你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
如何为 Azure VPN 网关配置 BGP:CLI
本文介绍如何使用 Azure CLI 在跨界站点到站点 (S2S) VPN 连接和 VNet 到 VNet 连接上启用 BGP。 还可以使用 Azure 门户或 PowerShell 步骤创建此配置。
BGP 是通常在 Internet 上使用的,用于在两个或更多网络之间交换路由和可访问性信息的标准路由协议。 BGP 允许 Azure VPN 网关和本地 VPN 设备(称为 BGP 对等节点或邻居)交换“路由”,这些路由将通知这两个网关这些前缀的可用性和可访问性,以便这些前缀可通过涉及的网关或路由器。 BGP 还可以通过将 BGP 网关从一个 BGP 对等节点获知的路由传播到所有其他 BGP 对等节点来允许在多个网络之间传输路由。
若要详细了解 BGP 优点,以及了解使用 BGP 的技术要求和注意事项,请参阅关于 BGP 和 Azure VPN 网关。
本文帮助你在网络连接中启用 BGP,其中的每一部分都是一个基本构建基块。 如果已完成所有三个部分(在网关上配置 BGP、S2S 连接和 VNet 到 VNet 连接),请如图 1 所示生成拓扑。
图示 1
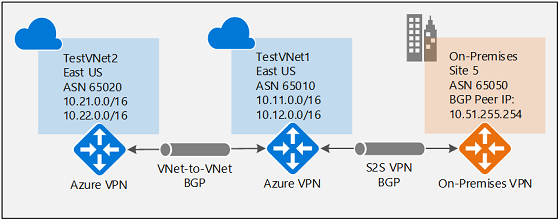
可将这些部分组合在一起,生成更复杂的多跃点传输网络来满足需求。
先决条件
在 Azure Cloud Shell 中使用 Bash 环境。 有关详细信息,请参阅 Azure Cloud Shell 中的 Bash 快速入门。
如需在本地运行 CLI 参考命令,请安装 Azure CLI。 如果在 Windows 或 macOS 上运行,请考虑在 Docker 容器中运行 Azure CLI。 有关详细信息,请参阅如何在 Docker 容器中运行 Azure CLI。
如果使用的是本地安装,请使用 az login 命令登录到 Azure CLI。 若要完成身份验证过程,请遵循终端中显示的步骤。 有关其他登录选项,请参阅使用 Azure CLI 登录。
出现提示时,请在首次使用时安装 Azure CLI 扩展。 有关扩展详细信息,请参阅使用 Azure CLI 的扩展。
运行 az version 以查找安装的版本和依赖库。 若要升级到最新版本,请运行 az upgrade。
为 VPN 网关启用 BGP
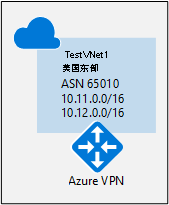
需要先完成此部分,才可执行另外两个配置部分中的任何步骤。 以下配置步骤设置 Azure VPN 网关的 BGP 参数,如图 2 中所示。
图示 2
创建并配置 TestVNet1
1. 创建资源组
以下示例在“eastus”位置创建名为 TestRG1 的资源组。 如果在想要创建虚拟网络的区域中已经有了一个资源组,则可改用该资源组。
az group create --name TestRG1 --location eastus
2. 创建 TestVNet1
以下示例创建一个名为 TestVNet1 的虚拟网络和三个子网:GatewaySubnet、FrontEnd 和 Backend。 替换值时,请务必始终将网关子网特意命名为 GatewaySubnet。 如果命名为其他名称,网关创建会失败。
第一个命令创建前端地址空间和 FrontEnd 子网。 第二个命令为后端子网创建额外的地址空间。 第三个和第四个命令创建 BackEnd 子网和 GatewaySubnet。
az network vnet create -n TestVNet1 -g TestRG1 --address-prefix 10.11.0.0/16 --subnet-name FrontEnd --subnet-prefix 10.11.0.0/24
az network vnet update -n TestVNet1 --address-prefixes 10.11.0.0/16 10.12.0.0/16 -g TestRG1
az network vnet subnet create --vnet-name TestVNet1 -n BackEnd -g TestRG1 --address-prefix 10.12.0.0/24
az network vnet subnet create --vnet-name TestVNet1 -n GatewaySubnet -g TestRG1 --address-prefix 10.12.255.0/27
使用 BGP 参数为 TestVNet1 创建 VPN 网关
1. 创建公共 IP 地址
请求公共 IP 地址。 将向为虚拟网络创建的 VPN 网关分配公共 IP 地址。
az network public-ip create -n GWPubIP -g TestRG1 --allocation-method Dynamic
