Azure Stack Hub Ruggedized 網路部署
本主題內容涵蓋 TOR 交換器、IP 位址指派及其他網路連線部署工作的存取權限。
規劃設定部署
接下來會在各節中介紹權限及 IP 位址指派。
實體交換器存取控制清單
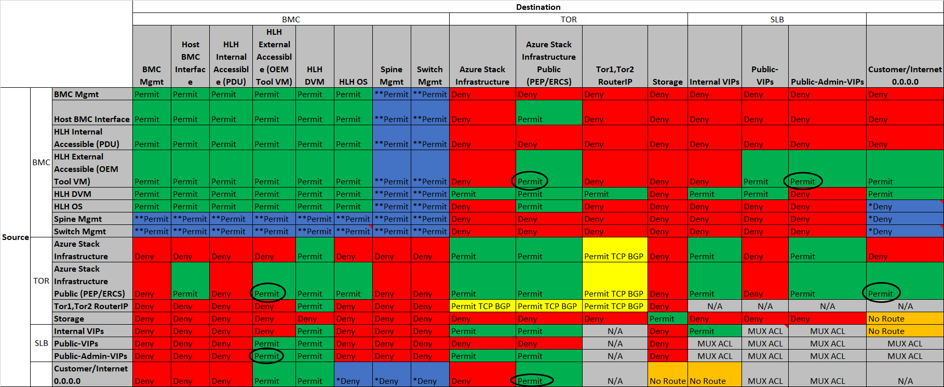
為了保護 Azure Stack 解決方案,我們已在 TOR 交換器上實作存取控制清單 (ACL)。 本節會說明此安全性功能的實作方式。 下表所列的是 Azure Stack 解決方案之內每個網路的來源和目的地:
下表會將 ACL 參考與 Azure Stack 網路彼此相互關聯。
| BMC Mgmt | 依據通訊協定和連接埠,已將部署 VM、BMC 介面、HLH 伺服器 NTP 伺服器和 DNS 伺服器 IP 作為「允許」包含。 |
|---|---|
| HLH 內部存取 (PDU) | 流量受限於 BMC 交換器 |
| HLH 外部存取 (OEM 工具 VM) | ACL 允許超出邊界裝置範圍的存取。 |
| Switch Mgmt | 專用交換器管理介面。 |
| Spine Mgmt | 專用的骨幹管理介面。 |
| Azure Stack | Azure Stack 基礎結構服務和虛擬機器、受限制的網路 |
| 基礎結構 | |
| Azure Stack | Azure Stack 受保護的端點、緊急復原主控台伺服器 |
| 基礎結構 | |
| 公用 (PEP/ERCS) | |
| Tor1、Tor2 RouterIP | 用於 SLB 與交換器/路由器之間邊界閘道協定對等互連的交換器 Loopback 介面。 |
| 儲存體 | 不會路由到區域範圍外的私人 IP |
| 內部 VIP | 不會路由傳送至區域範圍外的私人 IP |
| 公用 VIP | 由網路控制卡管理的租用戶網路位址空間。 |
| 公用管理員 VIP | 租用戶集區中的位址小型子集,與內部 VIP 及 Azure Stack 基礎結構通訊時需要使用 |
| 客戶/網際網路 | 客戶定義的網路。 以 Azure Stack 0.0.0.0 觀點而言,此為邊界裝置。 |
| 0.0.0.0 | |
| Deny | 客戶可以更新此欄位,以允許其他網路啟用管理功能。 |
| Permit | 啟用允許流量,但依預設會停用 SSH 存取。 客戶可以選擇啟用 SSH 服務。 |
| 無路由 | 不會將路由器散佈到 Azure Stack 環境之外。 |
| MUX ACL | 使用 Azure Stack MUX ACL。 |
| N/A | 不屬於 VLAN ACL。 |
IP 位址指派
在部署工作表中,會請您提供以下網路位址,用於協助 Azure Stack 部署流程。 部署小組會使用部署工作表工具,將 IP 網路打散成系統所需的較小規模網路。 如需每個網路的詳細說明,請參閱上述的「網路設計與基礎結構」一節。
本次範例中,要在部署工作表中的 [網路設定] 索引標籤填入以下值:
BMC 網路:10.193.132.0 /27
專用網儲存網路 & 內部VIP:11.11.128.0/24
基礎結構網路:12.193.130.0 /24
公用虛擬 IP (VIP) 網路:13.200.132.0 /24
交換器基礎結構網路:10.193.132.128 /26
執行部署工作表工具的「產生」函式時,會在試算表上建立兩個新的索引標籤。 第一個索引標籤是 [子網路摘要],會顯示如何分割超級網路,以建立系統所需的所有網路。 以下範例僅是此索引標籤上資料行的子集,實際結果包含下列每個網路的更多詳細資訊:
| 機架 | 子網路類型 | 名稱 | IPv4 子網路 | IPv4 位址 |
|---|---|---|---|---|
| 框線 | P2P 連結 | P2P_Border/Border1_To_Rack1/TOR1 | 10.193.132.128/30 | 4 |
| 框線 | P2P 連結 | P2P_Border/Border1_To_Rack1/TOR2 | 10.193.132.132/30 | 4 |
