使用 Microsoft Entra 驗證
適用於:Azure SQL Database
Azure SQL 受控執行個體
Azure Synapse Analytics
本文概述如何使用 Microsoft Entra ID(先前稱為 Azure Active Directory)向 Azure SQL 資料庫、Azure SQL 受控執行個體、Windows Azure VM 上的 SQL Server、Azure Synapse Analytics 中的 Synapse SQL 和適用於 Windows 和 Linux 的 SQL Server 進行驗證。
若要瞭解如何建立和填入 Microsoft Entra ID,然後使用 Azure SQL 資料庫、Azure SQL 受控執行個體 和 Azure Synapse SQL 在 Azure Synapse Analytics 中設定 Microsoft Entra ID 和 Microsoft Entra ID,請參閱在 Azure VM 上使用 SQL Server 設定 Microsoft Entra ID 和 Microsoft Entra ID。
注意
Microsoft Entra 標識符 先前稱為 Azure Active Directory (Azure AD)。
概觀
您可以使用 Microsoft Entra 驗證,在單一中央位置集中管理資料庫使用者和其他 Microsoft 服務的身分識別。 中央識別碼管理提供單一位置以管理資料庫使用者並簡化權限管理。 包括以下優點:
它提供 SQL Server 驗證的替代方案。
有助於停止跨伺服器使用過多的使用者身分識別。
允許在單一位置變換密碼。
客戶可以使用 Microsoft Entra 群組來管理資料庫許可權。
它可藉由啟用 Microsoft Entra ID 支援的整合式 Windows 驗證 和其他形式的驗證,來消除儲存密碼。
Microsoft Entra 驗證會使用自主資料庫用戶來驗證資料庫層級的身分識別。
Microsoft Entra ID 支援連線到 SQL 資料庫 和 SQL 受管理執行個體 的應用程式令牌型驗證。
Microsoft Entra 驗證支援:
- Microsoft Entra 僅限雲端身分識別。
- 支援下列專案的 Microsoft Entra 混合式身分識別:
- 雲端驗證,透過兩個選項結合無縫單一登入 (SSO) 傳遞驗證和密碼雜湊驗證。
- 同盟驗證。
- 如需 Microsoft Entra 驗證方法及其選擇方法的詳細資訊,請參閱下列文章:
SQL Server Management Studio 支援使用 Microsoft Entra 搭配多重要素驗證的連線。 多重要素驗證提供一系列簡易驗證選項的強式驗證:通話、簡訊、智慧卡與釘選或行動應用程式通知。 如需詳細資訊,請參閱使用 Azure SQL 資料庫、SQL 受管理執行個體 和 Azure Synapse 對 Microsoft Entra 多重要素驗證的 SSMS 支援
SQL Server Data Tools (SSDT) 也支援使用 Microsoft Entra ID 的各種驗證選項。 如需詳細資訊,請參閱 SQL Server Data Tools (SSDT) 中的 Microsoft Entra ID 支援。