2.使用 AS 编号创建 VPN 网关
为 TestVNet1 创建虚拟网络网关。 BGP 需要基于路由的 VPN 网关。 此外,还需要额外的参数 -Asn,为 TestVNet1 设置自治系统编号 (ASN)。 创建网关通常需要 45 分钟或更长的时间,具体取决于所选的网关 SKU。
如果使用 --no-wait 参数运行该命令,则不会显示任何反馈或输出。 --no-wait 参数允许在后台创建网关。 但并不意味着 VPN 网关会立即创建。
az network vnet-gateway create -n VNet1GW -l eastus --public-ip-address GWPubIP -g TestRG1 --vnet TestVNet1 --gateway-type Vpn --sku HighPerformance --vpn-type RouteBased --asn 65010 --no-wait
创建网关后,可以使用此网关通过 BGP 建立跨界连接或 VNet 到 VNet 连接。
3. 获取 Azure BGP 对等节点 IP 地址
创建网关后,需要在 Azure VPN 网关上获取 BGP 对等节点 IP 地址。 需要此地址才能将 VPN 网关配置为本地 VPN 设备的 BGP 对等节点。
运行以下命令。
az network vnet-gateway list -g TestRG1
记下显示在输出顶部的 bgpSettings 部分。 稍后你要使用此部分
"bgpSettings": {
"asn": 65010,
"bgpPeeringAddress": "10.12.255.30",
"peerWeight": 0
}
如果未看到作为 IP 地址显示的 BgpPeeringAddress,则表示网关仍在配置。 请在网关配置完成后重试。
使用 BGP 建立跨界连接
要建立跨界连接,需要创建本地网关来表示本地 VPN 设备。 然后将 Azure VPN 网关与本地网关连接在一起。 虽然这些步骤与创建其他连接的步骤类似,但它们包括指定 BGP 配置参数所需的其他属性,如图 3 中所示。
图示 3

创建和配置本地网关
此练习将继续生成图中所示的配置。 请务必将值替换为要用于配置的值。 使用本地网络网关时,请记住以下事项:
- 本地网关可以与 VPN 网关在相同的位置和资源组中,也可以在不同的位置和资源组中。 此示例演示网关在不同位置的不同资源组中。
- 需要为本地网关声明的最小前缀是 VPN 设备上的 BGP 对等节点 IP 地址中的主机地址。 在此示例中,它是“10.51.255.254/32”中的 /32 前缀。
- 提醒一下,在本地网络与 Azure 虚拟网络之间必须使用不同的 BGP ASN。 如果它们是相同的,则需要更改 VNet ASN(如果本地 VPN 设备已使用该 ASN 与其他 BGP 邻居对等)。
在继续操作之前,请确保已完成本练习的为 VPN 网关启用 BGP 部分。 请注意,在此示例中会创建新的资源组。 另请注意,本地网关的两个附加参数:Asn 和 BgpPeerAddress。
az group create -n TestRG5 -l westus
az network local-gateway create --gateway-ip-address 23.99.221.164 -n Site5 -g TestRG5 --local-address-prefixes 10.51.255.254/32 --asn 65050 --bgp-peering-address 10.51.255.254
连接 VNet 网关和本地网关
在此步骤中,创建从 TestVNet1 到 Site5 的连接。 必须指定 --enable-bgp 参数,以便为此连接启用 BGP。
在此示例中,虚拟网关和本地网关位于不同的资源组中。 网关位于不同的资源组中时,必须指定两个网关的整个资源 ID,以便在虚拟网络之间建立连接。
1. 获取 VNet1GW 的资源 ID
使用以下命令的输出,获取 VNet1GW 的资源 ID:
az network vnet-gateway show -n VNet1GW -g TestRG1
在输出中,找到 "id": 行。 引号中的值是在下一部分创建连接所必需的。
示例输出:
{
"activeActive": false,
"bgpSettings": {
"asn": 65010,
"bgpPeeringAddress": "10.12.255.30",
"peerWeight": 0
},
"enableBgp": true,
"etag": "W/\"<your etag number>\"",
"gatewayDefaultSite": null,
"gatewayType": "Vpn",
