Microsoft 身分識別平台 中的許可權和同意概觀
若要 存取 受保護的資源,例如電子郵件或行事曆數據,您的應用程式需要資源擁有者的 授權。 資源擁有者可以 同意 或拒絕應用程式的要求。 了解這些基本概念可協助您建置更安全且可信任的應用程式,只要求使用者和系統管理員存取所需的存取權。
存取情節
身為應用程式開發人員,您必須識別應用程式如何存取數據。 應用程式可以使用委派的存取權、代表登入的使用者或僅限應用程式存取權,只做為應用程式自己的身分識別。
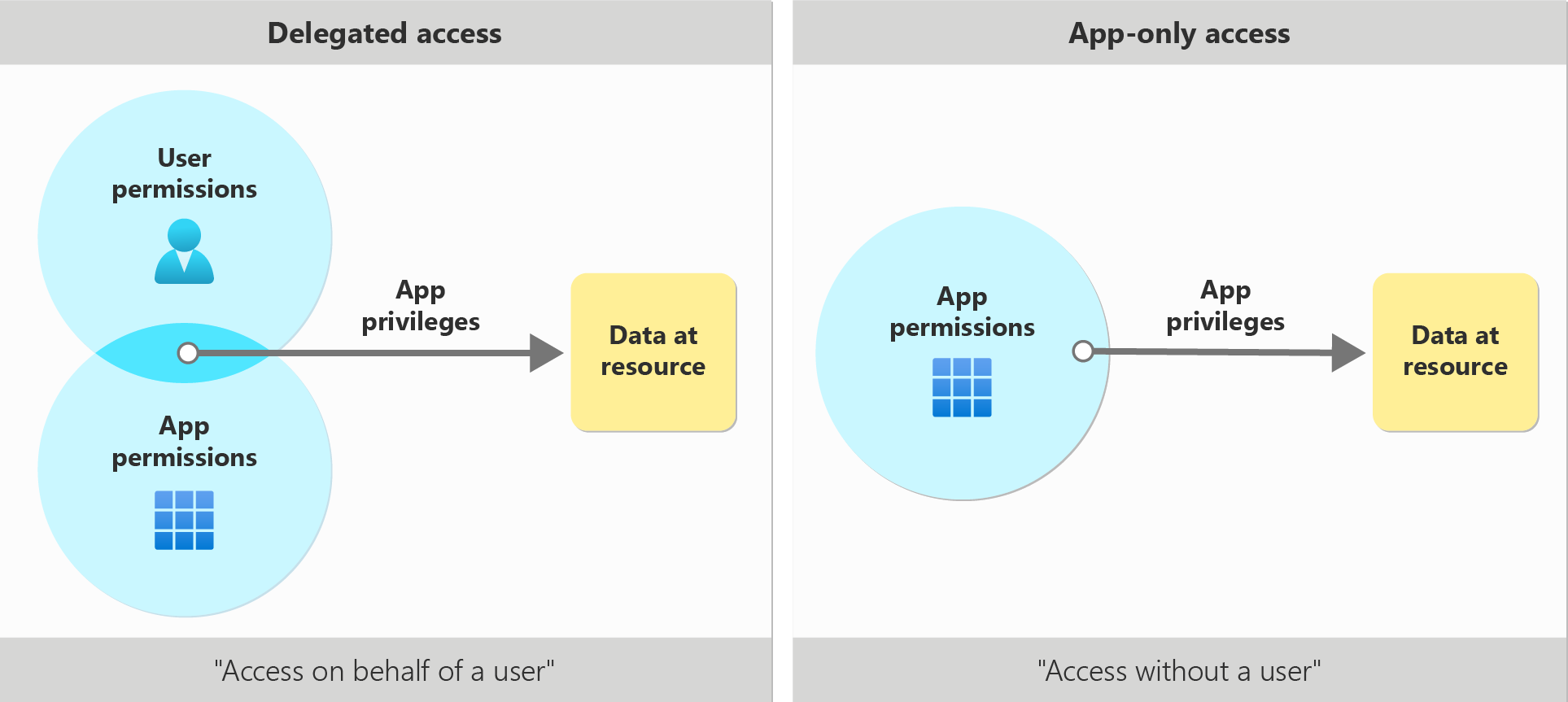
委派存取權(代表使用者存取權)
在此存取案例中,使用者已登入用戶端應用程式。 用戶端應用程式會代表使用者存取資源。 委派存取需要委派的許可權。 用戶端和用戶都必須分別獲得授權,才能提出要求。 如需委派存取案例的詳細資訊,請參閱 委派存取案例。
針對用戶端應用程式,必須授與正確的委派許可權。 委派的許可權也可以稱為範圍。 範圍是指定資源的許可權,代表用戶端應用程式可以代表使用者存取的內容。 如需範圍的詳細資訊,請參閱 範圍和許可權。
針對使用者,授權會依賴使用者已授與的許可權,讓他們存取資源。 例如,用戶可以獲得 Microsoft Entra 角色型存取控制 (RBAC) 存取目錄資源的授權,或透過 Exchange Online RBAC 存取郵件和行事歷資源。 如需應用程式 RBAC 的詳細資訊,請參閱 RBAC for applications。
只限應用程式存取權 (沒有使用者存取權)
在此存取案例中,應用程式會自行運作,且沒有使用者登入。 應用程式存取適用於自動化和備份等案例。 此案例包含以背景服務或精靈身分執行的應用程式。 如果不想讓特定使用者登入,或當所需的數據不能限定為單一使用者時,就很合適。 如需僅限應用程式存取案例的詳細資訊,請參閱 僅限應用程式存取。
僅限應用程式存取會使用應用程式角色,而不是委派的範圍。 透過同意授與時,應用程式角色也可能稱為應用程式許可權。 用戶端應用程式必須獲授與其呼叫之資源應用程式的適當應用程式許可權。 授與之後,用戶端應用程式就可以存取要求的數據。 如需將應用程式角色指派給用戶端應用程式的詳細資訊,請參閱 將應用程式角色指派給應用程式。
權限類型
委派的許可權 會用於委派存取案例中。 這些權限可讓應用程式代表使用者採取行動。 應用程式永遠無法存取登入使用者本身無法存取的任何專案。
例如,採用已代表使用者授與 Files.Read.All 委派許可權的應用程式。 應用程式只能讀取使用者可以個人存取的檔案。
應用程式許可權,也稱為應用程式角色,用於僅限應用程式存取案例,沒有登入的使用者存在。 應用程式將能夠存取與許可權相關聯的任何數據。
例如,授與 Microsoft Graph API 應用程式許可權 Files.Read.All 的應用程式將能夠使用 Microsoft Graph 讀取租使用者中的任何檔案。 一般而言,只有 API 服務主體的系統管理員或擁有者可以同意該 API 公開的應用程式許可權。
