身份验证
Azure Batch 支持通过 Microsoft Entra ID 进行身份验证,后者是 Microsoft 提供的多租户、基于云的目录和标识管理服务。 Azure 使用 Microsoft Entra ID 对其自己的客户、服务管理员和组织用户进行身份验证。
本文介绍了使用 Microsoft Entra 对 Azure Batch 进行身份验证的两种方法:
集成身份验证会验证与应用进行互动的用户的身份。 应用程序收集用户的凭据,并使用这些凭据对 Azure Batch 资源访问进行身份验证。
服务主体则对无人参与的应用程序进行身份验证。 服务主体定义应用程序的策略和权限,并在运行时借助应用程序访问 Azure Batch 资源。
有关 Microsoft Entra ID 的详细信息,请参阅 Microsoft Entra 文档。
收集身份验证终结点
若要使用 Microsoft Entra ID 对 Batch 应用程序进行身份验证,需要在代码中包含 Microsoft Entra 终结点和 Batch 资源终结点。
Microsoft Entra 终结点
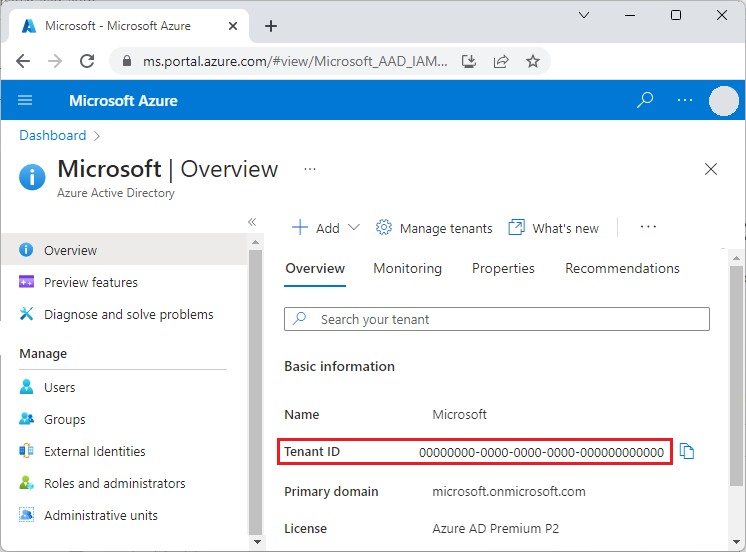
基础 Microsoft Entra 颁发机构终结点为 https://login.microsoftonline.com/。 若要使用 Microsoft Entra ID 进行身份验证,请将此终结点与识别要用于进行身份验证的 Microsoft Entra 租户的租户 ID 结合使用:
https://login.microsoftonline.com/<tenant-id>
可以从 Azure 门户中的主 Microsoft Entra ID 页面获取租户 ID。 还可以在左侧导航中选择“属性”,在“属性”页面上查看“租户 ID”。
重要
使用服务主体进行身份验证时,需要特定于租户的 Microsoft Entra 终结点。
使用集成身份验证进行身份验证时,虽然建议使用特定于租户的终结点,不过并非强制使用。 如果未提供特定于租户的终结点,也可以使用 Microsoft Entra 通用终结点提供通用凭据收集接口。 常用终结点为
https://login.microsoftonline.com/common。
有关 Microsoft Entra 终结点的详细信息,请参阅身份验证和授权。
Batch 资源终结点
Azure Batch 资源终结点 https://batch.core.windows.net/ 用于获取对 Azure Batch 服务的请求进行身份验证的令牌。
向租户注册应用程序
使用 Microsoft Entra 身份验证的第一步是在 Microsoft Entra 租户中注册应用程序。 注册应用程序后,就可从代码中调用 Microsoft 身份验证库 (MSAL)。 MSAL 提供了一个 API,用于从应用程序中使用 Microsoft Entra ID 进行身份验证。 无论是使用集成身份验证还是服务主体,都必须注册应用程序。
注册应用程序时,需要向 Microsoft Entra ID 提供关于应用程序的信息。 然后,Microsoft Entra ID 将提供一个应用程序 ID,用于在运行时将该应用程序关联到 Microsoft Entra ID。 有关应用程序 ID 的详细信息,请参阅 Microsoft Entra ID 中的应用程序对象和服务主体对象。
请按照注册应用程序中介绍的步骤,注册 Azure Batch 应用程序。
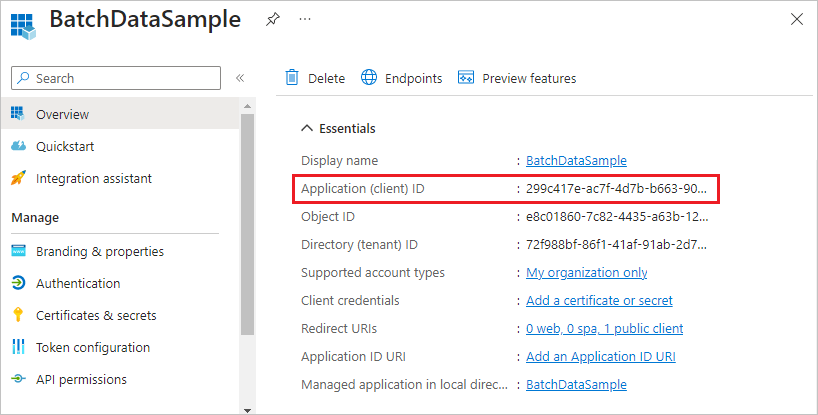
注册应用程序后,即可在应用程序的“概述”页面上看到“应用程序(客户端)ID”。
配置集成身份验证
若要使用集成身份验证进行验证,需要授予应用程序连接到 Azure Batch 服务 API 的权限。 此步骤使应用程序可使用 Microsoft Entra ID 对 Batch 服务 API 的调用进行验证。
注册应用程序后,请按照以下步骤为应用程序授予对 Azure Batch 服务的访问权限:
- 在 Azure 门户中,搜索并选择“应用注册”。
- 从“应用注册”页面中选择你的应用程序。
- 在应用程序的页面的左侧导航栏中选择“API 权限”。
- 在“API 权限”页上,选择“添加权限”。
- 在“请求 API 权限”页面上,选择“Azure Batch”。
- 在“Azure Batch”页面上,“选择权限”之下,选中“user_impersonation”旁边的复选框,然后选择“添加权限”。
现在,“API 权限”页面会显示你的 Microsoft Entra 应用程序有权访问 Microsoft Graph 和 Azure Batch。 将应用注册到 Microsoft Entra ID 时,系统会自动向 Microsoft Graph 授予权限。
配置服务主体
若要对以无人参与方式运行的应用程序进行验证,可以使用服务主体。 使用服务主体对应用程序进行验证时,它将同时向 Microsoft Entra ID 发送应用程序 ID 和密钥。
注册应用程序后,请按照 Azure 门户中的下列步骤配置服务主体:
- 为应用程序请求一个机密。
- 将 Azure 基于角色的访问控制 (Azure RBAC) 分配到应用程序。
为应用程序请求一个机密
按照以下步骤创建并复制要在代码中使用的密钥:
- 在 Azure 门户中,搜索并选择“应用注册”。
- 从“应用注册”页面中选择你的应用程序。
- 在应用程序页上,从左侧导航中选择“证书和机密”。
- 在“证书和机密”边栏页上,选择“新建客户端机密”。