| 框線 | P2P 連結 | P2P_Border/Border2_To_Rack1/TOR1 | 10.193.132.136/30 | 4 |
| 框線 | P2P 連結 | P2P_Border/Border2_To_Rack1/TOR2 | 10.193.132.140/30 | 4 |
| 框線 | P2P 連結 | P2P_Rack1/TOR1_To_Rack1/BMC | 10.193.132.144/30 | 4 |
| 框線 | P2P 連結 | P2P_Rack1/TOR2_To_Rack1/BMC | 10.193.132.148/30 | 4 |
| 機架 1 | 回送 | Loopback0_Rack1_TOR1 | 10.193.132.152/32 | 1 |
| 機架 1 | 回送 | Loopback0_Rack1_TOR2 | 10.193.132.153/32 | 1 |
| 機架 1 | 回送 | Loopback0_Rack1_BMC | 10.193.132.154/32 | 1 |
| 機架 1 | P2P 連結 | P2P_Rack1/TOR1-ibgp-1_To_Rack1/TOR2-ibgp-1 | 10.193.132.156/30 | 4 |
| 機架 1 | P2P 連結 | P2P_Rack1/TOR1-ibgp-2_To_Rack1/TOR2-ibgp-2 | 10.193.132.160/30 | 4 |
| 機架 1 | VLAN | BMCMgmt | 10.193.132.0/27 | 32 |
| 機架 1 | VLAN | SwitchMgmt | 10.193.132.168/29 | 8 |
| 機架 1 | VLAN | CL01-RG01-SU01-Storage | 11.11.128.0/25 | 128 |
| 機架 1 | VLAN | CL01-RG01-SU01-Infra | 12.193.130.0/24 | 256 |
| 機架 1 | 其他 | CL01-RG01-SU01-VIPS | 13.200.132.0/24 | 256 |
| 機架 1 | 其他 | CL01-RG01-SU01-InternalVIPS | 11.11.128.128/25 | 128 |
第二個索引標籤是 [IP Address Usage]\(IP 位址使用量\),顯示了 IP 的使用情況:
BMC 網路
BMC 網路的超級網路至少需要一個 /26 網路。 網路閘道會使用機架中的第一個 IP,隨後是機架中的 BMC 裝置。 硬體生命週期主機有多個在此網路上指派的位址,可用來部署、監視和支援機架。 這些 IP 會分散為 3 個群組:DVM、InternalAccessible 和 ExternalAccessible。
- 機架:Rack1
- 名稱:BMCMgmt
| 指派對象 | IPv4 位址 |
|---|---|
| 網路 | 10.193.132.0 |
| 閘道 | 10.193.132.1 |
| HLH-BMC | 10.193.132.2 |
| AzS-Node01 | 10.193.132.3 |
| AzS-Node02 | 10.193.132.4 |
| AzS-Node03 | 10.193.132.5 |
| AzS-Node04 | 10.193.132.6 |
| ExternalAccessible-1 | 10.193.132.19 |
| ExternalAccessible-2 | 10.193.132.20 |
| ExternalAccessible-3 | 10.193.132.21 |
| ExternalAccessible-4 | 10.193.132.22 |
| ExternalAccessible-5 | 10.193.132.23 |
| InternalAccessible-1 | 10.193.132.24 |
| InternalAccessible-2 | 10.193.132.25 |
| InternalAccessible-3 | 10.193.132.26 |
| InternalAccessible-4 | 10.193.132.27 |
