你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
与 Azure PaaS 服务的连接
本文提供了使用 Azure PaaS 服务的推荐连接方法。
设计注意事项
Azure PaaS 服务在其默认配置中通常通过 Microsoft 全球网络通过公开可用的终结点进行访问。 某些客户可能需要减少公共终结点的使用,因此 Azure 平台提供了可选功能来保护这些终结点,甚至使它们完全专用。
某些 PaaS 服务允许基于资源实例系统分配的托管标识(例如 Azure 存储)的公共访问限制
许多 PaaS 服务允许基于受信任的 Azure 服务的公共访问限制,例如Azure 容器注册表
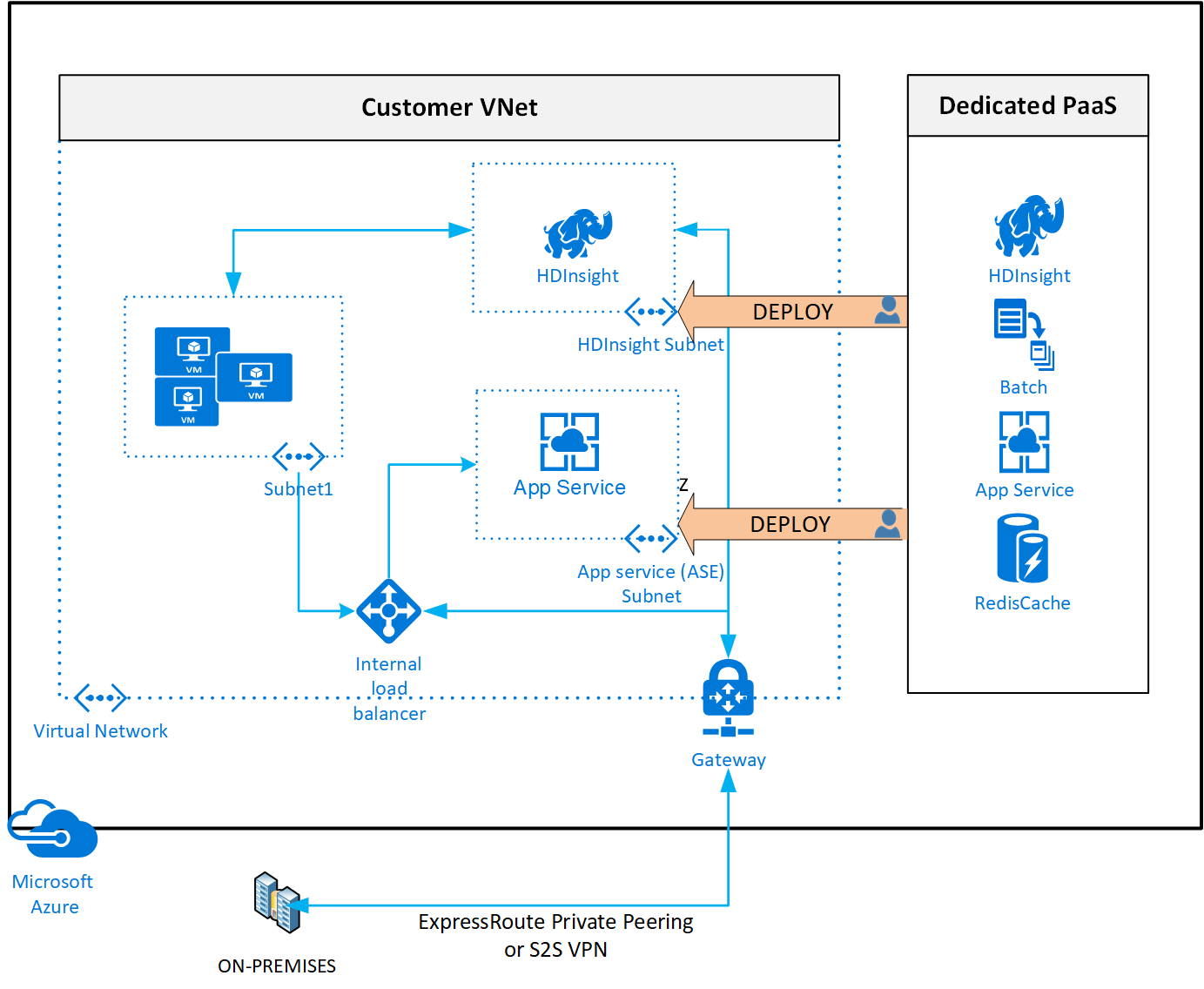
虚拟网络注入 为受支持的服务提供 专用部署 。 管理平面流量仍流经公共 IP 地址。
某些 PaaS 服务与 Azure 专用链接兼容,后者允许通过客户内部的 IP 地址进行专用访问。 有关详细信息,请参阅专用链接的主要优势。
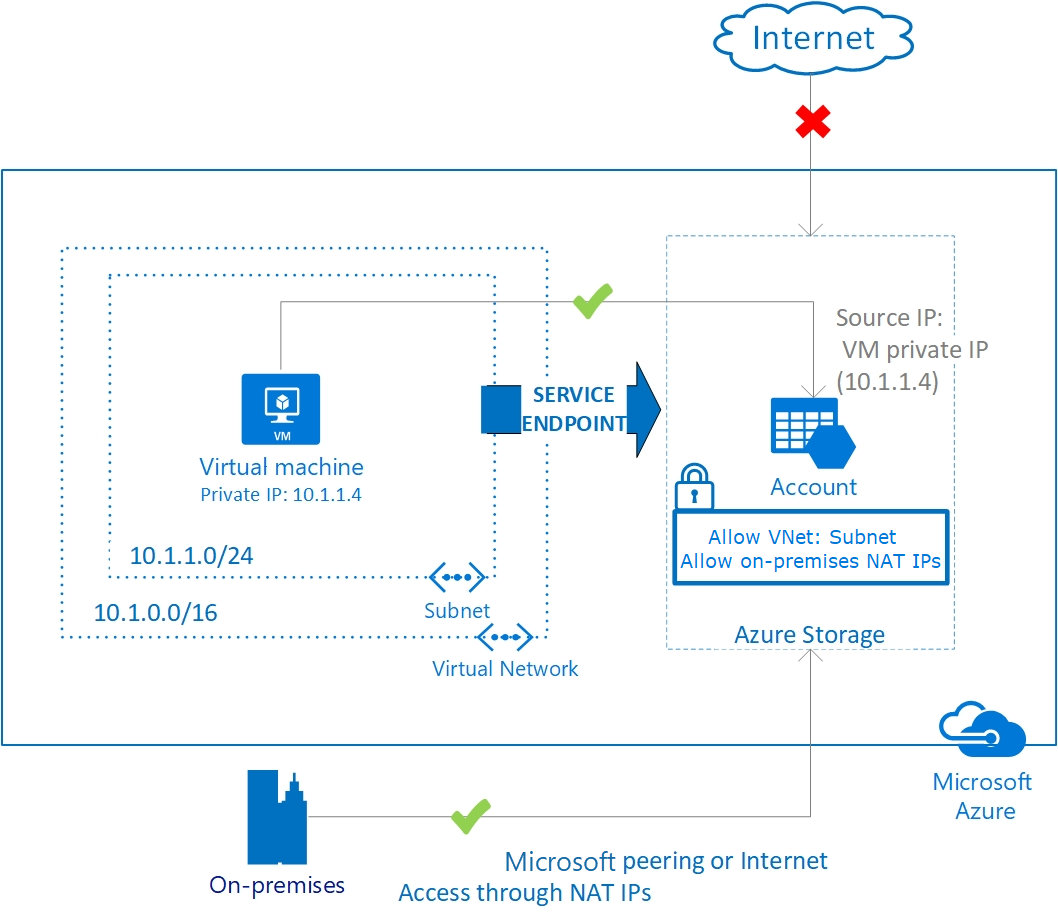
虚拟网络 服务终结点 提供从所选子网到所选 PaaS 服务的服务级别访问。 Azure 存储提供 服务终结点策略 ,允许进一步将服务终结点的使用限制为特定的存储帐户。 还可以利用网络虚拟设备 (NVA) 来执行第 7 层检查和服务终结点的 FQDN 筛选,但此方法附带了额外的性能和缩放注意事项。
服务终结点和专用终结点之间有什么区别?提供有关专用链接终结点与 VNet 服务终结点之间的差异说明。
设计建议
