單一登入 SAML 通訊協定
本文涵蓋 Microsoft Entra ID 支援單一登錄的 SAML 2.0 驗證要求和回應。
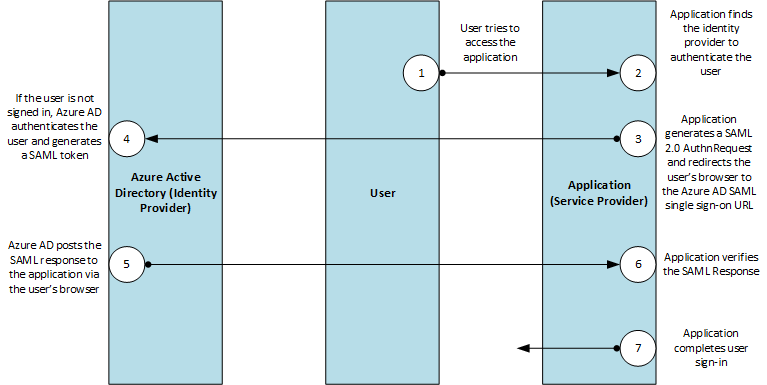
下列通訊協議圖表描述單一登錄順序。 雲端服務 (服務提供者) 會使用 HTTP 重新導向系結,將 (驗證要求) 元素傳遞 AuthnRequest 至 Microsoft Entra ID (識別提供者)。 Microsoft Entra ID 接著會使用 HTTP 張貼系結,將專案張貼 Response 至雲端服務。
注意
本文討論如何使用 SAML 進行單一登錄。 如需其他處理單一登錄方式的詳細資訊(例如,使用 OpenID 連線 或整合式 Windows 驗證),請參閱在 Microsoft Entra ID 中單一登錄應用程式。
AuthnRequest
若要要求使用者驗證,雲端服務會將專案傳送 AuthnRequest 至 Microsoft Entra ID。 範例 SAML 2.0 AuthnRequest 可能看起來像下列範例:
<samlp:AuthnRequest
xmlns="urn:oasis:names:tc:SAML:2.0:metadata"
ID="id6c1c178c166d486687be4aaf5e482730"
Version="2.0" IssueInstant="2013-03-18T03:28:54.1839884Z"
xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion">https://www.contoso.com</Issuer>
</samlp:AuthnRequest>
| 參數 | 類型 | 描述 |
|---|---|---|
ID |
必要 | Microsoft Entra ID 會使用這個屬性填入 InResponseTo 傳回響應的屬性。 標識元不得以數字開頭,因此常見的策略是在 GUID 的字串表示前面加上字串,例如 「ID」。 例如, id6c1c178c166d486687be4aaf5e482730 是有效的標識碼。 |
Version |
必要 | 此參數應設定為 2.0。 |
IssueInstant |
必要 | 這是具有UTC值和 來回格式 (“o”) 的DateTime字串。 Microsoft Entra ID 預期此類型的 DateTime 值,但不會評估或使用該值。 |
AssertionConsumerServiceURL |
選擇性 | 如果提供,此參數必須符合 RedirectUri Microsoft Entra ID 中雲端服務的 。 |
ForceAuthn |
選擇性 | 這是布爾值。 如果為 true,表示使用者將強制重新驗證,即使他們具有具有 Microsoft Entra ID 的有效會話也一樣。 |
IsPassive |
選擇性 | 這是布爾值,指定如果存在,Microsoft Entra ID 是否應該以無訊息方式驗證使用者,而不需用戶互動。 如果這是真的,Microsoft Entra ID 會嘗試使用會話 Cookie 來驗證使用者。 |
會忽略所有其他屬性,例如 Consent、Destination、AssertionConsumerServiceIndex、 AttributeConsumerServiceIndex和 ProviderName 。AuthnRequest
Microsoft Entra ID 也會忽略 Conditions 中的 AuthnRequest專案。
簽發者
Issuer中的 AuthnRequest 元素必須完全符合 Microsoft Entra ID 中雲端服務中的其中一個 ServicePrincipalNames。 一般而言,這會設定為 應用程式註冊期間指定的應用程式標識碼 URI 。
包含元素的 Issuer SAML 摘錄看起來像下列範例:
<Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion">https://www.contoso.com</Issuer>
NameIDPolicy
此元素會要求回應中的特定名稱標識碼格式,而且在傳送至 Microsoft Entra ID 的元素中 AuthnRequest 是選擇性的。
元素 NameIdPolicy 看起來像下列範例:
<NameIDPolicy Format="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent"/>
如果 NameIDPolicy 提供 ,您可以包含其選擇性 Format 屬性。 屬性 Format 只能有下列其中一個值;任何其他值都會導致錯誤。
