集成 Microsoft Purview 信息保护
Microsoft Defender for Cloud Apps 允许从 Microsoft Purview 信息保护自动应用敏感度标签。 这些标签作为文件策略治理操作应用于文件,根据标签配置,可以应用加密以获得额外保护。 此外还可以通过在 Defender for Cloud Apps 门户中筛选应用的敏感度标签来调查文件。 使用标签可以加强对云中敏感数据的可见性和控制力。 将 Microsoft Purview 信息保护与 Defender for Cloud Apps 集成非常简单,只需要选中一个复选框。
将 Microsoft Purview 信息保护集成到 Defender for Cloud Apps 中后,用户可以充分利用云中的服务和安全文件,包括:
- 能够将敏感度标签作为治理操作应用于符合特定策略的文件
- 能够在一个中心位置查看所有分类文件
- 能够根据分类级别开展调查,并量化云应用程序中敏感数据的公开
- 能够创建策略以确保正确处理分类文件
先决条件
注意
必须有 Defender for Cloud Apps 许可证和 Azure 信息保护高级版 P1 许可证,才能启用此功能。 只要这两个许可证就位,Defender for Cloud Apps 就会从 Azure 信息保护服务同步组织标签。
- 要使用 Microsoft Purview 信息保护集成,则必须启用 Microsoft 365 的应用连接器。
Defender for Cloud Apps 若要应用敏感度标签,则必须在 Microsoft Purview 合规门户中将其作为敏感度标签策略的一部分发布。
Defender for Cloud Apps 目前支持对以下文件类型应用来自 Microsoft Purview 信息保护的敏感度标签:
- Word:docm、docx、dotm、dotx
- Excel:xlam、xlsm、xlsx、xltx
- PowerPoint:potm、potx、ppsx、ppsm、pptm、pptx
- PDF
注意
对于 PDF,必须使用统一的标签。
此功能目前适用于存储在 Box、Google Workspace、SharePoint Online 和 OneDrive for Business 中的文件。 未来的版本将支持更多的云应用。
工作原理
可以在 Defender for Cloud Apps 中查看 Microsoft Purview 信息保护中的敏感度标签。 将 Defender for Cloud Apps 与 Microsoft Purview 信息保护集成后,Defender for Cloud Apps 会立即扫描文件,如下所示:
Defender for Cloud Apps 检索租户中使用的所有敏感度标签的列表。 每隔一小时执行一次此操作,使列表保持最新。
然后,Defender for Cloud Apps 扫描文件中的敏感度标签,如下所示:
- 如果启用了自动扫描,则会将所有新建或修改的文件添加到扫描队列,并对所有现有文件和存储库进行扫描。
