在 Azure Active Directory B2C 中設定密碼重設流程
開始之前,請使用 [選擇原則類型 選取器] 來選擇您要設定的原則類型。 Azure Active Directory B2C 提供兩種方法來定義使用者如何與您的應用程式互動:透過預先 定義的使用者流程 ,或透過完全可設定 的自定義原則。 本文中每個方法所需的步驟都不同。
在註冊和登入旅程圖中,用戶可以使用忘記密碼來重設自己的密碼? 此自助式密碼重設流程適用於使用電子郵件位址或具有密碼登入之 Azure Active Directory B2C (Azure AD B2C) 中的本機帳戶。
密碼重設流程牽涉到下列步驟:
- 在註冊和登入頁面上,用戶選取 [ 忘記密碼嗎? ] 連結。 Azure AD B2C 會起始密碼重設流程。
- 在下一個出現的對話框中,使用者輸入其電子郵件地址,然後選取 [ 傳送驗證碼]。 Azure AD B2C 會將驗證碼傳送至使用者的電子郵件帳戶。 使用者從電子郵件複製驗證碼、在 [Azure AD B2C 密碼重設] 對話框中輸入代碼,然後選取 [ 驗證碼]。
- 然後,使用者可以輸入新的密碼。 (驗證電子郵件之後,使用者仍然可以選取 變更電子郵件 按鈕;請參閱 隱藏變更電子郵件按鈕。)
提示
如果使用者忘記密碼並想要重設密碼,則可以使用自助式密碼重設流程來變更其密碼。 您也可以選擇下列其中一個使用者流程選項:
selfAsserted.html 中 [變更電子郵件] 按鈕的預設名稱是 changeclaims。 若要尋找按鈕名稱,請在註冊頁面上,使用 [檢查] 等瀏覽器工具來檢查頁面來源。
必要條件
- 建立使用者流程 ,讓使用者可以註冊並登入您的應用程式。
- 註冊 Web 應用程式。
- 完成開始使用 Active Directory B2C 中的自定義原則中的 步驟
- 註冊 Web 應用程式。
隱藏變更電子郵件按鈕
驗證電子郵件之後,使用者仍然可以選取 [變更電子郵件]、輸入另一個電子郵件地址,然後重複電子郵件驗證。 如果您要隱藏 [ 變更電子郵件 ] 按鈕,您可以修改 CSS 來隱藏對話框中相關聯的 HTML 元素。 例如,您可以將下列 CSS 專案新增至 selfAsserted.html,並使用 HTML 範本自定義使用者介面:
<style type="text/css">
.changeClaims
{
visibility: hidden;
}
</style>
自助式密碼重設(建議)
新的密碼重設體驗現在是註冊或登入原則的一部分。 當使用者選取 [忘記密碼嗎? ] 連結時,系統會立即將他們傳送至忘記密碼體驗。 您的應用程式不再需要處理 AADB2C90118錯誤碼,而且您不需要個別的原則來重設密碼。
自助式密碼重設體驗可以針對 [登入] 或 [建議] 或 [註冊和登入] 使用者流程進行設定。 如果您沒有設定其中一個使用者流程,請建立 註冊或登入 使用者流程。
若要設定註冊或登入使用者流程的自助式密碼重設:
- 登入 Azure 入口網站。
- 如果您有多個租使用者的存取權,請選取頂端功能表中的 設定 圖示,從 [目錄 + 訂用帳戶] 功能表切換至您的 Azure AD B2C 租使用者。
- 在 Azure 入口網站中,搜尋並選取 [Azure AD B2C]。
- 選取 [ 使用者流程]。
- 選取您要自訂的註冊或登入使用者流程(類型為 [建議] 。
- 在 [設定] 下的功能表中,選取 [屬性]。
- 在 [密碼設定] 底下,選取 [自助式密碼重設]。
- 選取 [儲存]。
- 在左側功能表的 [自定義] 下,選取 [版面配置]。
- 在 [版面配置版本] 中,選取 [2.1.3 ] 或更新版本。
- 選取 [儲存]。
下列各節說明如何將自助式密碼體驗新增至自定義原則。 此範例是以自定義原則入門套件中包含的原則檔案為基礎。
提示
您可以在 GitHub 上找到註冊和使用密碼重設原則登入的完整範例。
指出用戶已選取忘記密碼?連結
若要指示用戶選取 [忘記密碼嗎?] 鏈接的原則,請定義布爾宣告。 使用宣告將使用者旅程 導向至忘記密碼 技術配置檔。 宣告也可以發出至令牌,因此應用程式會偵測使用者使用忘記密碼使用者流程登入。
在宣告架構中宣告您的宣告。 在 SocialAndLocalAccounts/TrustFrameworkExtensions.xml 中開啟原則的擴展名檔案。
搜尋 BuildingBlocks 元素。 如果專案不存在,請加以新增。