- 在“添加客户端密码”页面中,输入说明并选择密钥的过期时长。
- 选择“添加”以创建机密并将其显示在“证书和机密”页上。
- 将密钥值复制到安全的位置,因为离开此页而后将无法再次访问它。 如果无法访问密钥,可以生成一个新密钥。
将 Azure RBAC 分配到应用程序
按照以下步骤将 Azure RBAC 角色分配给应用程序。 有关详细步骤,请参阅使用 Azure 门户分配 Azure 角色。
- 在 Azure 门户中,导航到应用程序使用的 Azure Batch 帐户。
- 在左侧导航栏中,选择“访问控制(IAM)”。
- 在“访问控制(IAM)”页上,选择“添加角色分配”。
- 在“添加角色分配”页面上,选择“角色”选项卡,然后为应用程序选择“参与者”或“读取器”角色。
- 选择“成员”选项卡,然后选择“成员”下的“选择成员”。
- 在“选择成员”屏幕上,搜索并选择你的应用程序,然后选择“选择”。
- 在“添加角色分配”页面上,选择“查看 + 分配”。
现在,Azure Batch 帐户的“访问控制 (IAM)”页面的“角色分配”选项卡上会显示你的应用程序。
分配自定义角色
自定义角色向用户授予用于提交作业、任务等的粒度权限。 可以使用自定义角色防止用户执行影响成本的操作,例如创建池或修改节点。
可以使用自定义角色向 Microsoft Entra 用户、组或服务主体授予或拒绝以下 Azure Batch RBAC 操作的权限:
- Microsoft.Batch/batchAccounts/pools/write
- Microsoft.Batch/batchAccounts/pools/delete
- Microsoft.Batch/batchAccounts/pools/read
- Microsoft.Batch/batchAccounts/jobSchedules/write
- Microsoft.Batch/batchAccounts/jobSchedules/delete
- Microsoft.Batch/batchAccounts/jobSchedules/read
- Microsoft.Batch/batchAccounts/jobs/write
- Microsoft.Batch/batchAccounts/jobs/delete
- Microsoft.Batch/batchAccounts/jobs/read
- Microsoft.Batch/batchAccounts/certificates/write
- Microsoft.Batch/batchAccounts/certificates/delete
- Microsoft.Batch/batchAccounts/certificates/read
- Microsoft.Batch/batchAccounts/read(适用于任何读取操作)
- Microsoft.Batch/batchAccounts/listKeys/action(适用于任何操作)
自定义角色适用于通过 Microsoft Entra ID 进行身份验证的用户,而不是 Batch 共享密钥帐户凭据。 Auzre Batch 帐户凭据为批处理帐户提供完全权限。 使用 AutoPool 的作业需要池级别权限。
注意
需要在 actions 字段中指定某些角色分配,而其他角色分配需要在 dataActions 字段中指定。 有关详细信息,请参阅 Azure 资源提供程序操作。
下面的示例演示了 Azure Batch 自定义角色定义的过程:
{
"properties":{
"roleName":"Azure Batch Custom Job Submitter",
"type":"CustomRole",
"description":"Allows a user to submit jobs to Azure Batch but not manage pools",
"assignableScopes":[
"/subscriptions/88888888-8888-8888-8888-888888888888"
],
"permissions":[
{
"actions":[
"Microsoft.Batch/*/read",
"Microsoft.Authorization/*/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Support/*",
"Microsoft.Insights/alertRules/*"
],
"notActions":[
],
"dataActions":[
"Microsoft.Batch/batchAccounts/jobs/*",
"Microsoft.Batch/batchAccounts/jobSchedules/*"
],
"notDataActions":[
]
}
]
}
}
有关如何创建自定义角色的更多信息,请参阅 Azure 自定义角色。
代码示例
此部分中的代码示例演示如何使用集成身份验证或服务主体通过 Microsoft Entra ID 进行验证。 这些代码示例使用了 .NET 和 Python,但概念与其他编程语言类似。
注意
Microsoft Entra 身份验证令牌在一小时后过期。 如果使用的是期限较长的 BatchClient 对象,最好在每次请求时从 MSAL 获取令牌,以确保始终拥有有效的令牌。