| InternalAccessible-5 | 10.193.132.28 |
| CL01-RG01-SU01-DVM00 | 10.193.132.29 |
| HLH-OS | 10.193.132.30 |
| 廣播 | 10.193.132.31 |
儲存體網路
儲存體網路是私人網路,並非用來路由到機架範圍之外。 這是「私人網路」超級網路的前半部,由分散的交換器使用,如下表所示。 網路閘道是子網路中的第一個 IP。 用於內部 VIP 的後半部為位址的私人集區,由 Azure Stack SLB 管理,且不會顯示於 [IP Address Usage]\(IP 位址使用量\) 索引標籤上。這些網路可支援 Azure Stack,且 TOR 交換器上的 ACL 會讓這些網路無法在解決方案範圍外受到通告及/或存取。
- 機架:Rack1
- 名稱:CL01-RG01-SU01-Storage
| 指派對象 | IPv4 位址 |
|---|---|
| 網路 | 11.11.128.0 |
| 閘道 | 11.11.128.1 |
| TOR1 | 11.11.128.2 |
| TOR2 | 11.11.128.3 |
| 廣播 | 11.11.128.127 |
Azure Stack 基礎結構網路
基礎結構網路的超級網路需要一個 /24 網路,且在部署工作表工具執行後仍會繼續維持 /24 網路。 網路閘道會是子網路中的第一個 IP。
- 機架:Rack1
- 名稱:CL01-RG01-SU01-Infra
| 指派對象 | IPv4 位址 |
|---|---|
| 網路 | 12.193.130.0 |
| 閘道 | 12.193.130.1 |
| TOR1 | 12.193.130.2 |
| TOR2 | 12.193.130.3 |
| 廣播 | 12.193.130.255 |
交換器基礎結構網路
基礎結構網路會分為多個實體交換器基礎結構所使用的網路。 這與 Azure Stack 基礎結構不同,僅支援 Azure Stack 軟體。 Switch Infra Network 僅支援實體交換器基礎結構。 基礎結構支援的網路如下:
| 名稱 | IPv4 子網路 |
|---|---|
| P2P_Border/Border1_To_Rack1/TOR1 | 10.193.132.128/30 |
| P2P_Border/Border1_To_Rack1/TOR2 | 10.193.132.132/30 |
| P2P_Border/Border2_To_Rack1/TOR1 | 10.193.132.136/30 |
| P2P_Border/Border2_To_Rack1/TOR2 | 10.193.132.140/30 |
| P2P_Rack1/TOR1_To_Rack1/BMC | 10.193.132.144/30 |
| P2P_Rack1/TOR2_To_Rack1/BMC | 10.193.132.148/30 |
| Loopback0_Rack1_TOR1 | 10.193.132.152/32 |
| Loopback0_Rack1_TOR2 | 10.193.132.153/32 |
| Loopback0_Rack1_BMC | 10.193.132.154/32 |
| P2P_Rack1/TOR1-ibgp-1_To_Rack1/TOR2-ibgp-1 | 10.193.132.156/30 |
| P2P_Rack1/TOR1-ibgp-2_To_Rack1/TOR2-ibgp-2 | 10.193.132.160/30 |
| SwitchMgmt | 10.193.132.168/29 |
點對點 (P2P):這些網路允許所有交換器之間的連線。 各 P2P 的子網路大小為 /30 網路。 最低 IP 一律會指派到堆疊上的上游 (North) 裝置。
Loopback:這些位址是 /32 網路,指派給機架中使用的每個交換器。 並未將 Loopback 指派給邊界裝置,因為不會將邊界裝置視為 Azure Stack 解決方案。