找出 ClaimsSchema 元素。 如果專案不存在,請加以新增。
將下列宣告新增至 ClaimsSchema 元素。
<!-- <BuildingBlocks> <ClaimsSchema> --> <ClaimType Id="isForgotPassword"> <DisplayName>isForgotPassword</DisplayName> <DataType>boolean</DataType> <AdminHelpText>Whether the user has selected Forgot your Password</AdminHelpText> </ClaimType> <!-- </ClaimsSchema> </BuildingBlocks> -->
升級版面配置版本
需要版面配置 2.1.2 版,才能在註冊或登入旅程圖中啟用自助式密碼重設流程。 若要升級版面配置版本:
開啟原則的基底檔案,例如 SocialAndLocalAccounts/TrustFrameworkBase.xml。
搜尋 BuildingBlocks 元素。 如果專案不存在,請加以新增。
找出 ContentDefinitions 元素。 如果專案不存在,請加以新增。
修改 ContentDefinition 元素內的 DataURI 元素,以具有識別碼
api.signuporsignin:<!-- <BuildingBlocks> <ContentDefinitions> --> <ContentDefinition Id="api.signuporsignin"> <DataUri>urn:com:microsoft:aad:b2c:elements:contract:unifiedssp:2.1.2</DataUri> </ContentDefinition> <!-- </ContentDefinitions> </BuildingBlocks> -->
新增技術配置檔
宣告轉換技術配置檔會 isForgotPassword 存取宣告。 稍後會參考技術配置檔。 叫用時,它會將宣告的值 isForgotPassword 設定為 true。
- 在 SocialAndLocalAccounts/TrustFrameworkExtensions.xml 中開啟原則的擴展名檔案。
- 尋找 ClaimsProviders 元素(如果元素不存在,請加以建立),然後新增下列宣告提供者:
<!--
<ClaimsProviders> -->
<ClaimsProvider>
<DisplayName>Local Account</DisplayName>
<TechnicalProfiles>
<TechnicalProfile Id="ForgotPassword">
<DisplayName>Forgot your password?</DisplayName>
<Protocol Name="Proprietary" Handler="Web.TPEngine.Providers.ClaimsTransformationProtocolProvider, Web.TPEngine, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null"/>
<OutputClaims>
<OutputClaim ClaimTypeReferenceId="isForgotPassword" DefaultValue="true" AlwaysUseDefaultValue="true"/>
</OutputClaims>
<UseTechnicalProfileForSessionManagement ReferenceId="SM-Noop" />
</TechnicalProfile>
<TechnicalProfile Id="SelfAsserted-LocalAccountSignin-Email">
<Metadata>
<Item Key="setting.forgotPasswordLinkOverride">ForgotPasswordExchange</Item>
</Metadata>
</TechnicalProfile>
<TechnicalProfile Id="LocalAccountWritePasswordUsingObjectId">
<UseTechnicalProfileForSessionManagement ReferenceId="SM-AAD" />
