什麼是 Azure Active Directory B2C?
Azure Active Directory B2C 提供企業對客戶身分識別即服務。 您的客戶會使用其慣用的社交、企業或本機帳戶身分識別取得應用程式和 API 的單一登入。
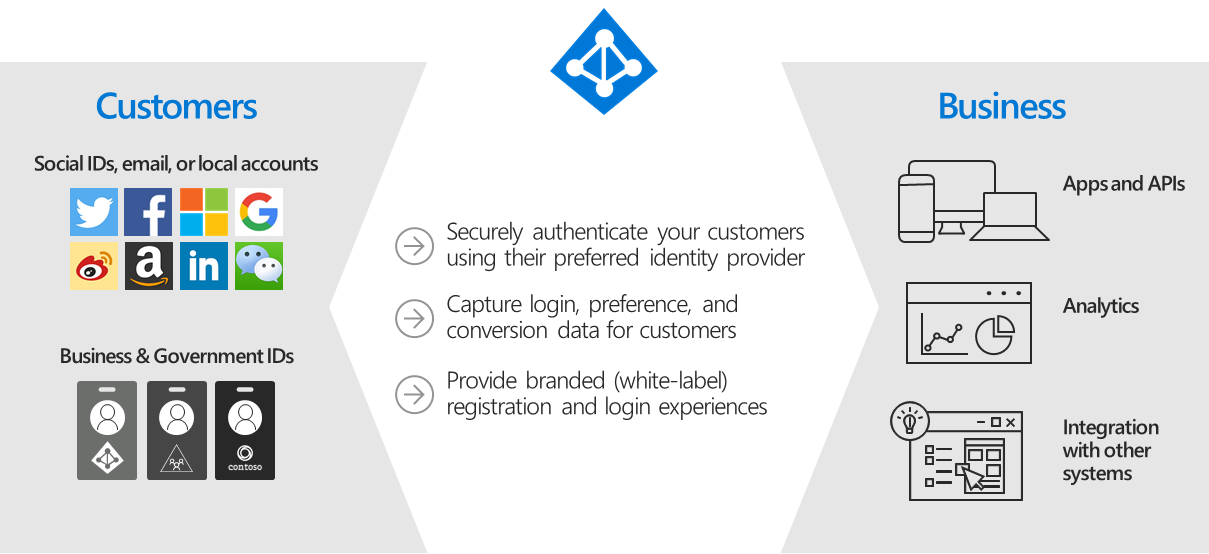
Azure AD B2C 是一種客戶身分識別存取管理 (CIAM) 解決方案,每天能夠支援數百萬名使用者和數十億次驗證。 負責驗證平台的規模調整和安全性,以及監控和自動處理威脅 (例如拒絕服務、密碼噴濺或暴力密碼破解攻擊)。
Azure AD B2C 是與Microsoft Entra識別碼不同的服務。 它是以與Microsoft Entra識別碼相同的技術為基礎,但基於不同目的。 它可讓企業建置面向客戶的應用程式,然後允許任何人註冊這些應用程式,且不會限制使用者帳戶。
誰會使用 Azure AD B2C?
任何想要使用白標驗證解決方案來向終端使用者驗證其 Web/行動應用程式的企業或個人。 除了驗證之外,Azure AD B2C 服務可用於授權,例如通過驗證的使用者存取 API 資源。 Azure AD B2C 的設計目的是要供 IT 系統管理員 和 開發人員使用。
自訂品牌的身分識別解決方案
Azure AD B2C 是一種白標驗證解決方案。 您可以使用自己的品牌自訂整個使用者體驗,使其與您的 Web 和行動應用程式順暢地融合。