urn:oasis:names:tc:SAML:2.0:nameid-format:persistent:Microsoft Entra ID 會NameID發出宣告做為成對標識碼。urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress:Microsoft Entra ID 會NameID以電子郵件地址格式發出宣告。urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified:這個值允許 Microsoft Entra ID 選取宣告格式。 Microsoft Entra ID 會將NameID宣告發出為成對標識碼。urn:oasis:names:tc:SAML:2.0:nameid-format:transient:Microsoft Entra ID 會將NameID宣告發出為目前 SSO 作業唯一的隨機產生值。 這表示值是暫時的,無法用來識別驗證使用者。
如果 SPNameQualifier 已指定,Microsoft Entra ID 會在回應中包含相同的 SPNameQualifier 。
Microsoft Entra ID 會 AllowCreate 忽略 屬性。
RequestedAuthnContext
元素 RequestedAuthnContext 會指定所需的驗證方法。 在傳送至 Microsoft Entra 識別符的元素中 AuthnRequest ,這是選擇性的。 Microsoft Entra ID 支援 AuthnContextClassRef 之類的 urn:oasis:names:tc:SAML:2.0:ac:classes:Password值。
範圍
元素 Scoping 包含識別提供者清單,在傳送至 Microsoft Entra ID 的元素中 AuthnRequest 是選擇性的。
如果提供,請勿包含 ProxyCount 屬性 IDPListOption 或 RequesterID 專案,因為它們不受支援。
簽章
Signature元素中的AuthnRequest元素是選擇性的。 您可以設定 Microsoft Entra ID,以便強制要求已簽署的驗證要求。 如果已啟用,則只會接受已簽署的驗證要求,否則只會回應已註冊的判斷提示取用者服務 URL 來提供要求者驗證。
主體
請勿包含 Subject 專案。 Microsoft Entra ID 不支援在 中 AuthnRequest 指定主旨,如果提供主旨,則會傳回錯誤。
您可以將參數新增至單一 login_hint 登錄 URL,並將主體的 NameID 作為參數值,來改為提供主體的 NameID。
回應
當要求的登入成功完成時,Microsoft Entra ID 會張貼雲端服務的回應。 成功登入嘗試的回應如下所示:
<samlp:Response ID="_a4958bfd-e107-4e67-b06d-0d85ade2e76a" Version="2.0" IssueInstant="2013-03-18T07:38:15.144Z" Destination="https://contoso.com/identity/inboundsso.aspx" InResponseTo="id758d0ef385634593a77bdf7e632984b6" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion"> https://login.microsoftonline.com/aaaabbbb-0000-cccc-1111-dddd2222eeee/</Issuer>
<ds:Signature xmlns:ds="https://www.w3.org/2000/09/xmldsig#">
...
</ds:Signature>
<samlp:Status>
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success" />
</samlp:Status>
<Assertion ID="_bf9c623d-cc20-407a-9a59-c2d0aee84d12" IssueInstant="2013-03-18T07:38:15.144Z" Version="2.0" xmlns="urn:oasis:names:tc:SAML:2.0:assertion">
<Issuer>https://login.microsoftonline.com/aaaabbbb-0000-cccc-1111-dddd2222eeee/</Issuer>
<ds:Signature xmlns:ds="https://www.w3.org/2000/09/xmldsig#">
...
