你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
管理 Azure 策略并将 Azure 监控代理扩展部署到 Azure Arc Linux 和 Windows 服务器
本文指导如何使用支持 Azure Arc 的服务器将 Azure 策略分配给 Azure 之外的 VM,无论它们是在本地还是在其他云上。 借助此功能,你现在可以使用 Azure Policy 审核支持 Azure Arc 的服务器的操作系统中的设置,如果设置不合规,你还可以触发修正任务。
在这种情况下,你将分配一个审核来审核连接 Azure Arc 的计算机是否安装了 Log Analytics 代理。 如果未安装,请使用扩展功能将其自动部署到 VM,这是一种与 Azure VM 相媲美的注册体验。 此方法可用于确保你的所有服务器都已连接到 Azure Monitor、Microsoft Defender for Cloud、Microsoft Sentinel 等服务。
你可以使用 Azure 门户、Azure 资源管理器模板(ARM 模板)或 PowerShell 脚本将策略分配给 Azure 订阅或资源组。 以下过程使用 ARM 模板分配内置策略。
重要
本文中的过程假定你已部署了在本地或其他云上运行的 VM 或服务器,并且你已将其连接到 Azure Arc。如果你尚未这样做,以下信息可以帮助你自动执行此过程。
- GCP Ubuntu 实例
- GCP Windows 实例
- AWS Ubuntu EC2 实例
- AWS Amazon Linux 2 EC2 实例
- VMware vSphere Ubuntu VM
- VMware vSphere Windows Server VM
- Vagrant Ubuntu box
- Vagrant Windows box
查看 Azure Monitor 支持的操作系统文档并确保支持用于这些过程的 VM。 对于 Linux VM,请检查 Linux 发行版和内核以确保你使用的是受支持的配置。
先决条件
克隆 Azure Arc 快速入门存储库。
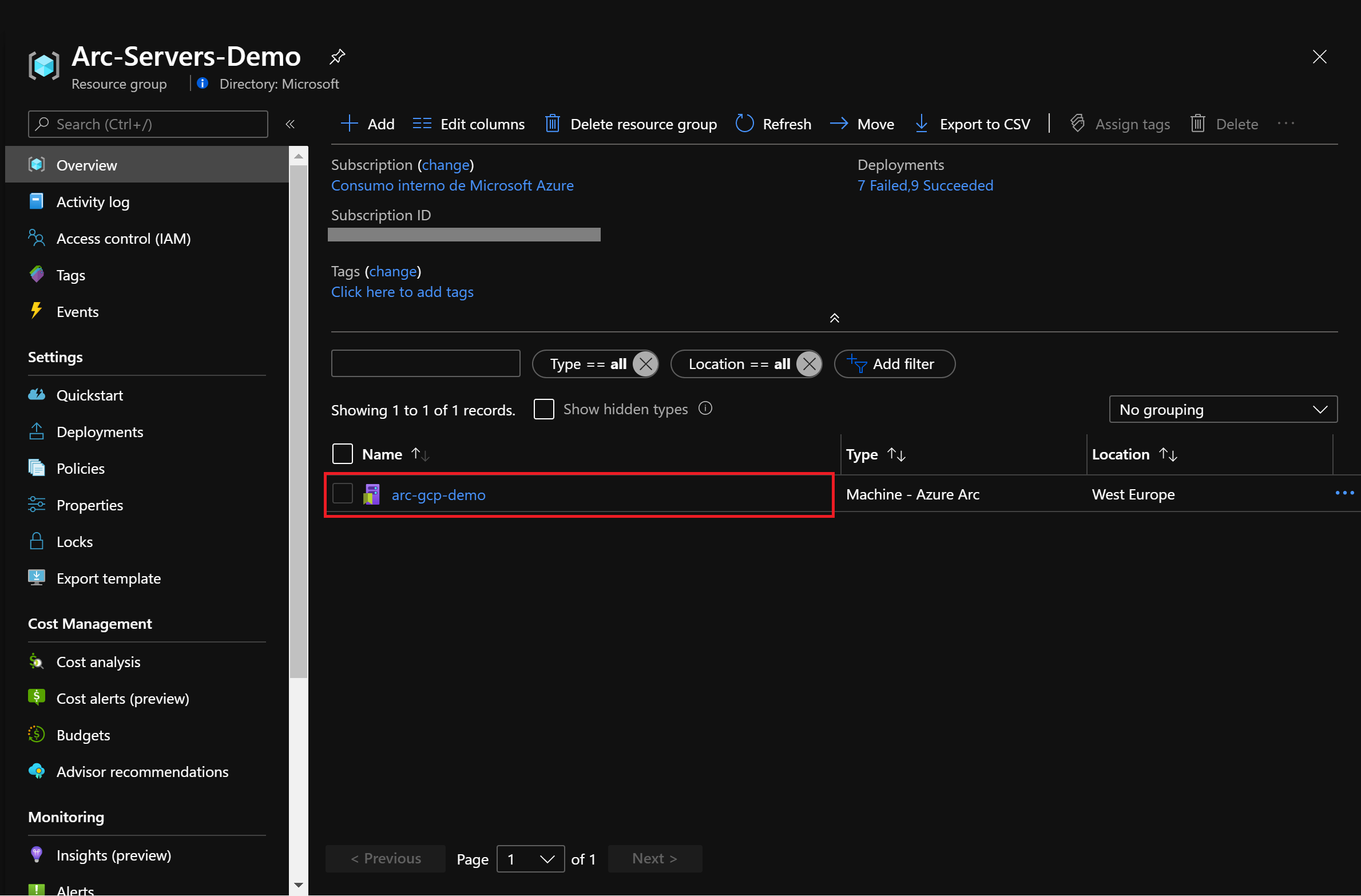
