啟用個別使用者的 Microsoft Entra 多重要素驗證來保護登入事件
若要保護 Microsoft Entra ID 中的使用者登入事件,您可以要求多重要素驗證。 使用條件式存取原則啟用 Microsoft Entra 多重要素驗證是保護用戶的建議方法。 條件式存取是 Microsoft Entra ID P1 或 P2 功能,可讓您在特定案例中視需要套用規則來要求 MFA。 若要開始使用條件式存取,請參閱 教學課程:使用 Microsoft Entra 多重要素驗證保護使用者登入事件。
對於沒有條件式存取的 Microsoft Entra ID Free 租使用者,您可以使用 安全性預設值來保護使用者。 系統會視需要提示使用者輸入 MFA,但您無法定義自己的規則來控制行為。
如有需要,您可以改為為每個使用者 Microsoft Entra 多重要素驗證啟用每個帳戶。 當使用者個別啟用時,會在每次登入時執行多重要素驗證(但有一些例外狀況,例如當他們從信任的IP位址 登入或開啟信任裝置 上的記住MFA功能時)。
除非您的 Microsoft Entra 識別元授權不包含條件式存取,而且您不想使用安全性預設值,否則不建議變更 用戶狀態 。 如需啟用 MFA 之不同方式的詳細資訊,請參閱 Microsoft Entra 多重要素驗證的功能和授權。
重要
本文詳細說明如何檢視和變更每個使用者 Microsoft Entra 多重要素驗證的狀態。 如果您使用條件式存取或安全性預設值,則不會使用下列步驟來檢閱或啟用用戶帳戶。
透過條件式存取原則啟用 Microsoft Entra 多重要素驗證並不會變更用戶的狀態。 如果用戶顯示為已停用,請勿發出警示。 條件式存取不會變更狀態。
如果您使用條件式存取原則,請勿啟用或強制執行個別使用者的 Microsoft Entra 多重要素驗證。
Microsoft Entra 多重要素驗證用戶狀態
用戶的狀態會反映系統管理員是否已在每個使用者 Microsoft Entra 多重要素驗證中註冊它們。 Microsoft Entra 多重要素驗證中的用戶帳戶具有下列三個不同的狀態:
| State | 描述 | 受影響的舊版驗證 | 受影響的瀏覽器應用程式 | 受影響的新式驗證 |
|---|---|---|---|---|
| 停用 | 未在每個使用者 Microsoft Entra 多重要素驗證中註冊之用戶的默認狀態。 | No | 無 | No |
| 已啟用 | 使用者已在每個使用者 Microsoft Entra 多重要素驗證中註冊,但仍可使用其密碼進行舊版驗證。 如果使用者尚未註冊 MFA 驗證方法,他們會收到提示,以便在下次使用新式驗證登入時註冊 (例如透過網頁瀏覽器)。 | 否。 舊版驗證會繼續運作,直到註冊程式完成為止。 | 是。 會話到期之後,需要 Microsoft Entra 多重要素驗證註冊。 | 是。 存取令牌到期之後,需要 Microsoft Entra 多重要素驗證註冊。 |
| 強制執行 | 使用者在 Microsoft Entra 多重要素驗證中註冊每個使用者。 如果使用者尚未註冊驗證方法,他們會收到提示,以便在下次使用新式驗證登入時註冊 (例如透過網頁瀏覽器)。 處於 啟用 狀態時完成註冊的用戶會自動移至 [強制] 狀態。 | 是。 應用程式需要應用程式密碼。 | 是。 登入時需要 Microsoft Entra 多重要素驗證。 | 是。 登入時需要 Microsoft Entra 多重要素驗證。 |
所有使用者一開始都是已停用。 當您在每個使用者 Microsoft Entra 多重要素驗證中註冊用戶時,其狀態會變更為 [已啟用]。 當已啟用的使用者登入並完成註冊流程時,他們的狀態會變更為強制執行。 系統管理員可以將使用者移至不同狀態,包括從強制執行移至已啟用或已停用。
注意
如果使用者重新啟用每個使用者 MFA,且使用者未重新註冊,其 MFA 狀態不會從 [已啟用] 轉換為 [在 MFA 管理 UI 中強制執行]。 系統管理員必須將使用者直接移至 [強制]。
檢視用戶的狀態
提示
本文中的步驟可能會根據您從開始的入口網站稍有不同。
若要檢視及管理用戶狀態,請完成下列步驟:
- 以至少驗證 管理員 istrator 身分登入 Microsoft Entra 系統管理中心。
