Microsoft Entra ID 中應用程式的同意體驗
在本文中,瞭解 Microsoft Entra 應用程式同意用戶體驗。 您可以針對組織及/或開發應用程式,以更順暢的同意體驗,以智慧方式管理應用程式。
同意是使用者授權應用程式代表使用者存取受保護的資源所用的程序。 系統管理員可以要求系統管理員或使用者同意允許存取其組織/個人資料。
授與同意的實際用戶體驗會因使用者租使用者、使用者授權範圍(或角色)和用戶端應用程式所要求的許可權類型而有所不同。 這表示應用程式開發人員和租用戶系統管理員對同意體驗有一些控制權。 管理員可彈性設定租用戶或應用程式控制其租用戶同意體驗的原則,和加以停用。 應用程式開發人員可以決定可要求的權限類型,以及是否要引導使用者進行使用者同意流程或管理員同意流程。
- 使用者同意流程 是應用程式開發人員將使用者導向授權端點,意圖只記錄目前使用者的同意。
- 管理員 同意流程是應用程式開發人員將用戶導向管理員同意端點,意圖記錄整個租使用者的同意。 為了確保管理員同意流程正常運作,應用程式開發人員必須在應用程式指令清單中的
RequiredResourceAccess屬性中列出所有許可權。 如需詳細資訊,請參閱應用程式資訊清單。
同意提示的建置組塊
同意提示的設計目的是要確保使用者有足夠的資訊來判斷他們是否信任用戶端應用程式代表他們存取受保護的資源。 瞭解建置組塊可協助授與同意的使用者做出更明智的決策,並協助開發人員建置更好的用戶體驗。
下圖和表格提供同意提示建置組塊的相關信息。
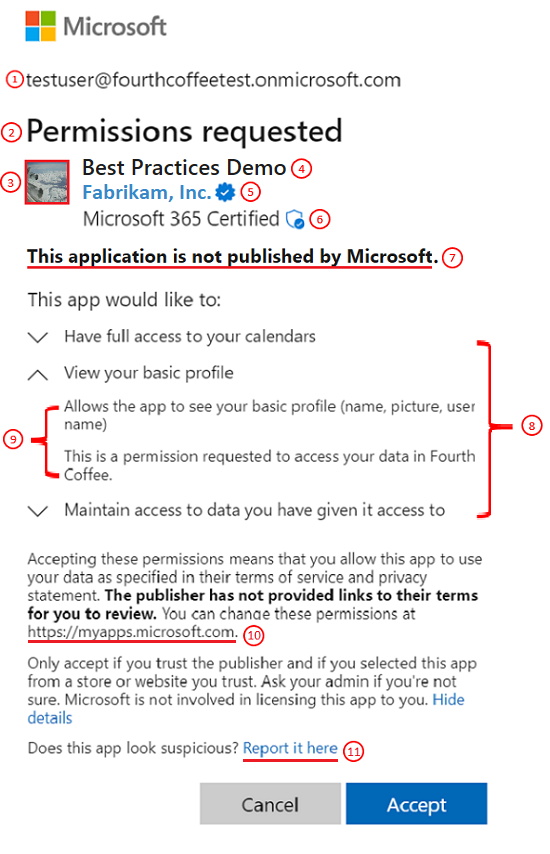
| # | 元件 | 目的 |
|---|---|---|
| 1 | 用戶標識碼 | 此標識子代表用戶端應用程式要求代表存取受保護資源的使用者。 |
| 2 | 標題 | 標題會根據用戶進行用戶或系統管理員同意流程而變更。 在使用者同意流程中,標題為「要求許可權」,而在系統管理員同意流程中,標題有另一行「接受您的組織」。 |
| 3 | 應用程式標誌 | 此影像應該可協助使用者有視覺提示,指出此應用程式是否為他們打算存取的應用程式。 此映像是由應用程式開發人員提供,且此映像的擁有權不會驗證。 |
| 4 | 應用程式名稱 | 此值應通知使用者哪些應用程式要求存取其數據。 請注意,此名稱是由開發人員提供,而且此應用程式名稱的擁有權不會驗證。 |
