教學課程:Microsoft Entra SSO 與 BIC 程式設計整合
在本教學課程中,您將瞭解如何整合 BIC 程式設計與 Microsoft Entra ID。 在整合 BIC 程式設計與 Microsoft Entra ID 時,您可以.
- 在 Microsoft Entra 識別碼中控制可存取 BIC 程式設計的人員。
- 讓使用者使用其 Microsoft Entra 帳戶自動登入 BIC 程序設計。
- 在一個中央位置管理您的帳戶。
必要條件
若要開始使用,您需要下列專案:
- Microsoft Entra 訂用帳戶。 如果您沒有訂用帳戶,可以取得免費帳戶。
- 已啟用 BIC 程式設計單一登入 (SSO) 的訂用帳戶。
注意
此整合也可從 Microsoft Entra US Government Cloud 環境使用。 您可以在 Microsoft Entra US Government 雲端應用連結庫中找到此應用程式,並以您從公用雲端所做的相同方式進行設定。
案例描述
在本教學課程中,您會在測試環境中設定及測試 Microsoft Entra SSO。
- BIC 進程設計支援 由SP 起始的 SSO。
- BIC 程式設計支援 自動使用者布建。
從資源庫新增 BIC 程序設計
若要設定將 BIC 程式設計整合到 Microsoft Entra ID 中,您需要從資源庫將 BIC 程式設計新增到受控 SaaS 應用程式清單。
- 以至少雲端應用程式 管理員 istrator 身分登入 Microsoft Entra 系統管理中心。
- 流覽至 [身分>識別應用程式>企業應用程式>] [新增應用程式]。
- 在 [ 從資源庫 新增] 區段的搜尋方塊中,輸入 BIC 程序設計 。
- 從結果面板中選取 [BIC 程式設計 ],然後新增應用程式。 將應用程式新增至您的租使用者時,請稍候幾秒鐘。
或者,您也可以使用企業 應用程式組態 精靈。 在此精靈中,您可以將應用程式新增至租使用者、將使用者/群組新增至應用程式、指派角色,以及逐步解說 SSO 設定。 深入瞭解 Microsoft 365 精靈。
設定及測試 BIC 程式設計的 Microsoft Entra SSO
以名為 B.Simon 的測試用戶,設定及測試與 BIC Process Design 搭配運作的 Microsoft Entra SSO。 若要讓 SSO 能夠運作,您必須建立 Microsoft Entra 使用者與 BIC 程式設計中相關使用者之間的連結關聯性。
若要設定及測試與 BIC 行程設計搭配運作的 Microsoft Entra SSO,請執行下列步驟:
- 設定 Microsoft Entra SSO - 讓使用者能夠使用此功能。
- 建立 Microsoft Entra 測試使用者 - 以使用 B.Simon 測試 Microsoft Entra 單一登錄。
- 指派 Microsoft Entra 測試使用者 - 讓 B.Simon 能夠使用 Microsoft Entra 單一登錄。