當您的使用者註冊、登入和修改其設定檔資訊時,自訂 Azure AD B2C 所顯示的每個頁面。 在使用者旅程圖中自訂 HTML、CSS 和 JavaScript,讓 Azure AD B2C 的外觀和操作體驗像是應用程式的原生部分。
以使用者提供的身分識別存取單一登入
Azure AD B2C 使用標準型驗證通訊協定,包括 OpenID Connect、OAuth 2.0 與安全性聲明標記語言 (SAML)。 它會與大多數現代化應用程式和商業現成軟體整合。
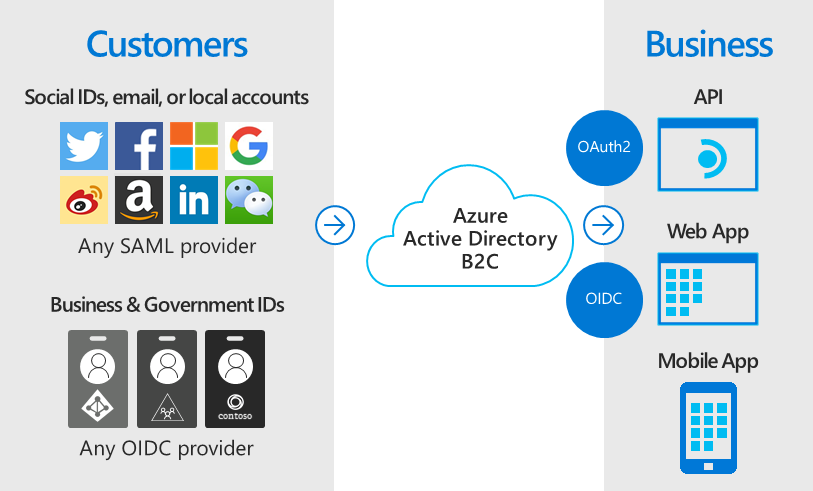
Azure AD B2C 可充當 Web 應用程式、行動應用程式和 API 的中央驗證授權單位,讓您為上述項目建置單一登入 (SSO) 解決方案。 集中收集使用者設定檔和喜好設定資訊,並擷取有關登入行為和註冊轉換的詳細分析。
與外部使用者存放區整合
Azure AD B2C 提供一個目錄,可為每個使用者保存 100 個自訂屬性。 但是,您也可以與外部系統整合。 例如,使用 Azure AD B2C 進行驗證,但將其委派給外部客戶關係管理 (CRM) 或客戶忠誠度資料庫,作為客戶資料的真實來源。
另一個外部使用者存放區案例是讓 Azure AD B2C 處理應用程式的驗證,但與儲存使用者設定檔或個人資料的外部系統整合。 例如,滿足資料落地需求,例如區域或內部部署資料儲存原則。 不過,Azure AD B2C 服務本身是透過 Azure 公用雲端,於全球各地提供。