Switch Mgmt 或 Switch Management:此 /29 網路會支援機架中交換器的專用管理介面。 指派的 IP 如下,也可在部署工作表的 [IP Address Usage]\(IP 位址使用量\) 索引標籤上找到此表:
機架:Rack1
名稱:SwitchMgmt
| 指派對象 | IPv4 位址 |
|---|---|
| 網路 | 10.193.132.168 |
| 閘道 | 10.193.132.169 |
| TOR1 | 10.193.132.170 |
| TOR2 | 10.193.132.171 |
| 廣播 | 10.193.132.175 |
準備環境
硬體生命週期主機映像不含必要的 Linux 容器,此種容器用來產生實體網路交換器設定。
最新合作夥伴部署工具組不含最新的容器映像。 若需要產生更新後的交換器設定,可替換硬體生命週期主機上的容器映像。
以下是容器映像的更新步驟:
下載容器映像
取代下列位置的容器映像
產生設定
接下來會逐步說明 JSON 檔案和 Network Switch Configuration 檔案的產生步驟:
開啟部署工作表
填妥所有索引標籤上的必要欄位
在部署工作表上叫用「產生」函式。
會再多建立兩個額外的索引標籤,顯示所產生的 IP 子網路和指派項目。請檢查資料,確認後即叫用「匯出」函式。
系統會出現提示,請您提供要做為 JSON 檔案儲存位置的資料夾。請使用 Invoke-SwitchConfigGenerator.ps1 來執行容器。 此指令碼需要較高權限的 PowerShell 主控台方能執行,且執行時需要以下參數。
ContainerName:將會產生交換器設定的容器名稱。
ConfigurationData:自部署工作表匯出的 ConfigurationData.json 檔案路徑。
OutputDirectory:輸出目錄的路徑。
Offline:代表該指令碼在離線模式下執行。
C:\\WINDOWS\\system32\> .\\Invoke-SwitchConfigGenerate.ps1 -ContainerName generalonrampacr.azurecr.io/master -ConfigurationData .\\ConfigurationData.json -OutputDirectory c:\\temp -Offline
指令碼結束時會產生 ZIP 檔案,帶有工作表中所用的前置詞。
C:\WINDOWS\system32> .\Invoke-SwitchConfigGenerate.ps1 -ContainerName generalonrampacr.azurecr.io/master -ConfigurationData .\ConfigurationData.json -OutputDirectory c:\temp -Offline
Seconds : 2
Section : Validation
Step : WindowsRequirement
Status : True
Detail : @{CurrentImage=10.0.18363.0}
Seconds : 2
Section : Validation
Step : DockerService
Status : True
Detail : @{Status=Running}
Seconds : 9
Section : Validation
Step : DockerSetup
Status : True
Detail : @{CPU=4; Memory=4139085824; OS=Docker Desktop; OSType=linux}
Seconds : 9
Section : Validation
Step : DockerImage
Status : True
Detail : @{Container=generalonrampacr.azurecr.io/master:1.1910.78.1}
Seconds : 10
Section : Run
Step : Container
Status : True