要在 .NET 中实现此目的,可编写一个方法从 Microsoft Entra ID 中检索令牌,然后将该方法作为委派传递给 BatchTokenCredentials 对象。 发送给 Azure Batch 服务的每一个请求都会调用该委派方法,确保提供有效的令牌。 默认情况下,MSAL 会缓存令牌,以便只在必要时,才从 Microsoft Entra 中检索新令牌。 有关 Microsoft Entra ID 中的令牌的详细信息,请参阅安全令牌。
代码示例:将 Microsoft Entra 集成身份验证与 Batch .NET 一起使用
若要从 Azure Batch .NET 使用集成身份验证进行身份验证,请执行以下操作:
安装 Azure Batch .NET 和 MSAL NuGet 包。
在代码中包含以下
using语句:using Microsoft.Azure.Batch; using Microsoft.Azure.Batch.Auth; using Microsoft.Identity.Client;引用 Microsoft Entra 终结点,包括租户 ID。 可以从 Azure 门户中的 Microsoft Entra ID 概述页面获取租户 ID。
private const string AuthorityUri = "https://login.microsoftonline.com/<tenant-id>";引用 Batch 服务资源终结点:
private const string BatchResourceUri = "https://batch.core.windows.net/";引用 Batch 帐户:
private const string BatchAccountUrl = "https://<myaccount>.<mylocation>.batch.azure.com";指定应用程序的应用程序(客户端 ID)。 可以从 Azure 门户中的应用程序的“概述”页面获取应用程序 ID。
private const string ClientId = "<application-id>";注明注册应用程序时提供的重定向 URL。
private const string RedirectUri = "https://<redirect-uri>";编写一个回调方法从 Microsoft Entra ID 获取身份验证令牌。 以下示例调用了 MSAL 来对与应用程序交互的用户进行身份验证。 MSAL IConfidentialClientApplication.AcquireTokenByAuthorizationCode 方法提示用户输入凭据。 用户提供凭据后,应用程序将继续运行。
authorizationCode 参数是在用户进行身份验证后,从授权服务器获取到的授权代码。
WithRedirectUri指定身份验证后授权服务器重定向用户的重定向 URL。public static async Task<string> GetTokenUsingAuthorizationCode(string authorizationCode, string redirectUri, string[] scopes) { var app = ConfidentialClientApplicationBuilder.Create(ClientId) .WithAuthority(AuthorityUri) .WithRedirectUri(RedirectUri) .Build(); var authResult = await app.AcquireTokenByAuthorizationCode(scopes, authorizationCode).ExecuteAsync(); return authResult.AccessToken; }使用以下代码调用此方法,将
<authorization-code>替换为从授权服务器获取的授权代码。 范围.default确保用户有权访问资源的所有范围。var token = await GetTokenUsingAuthorizationCode("<authorization-code>", "RedirectUri", new string[] { "BatchResourceUri/.default" });构造使用委派作为参数的 BatchTokenCredentials 对象。 使用这些凭据打开 BatchClient 对象。 然后,使用该 BatchClient 对象针对 Azure Batch 服务执行后续操作:
public static void PerformBatchOperations() { Func<Task<string>> tokenProvider = () => GetTokenUsingAuthorizationCode(); using (var client = BatchClient.Open(new BatchTokenCredentials(BatchAccountUrl, tokenProvider))) { client.JobOperations.ListJobs(); } }
代码示例:将 Microsoft Entra 服务主体与 Batch .NET 一起使用
若要使用 Azure Batch .NET 的服务主体进行身份验证,请执行以下操作:
安装 Azure Batch .NET 和 MSAL NuGet 包。
在代码中包含以下
using语句:using Microsoft.Azure.Batch; using Microsoft.Azure.Batch.Auth; using Microsoft.Identity.Client;引用 Microsoft Entra 终结点,包括租户 ID。 使用服务主体时,必须提供特定于租户的终结点。 可以从 Azure 门户中的 Microsoft Entra ID 概述页面获取租户 ID。
