在 Azure Kubernetes Service (AKS) 中設定 Azure CNI 網路
本文顯示如何使用 Azure CNI 網路,以針對 AKS 叢集建立和使用虛擬網路子網路。 如需網路選項和考量的詳細資訊,請參閱 Kubernetes 和 AKS 的網路概念。
必要條件
- 具有有效訂用帳戶的 Azure 帳戶。 免費建立帳戶。
設定網路
如需規劃 AKS 叢集的 IP 定址的相關資訊,請參閱規劃叢集的 IP 定址。
登入 Azure 入口網站。
在入口網站頂端的搜尋方塊中,輸入 Kubernetes services,然後從搜尋結果中選取 [Kubernetes services]。
選取 [+ 建立],然後選取 [建立 Kubernetes 叢集]。
在 [建立 Kubernetes 叢集] 中,輸入或選取下列資訊:
設定 值 專案詳細資料 訂用帳戶 選取您的訂用帳戶。 資源群組 選取 [test-rg]。 叢集詳細資料 叢集預設設定 保留預設值 [生產標準]。 Kubernetes 叢集名稱 輸入 aks-cluster。 區域 選取 [(美國) 美國東部 2]。 可用性區域 保留預設值 [區域 1、2、3]。 AKS 定價層 保留預設值 [標準]。 Kubernetes 版本 保留預設值 [1.26.6]。 自動升級 保留預設值 [啟用時使用修補 (建議)]。 驗證和授權 保留預設值 [具有 Kubernetes RBAC 的本機帳戶]。 選取 [下一步: 節點集區 >] ,然後選取 [下一步: 網路 >]。
在 [網路] 索引標籤的 [容器網路] 中,確認已選取 [Azure CNI]。
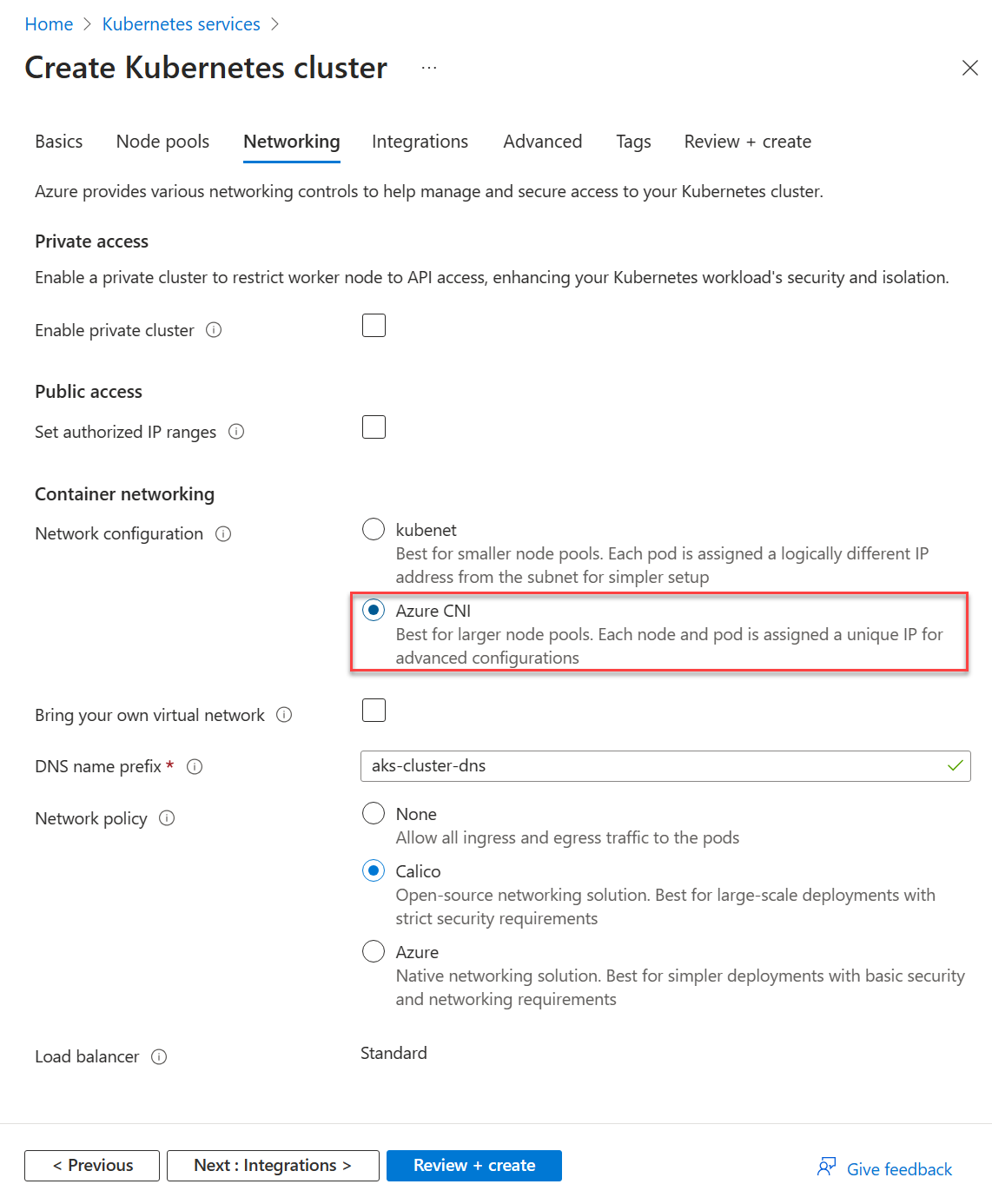
選取 [檢閱 + 建立]。
選取 建立。
下一步
若要設定具有動態 IP 配置和增強型子網路支援的 Azure CNI 網路,請參閱在 AKS 中設定 Azure CNI 網路,以動態配置 IP 並增強子網路支援。