- 設定 BIC 程式設計 SSO - 在應用程式端設定單一登入設定。
- 建立 BIC Process Design 測試使用者 - 使 BIC Process Design 中對應的 B.Simon 連結到該使用者在 Microsoft Entra 中的代表專案。
- 測試 SSO - 確認組態是否正常運作。
設定 Microsoft Entra SSO
請遵循下列步驟來啟用 Microsoft Entra SSO。
以至少雲端應用程式 管理員 istrator 身分登入 Microsoft Entra 系統管理中心。
流覽至 [身分>識別應用程式企業應用程式>>] BIC 程式設計>單一登錄。
在 [ 選取單一登錄方法] 頁面上,選取 [SAML]。
在 [使用 SAML 設定單一登錄] 頁面上,按兩下 [基本 SAML 組態] 的鉛筆圖示以編輯設定。

在 [ 基本 SAML 組態 ] 區段上,如果您有 服務提供者元數據檔案,請執行下列步驟:
a. 按兩下 [ 上傳元數據檔案]。

b. 按兩下 資料夾標誌 以選取元資料檔案,然後按兩下 [ 上傳]。
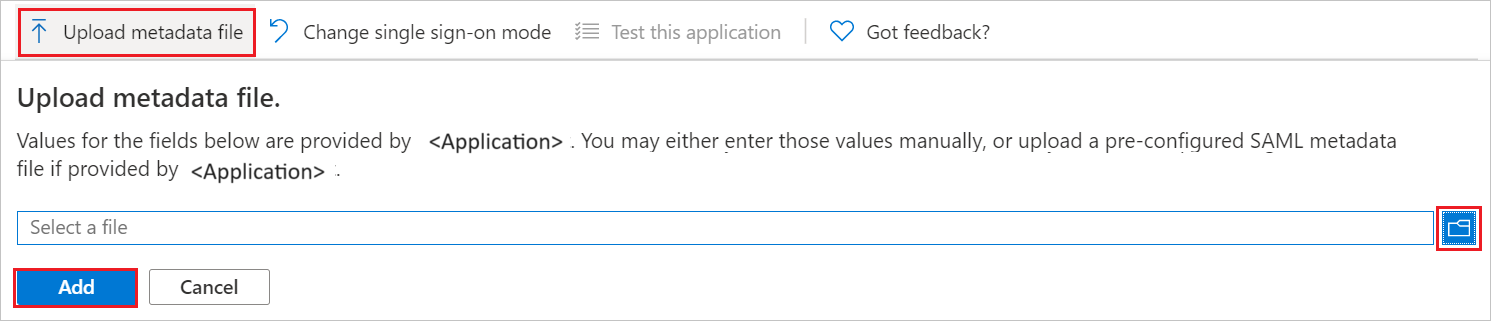
c. 成功上傳元數據檔案之後, [基本 SAML 組態] 區段中會自動填入 [標識符 ] 值。
d. 在 [ 登入 URL ] 文字框中,使用下列其中一種模式輸入 URL:
登入 URL https://<CUSTOMER_SPECIFIC_NAME/TENANT>.biccloud.comhttps://<CUSTOMER_SPECIFIC_NAME/TENANT>.biccloud.de注意
如果標識碼值未自動填入,請根據您的需求手動填入值。 登入 URL 值不是真實的。 使用實際的登入 URL 更新此值。 請連絡 BIC 程式設計用戶端支援小組 以取得此值。 您也可以參考基本 SAML 組態一節中顯示的模式。
BIC 程式設計應用程式需要特定格式的 SAML 判斷提示,因此您必須將自訂屬性對應新增至 SAML 令牌屬性組態。 下列螢幕快照顯示預設屬性的清單。
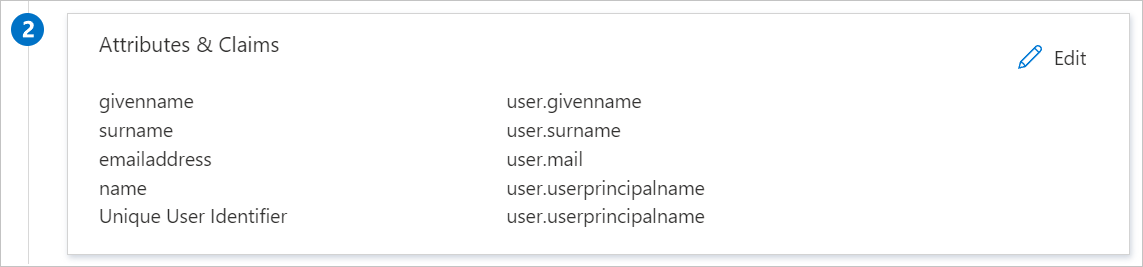
除了上述屬性外,BIC 程式設計應用程式還需要在 SAML 回應中多傳回幾個屬性,如下所示。 這些屬性也會預先填入,但您可以根據您的需求檢閱這些屬性。
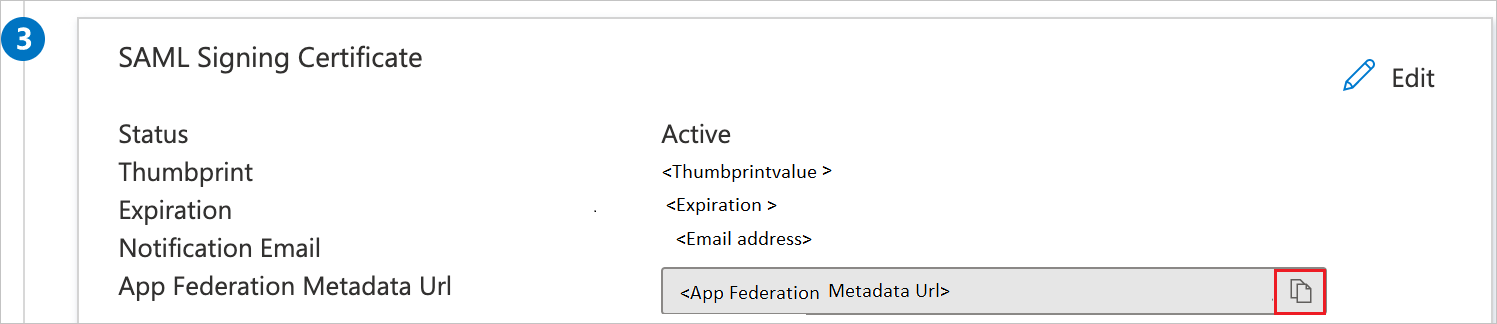
名稱 來源屬性 名稱 user.name 電子郵件地址 user.mail 名稱 ID user.userprincipalname 電子郵件 user.mail nametest user.displayname 在 [ 使用 SAML 設定單一登錄] 頁面上的 [SAML 簽署憑證 ] 區段中,按兩下 [複製] 按鈕以複製 [應用程式同盟元數據 URL ],並將其儲存在您的電腦上。
建立 Microsoft Entra 測試使用者