Detail : @{ID=2a20ba622ef9f58f9bcd069c3b9af7ec076bae36f12c5653f9469b988c01706c; ExternalPort=32768}
Seconds : 38
Section : Generate
Step : Config
Status : True
Detail : @{OutputFile=c:\temp\N22R19.zip}
Seconds : 38
Section : Exit
Step : StopContainer
Status : True
Detail : @{ID=2a20ba622ef9f58f9bcd069c3b9af7ec076bae36f12c5653f9469b988c01706c}
自訂組態
您可以修改 Azure Stack 交換器設定的幾個環境設定。 您可以辨識出範本中所能變更的設定。 此文章說明每個可自訂的設定,以及這些變更對您的 Azure Stack 有何影響。 這些設定包括密碼更新、syslog 伺服器、SNMP 監視、驗證與存取控制清單。
在 Azure Stack 解決方案部署期間,原始設備製造商 (OEM) 會同時建立並套用 TORs 與 BMC 的交換器設定。 OEM 會使用 Azure Stack 自動化工具來驗證這些裝置上的必要設定是否正確設定。 設定是以 Azure Stack 部署工作表中的資訊為基礎。
注意
請勿在 OEM 或 Microsoft Azure Stack 工程小組同意的情況下修改設定。 網路裝置設定的變更可能會大幅影響 Azure Stack 執行個體中網路問題的作業或疑難排解。 如需有關網路裝置上這些功能的詳細資訊,請連絡您的 OEM 硬體提供者或 Microsoft 支援服務。 您的 OEM 具有以您的 Azure Stack 部署工作表為基礎的自動化工具所建立的設定檔。
不過,有一些值可以在網路交換器設定上新增、移除或變更。
密碼更新
操作員可以隨時更新網路交換器上任何使用者的密碼。 不需要變更 Azure Stack 系統上的任何資訊,或使用在 Azure Stack 中輪替使用祕密的步驟。
Syslog 伺服器
操作員可以將交換器記錄檔重新導向至其資料中心的 syslog 伺服器。 使用此設定可確保來自特定時間點的記錄可用於進行疑難排解。 根據預設,記錄檔會儲存在交換器上;其儲存記錄的容量有限。 如需如何設定交換器管理存取權的概觀,請參閱存取控制清單更新一節。
SNMP 監視
操作員可以設定簡易網路管理通訊協定 (SNMP) v2 或 v3 來監視網路裝置,並將陷阱傳送到資料中心上的網路監視應用程式。 基於安全性理由,請使用 SNMPv3,因為它比 v2 更安全。 請連絡您的 OEM 硬體提供者,以取得所需的 MIB 與設定。 如需如何設定交換器管理存取權的概觀,請參閱存取控制清單更新一節。
驗證
操作員可以設定 RADIUS 或 TACACS 來管理網路裝置上的驗證。 請連絡您的 OEM 硬體提供者,以取得所需的支援方法與設定。 如需如何設定交換器管理存取權的概觀,請參閱存取控制清單更新一節。
存取控制清單更新
操作員可以變更某些存取控制清單 (ACL),以允許從受信任的資料中心網路範圍存取網路裝置管理介面與硬體生命週期主機 (HLH)。 操作員可以挑選可連線的元件,以及連線位置。 使用存取控制清單時,操作員可以允許特定網路範圍內的管理 Jumpbox VM 存取交換器管理介面、HLH OS 與 HLH BMC。
如需詳細資訊,請參閱實體交換器存取控制清單。
TACACS、RADIUS、Syslog
Azure Stack 解決方案並未隨附 TACACS 或 RADIUS 這類用於裝置存取控制 (如交換器和路由器) 的解決方案,也未蕤負用於擷取交換器記錄的 Syslog 解決方案,但所有這些裝置都能支援上述服務。 為了方便與您環境中既有的 TACACS、RADIUS 及/或 Syslog 伺服器整合,會與 Network Switch Configuration 一起提供另外的額外檔案,如此現場工程師便能配合客戶需求自訂交換器。
後續步驟
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應