</TechnicalProfile>
</TechnicalProfiles>
</ClaimsProvider>
<!--
</ClaimsProviders> -->
SelfAsserted-LocalAccountSignin-Email 技術配置檔設定.forgotPasswordLinkOverride 會定義在您的使用者旅程圖中執行的密碼重設宣告交換。
需要 LocalAccountWritePasswordUsingObjectId 技術配置檔 UseTechnicalProfileForSessionManagementSM-AAD 會話管理員,使用者才能在 SSO 條件下成功預先建立後續登入。
新增密碼重設子旅程圖
用戶現在可以在使用者旅程圖中登入、註冊和執行密碼重設。 若要更妥善地組織使用者旅程圖,您可以使用 子旅程 來處理密碼重設流程。
子旅程圖會從使用者旅程圖呼叫,並執行將密碼重設體驗傳遞給使用者的特定步驟。 Call使用類型子旅程圖,讓子旅程完成時,控制權會傳回起始子旅程的協調流程步驟。
- 開啟原則的擴展名檔案,例如 SocialAndLocalAccounts/TrustFrameworkExtensions.xml。
- 尋找 SubJourneys 元素。 如果元素不存在,請在User Journeys元素之後新增它。 然後,新增下列子旅程圖:
<!--
<SubJourneys>-->
<SubJourney Id="PasswordReset" Type="Call">
<OrchestrationSteps>
<!-- Validate user's email address. -->
<OrchestrationStep Order="1" Type="ClaimsExchange">
<ClaimsExchanges>
<ClaimsExchange Id="PasswordResetUsingEmailAddressExchange" TechnicalProfileReferenceId="LocalAccountDiscoveryUsingEmailAddress" />
</ClaimsExchanges>
</OrchestrationStep>
<!-- Collect and persist a new password. -->
<OrchestrationStep Order="2" Type="ClaimsExchange">
<ClaimsExchanges>
<ClaimsExchange Id="NewCredentials" TechnicalProfileReferenceId="LocalAccountWritePasswordUsingObjectId" />
</ClaimsExchanges>
</OrchestrationStep>
</OrchestrationSteps>
</SubJourney>
<!--
</SubJourneys>-->
準備您的使用者旅程圖
接下來,若要連接忘記密碼?連結至忘記密碼子旅程圖,您必須參考 CombinedSignInAndSignUp 步驟之 ClaimsProviderSelection 元素中的忘記密碼子旅程標識符。
如果您沒有具有 CombinedSignInAndSignUp 步驟的自定義使用者旅程圖,請完成下列步驟來複製現有的註冊或登入使用者旅程圖。 否則,請繼續進行下一節。
- 在入門套件中,開啟 TrustFrameworkBase.xml 檔案,例如 SocialAndLocalAccounts/TrustFrameworkBase.xml。
- 尋找並複製包含
Id="SignUpOrSignIn"之 UserJourney 元素的整個內容。 - 開啟 TrustFrameworkExtensions.xml 檔案,例如 SocialAndLocalAccounts/TrustFrameworkExtensions.xml,並尋找 UserJourneys 元素。 如果專案不存在,請加以建立。
- 貼上您在步驟 2 中複製之 UserJourney 元素的整個內容,以建立 UserJourneys 元素的子元素。
- 重新命名使用者旅程圖的標識碼。 例如:
Id="CustomSignUpSignIn"。
連線 忘記密碼連結至忘記密碼子旅程圖