对于支持虚拟网络注入的 Azure PaaS 服务,如果需要通过虚拟网络网关) 访问专用网络 (本地资源,请考虑启用虚拟网络注入功能。 另请注意,注入虚拟网络的这些服务仍通过使用特定于服务的公共 IP 地址来执行管理平面操作。 必须保证连接性才能使服务正常运行。 使用 UDR 和 NSG 在虚拟网络中锁定此通信。 你可以使用 UDR 中的服务标记来减少必要路由的数量并覆盖默认路由(如果使用)。
当数据外泄保护和仅使用专用 IP 寻址是坚定的要求时,请考虑使用Azure 专用链接(如果可用)。
在数据外泄问题较少、专用链接不可用或需要成本优化的大数据引入的情况下,请考虑使用虚拟网络服务终结点来保护从虚拟网络内部访问 Azure PaaS 服务的安全。 (Azure 服务终结点不会产生任何费用,相比之下,Azure 专用链接包括基于每 GB 网络数据) 的成本部分。
如果需要从本地访问 Azure PaaS 服务,请使用以下选项:
- 如果不需要专用访问且本地 Internet 带宽足够,则通过 Internet 和 Microsoft 全球网络使用 PaaS 服务的默认公共终结点。
- 将专用混合连接 (ExpressRoute 与专用对等互连或站点到站点 VPN) 与虚拟网络注入或Azure 专用链接配合使用。
默认情况下,不要在所有子网中启用虚拟网络服务终结点。 根据 PaaS 服务功能可用性以及你自己的性能和安全要求,逐个遵循上述考虑的方法。
尽可能避免使用强制隧道 (通过本地通过本地定向来自 Azure 虚拟网络的 Internet 绑定流量,方法是通过专用混合连接) 播发默认路由,因为这样可能会增加使用某些 Azure PaaS 服务(例如应用程序网关 V2)管理控制平面操作的复杂性。
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