如何配置 Azure 信息保护的自动和建议分类的条件
在配置标签的条件时,可以自动将标签分配到文档或电子邮件。 或者,可以提示用户选择建议的标签。
配置这些条件时,可使用预定义的模式,如“信用卡号”或“美国社会安全号码 (SSN)”。 或者,你可以定义自定义字符串或模式作为自动分类的条件。 这些条件适用于文档和电子邮件中的正文文本和页眉及页脚。 有关这些条件的详细信息,请参阅以下过程中的步骤 5。
若要获取最佳用户体验并确保业务连续性,我们建议你从用户建议分类开始,而不是自动操作。 此配置使你的用户能够接受分类和任何关联保护,或覆盖这些建议(如果它们不适用于其文档或电子邮件)。
通过自定义策略提示配置条件以将标签应用于建议的操作的示例提示:
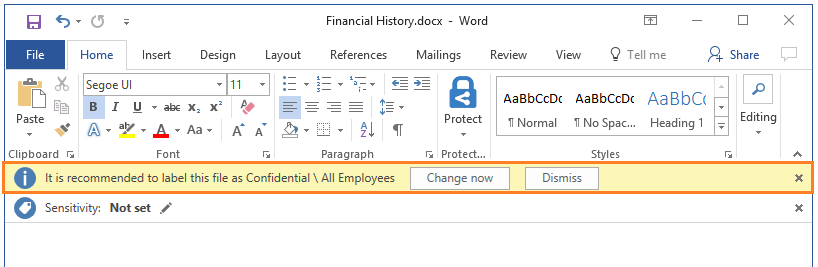
在此示例中,用户可以单击“立即更改”应用建议的标签,或通过选择“消除”来替代该建议。 如果用户选择消除建议并且在下一次打开文档时该条件仍然适用,会再次显示标签建议。
如果配置自动分类(而不是建议分类),系统自动应用标签,并且用户仍会在自己的 Word、Excel 和 PowerPoint 中看到通知。 但是,现在“立即更改”和“消除”按钮都被替换为“确定” 。 在 Outlook 中,自动分类无通知,且发送电子邮件时将应用标签。
重要
请勿为自动分类和用户定义的权限配置标签。 “用户定义的权限”选项是一个保护设置,允许用户指定应向其授予权限的人员。
如果为自动分类和用户定义的权限配置标签,则会检查内容是否符合条件,并且不会应用用户定义的权限设置。 可使用建议的分类和用户定义的权限。
如何应用自动标签或建议的标签
自动分类会应用于 Word、Excel 和 PowerPoint(在保存文档时)和 Outlook(在发送电子邮件时)。
不能将自动分类用于以前已手动标记的或者以前已使用更高分类自动标记的文档和电子邮件。
在保存 Word、Excel 和 PowerPoint 文档时,建议的分类会应用于这些文档。 除非配置当前处于预览阶段的高级客户端设置,否则无法使用建议的 Outlook 分类。
对于之前已设置标签(更高级别的分类标签)的文档,无法使用建议的分类。
可以更改此行为,以便 Azure 信息保护客户端定期检查文档是否符合指定的条件规则。 例如,当你使用 Office 应用的自动保存功能(自动保存 Microsoft SharePoint、OneDrive for Work、OneDrive for School 或 OneDrive for Home 中的文档)时,这种做法就非常合适。 要支持此场景,可以配置高级客户端设置(当前处于预览阶段)。 该设置可启用在后台持续运行的分类。
多条件应用到多个标签时的评估方式
根据在策略中指定的位置,将标签排序以供评估:排在第一的标签具有最低的位置(敏感度最低),排在最后的标签具有最高位置(敏感度最高)。
应用最敏感的标签。
将应用最后一个子标签。
配置标签的建议或自动分类
如果尚未这样做,请打开新的浏览器窗口,登录到 Azure 门户, 然后导航到“Azure 信息保护”窗格。
例如,在资源、服务和文档的搜索框中:开始键入“信息”并选择“Azure 信息保护”。
从“分类”“标签”菜单选项:在“Azure 信息保护 - 标签”窗格上,选择要配置的标签。
在“标签”窗格上的“配置条件以自动应用该标签”部分中,单击“添加新的条件” 。
在“条件”窗格上,选择“信息类型”(如果要使用预定义的条件)或“自定义”(如果要指定自己的条件) :