在您的使用者旅程圖中,您可以將 [忘記密碼] 子旅程圖表示為 ClaimsProviderSelection。 藉由新增此元素,您會將 [忘記密碼?] 鏈接連接到 [忘記密碼] 子旅程圖。
開啟 TrustFrameworkExtensions.xml 檔案,例如 SocialAndLocalAccounts/TrustFrameworkExtensions.xml。
在使用者旅程圖中,尋找包含
Type="CombinedSignInAndSignUp"或Type="ClaimsProviderSelection"的協調流程步驟元素。 通常是第一個協調流程步驟。 ClaimsProviderSelections 元素包含用戶可用來登入的識別提供者清單。 新增下列這一行:<ClaimsProviderSelection TargetClaimsExchangeId="ForgotPasswordExchange" />在下一個 協調流程步驟中,新增 ClaimsExchange 元素,方法是新增下列這一行:
<ClaimsExchange Id="ForgotPasswordExchange" TechnicalProfileReferenceId="ForgotPassword" />在目前步驟和下一個步驟之間新增下列協調流程步驟。 您新增的新協調流程步驟會檢查 isForgotPassword 宣告是否存在。 如果宣告存在,它會叫用 密碼重設子旅程圖。
<OrchestrationStep Order="3" Type="InvokeSubJourney"> <Preconditions> <Precondition Type="ClaimsExist" ExecuteActionsIf="false"> <Value>isForgotPassword</Value> <Action>SkipThisOrchestrationStep</Action> </Precondition> </Preconditions> <JourneyList> <Candidate SubJourneyReferenceId="PasswordReset" /> </JourneyList> </OrchestrationStep>新增協調流程步驟之後,請循序重新編號步驟,而不需要略過從 1 到 N 的任何整數。
設定要執行的使用者旅程圖
既然您已修改或建立使用者旅程圖,請在 [信賴憑證者 ] 區段中指定 Azure AD B2C 針對此自定義原則執行的旅程。
開啟具有 信賴憑證者 元素的檔案,例如 SocialAndLocalAccounts/SignUpOrSignin.xml。
在 RelyingParty 元素中 ,尋找 DefaultUserJourney 元素。
更新 DefaultUserJourney ReferenceId,以符合您新增 ClaimsProviderSelections 的使用者旅程圖標識符。
<RelyingParty>
<DefaultUserJourney ReferenceId="CustomSignUpSignIn" />
...
</RelyingParty>
指出忘記密碼流程至您的應用程式
您的應用程式可能需要偵測使用者是否使用忘記密碼使用者流程登入。 isForgotPassword 宣告包含布爾值,指出它們已執行。 宣告可以在傳送至應用程式的令牌中發出。 如有必要,請將isForgotPassword 新增至信賴憑證者區段中的輸出宣告。 您的應用程式可以檢查 isForgotPassword 宣告,以判斷使用者是否重設其密碼。
<RelyingParty>
<OutputClaims>
...
<OutputClaim ClaimTypeReferenceId="isForgotPassword" DefaultValue="false" />
</OutputClaims>
</RelyingParty>
上傳自定義原則
- 登入 Azure 入口網站。
- 如果您有多個租使用者的存取權,請選取頂端功能表中的 [設定] 圖示,以從 [目錄 + 訂用帳戶] 功能表切換至 Azure AD B2C 租使用者。
- 在 Azure 入口網站中,搜尋並選取 [Azure AD B2C]。
- 在 [原則] 下的功能表中,選取 [身分識別體驗架構]。
- 選取 [ 上傳自定義原則]。 依下列順序,上傳您變更的原則檔案:
- 原則的基底檔案,例如 TrustFrameworkBase.xml。
