在 Azure App Service 中使用 TLS/SSL 繫結保護自訂 DNS 名稱
本文說明如何藉由建立憑證繫結,在您的 App Service 應用程式或函式應用程式中保護自訂網域。 完成此作業後,您將可在自訂 DNS 名稱的 https:// 端點存取您的 App Service 應用程式 (例如 https://www.contoso.com)。

必要條件
- 將 App Service 應用程式擴大為其中一個支援的價格層:基本、標準、進階。
- 將網域名稱對應至應用程式或在 Azure 中加以購買與設定。
1.新增繫結
在 Azure 入口網站:
從左側功能表選取 [應用程式服務]><app-name>。
在應用程式頁面的左側導覽中,選取 [自訂網域]
在自訂網域旁,選取 [新增繫結]
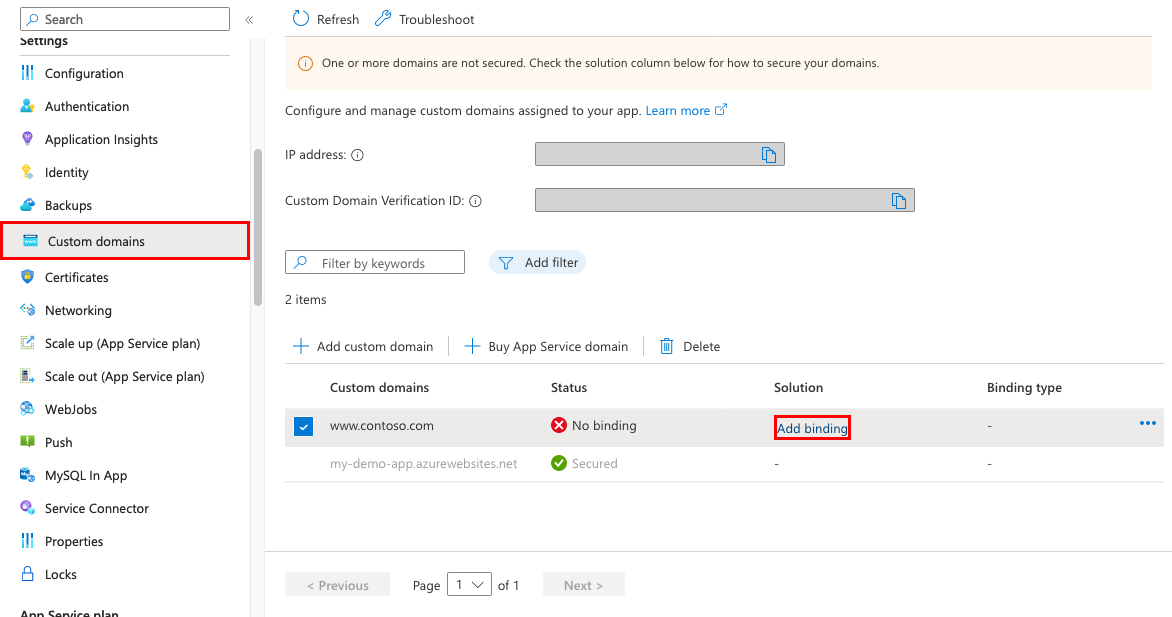
如果應用程式已經有所選自訂網域的憑證,則可以在 [憑證] 中選取該憑證。 如果沒有,您必須使用來源中的其中一個選取項目來新增憑證。
- 建立 App Service 受控憑證:讓 App Service 為所選網域建立受控憑證。 這是最簡單的選項。 如需詳細資訊,請參閱建立免費的受控憑證。
- 匯入 App Service 憑證:在 App Service 憑證中,選擇您為所選網域購買的 App Service 憑證。
- 上傳憑證 (.pfx):請遵循上傳私人憑證的工作流程,以從本機機器上傳 PFX 憑證並指定憑證密碼。
- 從金鑰保存庫匯入:選取 [選取金鑰保存庫憑證],然後在對話方塊中選取該憑證。
在 TLS/SSL 類型中,在 SNI SSL 和 IP 型 SSL 之間選擇。
- SNI SSL:可新增多個 SNI SSL 繫結。 此選項可允許多個 TLS/SSL 憑證保護同一個 IP 位址上的多個網域。 現今大部分的瀏覽器 (包括 Internet Explorer、Chrome、Firefox 和 Opera) 都支援 SNI (如需詳細資訊,請參閱伺服器名稱指示)。
-
- IP 型 SSL:只能新增一個 IP SSL 繫結。 此選項只允許一個 TLS/SSL 憑證保護專用的公用 IP 位址。 設定繫結之後,請依照 2.為 IP 型 SSL 重新對應記錄中的步驟執行。
只有在標準層或更高的層級才支援 IP SSL。
- IP 型 SSL:只能新增一個 IP SSL 繫結。 此選項只允許一個 TLS/SSL 憑證保護專用的公用 IP 位址。 設定繫結之後,請依照 2.為 IP 型 SSL 重新對應記錄中的步驟執行。
新增憑證時,請選取 [驗證] 來驗證新的憑證。
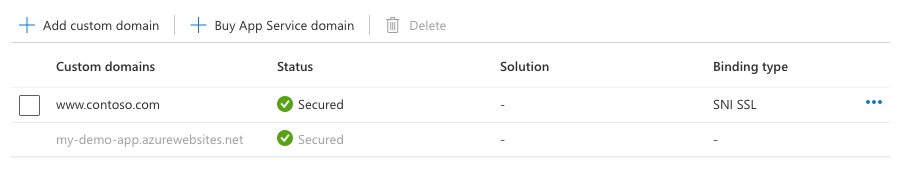
選取 [新增]。
作業完成後,自訂網域的 TLS/SSL 狀態會變更為安全。
注意
自訂網域中的安全狀態表示網域已透過憑證來保護,但是 App Service 不會檢查憑證是否已自我簽署或已過期等等,而這些狀況會導致瀏覽器顯示錯誤或警告。
2.為 IP 型 SSL 重新對應記錄
只有 IP 型 SSL 才需要此步驟。 針對 SNI SSL 繫結,請跳至測試自訂網域的 HTTPS。
您可能需要進行兩個變更:
根據預設,您的應用程式會使用共用的公用 IP 位址。 當您將憑證與 IP SSL 繫結時,App Service 會為您的應用程式建立新的專用 IP 位址。 如果您已將 A 記錄對應至應用程式,請使用這個新的專用 IP 位址來更新網域登錄。
應用程式的 [自訂網域] 頁面即會使用新的專用 IP 位址加以更新。 複製此 IP 位址,然後將 A 記錄重新對應至這個新的 IP 位址。
如果您有繫結至
<app-name>.azurewebsites.net的 SNI SSL,請重新對應任何 CNAME 對應,以改為指向sni.<app-name>.azurewebsites.net(新增sni前置詞)。
3.測試 HTTPS
在各種瀏覽器中瀏覽至 https://<your.custom.domain>,以確認它是否為您的應用程式提供服務。

您的應用程式程式碼可以透過 "x-appservice-proto" 標頭來檢查通訊協定。 標頭值為 http 或 https。
注意
如果您的應用程式出現憑證驗證錯誤,您可能使用了自我簽署憑證。
如果不是,在您將憑證匯出為 PFX 檔案時,可能遺漏了中繼憑證。
常見問題集
- 如何確定應用程式 IP 位址在變更憑證繫結時不會變更?
- 我可以將從 HTTP 至 HTTPS 的強制重新導向停用嗎?
- 如何變更應用程式的最低 TLS 版本?
- 如何在 App Service 中處理 TLS 終止?
如何在變更憑證繫結時,確定應用程式的 IP 位址不會變更?
當您刪除繫結時,您可以變更輸入 IP 位址,即使該繫結是 IP SSL 亦然。 當您更新已在 IP SSL 繫結中的憑證時,這一點尤為重要。 若要避免變更應用程式的 IP 位址,請依序執行下列步驟:
- 上傳新憑證。
- 將新的憑證繫結至您要的自訂網域,而不刪除舊憑證。 此動作會取代繫結,而不會移除舊的繫結。