- 流覽至 [身分>識別使用者>所有使用者]。
- 選取 [ 個別使用者 MFA]。
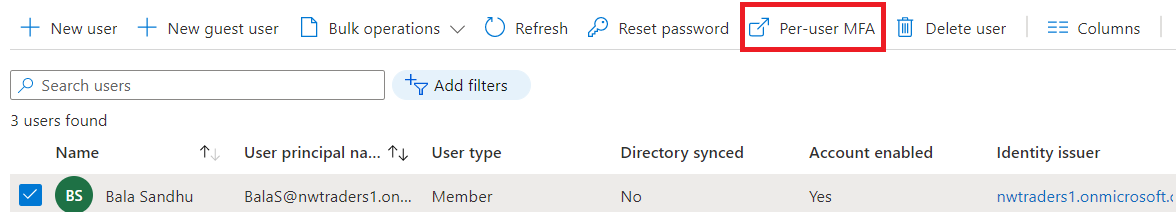
- 隨即開啟顯示用戶狀態的新頁面,如下列範例所示。
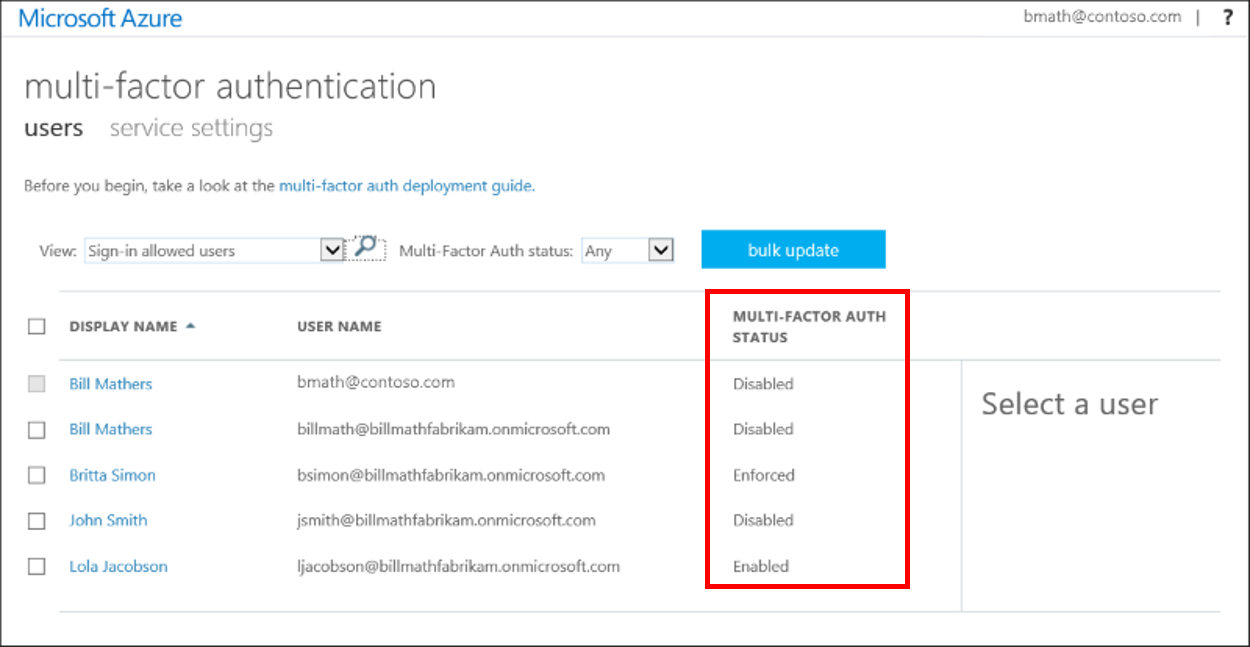
變更用戶的狀態
若要變更使用者的個別使用者 Microsoft Entra 多重要素驗證狀態,請完成下列步驟:
使用先前的步驟來 檢視用戶 的狀態,以取得 Microsoft Entra 多重要素驗證 用戶 頁面。
尋找您想要針對個別使用者 Microsoft Entra 多重要素驗證啟用的使用者。 您可能需要將頂端的檢視變更為 使用者。
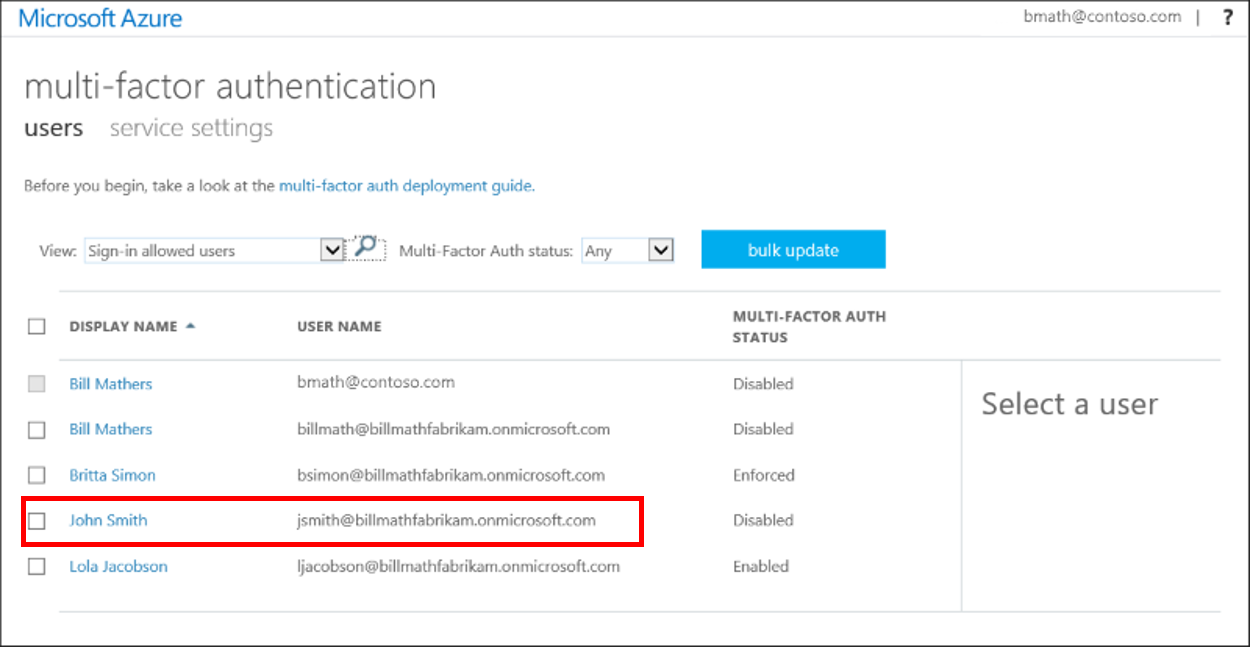
核取使用者名稱(s) 旁的方塊,以變更的狀態。
在右側的快速步驟下,選擇 [啟用] 或 [停用]。 在下列範例中,使用者 John Smith 在其名稱旁邊有一個檢查,並啟用以供使用:

提示
啟用的使用者 會在註冊 Microsoft Entra 多重要素驗證時自動切換為 [強制 ]。 請勿手動將用戶狀態變更為 [強制 ],除非用戶已註冊,或使用者可接受使用者遇到與舊版驗證通訊協定連線中斷的情況。
在開啟的彈出視窗中確認您的選取專案。
啟用使用者後請透過電子郵件通知他們。 告訴使用者,系統會顯示提示,要求他們在下次登入時註冊。 此外,如果您的組織使用不支援現今驗證的非瀏覽器應用程式,則其必須建立應用程式密碼。 如需詳細資訊,請參閱 Microsoft Entra 多重要素驗證使用者指南 ,以協助他們開始使用。
下一步
若要設定 Microsoft Entra 多重要素驗證設定,請參閱 設定 Microsoft Entra 多重要素驗證設定。
若要管理 Microsoft Entra 多重要素驗證的使用者設定,請參閱 使用 Microsoft Entra 多重要素驗證管理用戶設定。
若要瞭解用戶為何收到提示或未提示執行 MFA,請參閱 Microsoft Entra 多重要素驗證報告。