- 擴充原則,例如 TrustFrameworkExtensions.xml。
- 信賴憑證者原則,例如 SignUpSignIn.xml。
測試密碼重設流程
- 選取您想要測試的註冊或登入使用者流程(建議類型)。
- 選取執行使用者流程。
- 針對 [ 應用程式],選取您稍早註冊的 Web 應用程式名為 webapp1 。 回覆 URL 應該會顯示
https://jwt.ms。 - 選取執行使用者流程。
- 在 [註冊或登入] 頁面上,選取 [ 忘記密碼?]。
- 確認您稍早建立之帳戶的電子郵件地址,然後選取 [ 繼續]。
- 在顯示的對話框中,變更使用者的密碼,然後選取 [ 繼續]。 令牌會傳回 ,
https://jwt.ms而瀏覽器會顯示它。 - 檢查傳回令牌的 isForgotPassword 宣告值。 如果存在且 設定為
true,則使用者已重設密碼。
密碼重設原則 (舊版)
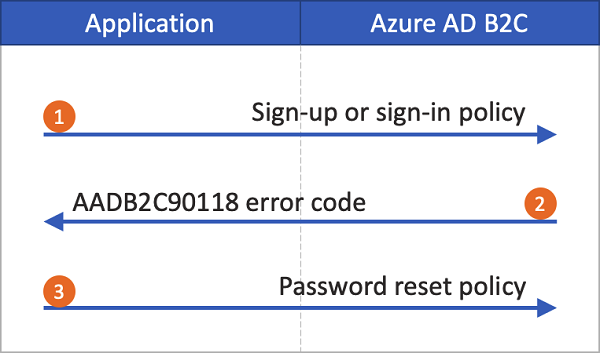
如果未啟用自助式密碼重設體驗,選取此連結不會自動觸發密碼重設使用者流程。 相反地,錯誤碼 AADB2C90118 會傳回至您的應用程式。 您的應用程式必須重新初始化驗證連結庫,以驗證 Azure AD B2C 密碼重設使用者流程,以處理此錯誤碼。
下圖描述此程式:
在應用程式中,用戶選取 [登入]。 應用程式會起始授權要求,並重新導向至 Azure AD B2C,讓使用者完成登入。 授權要求會指定註冊或登入原則名稱,例如 B2C_1_signup_signin。
用戶選取 [ 忘記密碼嗎?] 連結。 Azure AD B2C 會將
AADB2C90118錯誤碼傳回給應用程式。應用程式會處理錯誤碼並起始新的授權要求。 授權要求會指定密碼重設原則名稱,例如 B2C_1_pwd_reset。
您可以看到基本的 ASP.NET 範例,示範使用者流程連結的方式。
建立密碼重設使用者流程
若要讓您的應用程式使用者重設其密碼,請建立密碼重設使用者流程:
- 在 Azure 入口網站 中,移至 Azure AD B2C 租使用者概觀。
- 在左側功能表的 [原則] 底下,選取 [使用者流程],然後選取 [新增使用者流程]。
- 在 [建立使用者流程] 中,選取 [ 密碼重設 使用者流程]。
- 在 [選取版本] 下,選取 [建議],然後選取 [建立]。
- 針對 [ 名稱],輸入使用者流程的名稱。 例如, passwordreset1。
- 針對識別提供者,使用使用者名稱啟用重設密碼,或使用電子郵件位址重設密碼。
- 在 [多重要素驗證] 底下,如果您想要要求使用者使用第二個驗證方法來驗證其身分識別,請選取方法類型,以及何時強制執行多重要素驗證。 深入了解。
- 在 [條件式存取] 下,如果您已為 Azure AD B2C 租使用者設定條件式存取原則,而且您想要在此使用者流程中使用它們,請選取 [強制執行條件式存取原則] 複選框。 您不需要指定原則名稱。 深入了解。
- 在 [應用程式宣告] 底下,選取 [顯示更多]。 選擇您要在授權令牌中傳回的宣告,這些宣告會傳回給您的應用程式。 例如,選取 [使用者的對象標識符]。
- 選取 [確定]。
- 選取 [建立],以新增使用者流程。 B2C_1前置詞會自動新增至名稱。
測試使用者流程
若要測試使用者流程:
- 選取您建立的使用者流程。 在 [使用者流程概觀] 頁面上,選取 [ 執行使用者流程]。
- 針對 [應用程式],選取您想要測試的 Web 應用程式,例如您稍早註冊的 Webapp1。 回覆 URL 應該是
https://jwt.ms。 - 選取 [ 執行使用者流程],確認您要重設密碼之帳戶的電子郵件地址,然後選取 [ 繼續]。
- 變更密碼,然後選取 [ 繼續]。 令牌會傳回 ,
https://jwt.ms而瀏覽器會顯示它。
建立密碼重設原則
自定義原則是一組 XML 檔案,您上傳至 Azure AD B2C 租使用者以定義使用者旅程圖。 我們提供具有數個預先建置原則的入門套件,包括註冊和登入、密碼重設和配置檔編輯原則。 如需詳細資訊,請參閱 開始使用 Azure AD B2C 中的自定義原則。
針對 Azure AD B2C 使用者流程和自定義原則進行疑難解答
您的應用程式必須處理來自 Azure B2C 服務的特定錯誤。 瞭解如何 針對 Azure AD B2C 的使用者流程和自定義原則進行疑難解答。
下一步
設定 強制密碼重設。
使用內嵌密碼重設註冊和登入。