</ds:Signature>
<Subject>
<NameID>Uz2Pqz1X7pxe4XLWxV9KJQ+n59d573SepSAkuYKSde8=</NameID>
<SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<SubjectConfirmationData InResponseTo="id758d0ef385634593a77bdf7e632984b6" NotOnOrAfter="2013-03-18T07:43:15.144Z" Recipient="https://contoso.com/identity/inboundsso.aspx" />
</SubjectConfirmation>
</Subject>
<Conditions NotBefore="2013-03-18T07:38:15.128Z" NotOnOrAfter="2013-03-18T08:48:15.128Z">
<AudienceRestriction>
<Audience>https://www.contoso.com</Audience>
</AudienceRestriction>
</Conditions>
<AttributeStatement>
<Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name">
<AttributeValue>testuser@contoso.com</AttributeValue>
</Attribute>
<Attribute Name="http://schemas.microsoft.com/identity/claims/objectidentifier">
<AttributeValue>3F2504E0-4F89-11D3-9A0C-0305E82C3301</AttributeValue>
</Attribute>
...
</AttributeStatement>
<AuthnStatement AuthnInstant="2013-03-18T07:33:56.000Z" SessionIndex="_bf9c623d-cc20-407a-9a59-c2d0aee84d12">
<AuthnContext>
<AuthnContextClassRef> urn:oasis:names:tc:SAML:2.0:ac:classes:Password</AuthnContextClassRef>
</AuthnContext>
</AuthnStatement>
</Assertion>
</samlp:Response>
回應
元素 Response 包含授權要求的結果。 Microsoft Entra ID 會ID設定 元素中的 Response 、 Version 和 IssueInstant 值。 它也會設定下列屬性:
Destination:登入成功完成時,這會設定為RedirectUri服務提供者 (雲端服務) 的 。InResponseTo:這會設定為ID起始回應之AuthnRequest項目的 屬性。
簽發者
Microsoft Entra ID 會將 Issuer 元素設定為 https://sts.windows.net/<TenantIDGUID>/ ,其中 <TenantIDGUID> 是 Microsoft Entra 租使用者的租用戶標識符。
例如,具有Issuer元素的回應看起來可能類似下列範例:
<Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion"> https://sts.windows.net/aaaabbbb-0000-cccc-1111-dddd2222eeee/</Issuer>
狀態
元素 Status 會傳達登入的成功或失敗。 它包含 StatusCode 元素,其中包含程式碼或一組巢狀程序代碼,代表要求的狀態。 它也包含 StatusMessage 元素,其中包含登入程式期間產生的自定義錯誤訊息。
下列範例是 SAML 回應,以嘗試登入失敗。
<samlp:Response ID="_f0961a83-d071-4be5-a18c-9ae7b22987a4" Version="2.0" IssueInstant="2013-03-18T08:49:24.405Z" InResponseTo="iddce91f96e56747b5ace6d2e2aa9d4f8c" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion">https://sts.windows.net/aaaabbbb-0000-cccc-1111-dddd2222eeee/</Issuer>
<samlp:Status>
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Requester">
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:RequestUnsupported" />
</samlp:StatusCode>
<samlp:StatusMessage>AADSTS75006: An error occurred while processing a SAML2 Authentication request. AADSTS90011: The SAML authentication request property 'NameIdentifierPolicy/SPNameQualifier' is not supported.