| 5 | 發行者名稱和驗證 | 藍色「已驗證」徽章表示應用程式發行者已使用 Microsoft 合作夥伴網路帳戶驗證其身分識別,並已完成驗證程式。 如果應用程式已驗證發行者,則會顯示發行者名稱。 如果應用程式未經過發行者驗證,則會顯示「未驗證」,而不是發行者名稱。 如需詳細資訊,請參閱發行 者驗證。 選取發行者名稱會顯示更多可用的應用程式資訊,例如發行者名稱、發行者網域、建立日期、認證詳細數據和回復 URL。 |
| 6 | Microsoft 365 認證 | Microsoft 365 認證標誌表示應用程式已針對衍生自領先業界標準架構的控件進行審查,且強式安全性與合規性做法已就緒以保護客戶數據。 如需詳細資訊,請參閱 Microsoft 365 認證。 |
| 7 | 發行者資訊 | 顯示應用程式是否由 Microsoft 發佈。 |
| 8 | 權限 | 此清單包含用戶端應用程式所要求的許可權。 用戶應一律評估要求的許可權類型,以瞭解用戶端應用程式在接受時將代表他們存取哪些數據。 身為應用程式開發人員,最好以最低許可權要求存取許可權。 |
| 9 | 許可權描述 | 這個值是由公開許可權的服務所提供。 若要查看許可權描述,您必須切換許可權旁邊的箭號。 |
| 10 | https://myapps.microsoft.com |
這是使用者可以檢閱和移除目前可存取其數據的任何非 Microsoft 應用程式的連結。 |
| 11 | 在此處報告 | 如果您不信任應用程式,則此連結可用來報告可疑的應用程式,如果您認為應用程式正在模擬另一個應用程式,如果您認為應用程式會濫用您的數據,或基於其他原因。 |
常見案例和同意體驗
下一節說明每個案例的常見案例和預期的同意體驗。
應用程式需要用戶有權授與的許可權
在此同意案例中,使用者會存取需要使用者授權範圍內許可權集合的應用程式。 使用者會被導向至使用者同意流程。
管理員 會在傳統同意提示中看到另一個控件,允許代表整個租使用者同意。 控件預設為關閉,因此只有在系統管理員明確核取方塊時,才會代表整個租使用者授與該方塊。 複選框只會顯示全域 管理員 istrator 角色,因此 Cloud 管理員 和 App 管理員 不會看到此複選框。
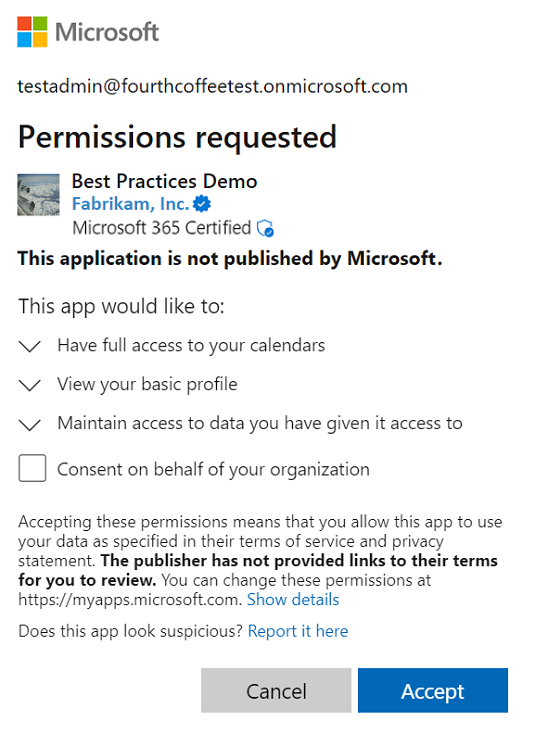
使用者會看到傳統的同意提示。
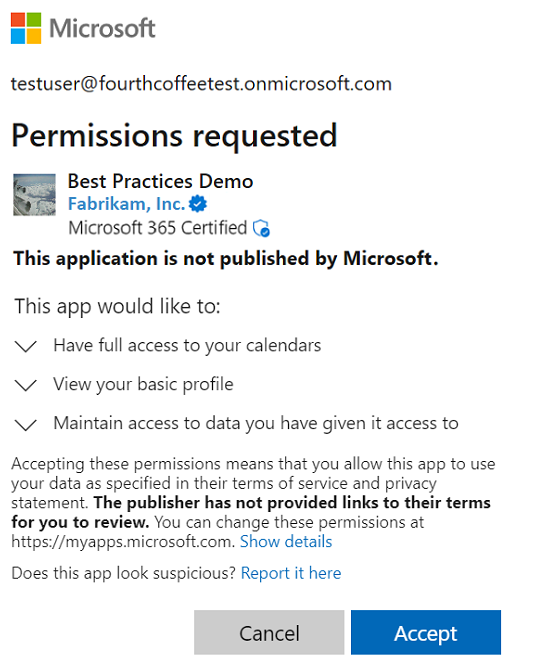
應用程式需要用戶無權授與的許可權