对于“信息类型”:从可用条件列表中选择,然后选择最小出现次数以及出现计数中是否应具有唯一的值。
信息类型使用 Microsoft 365 数据丢失防护 (DLP) 敏感信息类型和模式检测。 可以从多种常见敏感信息类型中进行选择,其中某些类型特定于不同的区域。 有关详细信息,请参阅 Microsoft 365 文档中的敏感信息类型查找的内容。
可从 Azure 门户选择的信息类型列表会定期更新,以包含任何新的 Office DLP 添加。 但是,该列表不包含作为规则包定义和上传到 Office 365 安全与合规中心的任何自定义敏感信息类型。
重要
某些信息类型需要最低版本的客户端。 详细信息
Azure 信息保护评估你选择的信息类型时,不使用 Office DLP 置信度设置,而是根据最低置信度进行匹配。
对于“自定义”:指定匹配的名称和短语,其必须排除引号和特殊字符。 然后指定是否匹配正则表达式,区分大小写,发生的最小数目以及发生计数中是否应具有唯一的值。
正则表达式使用 Office 365 正则表达式模式。 为帮助你指定自定义条件的正则表达式,请参阅 Boost 的以下特定版本的 Perl 正则表达式语法。 自定义正则表达式必须符合 .NET 文档中所述的内容。 另外,不支持用于指定 Unicode 的 Perl 5 字符转义(形式 \x{####…},其中 ####… 是一系列十六进制数字)。
确定是否需要更改“最小出现次数”和“仅计算唯一值的出现次数”,然后选择“保存”。
出现次数选项示例:选择社会安全号码的信息类型并将最小出现次数设置为 2,并且文档已两次列出同一社会安全号码:如果将“仅计算唯一值的出现次数”设置为“开”,则不符合条件。 如果将此选项设置为“关闭”,则满足条件。
返回“标签”窗格,配置以下内容,然后单击“保存” :
选择自动或建议的分类:对于选择如何应用该标签:自动或向用户建议,选择“自动”或“建议”。
指定用户提示或策略提示文本:保持默认文本或指定你自己的字符串。
单击“保存”时,更改将会自动提供给用户和服务。 不再提供单独发布选项。
需要最低版本客户端的敏感信息类型
以下敏感信息类型需要使用版本最低为 1.48.204.0 的 Azure 信息保护客户端:
- Azure 服务总线连接字符串
- Azure IoT 连接字符串
- Azure 存储帐户
- Azure IAAS 数据库连接字符串和 Azure SQL 连接字符串
- Azure Redis 缓存连接字符串
- Azure SAS
- SQL Server 连接字符串
- Azure DocumentDB 身份验证密钥
- Azure 发布设置密码
- Azure 存储帐户密钥(通用)
有关这些敏感信息类型的详细信息,请参阅以下博客文章:Azure 信息保护通过自动发现凭据来帮助你提高安全性
此外,从 1.48.204.0 版本的 Azure 信息保护客户端开始,以下敏感信息类型不受支持且不再显示在 Azure 门户中。 如果你有使用这些敏感信息类型的标签,建议删除它们,因为我们无法保证能对它们进行正确的检测,并且应在扫描程序报告中忽略对它们的任何引用:
- 欧盟电话号码
- 欧盟 GPS 坐标
后续步骤
请考虑部署 Azure 信息保护扫描程序,它可使用自动分类规则发现和保护网络共享和本地文件存储中的文件并对其进行分类。
有关配置 Azure 信息保护策略的详细信息,请使用配置组织的策略部分中的链接。