Trace ID: 0000aaaa-11bb-cccc-dd33-eeeeee333333
Timestamp: 2013-03-18 08:49:24Z</samlp:StatusMessage>
</samlp:Status>
</samlp:Response>
Assertion
除了 ID、 IssueInstant 和 Version之外,Microsoft Entra ID 也會在回應的 元素中 Assertion 設定下列元素。
簽發者
這會設定為 https://sts.windows.net/<TenantIDGUID>/其中 <TenantIDGUID> 是 Microsoft Entra 租使用者的租用戶標識碼。
<Issuer>https://sts.windows.net/aaaabbbb-0000-cccc-1111-dddd2222eeee/</Issuer>
簽章
Microsoft Entra ID 會簽署判斷提示,以回應成功的登入。 元素 Signature 包含雲端服務可用來驗證來源的數字簽名,以驗證判斷提示的完整性。
為了產生此數字簽名,Microsoft Entra ID 會在其元數據檔的 元素中使用 IDPSSODescriptor 簽署密鑰。
<ds:Signature xmlns:ds="https://www.w3.org/2000/09/xmldsig#">
digital_signature_here
</ds:Signature>
主體
這會指定判斷提示中語句主體的原則。 它包含 NameID 元素,表示已驗證的使用者。 值 NameID 是目標標識碼,只會導向至令牌物件之服務提供者。 它是持續性的 - 它可以撤銷,但永遠不會重新指派。 它也不透明,因為它不會顯示使用者的任何專案,而且不能當做屬性查詢的標識碼使用。
項目的 Method 屬性 SubjectConfirmation 一律設定為 urn:oasis:names:tc:SAML:2.0:cm:bearer。
<Subject>
<NameID>Uz2Pqz1X7pxe4XLWxV9KJQ+n59d573SepSAkuYKSde8=</NameID>
<SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<SubjectConfirmationData InResponseTo="id758d0ef385634593a77bdf7e632984b6" NotOnOrAfter="2013-03-18T07:43:15.144Z" Recipient="https://contoso.com/identity/inboundsso.aspx" />
</SubjectConfirmation>
</Subject>
條件
這個專案會指定條件,以定義可接受的 SAML 判斷提示用法。
<Conditions NotBefore="2013-03-18T07:38:15.128Z" NotOnOrAfter="2013-03-18T08:48:15.128Z">
<AudienceRestriction>
<Audience>https://www.contoso.com</Audience>
</AudienceRestriction>
</Conditions>
NotBefore和 NotOnOrAfter 屬性會指定判斷提示有效的間隔。
- 屬性的值
NotBefore等於或稍微 (小於一秒)晚於 元素的IssueInstantAssertion屬性值。 Microsoft Entra ID 不會考慮本身與雲端服務(服務提供者)之間的任何時間差異,而且不會在此時間新增任何緩衝區。 - 屬性的值
NotOnOrAfter比 屬性的值NotBefore晚 70 分鐘。
受眾
這包含可識別預定物件的 URI。 Microsoft Entra ID 會將這個專案的值設定為起始登入之 的 AuthnRequest 元素值Issuer。 若要評估 Audience 值,請使用應用程式註冊期間所指定的 值 App ID URI 。
<AudienceRestriction>
<Audience>https://www.contoso.com</Audience>
</AudienceRestriction>
Issuer與值一樣,Audience值必須完全符合其中一個服務主體名稱,以 Microsoft Entra ID 表示雲端服務。 不過,如果元素的值 Issuer 不是 URI 值, Audience 回應中的值會是 Issuer 前面加上 spn:的值。
AttributeStatement
這包含有關主體或使用者的宣告。 下列摘錄包含範例 AttributeStatement 專案。 省略號表示元素可以包含多個屬性和屬性值。
<AttributeStatement>
<Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name">
<AttributeValue>testuser@contoso.com</AttributeValue>
</Attribute>
<Attribute Name="http://schemas.microsoft.com/identity/claims/objectidentifier">
<AttributeValue>3F2504E0-4F89-11D3-9A0C-0305E82C3301</AttributeValue>
</Attribute>
...
</AttributeStatement>
- 名稱宣告 - 屬性的值
Name(http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name) 是已驗證使用者的使用者主體名稱,例如testuser@managedtenant.com。 - ObjectIdentifier Claim - 屬性 (
http://schemas.microsoft.com/identity/claims/objectidentifier) 的值ObjectIdentifier是ObjectId目錄物件的 ,代表 Microsoft Entra ID 中已驗證的使用者。ObjectId是固定、全域唯一且重複使用已驗證使用者的安全標識碼。
AuthnStatement
此元素會判斷提示主體在特定時間透過特定方式進行驗證。
- 屬性
AuthnInstant會指定使用者以 Microsoft Entra ID 進行驗證的時間。 - 元素
AuthnContext會指定用來驗證使用者的驗證內容。
<AuthnStatement AuthnInstant="2013-03-18T07:33:56.000Z" SessionIndex="_bf9c623d-cc20-407a-9a59-c2d0aee84d12">
<AuthnContext>
<AuthnContextClassRef> urn:oasis:names:tc:SAML:2.0:ac:classes:Password</AuthnContextClassRef>
</AuthnContext>
</AuthnStatement>