什麼是 Identity Protection?
Microsoft Entra ID Protection 可協助組織偵測、調查和修復身分識別型風險。 這些身分識別型風險可進一步饋送至條件式存取之類的工具,以做出存取決策,或饋送回安全性資訊與事件管理 (SIEM) 工具,以進行深入調查和相互關聯。
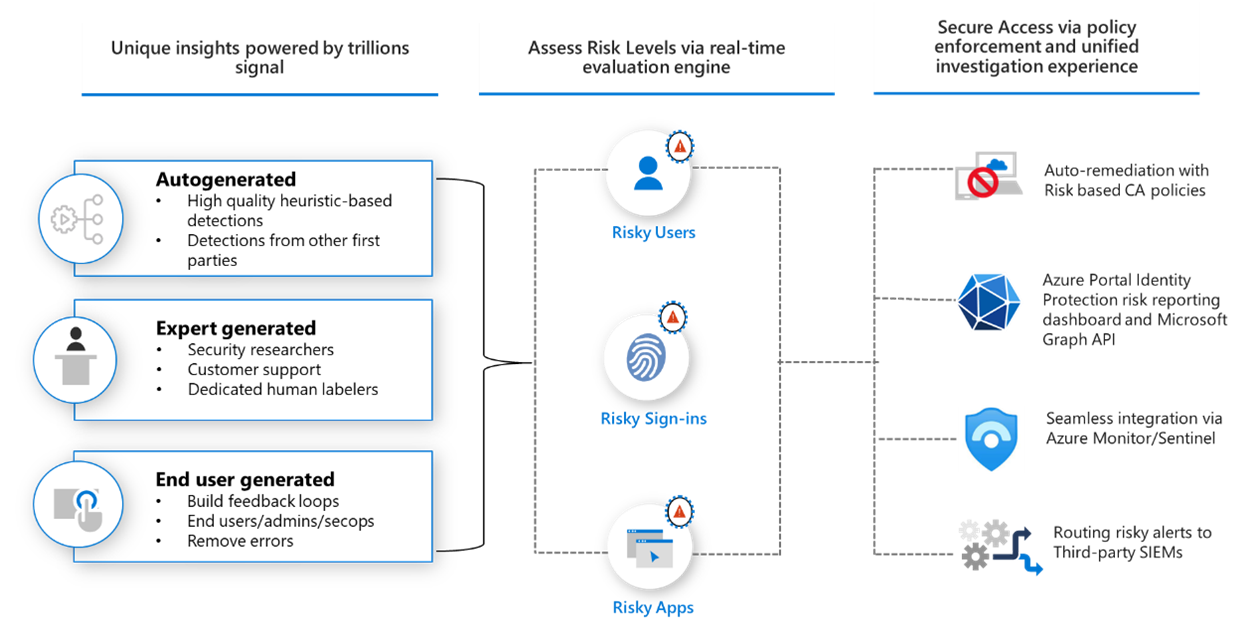
偵測風險
Microsoft 會持續在我們的目錄中新增和更新偵測,以保護組織。 這些偵測來自於我們每天對來自 Active Directory、Microsoft 帳戶和 Xbox 遊戲的數兆個訊號的分析。 這種廣泛的訊號有助於 Identity Protection 偵測危險行為,例如:
- 匿名 IP 位址使用
- 密碼噴灑攻擊
- 認證外洩
- 還有更多...
在每個登入期間,Identity Protection 會執行所有產生登入會話風險層級的即時登入偵測,指出登入遭到入侵的可能性。 系統會根據此風險層級接著套用原則來保護使用者和組織。
如需風險的完整清單及其偵測方式,請參閱什麼是風險一文。
調查
系統會追蹤在身分識別上偵測到的任何風險,並提供報告。 Identity Protection 提供三個主要報告,可讓系統管理員調查風險並採取行動:
- 風險偵測:偵測到的每個風險都會回報為風險偵測。
- 風險性登入:當有一或多個針對該登入回報的風險偵測時,即會回報風險性登入。
- 風險性使用者:當下列任一項或兩者都成立時,即會回報風險性使用者:
- 使用者有一或多個風險性登入。
- 報告一或多個風險偵測。
如需如何使用報告的詳細資訊,請參閱如何:調查風險一文。
修復風險
為什麼自動化在安全性方面很重要?
在部落格文章 網路訊號:使用 2022 年 2 月 3 日日期的最新研究、見解和趨勢 來防禦網路威脅時,Microsoft 分享了威脅情報簡報,包括下列統計數據:
分析 ...我們結合 24 兆個安全性訊號,與監視 40 個以上國家/地區狀態群組和 140 個以上威脅群組的追蹤情報...