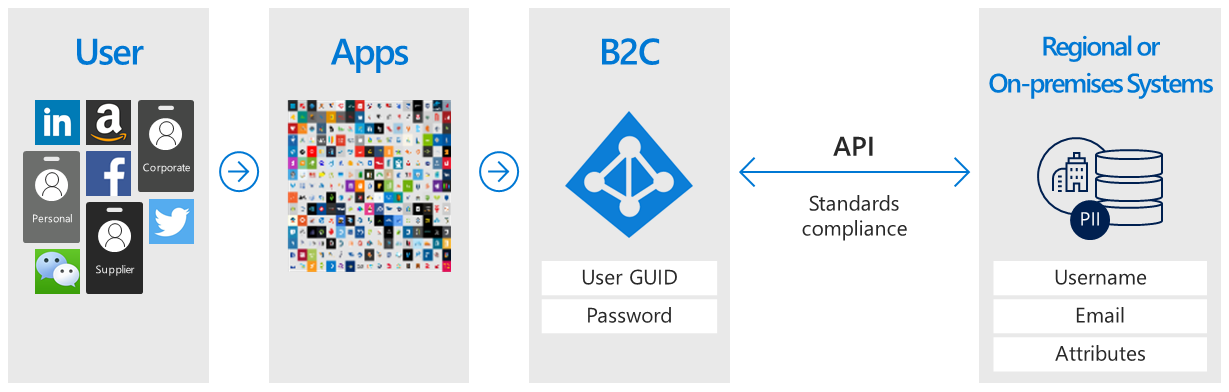
Azure AD B2C 可以在註冊或設定檔編輯期間,協助向使用者收集資訊,然後透過 API 來將該資料交給外部系統。 接著,在未來驗證期間,Azure AD B2C 可從外部系統擷取資料,並視需要將其包含在它傳送至您應用程式的驗證權杖回應中。
漸進式分析
另一個使用者旅程圖選項包含漸進式分析。 漸進式分析可讓客戶藉由收集最少量的資訊,快速完成其第一筆交易。 然後,在未來登入時,向客戶逐漸收集更多設定檔資料。
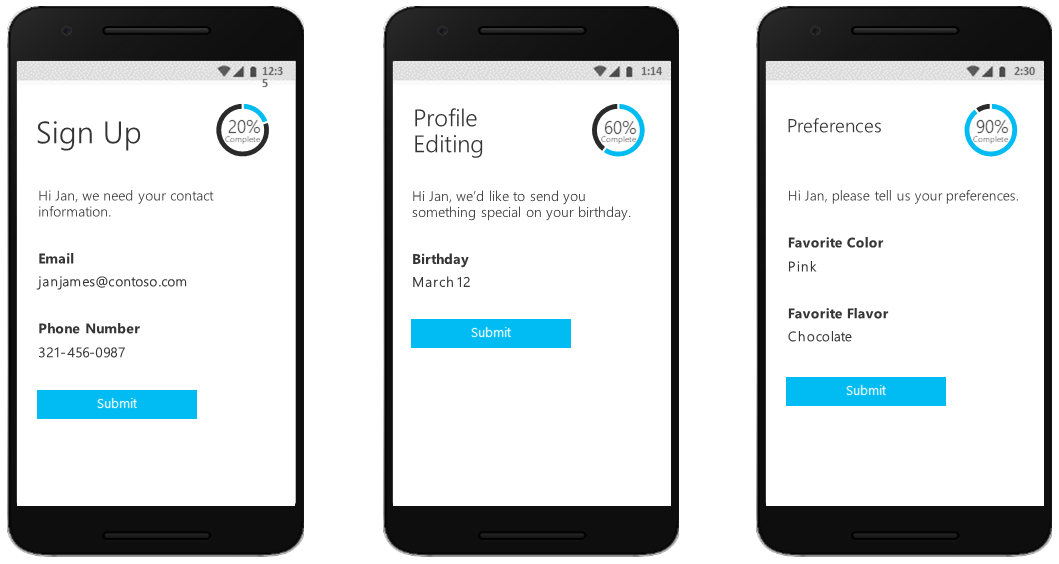
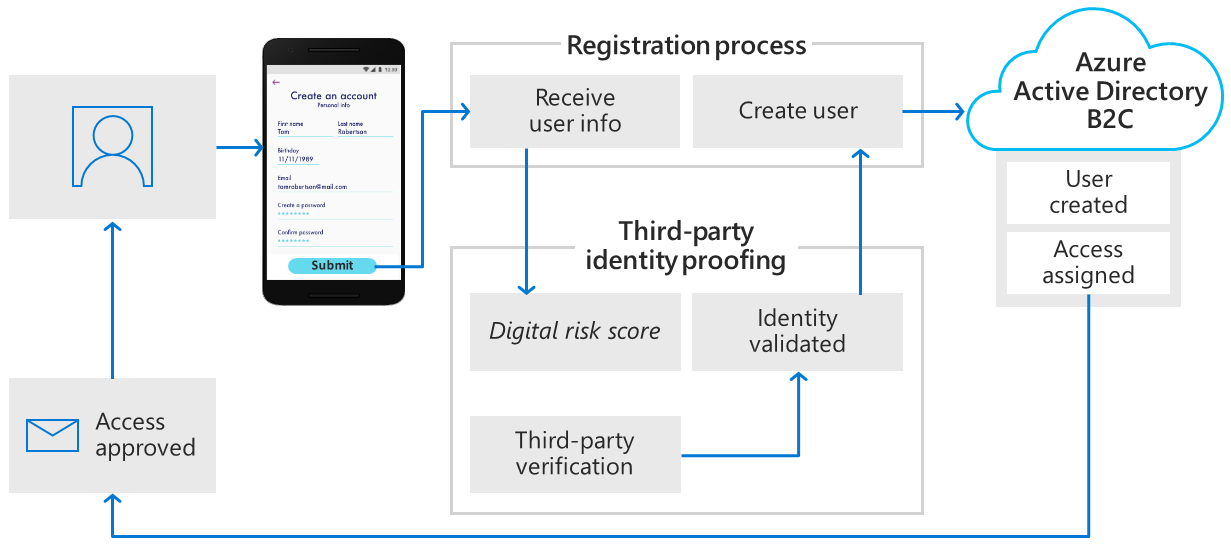
第三方身分識別驗證和證明
使用 Azure AD B2C 收集使用者資料,然後將其傳遞至第三方系統,以執行驗證、信任評分及核准建立使用者帳戶,進而促進身分識別驗證和證明。
您已經了解可將 Azure AD B2C 當作企業對客戶的身分識別平台來執行的一些作業。 您現在可以直接移至 更深入的 Azure AD B2C 技術概觀。
後續步驟
您現在已了解 Azure AD B2C 是什麼以及它可協助處理的一些案例,請進一步了解其功能和技術層面。