"id": "/subscriptions/<subscription ID>/resourceGroups/TestRG1/providers/Microsoft.Network/virtualNetworkGateways/VNet1GW",
将 "id": 后的值复制到文本编辑器(例如记事本),这样就可以在创建连接时轻松粘贴它们。
"id": "/subscriptions/<subscription ID>/resourceGroups/TestRG1/providers/Microsoft.Network/virtualNetworkGateways/VNet1GW"
2. 获取 Site5 的资源 ID
使用以下命令,从输出中获取 Site5 的资源 ID:
az network local-gateway show -n Site5 -g TestRG5
3. 创建 TestVNet1 到 Site5 的连接
在此步骤中,创建从 TestVNet1 到 Site5 的连接。 如前所述,同一 Azure VPN 网关可以同时具有 BGP 连接和非 BGP 连接。 除非在连接属性中启用了 BGP,否则 Azure 不会为此连接启用 BGP,即使已在这两个网关上配置了 BGP 参数。 将该订阅 ID 替换为自己的订阅 ID。
az network vpn-connection create -n VNet1ToSite5 -g TestRG1 --vnet-gateway1 /subscriptions/<subscription ID>/resourceGroups/TestRG1/providers/Microsoft.Network/virtualNetworkGateways/VNet1GW --enable-bgp -l eastus --shared-key "abc123" --local-gateway2 /subscriptions/<subscription ID>/resourceGroups/TestRG5/providers/Microsoft.Network/localNetworkGateways/Site5
本地设备配置
下面的示例列出了可在本地 VPN 设备上的 BGP 配置节中为此练习输入的参数:
- Site5 ASN : 65050
- Site5 BGP IP : 10.51.255.254
- Prefixes to announce : (for example) 10.51.0.0/16
- Azure VNet ASN : 65010
- Azure VNet BGP IP : 10.12.255.30
- Static route : Add a route for 10.12.255.30/32, with nexthop being the VPN tunnel interface on your device
- eBGP Multihop : Ensure the "multihop" option for eBGP is enabled on your device if needed
几分钟后,应会建立连接。 建立 IPsec 连接后,可开始 BGP 对等会话。
使用 BGP 建立 VNet 到 VNet 连接
此部分将添加使用 BGP 的 VNet 到 VNet 连接,如图 4 中所示。
图示 4

以下说明延续前面各部分中的步骤。 必须完成为 VPN 网关启用 BGP 部分,才能使用 BGP 创建和配置 TestVNet1 和 VPN 网关。
创建 TestVNet2 和 VPN 网关
必须确保新虚拟网络的 IP 地址空间 TestVNet2 不与任何 VNet 范围重叠。
在本示例中,虚拟网络属于同一订阅。 可在不同订阅之间设置 VNet 到 VNet 连接。 若要了解详细信息,请参阅配置 VNet 到 VNet 的连接。 请确保在创建连接时添加 -EnableBgp $True,以启用 BGP。
1. 创建新的资源组
az group create -n TestRG2 -l eastus
2.在新资源组中创建 TestVNet2
第一个命令创建前端地址空间和 FrontEnd 子网。 第二个命令为后端子网创建额外的地址空间。 第三个和第四个命令创建 BackEnd 子网和 GatewaySubnet。
az network vnet create -n TestVNet2 -g TestRG2 --address-prefix 10.21.0.0/16 --subnet-name FrontEnd --subnet-prefix 10.21.0.0/24
az network vnet update -n TestVNet2 --address-prefixes 10.21.0.0/16 10.22.0.0/16 -g TestRG2