- 刪除舊的憑證。
我可以將從 HTTP 至 HTTPS 的強制重新導向停用嗎?
根據預設,App Service 會強制從 HTTP 要求重新導向至 HTTPS。 若要停用此行為,請參閱進行一般設定。
如何變更應用程式的最低 TLS 版本?
根據預設,您的應用程式會允許 TLS 1.2,此為業界標準 (例如 PCI DSS) 建議的 TLS 層級。 若要強制執行不同的 TLS 版本,請參閱進行一般設定。
如何在 App Service 中處理 TLS 終止?
在 App Service 中,TLS 終止會在網路負載平衡器上發生,因此所有的 HTTPS 要求都會以未加密 HTTP 要求的形式進入您的應用程式。 如果您的應用程式邏輯需要檢查使用者要求是否有加密,請檢查 X-Forwarded-Proto 標頭。
語言專屬的設定指南 (如 Linux Node.js 設定指南) 會說明如何在應用程式的程式碼中偵測 HTTPS 工作階段。
使用指令碼進行自動化
Azure CLI
PowerShell
$fqdn="<Replace with your custom domain name>"
$pfxPath="<Replace with path to your .PFX file>"
$pfxPassword="<Replace with your .PFX password>"
$webappname="mywebapp$(Get-Random)"
$location="West Europe"
# Create a resource group.
New-AzResourceGroup -Name $webappname -Location $location
# Create an App Service plan in Free tier.
New-AzAppServicePlan -Name $webappname -Location $location `
-ResourceGroupName $webappname -Tier Free
# Create a web app.
$webapp = New-AzWebApp -Name $webappname -Location $location -AppServicePlan $webappname `
-ResourceGroupName $webappname
Write-Host "Sign in to your domain provider's website and configure the following records:"
Write-Host "A CNAME record that maps $fqdn to $webappname.azurewebsites.net"
Write-Host "A TXT record that maps asuid.$fqdn to the domain verification ID $($webapp.CustomDomainVerificationId)"
Read-Host "Press [Enter] key when ready ..."
# Before continuing, go to your DNS configuration UI for your custom domain and follow the
# instructions at https://aka.ms/appservicecustomdns to configure a CNAME record for the
# hostname "www" and point it your web app's default domain name.
# Upgrade App Service plan to Basic tier (minimum required by custom SSL certificates)
Set-AzAppServicePlan -Name $webappname -ResourceGroupName $webappname `
-Tier Basic
# Add a custom domain name to the web app.
Set-AzWebApp -Name $webappname -ResourceGroupName $webappname `
-HostNames @($fqdn,"$webappname.azurewebsites.net")
# Upload and bind the SSL certificate to the web app.
New-AzWebAppSSLBinding -WebAppName $webappname -ResourceGroupName $webappname -Name $fqdn `
-CertificateFilePath $pfxPath -CertificatePassword $pfxPassword -SslState SniEnabled