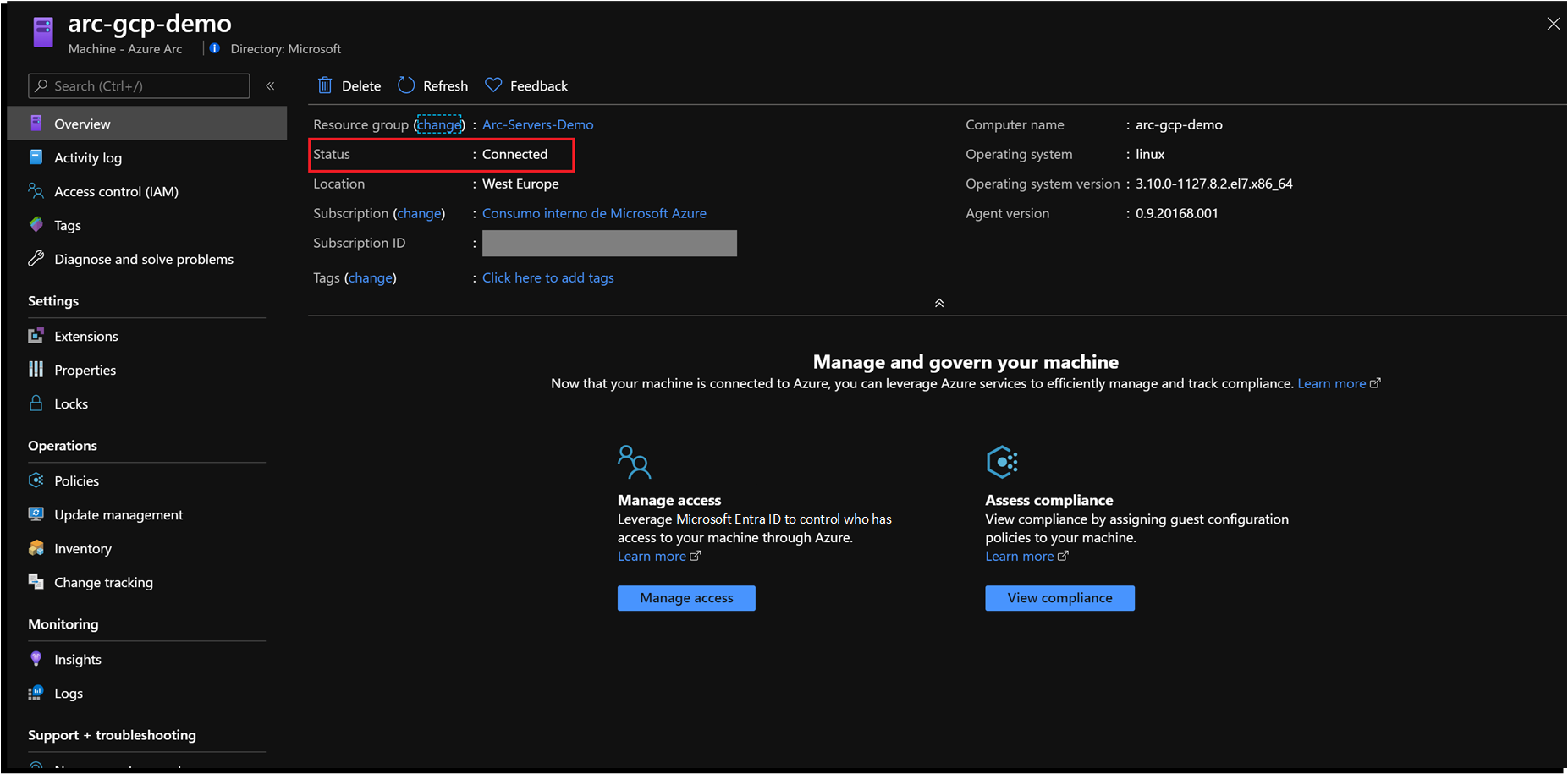
git clone https://github.com/microsoft/azure_arc如上所述,本指南从你已经部署并连接到 Azure Arc 的 VM 或服务器开始。在以下屏幕截图中,Google Cloud Platform (GCP) 服务器已与 Azure Arc 连接,并且在 Azure 中显示为资源。
要安装或更新 Azure CLI。 Azure CLI 应运行版本 2.7 或更高版本。 使用
az --version检查当前安装的版本。创建 Azure 服务主体。
要将 VM 或裸机服务器连接到 Azure Arc,需要使用获分配参与者角色的 Azure 服务主体。 要创建此角色,请登录 Azure 帐户并运行以下命令。 还可以在 Azure Cloud Shell 中运行此命令。
