建立可存取資源的 Microsoft Entra 應用程式和服務主體
在本文中,您將瞭解如何建立可與角色型訪問控制搭配使用的 Microsoft Entra 應用程式和服務主體。 當您在 Microsoft Entra ID 中註冊新的應用程式時,系統會自動建立服務主體以進行應用程式註冊。 服務主體是 Microsoft Entra 租使用者中的應用程式身分識別。 資源存取受限於指派給服務主體的角色,讓您控制哪些資源可以存取和哪個層級。 基於安全性考慮,一律建議使用服務主體搭配自動化工具,而不是允許他們以使用者身分識別登入。
在本文中,您將在 Azure 入口網站 中建立單一租用戶應用程式。 此範例適用於一個組織內所使用的企業營運應用程式。 您也可以 使用 Azure PowerShell 或 Azure CLI 來建立服務主體。
重要
請考慮針對應用程式身分識別使用 Azure 資源的受控識別,而不是建立服務主體。 如果您的程式代碼在支援受控識別的服務上執行,並存取支援 Microsoft Entra 驗證的資源,則受控識別是較適合您的選項。 若要深入瞭解 Azure 資源的受控識別,包括目前支援哪些服務,請參閱 什麼是 Azure 資源的受控識別?。
如需應用程式註冊、應用程式對象和服務主體之間關聯性的詳細資訊,請參閱 Microsoft Entra ID 中的應用程式和服務主體物件。
必要條件
若要在 Microsoft Entra 租使用者中註冊應用程式,您需要:
- Microsoft Entra 用戶帳戶。 如果您還沒有帳戶,您可以 免費建立帳戶。
註冊應用程式所需的許可權
您必須具備足夠的許可權,才能向 Microsoft Entra 租用戶註冊應用程式,並將角色指派給應用程式 Azure 訂用帳戶中的角色。 若要完成這些工作,您需要 Application.ReadWrite.All許可權。
使用 Microsoft Entra ID 註冊應用程式,並建立服務主體
提示
本文中的步驟可能會根據您從開始的入口網站稍有不同。
以至少雲端應用程式 管理員 istrator 身分登入 Microsoft Entra 系統管理中心。
流覽至 [身分>識別應用程式> 應用程式註冊 然後選取 [新增註冊]。
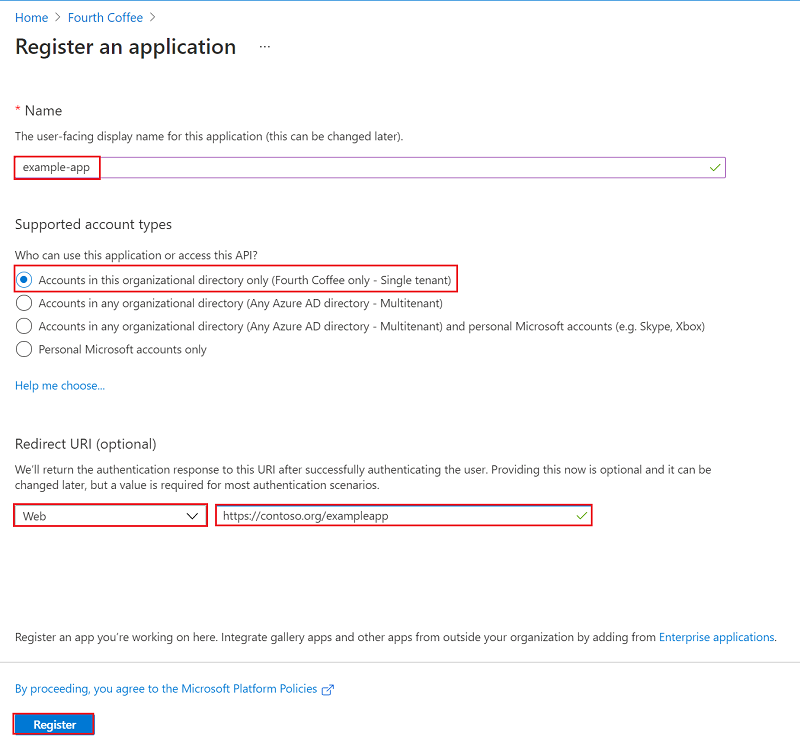
將應用程式命名為 「example-app」。
選取支援的帳戶類型,以決定誰可以使用應用程式。
在 [重新導向 URI] 底下,針對您要建立的應用程式類型選取 [Web]。 輸入要傳送存取令牌的 URI。
選取註冊。
您已建立 Microsoft Entra 應用程式和服務主體。
將角色指派給應用程式
若要存取訂用帳戶中的資源,您必須將角色指派給應用程式。 決定哪個角色為應用程式提供正確的許可權。 若要瞭解可用的角色,請參閱 Azure 內建角色。