- 如果将文件策略设置为搜索敏感度标签,这些文件会被添加到敏感度标签的扫描队列。
如前所述,这些扫描是针对初次扫描中发现的敏感度标签,Defender for Cloud Apps 执行此次扫描以查看租户中所使用的敏感度标签。 租户外部的人员设置的外部标签和分类标签添加到分类标签的列表中。 如果不想扫描这些数据,请选择“仅从此租户扫描文件的 Microsoft Purview 信息保护中的敏感度标签和内容检查警告”复选框。
在 Defender for Cloud Apps 上启用 Microsoft Purview 信息保护后,添加到已连接云应用的所有新文件都将进行扫描以查找敏感度标签。
可以在 Defender for Cloud Apps 中创建新策略,以自动应用敏感度标签。
集成限制
将 Microsoft Purview 标签与 Defender for Cloud Apps 配合使用时,请注意以下限制。
| 限制 | 说明 |
|---|---|
| 在 Defender for Cloud Apps 外部应用了标签或保护的文件 | 在 Defender for Cloud Apps 外应用的未受保护的标签可由 Defender for Cloud Apps 重写,但无法移除。 Defender for Cloud Apps 无法从在 Defender for Cloud Apps 外部标记的文件中移除具有保护的标签。 若要扫描在 Defender for Cloud Apps 外部应用保护的文件,请授予检查受保护文件的内容的权限。 |
| Defender for Cloud Apps 标记的文件 | Defender for Cloud Apps 不会覆盖 Defender for Cloud Apps 已标记的文件上的标签。 |
| 受密码保护的文件 | Defender for Cloud Apps 无法读取受密码保护文件上的标签。 |
| 空文件 | Defender for Cloud Apps 不会标记空文件。 |
| 需要检出的库 | Defender for Cloud Apps 不支持标记库中已配置为需要检出的文件。 |
| 范围要求 | 为了使 Defender for Cloud Apps 能够识别敏感度标签,必须至少为文件和电子邮件配置 Purview 中的标签范围。 |
注意
Microsoft Purview 是 Microsoft 用于标记服务的主要解决方案。 有关详细信息,请参阅 Microsoft Purview 文档。
如何将 Microsoft Purview 信息保护与 Defender for Cloud Apps 集成
启用 Microsoft Purview 信息保护
将 Microsoft Purview 信息保护与 Defender for Cloud Apps 集成只需要选中一个复选框。 通过启用自动扫描,可以在 Microsoft 365 文件上搜索 Microsoft Purview 信息保护中的敏感度标签,且无需创建策略。 启用后,如果已使用 Microsoft Purview 信息保护中的敏感度标签标记云环境中的文件,在 Defender for Cloud Apps 中会看到这些文件。