az login az account set -s <Your Subscription ID> az ad sp create-for-rbac -n "<Unique SP Name>" --role contributor --scopes "/subscriptions/<Your Subscription ID>"例如:
az ad sp create-for-rbac -n "http://AzureArcServers" --role contributor --scopes "/subscriptions/00000000-0000-0000-0000-000000000000"输出应如下所示:
{ "appId": "XXXXXXXXXXXXXXXXXXXXXXXXXXXX", "displayName": "http://AzureArcServers", "password": "XXXXXXXXXXXXXXXXXXXXXXXXXXXX", "tenant": "XXXXXXXXXXXXXXXXXXXXXXXXXXXX" }注意
我们强烈建议你将服务主体的范围限定为特定的 Azure 订阅和资源组。
你还需要部署一个 Log Analytics 工作区。 要自动化部署,可以编辑 ARM 模板参数文件并为你的工作区提供名称和位置。
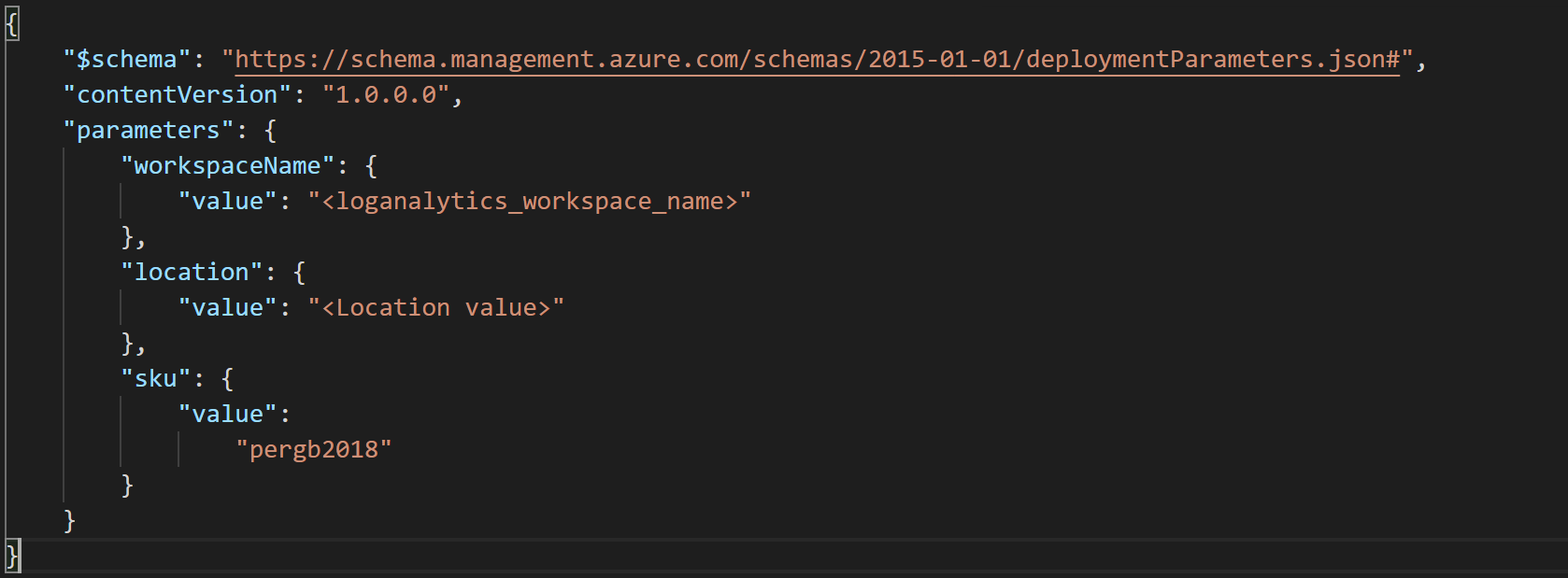
若要部署 ARM 模板,请导航到部署文件夹并运行以下命令:
az deployment group create --resource-group <Name of the Azure resource group> \
--template-file <The `log_analytics-template.json` template file location> \
--parameters <The `log_analytics-template.parameters.json` template file location>
将策略分配给连接 Azure Arc 的计算机
设置所有先决条件后,你可以将策略分配给连接 Azure Arc 的计算机。 编辑参数文件以提供订阅 ID 以及 Log Analytics 工作区。

要开始部署,请使用以下命令:
az policy assignment create --name 'Enable Azure Monitor for VMs' \ --scope '/subscriptions/<Your subscription ID>/resourceGroups/<Name of the Azure resource group>' \ --policy-set-definition '55f3eceb-5573-4f18-9695-226972c6d74a' \ -p <The *policy.json* template file location> \ --assign-identity --location <Azure Region>policy-set-definition标志指向计划Enable Azure MonitorID。分配倡议后,大约需要 30 分钟才能将分配应用于定义的范围。 然后,Azure Policy 针对连接 Azure Arc 的计算机启动评估周期,并将其识别为不合规,因为它仍未部署 Log Analytics 代理配置。 若要检查这一点,请转到“策略”部分下的 Azure Arc 连接计算机。
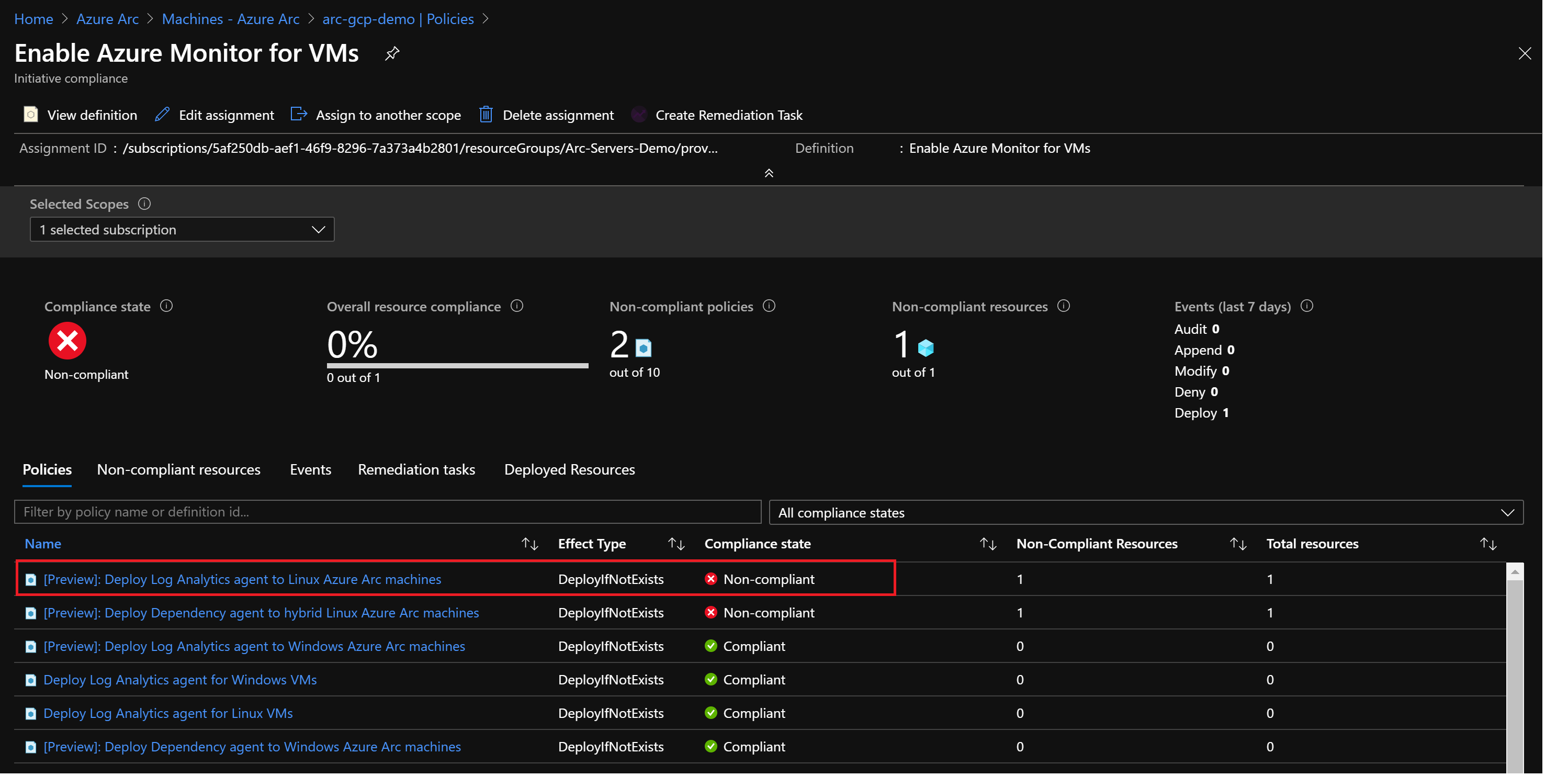
现在,将修正任务分配给不合规资源可使其进入合规状态。
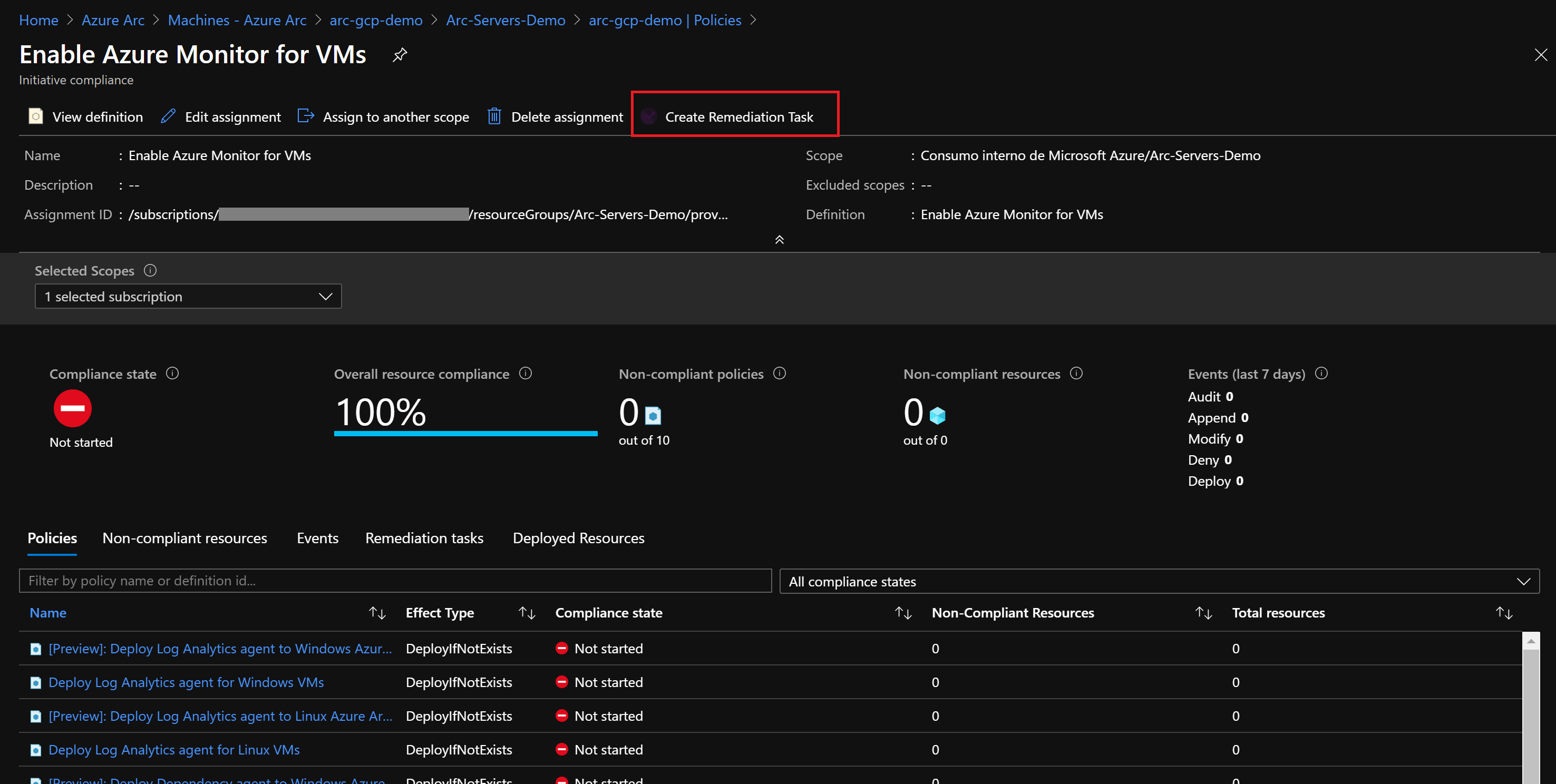
在“要修正的策略”下,选择“[预览] 将日志分析代理部署到 Linux Azure Arc 计算机”,然后选择“修正”。 此修正任务指示 Azure 策略运行
DeployIfNotExists效果,并使用 Azure Arc 扩展管理功能在 VM 上部署 Log Analytics 代理。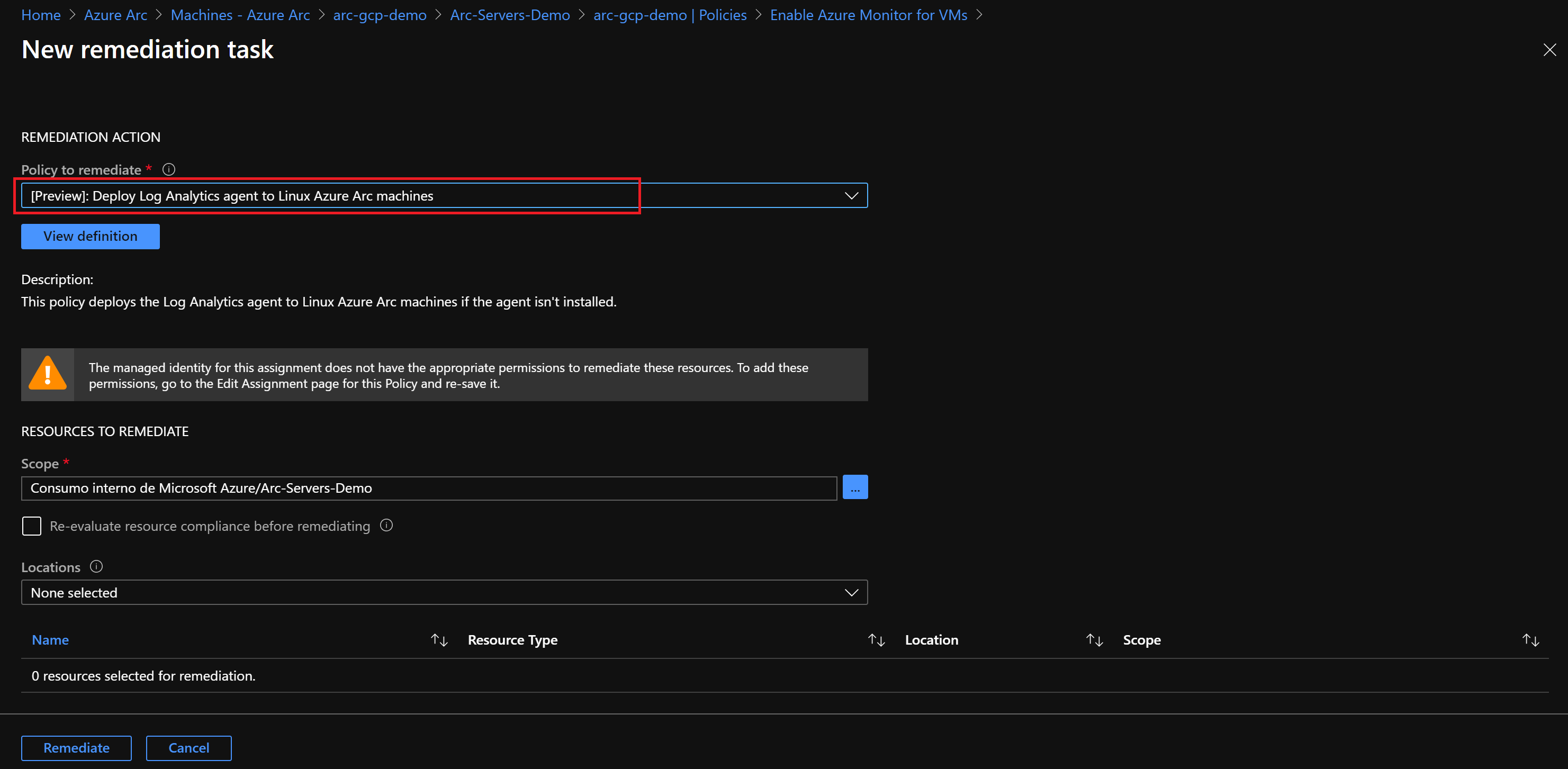
在你分配了修正任务后,系统将再次评估该策略。 系统应该显示 GCP 上的服务器是合规的,并且 Log Analytics 代理已安装在 Azure Arc 计算机上。
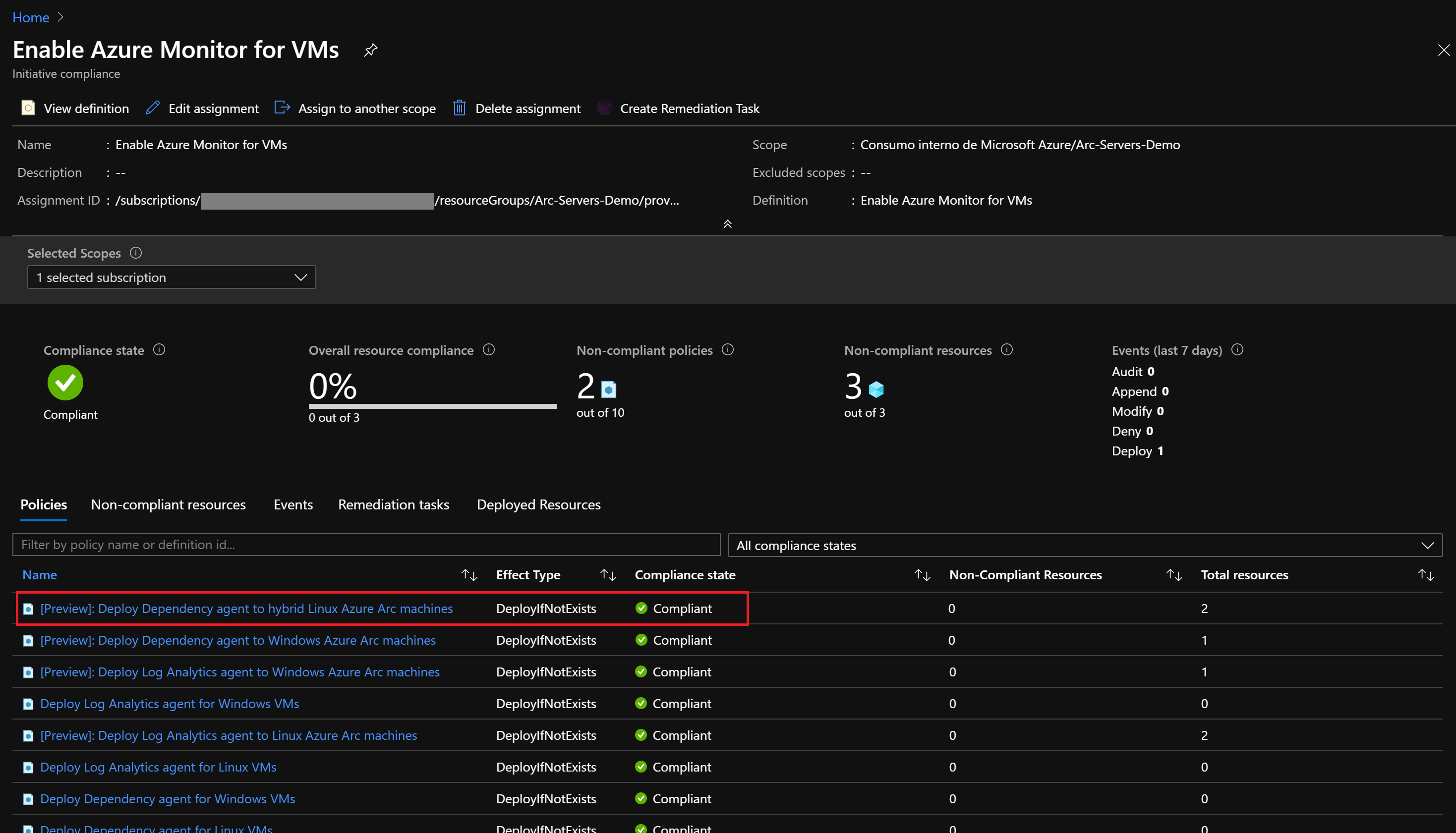
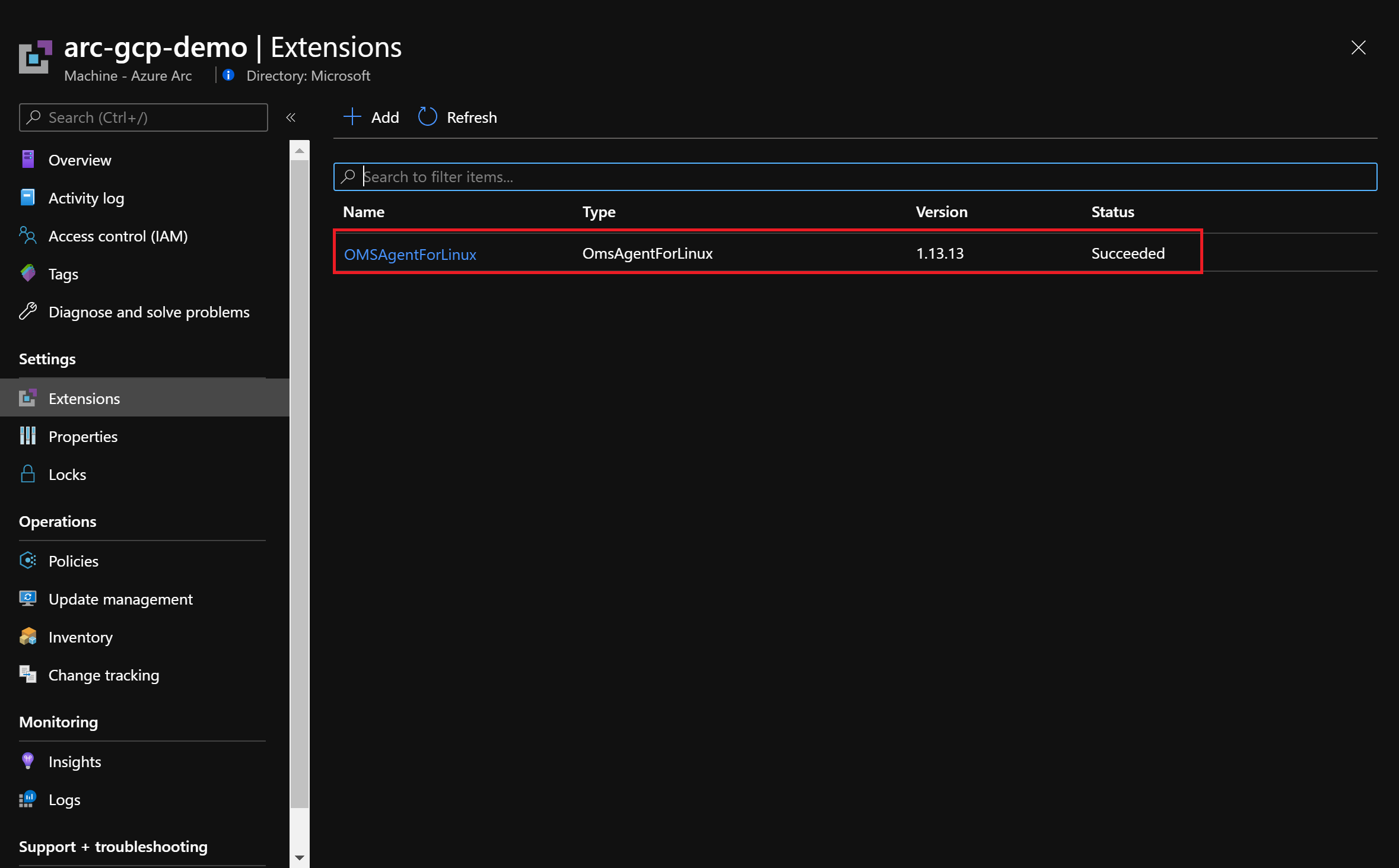
清理环境
完成以下步骤来清理环境。
按照每个指南中的拆卸说明,从每个环境中删除虚拟机。
通过在 Azure CLI 中执行以下脚本来移除 Azure Policy 分配。
az policy assignment delete --name 'Enable Azure Monitor for VMs' --resource-group <resource-group>通过在 Azure CLI 中执行以下脚本来移除 Log Analytics 工作区。 提供在创建 Log Analytics 工作区时使用的工作区名称。
az monitor log-analytics workspace delete --resource-group <Name of the Azure resource group> --workspace-name <Log Analytics workspace Name> --yes
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