在此同意案例中,使用者存取需要至少一個超出使用者授權範圍許可權的應用程式。
管理員 會在傳統同意提示中看到另一個控件,以代表整個租使用者同意。

不是系統管理員的使用者會被封鎖而無法授與應用程式的同意,他們被告知要求其系統管理員存取應用程式。 如果使用者的租使用者中已啟用管理員同意工作流程,使用者就能夠從同意提示提交管理員核准要求。 如需管理員同意工作流程的詳細資訊,請參閱 管理員 同意工作流程。

用戶會導向管理員同意流程
在此同意案例中,用戶會流覽至或導向管理員同意流程。
管理員 使用者會看到系統管理員同意提示。 在此提示上變更的標題和許可權描述,這些變更會反白顯示接受此提示會代表整個租使用者授與應用程式對所要求數據的存取權。
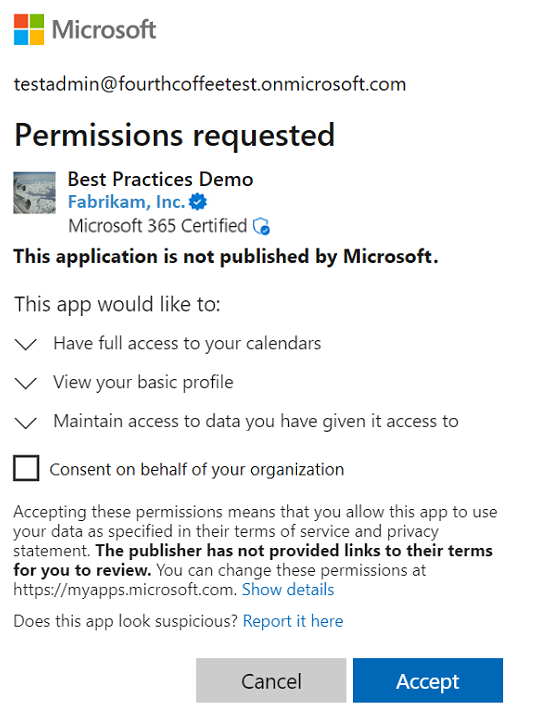
用戶無法授與應用程式的同意,並被告知要求其系統管理員存取應用程式。

透過 Microsoft Entra 系統管理中心 管理員 同意
在此案例中,系統管理員同意應用程式要求的所有許可權,這些許可權可以代表租使用者中的所有使用者包含委派的許可權。 系統管理員會透過 Microsoft Entra 系統管理中心內應用程式註冊的 API 許可權頁面授與同意。
除非應用程式需要新的許可權,否則該租使用者中的所有使用者都不會看到同意對話框。 若要瞭解哪些系統管理員角色可以同意委派的許可權,請參閱 Microsoft Entra ID 中的 管理員 istrator 角色許可權。
重要
目前,使用 MSAL.js 的單頁應用程式 (SPA) 必須使用 [授與權限] 按鈕,以授與明確同意。 否則,應用程式會在要求存取權杖時失敗。
常見的問題
本節概述同意體驗的常見問題和可能的疑難解答秘訣。
403 錯誤
用戶無法同意
- 檢查租使用者管理員是否已為貴組織停用使用者同意
- 確認您要求的許可權是否為系統管理員限制許可權。
即使管理員已同意,使用者仍會遭到封鎖
- 檢查靜態許可權是否已設定為動態要求的許可權超集。
- 檢查應用程式是否需要使用者指派。
針對已知錯誤進行疑難解答
如需疑難排解步驟,請參閱同意應用程式時發生未預期的錯誤。
另請參閱
- 取得 Microsoft Entra 同意架構如何實作同意的逐步概觀。
- 深入了解多租用戶應用程式如何使用同意架構來實作「使用者」與「系統管理員」同意,進而支援更進階的多層應用程式模式。
- 瞭解如何 設定應用程式的發行者網域。