在本節中,您將建立名為 B.Simon 的測試使用者。
- 以至少使用者 管理員 istrator 身分登入 Microsoft Entra 系統管理中心。
- 流覽至 [身分>識別使用者>所有使用者]。
- 選取畫面頂端的 [新增使用者>建立新使用者]。
- 在 [ 用戶 屬性] 中,遵循下列步驟:
- 在 [ 顯示名稱] 欄位中, 輸入
B.Simon。 - 在 [ 使用者主體名稱] 欄位中, 輸入 username@companydomain.extension。 例如:
B.Simon@contoso.com。 - 選取 [顯示密碼] 複選框,然後記下 [密碼] 方塊中顯示的值。
- 選取 [檢閱 + 建立]。
- 在 [ 顯示名稱] 欄位中, 輸入
- 選取 建立。
指派 Microsoft Entra 測試使用者
在本節中,您會將 BIC 進程設計的存取權授與 B.Simon,讓其能夠使用單一登錄。
- 以至少雲端應用程式 管理員 istrator 身分登入 Microsoft Entra 系統管理中心。
- 流覽至 [身分>識別應用程式>企業應用程式>] BIC 程式設計。
- 在應用程式的 [概觀] 頁面中,選取 [ 使用者和群組]。
- 選取 [新增使用者/群組],然後在 [新增指派] 對話框中選取 [使用者和群組]。
- 在 [ 使用者和群組] 對話框中,從 [使用者] 列表中選取 B.Simon ,然後按兩下畫面底部的 [ 選取 ] 按鈕。
- 如果您預期將角色指派給使用者,您可以從 [選取角色] 下拉式清單中選取該 角色 。 如果未為此應用程式設定任何角色,您會看到已選取 [預設存取] 角色。
- 在 [新增指派] 對話框中,按兩下 [指派] 按鈕。
設定 BIC 程式設計 SSO
若要在 BIC 程式設計端設定單一登錄,您必須將應用程式同盟元數據 URL 傳送給 BIC 程式設計支援小組。 此設定是為了正確設定雙方的 SAML SSO 連線。
建立 BIC 程式設計測試使用者
在本節中,您會在 BIC 程式設計中建立名為 B.Simon 的使用者。 請與 BIC 程式設計支援小組合作 ,在 BIC 程式設計平臺中新增使用者。 用戶必須先建立並啟用,才能使用單一登錄。
測試 SSO
在本節中,您會使用下列選項來測試您的 Microsoft Entra 單一登錄設定。
按兩下 [ 測試此應用程式],這會重新導向至您可以起始登入流程的 BIC 進程設計登入 URL。
直接移至 BIC 程式設計登入 URL,然後從該處起始登入流程。
您可以使用 Microsoft 我的應用程式。 當您在 我的應用程式 中按兩下 [BIC 程式設計] 圖格時,這會重新導向至 BIC 程式設計登入 URL。 如需詳細資訊,請參閱 Microsoft Entra 我的應用程式。
下一步
設定 BIC 程式設計後,您可以強制執行工作階段控制項,以即時防止組織的敏感數據遭到外洩和滲透。 會話控件會從條件式存取延伸。 瞭解如何使用 Microsoft 雲端 App 安全性 強制執行工作階段控制件。