...從 2021 年 1 月到 2021 年 12 月,我們已封鎖超過 256 億 Microsoft Entra 暴力密碼破解驗證攻擊...
信號和攻擊的更大規模需要一些程度的自動化才能跟上。
自動補救
您可以啟用風險型條件式存取 原則,以要求訪問控制,例如提供強身份驗證方法、執行多重要素驗證,或根據偵測到的風險等級執行安全密碼重設。 如果使用者成功完成存取控制,風險即會自動補救。
手動補救
未啟用使用者補救時,系統管理員必須在入口網站、透過 API 或在 Microsoft 365 Defender 中手動檢閱報告中的風險。 系統管理員可以執行手動動作,以消除風險、確認安全或確認風險的危害。
運用資料
Identity Protection 中的資料可匯出至其他工具以進行封存、進一步調查和建立相互關聯。 以 Microsoft Graph 為基礎的 API 可讓組織收集這項資料,以便在 SIEM 之類的工具中進一步處理。 如需如何存取 Identity Protection API 的相關信息,請參閱開始使用 Microsoft Entra ID Protection 和 Microsoft Graph 一文
如需將 Identity Protection 資訊與 Microsoft Sentinel 整合的相關信息,請參閱 Microsoft Entra ID Protection 中的數據 連線 一文。
組織可能會藉由變更 Microsoft Entra 識別碼中的診斷設定,來儲存較長期間的數據。 他們可以選擇將資料傳送至 Log Analytics 工作區、將資料封存至儲存體帳戶、將資料串流至事件中樞,或將資料傳送至另一個解決方案。 如需執行方式的詳細資訊,請參閱操作說明:匯出風險資料一文。
必要角色
Identity Protection 要求用戶獲指派下列一或多個角色才能存取。
| Role | Can do | Can't do |
|---|---|---|
| 安全性系統管理員 | 完整存取 Identity Protection | 重設使用者的密碼 |
| 安全性操作員 | 檢視所有 Identity Protection 報告和概觀 解除使用者風險、確認安全登入、確認洩漏 |
設定或變更原則 重設用戶的密碼 設定警示 |
| 安全性讀取者 | 查看所有 Identity Protection 報告和概觀 | 設定或變更原則 重設用戶的密碼 設定警示 在偵測上提供意見反應 |
| 全域讀取器 | 唯讀存取 Identity Protection | |
| 使用者管理員 | 重設用戶密碼 |
目前,安全性操作員角色無法存取風險性登入報告。
條件式存取系統管理員可以建立原則,以將使用者或登入風險視為條件。 在下列文章中尋找詳細資訊:條件式存取:條件。
授權需求
使用此功能需要 Microsoft Entra ID P2 授權。 若要尋找適合您需求的授權,請參閱比較 Microsoft Entra ID 正式推出的功能。
| 功能 | 詳細資料 | Microsoft Entra ID Free / Microsoft 365 Apps | Microsoft Entra ID P1 | Microsoft Entra ID P2 |
|---|---|---|---|---|
| 風險原則 | 登入和用戶風險原則(透過 Identity Protection 或條件式存取) | No | 無 | 是 |
| 安全性報告 | 概觀 | 否 | 無 | 是 |
| 安全性報告 | 具風險使用者 | 有限資訊。 只會顯示具有中等和高風險的使用者。 沒有詳細資料選單,也沒有風險歷程記錄。 | 有限資訊。 只會顯示具有中等和高風險的使用者。 沒有詳細資料選單,也沒有風險歷程記錄。 | 完整存取 |
| 安全性報告 | 有風險的登入 | 有限資訊。 不會顯示任何風險詳細資料或風險層級。 | 有限資訊。 不會顯示任何風險詳細資料或風險層級。 | 完整存取 |
| 安全性報告 | 風險偵測 | 否 | 有限資訊。 沒有詳細資料選單。 | 完整存取 |
| 通知 | 偵測到具風險使用者的警示 | 否 | 無 | 是 |
| 通知 | 每週摘要 | 否 | 無 | 是 |
| MFA 註冊原則 | 否 | 無 | 是 |
如需這些豐富報告的詳細資訊,請參閱下列文章:如何:調查風險。
若要使用工作負載身分識別風險,包括系統管理中心 [風險偵測] 窗格中的 [具風險工作負載身分識別] 和 [工作負載身分識別偵測] 索引卷標,您必須擁有工作負載身分識別 進階版 授權。 如需詳細資訊,請參閱保護工作負載身分識別一文。