Configuration Manager基于角色的管理基础知识
适用于: Configuration Manager(current branch)
使用 Configuration Manager,可以使用基于角色的管理来保护管理用户使用Configuration Manager所需的访问权限。 还可以保护对所管理的对象(如集合、部署和站点)的访问。
基于角色的管理模型集中定义和管理层次结构范围的安全访问。 此模型适用于所有站点和站点设置,方法是使用以下项:
安全角色分配给管理用户,以授予他们Configuration Manager对象的权限。 例如,创建或更改客户端设置的权限。
安全范围 用于对管理用户负责管理的对象的特定实例进行分组。 例如,安装 Configuration Manager 控制台的应用程序。
集合用于指定管理用户可以在Configuration Manager中管理的用户组和设备组。
通过角色、范围和集合的组合,可以隔离满足组织要求的管理分配。 它们一起使用,可定义用户的 管理范围 。 此管理范围控制管理用户在 Configuration Manager 控制台中查看的对象,并控制用户对这些对象拥有的权限。
优点
以下各项是Configuration Manager中基于角色的管理的优势:
网站不用作管理边界。 换句话说,不要将独立主站点扩展到具有管理中心站点的层次结构,以分隔管理用户。
为层次结构创建管理用户,只需为其分配一次安全性。
所有安全分配都会在整个层次结构中复制并可用。 基于角色的管理配置作为全局数据复制到层次结构中的每个站点,然后应用于所有管理连接。
重要
站点间复制延迟可能会阻止站点接收基于角色的管理的更改。 有关如何监视站点间数据库复制的详细信息,请参阅 站点之间的数据传输。
有一些内置安全角色用于分配典型的管理任务。 创建自己的自定义安全角色以支持特定的业务要求。
管理用户仅看到他们有权管理的对象。
可以审核管理安全操作。
安全角色
使用安全角色向管理用户授予安全权限。 安全角色是分配给管理用户的安全权限组,以便他们可以执行其管理任务。 这些安全权限定义管理用户可以执行的操作以及为特定对象类型授予的权限。 作为安全最佳做法,请分配提供任务所需的最低权限的安全角色。
Configuration Manager具有多个内置安全角色,以支持管理任务的典型分组。 可以创建自己的自定义安全角色来支持特定的业务需求。
下表汇总了所有内置角色:
| 名称 | 说明 |
|---|---|
| 应用程序管理员 | 合并 应用程序部署管理器 和 应用程序作者 角色的权限。 具有此角色的管理用户还可以管理查询、查看站点设置、管理集合、编辑用户设备相关性设置以及管理 App-V 虚拟环境。 |
| 应用程序作者 | 可以创建、修改和停用应用程序。 具有此角色的管理用户还可以管理应用程序、包和 App-V 虚拟环境。 |
| 应用程序部署管理器 | 可以部署应用程序。 具有此角色的管理用户可以查看应用程序列表。 他们可以管理应用程序、警报和包的部署。 他们可以查看集合及其成员、状态消息、查询、条件传递规则和 App-V 虚拟环境。 |
| 资产管理器 | 授予管理资产智能同步点、资产智能报告类、软件清单、硬件清单和计量规则的权限。 |
| 公司资源访问管理器 | 授予创建、管理和部署公司资源访问配置文件的权限。 例如,Wi-Fi、VPN、Exchange ActiveSync电子邮件和证书配置文件。 |
| 合规性设置管理器 | 授予定义和监视符合性设置的权限。 具有此角色的管理用户可以创建、修改和删除配置项目和基线。 他们还可以将配置基线部署到集合、启动符合性评估,并开始对不符合的计算机进行修正。 |
| Endpoint Protection Manager | 授予创建、修改和删除终结点保护策略的权限。 他们可以将这些策略部署到集合、创建和修改警报,以及监视终结点保护状态。 |
| 完全管理员 | 授予 Configuration Manager 中的所有权限。 安装 Configuration Manager 的管理用户会自动获得此安全角色、所有作用域和所有集合的授权。 |
| 基础结构管理员 | 授予创建、删除和修改Configuration Manager服务器基础结构以及运行迁移任务的权限。 |
| 操作系统部署管理器 | 授予创建 OS 映像并将其部署到计算机、管理 OS 升级包和映像、任务序列、驱动程序、启动映像和状态迁移设置的权限。 |
| 操作管理员 | 授予Configuration Manager中所有操作的权限,但管理安全性的权限除外。 此角色无法管理管理用户、安全角色和安全作用域。 |
| 只读分析师 | 授予查看所有Configuration Manager对象的权限。 |
| 远程工具操作员 | 授予运行和审核帮助用户解决计算机问题的远程管理工具的权限。 具有此角色的管理用户可以从 Configuration Manager 控制台运行远程控制、远程协助和远程桌面。 |
| 安全管理员 | 授予添加和删除管理用户以及将管理用户与安全角色、集合和安全范围关联的权限。 具有此角色的管理用户还可以创建、修改和删除安全角色及其分配的安全范围和集合。 |