若要启用 Defender for Cloud Apps 以扫描已为敏感度标签启用内容检查的文件,请执行以下操作:
在 Microsoft Defender 门户中,选择“设置”。 然后选择“云应用”。 然后转到“信息保护” ->“Microsoft 信息保护”。
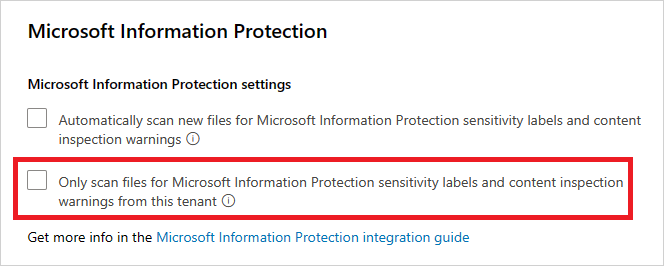
在“Microsoft 信息保护”设置下,选择“自动扫描新文件中的来自 Microsoft Purview 信息保护和内容检查警告的敏感度标签”。

启用 Microsoft Purview 信息保护后,在 Defender for Cloud Apps 中便能够看到具有敏感度标签的文件并且可以根据标签进行筛选。 Defender for Cloud Apps 连接到云应用后,可以使用 Microsoft Purview 信息保护集成功能,以便在 Defender for Cloud Apps 门户中应用 Microsoft Purview 信息保护中的敏感度标签(无论是否加密),方法是将这些标签直接添加到文件或配置以治理操作的形式自动应用敏感度标签的文件策略。
注意
自动扫描不会扫描现有文件,除非它们重新经过修改。 若要扫描现有文件的 Microsoft Purview 信息保护敏感度标签,必须至少有一个包含内容检查的“文件策略”。 如果没有,请创建新的“文件策略”,删除所有预设筛选器,在“检查方法”下选择“内置 DLP”。 在“内容检查”字段中,选择“包括匹配预设表达式的文件”,并选择任何预定义的值,再保存该策略。 这会启用内容检查,此功能可自动检测 Microsoft Purview 信息保护中的敏感度标签。
设置内部和外部标签
Defender for Cloud Apps 默认扫描组织中定义的敏感度标签,以及其他组织定义的外部敏感度标签。
若要忽略组织外部设置的敏感度标签,请转到 Microsoft Defender 门户并选择“设置”。 然后选择“云应用”。 在“信息保护”下,选择“Microsoft Purview 信息保护”。 然后选择“仅从此租户扫描文件的 Microsoft Purview 信息保护中的敏感度标签和内容检查警告”。
将标签直接应用于文件
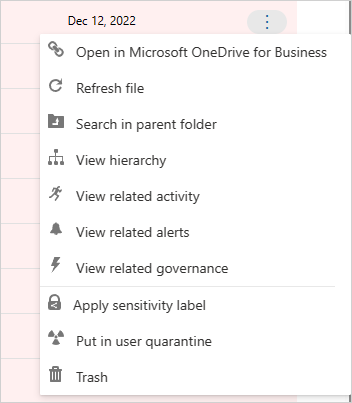
在 Microsoft Defender 门户的“云应用”下,选择“文件”。 然后,选择要保护的文件。 选择文件行末尾的三个点,然后选择“应用敏感度标签”。
注意
Defender for Cloud Apps 可以对最大 30 MB 的文件应用 Microsoft Purview 信息保护。
选择要应用于该文件的组织敏感度标签之一,然后选择“应用”。

选择敏感度标签并选择“应用”后,Defender for Cloud Apps 会将敏感度标签应用于原始文件。
此外还可以通过选择“移除敏感度标签”选项来移除敏感度标签。