委派和應用程式許可權的比較
| 權限類型 | 委派的權限 | 應用程式權限 |
|---|---|---|
| 應用程式類型 | Web / 行動 / 單頁應用程式 (SPA) | Web/精靈 |
| 存取內容 | 代表使用者進行存取 | 無需使用者即進行存取 |
| 有權同意者 | - 用戶可以同意其數據 - 管理員 可以同意所有使用者 |
僅管理員可同意 |
| 同意方法 | - 靜態:應用程式註冊的已設定清單 - 動態:在登入時要求個別許可權 |
- 僅限靜態:在應用程式註冊上設定的清單 |
| 其他名稱 | -範圍 - OAuth2 許可權範圍 |
- 應用程式角色 - 僅限應用程式的許可權 |
| 同意結果(Microsoft Graph 專屬) | OAuth2PermissionGrant | 應用程式角色指派 |
同意
授與應用程式許可權的其中一種方式是透過同意。 同意是使用者或系統管理員授權應用程式存取受保護資源的程序。 例如,當使用者第一次嘗試登入應用程式時,應用程式可以要求許可權來查看使用者的配置檔,並讀取使用者信箱的內容。 使用者會看到應用程式透過同意提示要求的許可權清單。 使用者可能會看到同意提示的其他案例包括:
- 撤銷先前授與同意的時機。
- 將應用程式編碼為在登入期間特別提示同意時。
- 當應用程式使用動態同意在運行時間視需要要求新許可權時。
同意提示的主要詳細數據是應用程式所需的許可權清單和發行者資訊。 如需有關系統管理員和使用者同意提示和同意體驗的詳細資訊,請參閱 應用程式同意體驗。
使用者同意
當使用者嘗試登入應用程式時,就會發生使用者同意。 使用者會提供其登入認證,其會檢查以判斷是否已授與同意。 如果先前沒有使用者或系統管理員同意所需的許可權記錄存在,則會顯示使用者同意提示,並要求將要求的許可權授與應用程式。 系統管理員可能需要代表使用者授與同意。
管理員 istrator 同意
根據他們所需的許可權,某些應用程式可能需要系統管理員成為授與同意者。 例如,應用程式許可權和許多高許可權委派許可權只能由系統管理員同意。
管理員 istrator 可以為自己或整個組織授與同意。 如需使用者和系統管理員同意的詳細資訊,請參閱 使用者和系統管理員同意概觀。
如果未授與同意,以及其中一個要求高許可權許可權許可權,系統會提示要求系統管理員同意驗證要求。
包含自定義應用程式範圍的許可權要求不會被視為高許可權,因此不需要管理員同意。
預先授權
預先授權可讓資源應用程式擁有者授與許可權,而不需要使用者查看已預先授權之相同許可權集的同意提示。 如此一來,預先授權的應用程式將不會要求使用者同意許可權。 資源擁有者可以在 Azure 入口網站 或使用PowerShell和 API,例如 Microsoft Graph 預先授權用戶端應用程式。