| 软件更新管理器 | 授予定义和部署软件更新的权限。 此角色中的管理用户可以管理软件更新组、部署和部署模板。 |
提示
如果你有权限,则可以在Configuration Manager控制台中查看所有安全角色的列表。 若要查看角色,请转到 “管理 ”工作区,展开“ 安全性”,然后选择“ 安全角色” 节点。
除了添加管理用户之外,不能修改内置安全角色。 可以复制角色、进行更改,然后将这些更改保存为新的自定义安全角色。 还可以导入已从其他层次结构(例如实验室环境)导出的安全角色。 有关详细信息,请参阅 配置基于角色的管理。
查看安全角色及其权限,以确定是要使用内置安全角色,还是必须创建自己的自定义安全角色。
角色权限
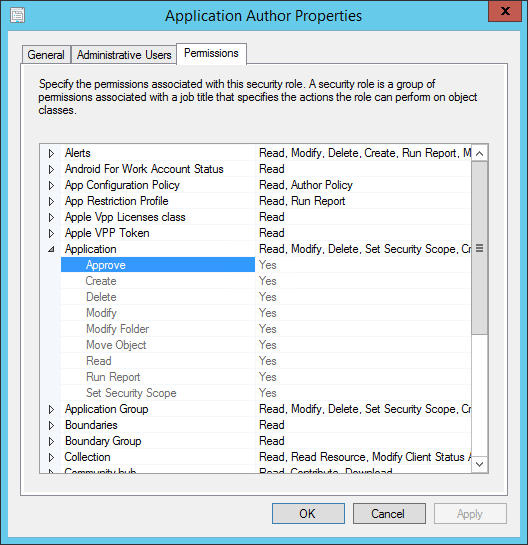
每个安全角色对不同的对象类型具有特定权限。 例如, 应用程序作者 角色对 应用程序具有以下权限:
- 批准
- 创建
- 删除
- 修改
- 修改文件夹
- 移动对象
- 读取
- 运行报表
- 设置安全范围
此角色还具有其他对象的权限。
有关如何查看角色的权限或更改自定义角色的权限的详细信息,请参阅 配置基于角色的管理。
规划安全角色
使用此过程来规划环境中Configuration Manager安全角色:
确定管理用户需要在Configuration Manager中执行的任务。 这些任务可能与一组或多组管理任务相关。 例如,部署符合性的操作系统和设置。
将这些管理任务映射到一个或多个内置角色。
如果某些管理用户执行多个角色的任务,请将用户分配到多个角色。 不要创建合并权限的自定义角色。
如果标识的任务未映射到内置安全角色,请创建并测试自定义角色。
有关详细信息,请参阅 创建自定义安全角色 和 配置安全角色。
集合
集合指定管理用户可以查看或管理的用户和设备。 例如,若要将应用程序部署到设备,管理用户需要具有授予对包含该设备的集合的访问权限的安全角色。
有关集合的详细信息,请参阅 集合简介。
在配置基于角色的管理之前,请确定是否必须出于以下任何原因创建新集合:
- 职能组织。 例如,服务器和工作站的单独集合。
- 地理对齐。 例如,北美和欧洲的单独集合。
- 安全要求和业务流程。 例如,生产计算机和测试计算机的单独集合。
- 组织一致性。 例如,每个业务部门的单独集合。
有关详细信息,请参阅 配置集合以管理安全性。
安全范围
使用安全作用域为管理用户提供对安全对象的访问权限。 安全作用域是一组命名的安全对象,这些对象作为组分配给管理员用户。 所有安全对象都分配给一个或多个安全作用域。 Configuration Manager有两个内置安全作用域:
全部:授予对所有范围的访问权限。 无法将对象分配给此安全范围。
默认值:默认情况下,此范围用于所有对象。 安装 Configuration Manager 时,会将所有对象分配给此安全范围。
如果要限制管理用户可以查看和管理的对象,请创建自己的自定义安全作用域。 安全范围不支持分层结构,并且无法嵌套。 安全作用域可以包含一个或多个对象类型,其中包括以下项:
- 警报订阅
- 应用程序和应用程序组
- App-V 虚拟环境
- 启动映像
- 边界组
- 配置项目和基线
- 自定义客户端设置
- 分发点和分发点组
- 驱动程序包
- 终结点保护策略 (所有)
- 文件夹
- 全局条件
- 迁移作业
- OneDrive for Business配置文件
- OS 映像
- OS 升级包
- 包
- 查询
- 远程连接配置文件
- 脚本
- 网站
- 软件计数规则
- 软件更新组
- 软件更新包
- 任务序列
- 用户数据和配置文件配置项目
- 适用于企业的 Windows 更新 策略
还有一些对象不能包含在安全作用域中,因为它们仅由安全角色保护。 对这些对象的管理访问权限不能限制为可用对象的子集。 例如,你可能有一个管理用户创建用于特定站点的边界组。 由于边界对象不支持安全范围,因此无法为此用户分配仅提供对可能与该站点关联的边界的访问权限的安全范围。 由于边界对象无法关联到安全范围,因此在向用户分配包含对边界对象访问权限的安全角色时,该用户可以访问层次结构中的每个边界。
不支持安全范围的对象包括但不限于以下项:
- Active Directory 林
- 管理用户
- 警报
- 边界
- 计算机关联
- 默认客户端设置
- 部署模板
- 设备驱动程序
- 迁移站点到站点映射
- 安全角色
- 安全范围
- 站点地址
- 站点系统角色
- 软件更新
- 状态消息
- 用户设备相关性
当必须限制对单独的对象实例的访问时,请创建安全范围。 例如:
你有一组需要查看生产应用程序而不是测试应用程序的管理用户。 为生产应用程序创建一个安全作用域,为测试应用程序创建另一个安全作用域。
一组管理用户需要对特定软件更新组具有读取权限。 另一组管理用户需要其他软件更新组的“修改”和“删除”权限。 为这些软件更新组创建不同的安全作用域。
有关详细信息,请参阅 为对象配置安全作用域。
后续步骤
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