您可以在訂用帳戶、資源群組或資源層級設定範圍。 許可權會繼承至較低層級的範圍。
登入 Azure 入口網站。
選取您想要指派應用程式的範圍層級。 例如,若要在訂用帳戶範圍指派角色,請搜尋並選取 [ 訂用帳戶]。 如果您沒有看到您要尋找的訂用帳戶,請選取 [全域訂用帳戶篩選]。 請確定已針對租用戶選取您想要的訂用帳戶。
選取 [存取控制 (IAM)]。
選取 [ 新增],然後選取 [ 新增角色指派]。
在 [角色] 索引標籤中,選取您想要指派給清單中應用程式的角色。 例如,若要允許應用程式執行重新啟動、啟動和停止實例等動作,請選取參與者角色。
選取 [ 下一步]。
在 [ 成員] 索引標籤上。選取 [指派存取權] ,然後選取 [ 使用者、群組或服務主體]
選取 [選取成員]。 根據預設,Microsoft Entra 應用程式不會顯示在可用的選項中。 若要尋找您的應用程式,請依其名稱搜尋它。
選取 [ 選取 ] 按鈕,然後選取 [ 檢閱 + 指派]。

您的服務主體已設定。 您可以開始使用它來執行文稿或應用程式。 若要管理服務主體(許可權、使用者同意的許可權、查看哪些使用者已同意、檢閱許可權、請參閱登入資訊等等),請移至 企業應用程式。
下一節說明如何以程序設計方式登入時取得所需的值。
登入應用程式
以程式設計方式登入時,請在驗證要求中傳遞租使用者標識碼和應用程式識別碼。 您也需要憑證或驗證金鑰。 若要取得目錄(租使用者)識別碼和應用程式識別碼:
- 流覽至 [身分>識別應用程式> 應用程式註冊],然後選取您的應用程式。
- 在應用程式的 [概觀] 頁面上,複製 [目錄] [租使用者] 識別符值,並將其儲存在您的應用程式程式代碼中。
- 複製應用程式 (用戶端) 識別碼,並將其儲存在您的應用程式程式代碼中。
設定驗證
有兩種驗證類型可用於服務主體:密碼式驗證 (應用程式密碼) 和憑證式驗證。 建議您使用證書頒發機構單位簽發的受信任憑證,但您也可以建立應用程式秘密,或建立自我簽署憑證進行測試。
選項 1(建議):上傳證書頒發機構單位簽發的受信任憑證
若要上傳憑證檔案:
- 流覽至 [身分>識別應用程式> 應用程式註冊],然後選取您的應用程式。
- 選取 [ 憑證與秘密]。
- 選取 [ 憑證],然後選取 [上傳憑證 ],然後選取要上傳的憑證檔案。
- 選取新增。 上傳憑證之後,會顯示指紋、開始日期和到期值。
在應用程式註冊入口網站中向您的應用程式註冊憑證之後,請啟用 機密用戶端應用程式 程式代碼以使用憑證。
選項 2:僅測試-建立和上傳自我簽署憑證
您可以選擇性地建立自我簽署憑證,僅供 測試之用。 若要建立自我簽署憑證,請開啟 Windows PowerShell,並使用下列參數執行 New-SelfSignedCertificate ,以在計算機上的使用者證書存儲中建立憑證:
$cert=New-SelfSignedCertificate -Subject "CN=DaemonConsoleCert" -CertStoreLocation "Cert:\CurrentUser\My" -KeyExportPolicy Exportable -KeySpec Signature
使用從 Windows 控制台 存取的管理用戶憑證 MMC 嵌入式管理單元,將此憑證導出至檔案。
- 從 [開始] 功能選取 [執行],然後輸入 certmgr.msc。 隨即出現目前使用者的憑證管理員工具。
- 若要檢視憑證,請在 左窗格中的 [憑證 - 目前使用者 ] 底下,展開 [個人 ] 目錄。
- 以滑鼠右鍵按下您所建立的憑證,選取 [所有工作匯出>]。
- 遵循憑證導出精靈。
若要上傳憑證:
- 流覽至 [身分>識別應用程式> 應用程式註冊],然後選取您的應用程式。
- 選取 [ 憑證與秘密]。
- 選取 [ 憑證],然後選取 [上傳憑證 ],然後選取憑證(您導出的現有憑證或自我簽署憑證)。
- 選取新增。
在應用程式註冊入口網站中向您的應用程式註冊憑證之後,請啟用 機密用戶端應用程式 程式代碼以使用憑證。
選項3:建立新的客戶端密碼
如果您選擇不使用憑證,您可以建立新的客戶端密碼。
- 流覽至 [身分>識別應用程式> 應用程式註冊],然後選取您的應用程式。
- 選取 [ 憑證與秘密]。
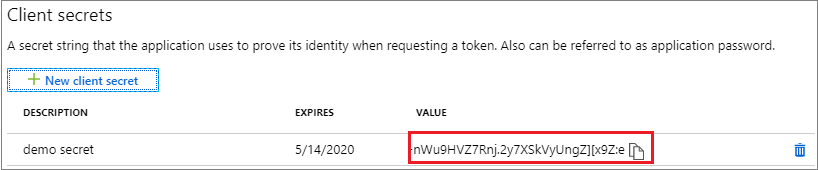
- 選取 [客戶端密碼],然後選取 [ 新增客戶端密碼]。
- 提供秘密的描述,以及持續時間。
- 選取新增。
儲存客戶端密碼之後,就會顯示客戶端密碼的值。 這隻會顯示一次,因此請複製此值,並將它儲存在應用程式可以擷取的位置,通常您的應用程式會保留如 clientId、或 authoruty 原始程式碼中的值。 您將提供秘密值,以及應用程式用戶端識別碼,以應用程式身分登入。
在資源上設定存取原則
您可能需要對應用程式需要存取的資源設定額外的許可權。 例如,您也必須 更新密鑰保存庫的存取原則 ,讓您的應用程式能夠存取密鑰、秘密或憑證。
若要設定存取原則:
登入 Azure 入口網站。
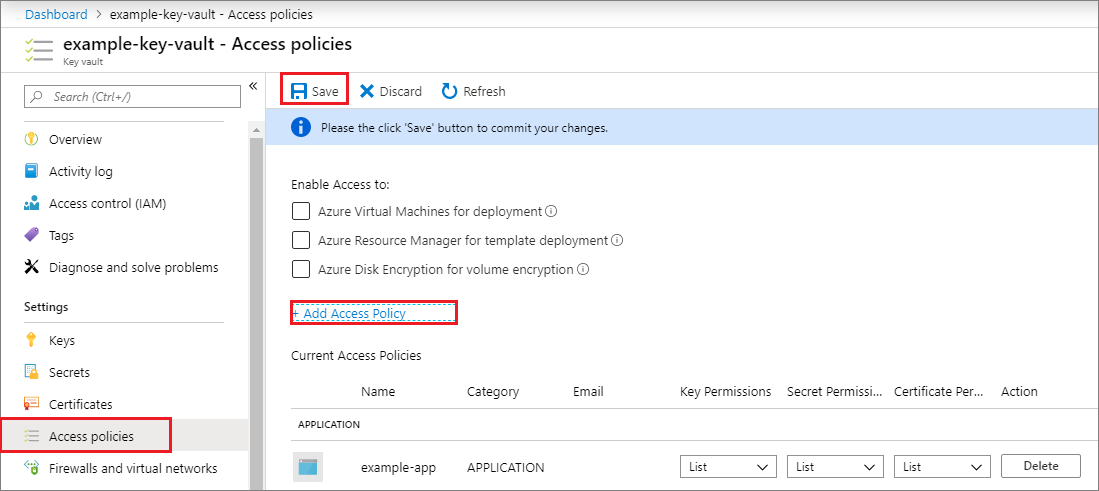
選取您的金鑰保存庫,然後選取 [ 存取原則]。
選取 [ 新增存取原則],然後選取您要授與應用程式的密鑰、秘密和憑證許可權。 選取您先前建立的服務主體。
選取 [ 新增 ] 以新增存取原則。
儲存。
下一步
- 瞭解如何使用 Azure PowerShell 或 Azure CLI 來建立服務主體。
- 若要瞭解如何指定安全策略,請參閱 Azure 角色型訪問控制(Azure RBAC)。
- 如需可授與或拒絕使用者的可用動作清單,請參閱 Azure Resource Manager 資源提供者作業。
- 如需使用 Microsoft Graph 處理應用程式註冊的相關信息,請參閱 應用程式 API 參考。