有关 Defender for Cloud Apps 和 Microsoft Purview 信息保护如何协同工作的详细信息,请参阅从 Microsoft Purview 信息保护自动应用敏感度标签。
自动对文件添加标签
通过创建文件策略并设置“应用敏感度标签”作为治理操作,可自动对文件应用敏感度标签。
按照以下说明创建文件策略:
创建文件策略。
设置策略以包含要检测的文件类型。 例如,选择“访问级别”不等于“内部”并且“所有者 OU”等于“财务团队”的所有文件。
在相关应用的治理操作下,选择“应用敏感度标签”,然后选择标签类型。

注意
- 能够应用敏感度标签是一项强大的功能。 为了防止客户将标签错误应用到大量文件,作为安全预防措施,每个应用程序每个租户对应的“应用标签”操作的每日限制数为 100。 在达到每日限制后,应用标签操作会暂停,并在第二天(12:00 UTC 过后)自动继续。
- 禁用策略后,该策略的所有挂起标记任务都会暂停。
- 在标签配置中,必须将权限分配给任何经过身份验证的用户或组织中的所有用户,Defender for Cloud Apps 才能读取标签信息。
控制文件公开
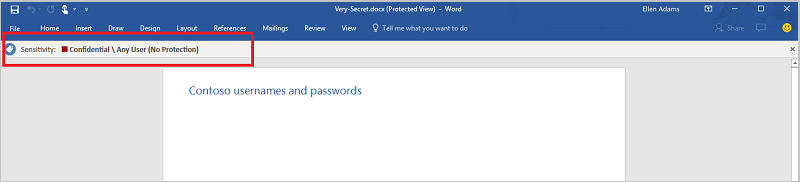
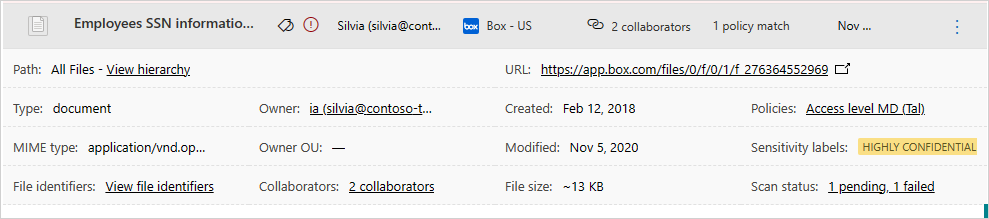
例如,假设使用 Microsoft Purview 信息保护敏感度标签标记了以下文档:
可以在 Defender for Cloud Apps 中查看本文档,方法是在“文件”页中筛选 Microsoft Purview 信息保护的敏感度标签。
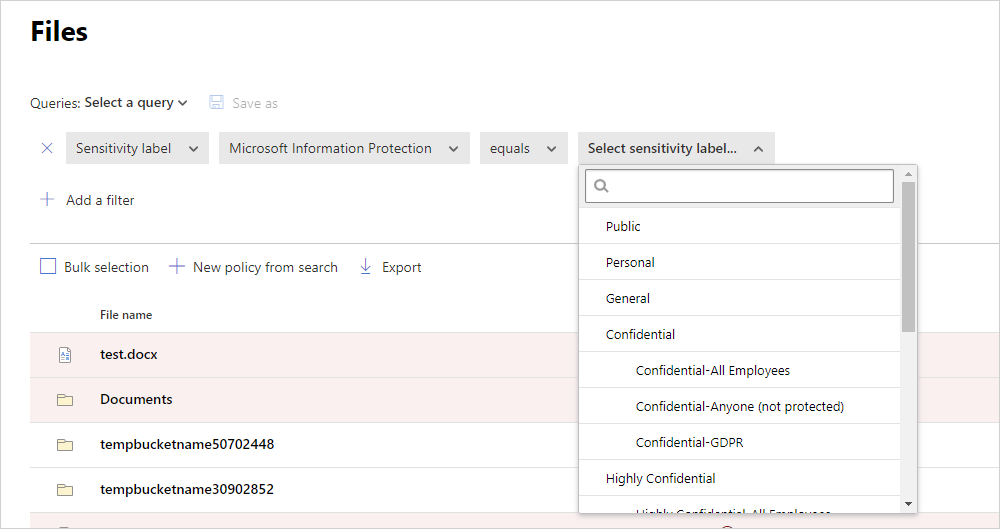
在文件抽屉中,可以获取有关这些文件及其敏感度标签的详细信息。 只需在“文件”页中选择相关文件,然后查看其是否具有敏感度标签。
然后,可以在 Defender for Cloud Apps 中创建文件策略,以控制不恰当共享的文件和查找已标记的并且最近修改的文件。
- 可以创建策略,使敏感度标签自动应用于特定文件。
- 还可以对与文件分类相关的活动触发警报。
注意
在文件中禁用敏感度标签时,禁用的标签在 Defender for Cloud Apps 中会显示为已禁用。 已删除的标签不会显示。
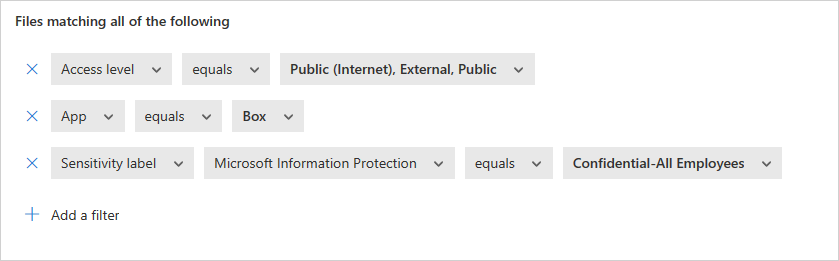
示例策略 - 在 Box 上外部共享的机密数据:
创建文件策略。
设置策略的名称、严重性和类别。
添加以下筛选器以查找在 Box 上外部共享的所有机密数据:
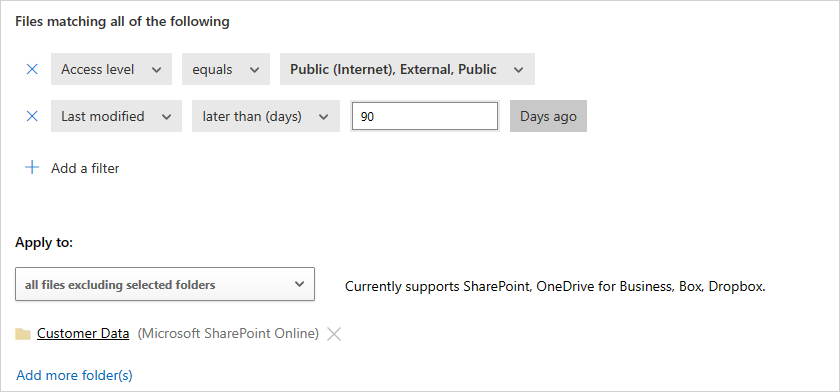
示例策略 - 在 SharePoint 上的 Customer Data 文件夹外最近修改的受限数据:
创建文件策略。
设置策略的名称、严重性和类别。
添加以下筛选器以查找最近修改的所有受限文件,同时在“文件夹选择”选项中排除 Customer Data 文件夹:
还可选择设置警报、用户通知或立即执行这些策略。 了解有关治理操作的详细信息。
详细了解 Microsoft Purview 信息保护。
后续步骤
如果遇到任何问题,我们可以提供帮助。 要获取产品问题的帮助或支持,请开立支持票证。