az network vnet subnet create --vnet-name TestVNet2 -n BackEnd -g TestRG2 --address-prefix 10.22.0.0/24
az network vnet subnet create --vnet-name TestVNet2 -n GatewaySubnet -g TestRG2 --address-prefix 10.22.255.0/27
3. 创建公共 IP 地址
请求公共 IP 地址。 将向为虚拟网络创建的 VPN 网关分配公共 IP 地址。
az network public-ip create -n GWPubIP2 -g TestRG2 --allocation-method Dynamic
4. 使用 AS 编号创建 VPN 网关
为 TestVNet2 创建虚拟网络网关。 必须覆盖 Azure VPN 网关上的默认 ASN。 连接的虚拟网络的 ASN 必须不同,才能启用 BGP 和传输路由。
az network vnet-gateway create -n VNet2GW -l eastus --public-ip-address GWPubIP2 -g TestRG2 --vnet TestVNet2 --gateway-type Vpn --sku Standard --vpn-type RouteBased --asn 65020 --no-wait
连接 TestVNet1 和 TestVNet2 网关
在此步骤中,创建从 TestVNet1 到 Site5 的连接。 必须指定 --enable-bgp 参数,以便为此连接启用 BGP。
在以下示例中,虚拟网关和本地网关位于不同的资源组中。 网关位于不同的资源组中时,必须指定两个网关的整个资源 ID,以便在虚拟网络之间建立连接。
1. 获取 VNet1GW 的资源 ID
从以下命令的输出中获取 VNet1GW 的资源 ID:
az network vnet-gateway show -n VNet1GW -g TestRG1
网关资源的示例值:
"/subscriptions/<subscripion ID value>/resourceGroups/TestRG2/providers/Microsoft.Network/virtualNetworkGateways/VNet2GW"
2. 获取 VNet2GW 的资源 ID
从以下命令的输出中获取 VNet2GW 的资源 ID:
az network vnet-gateway show -n VNet2GW -g TestRG2
3. 创建连接
创建从 TestVNet1 到 TestVNet2 的连接,以及从 TestVNet2 到 TestVNet1 的连接。 这些命令使用资源 ID。 对于本练习,示例中已包含资源 ID 的大多数组成部分。 请务必将订阅 ID 值替换为你自己的值。 订阅 ID 在同一命令中的多个位置使用。 在生产环境中使用此命令时,将替换要引用的每个对象的整个资源 ID。
az network vpn-connection create -n VNet1ToVNet2 -g TestRG1 --vnet-gateway1 /subscriptions/<subscription ID>/resourceGroups/TestRG1/providers/Microsoft.Network/virtualNetworkGateways/VNet1GW --enable-bgp -l eastus --shared-key "abc123" --vnet-gateway2 /subscriptions/<subscription ID>/resourceGroups/TestRG2/providers/Microsoft.Network/virtualNetworkGateways/VNet2GW
az network vpn-connection create -n VNet2ToVNet1 -g TestRG2 --vnet-gateway1 /subscriptions/<subscription ID>/resourceGroups/TestRG2/providers/Microsoft.Network/virtualNetworkGateways/VNet2GW --enable-bgp -l eastus --shared-key "abc123" --vnet-gateway2 /subscriptions/<subscription ID>/resourceGroups/TestRG1/providers/Microsoft.Network/virtualNetworkGateways/VNet1GW
重要
为这两个连接启用 BGP。
完成这些步骤后,可在几分钟内建立连接。 完成 VNet 到 VNet 的连接后,BGP 对等会话即可运行。
后续步骤
有关 BGP 的详细信息,请参阅关于 BGP 和 VPN 网关。