private const string AuthorityUri = "https://login.microsoftonline.com/<tenant-id>";引用 Batch 服务资源终结点:
private const string BatchResourceUri = "https://batch.core.windows.net/";引用 Batch 帐户:
private const string BatchAccountUrl = "https://<myaccount>.<mylocation>.batch.azure.com";指定应用程序的应用程序(客户端 ID)。 可以从 Azure 门户中的应用程序的“概述”页面获取应用程序 ID。
private const string ClientId = "<application-id>";指定从 Azure 门户复制的密钥。
private const string ClientKey = "<secret-key>";编写一个回调方法从 Microsoft Entra ID 获取身份验证令牌。 以下 ConfidentialClientApplicationBuilder.Create 方法调用 MSAL 进行无人参与的身份验证。
public static async Task<string> GetAccessToken(string[] scopes) { var app = ConfidentialClientApplicationBuilder.Create(clientId) .WithClientSecret(ClientKey) .WithAuthority(new Uri(AuthorityUri)) .Build(); var result = await app.AcquireTokenForClient(scopes).ExecuteAsync(); return result.AccessToken; }使用以下代码调用此方法。 范围
.default确保应用程序有权访问资源的所有范围。var token = await GetAccessToken(new string[] { "BatchResourceId/.default" });构造使用委派作为参数的 BatchTokenCredentials 对象。 使用这些凭据打开 BatchClient 对象。 然后,使用该 BatchClient 对象针对 Azure Batch 服务执行后续操作:
public static void PerformBatchOperations() { Func<Task<string>> tokenProvider = () => GetAccessToken(); using (var client = BatchClient.Open(new BatchTokenCredentials(BatchAccountUrl, tokenProvider))) { client.JobOperations.ListJobs(); } }
代码示例:将 Microsoft Entra 服务主体与 Batch Python 一起使用
若要使用 Azure Batch Python 的服务主体进行身份验证,请执行以下操作:
安装 azure-batch 和 azure-common Python 模块。
引用模块:
from azure.batch import BatchServiceClient from azure.common.credentials import ServicePrincipalCredentials若要使用服务主体,请提供特定于租户的终结点。 可以从 Azure 门户中的 Microsoft Entra ID“概述”页面或“属性”页面获取租户 ID。
TENANT_ID = "<tenant-id>"引用 Batch 服务资源终结点:
RESOURCE = "https://batch.core.windows.net/"引用 Batch 帐户:
BATCH_ACCOUNT_URL = "https://<myaccount>.<mylocation>.batch.azure.com"指定应用程序的应用程序(客户端 ID)。 可以从 Azure 门户中的应用程序的“概述”页面获取应用程序 ID。
CLIENT_ID = "<application-id>"指定从 Azure 门户复制的密钥:
SECRET = "<secret-key>"创建一个 ServicePrincipalCredentials 对象:
credentials = ServicePrincipalCredentials( client_id=CLIENT_ID, secret=SECRET, tenant=TENANT_ID, resource=RESOURCE )使用服务主体凭据打开一个 BatchServiceClient 对象。 然后,使用该 BatchServiceClient 对象针对 Batch 服务执行后续操作。
batch_client = BatchServiceClient( credentials, batch_url=BATCH_ACCOUNT_URL )
有关如何创建使用 Microsoft Entra 令牌进行身份验证的 Batch 客户端的 Python 示例,请参阅使用 Python 脚本部署 Azure Batch 自定义映像示例。