組態步驟包括下列程式來設定及使用 Microsoft Entra 驗證。
- 建立並填入 Microsoft Entra 租使用者。
- 選擇性:關聯或變更與您的 Azure 訂用帳戶相關聯的目前目錄。
- 建立 Microsoft Entra 系統管理員。
- 設定用戶端電腦。
- 在您的資料庫中建立對應至 Microsoft Entra 身分識別的自主資料庫使用者。
- 使用 Microsoft Entra 身分識別 連線 至您的資料庫。
注意
針對 Azure SQL、Azure VM 和 SQL Server 2022,Microsoft Entra 驗證僅支援源自 Microsoft Entra ID 且不支援第三方存取令牌的存取令牌。 Microsoft Entra ID 也不支援將 Microsoft Entra ID 查詢重新導向至第三方端點。 這適用於所有支援 Microsoft Entra 驗證的 SQL 平臺和所有作業系統。
信認架構
- 只有 Microsoft Entra ID、SQL 資料庫、SQL 受管理執行個體、Windows Azure VM 上的 SQL Server 和 Azure Synapse 的雲端部分才會被視為支援 Microsoft Entra 原生使用者密碼。
- 若要支援 Windows 單一登錄認證(或 Windows 認證的使用者/密碼),請使用同盟或受控網域中的 Microsoft Entra 認證,針對傳遞和密碼哈希驗證設定無縫單一登錄。 如需詳細資訊,請參閱 Microsoft Entra 無縫單一登入。
- 若要支援同盟驗證 (或 Windows 認證的使用者/密碼),需要與 ADFS 區塊進行通訊。
如需 Microsoft Entra 混合式身分識別、設定和同步處理的詳細資訊,請參閱下列文章:
- 密碼哈希驗證 - 使用 Microsoft Entra 連線 Sync 實作密碼哈希同步處理
- 傳遞驗證 - Microsoft Entra 傳遞驗證
- 同盟驗證 - 在 Azure 和 Microsoft Entra 連線 和同盟中部署 Active Directory 同盟服務
如需使用 ADFS 基礎結構 (或 Windows 認證的使用者/密碼) 的同盟驗證範例,請參閱下圖。 箭頭表示通訊路徑。
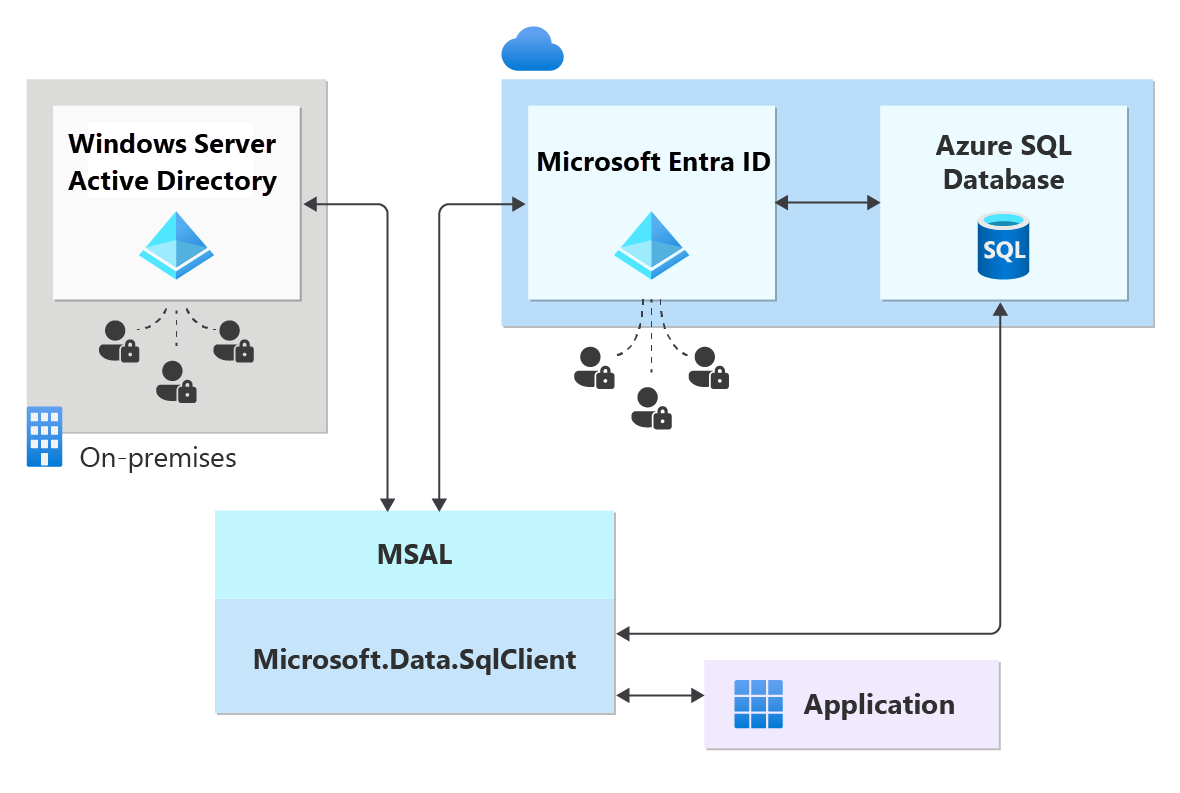
下圖表示允許用戶端藉由提交權杖連線到資料庫的同盟、信任和主控關聯性。 令牌是由 Microsoft Entra ID 驗證,而且由資料庫信任。 客戶 1 可以代表 Microsoft Entra 識別碼與原生使用者或 Microsoft Entra 識別碼與同盟使用者。 客戶 2 代表可能的解決方案,包括匯入的使用者,在此範例中,來自同盟的 Microsoft Entra 標識符,且 ADFS 與 Microsoft Entra ID 同步處理。 請務必瞭解使用 Microsoft Entra 驗證存取資料庫時,需要裝載訂用帳戶與 Microsoft Entra 識別符相關聯。 必須使用相同的訂用帳戶來建立 Azure SQL Database、SQL 受控執行個體或 Azure Synapse 資源。
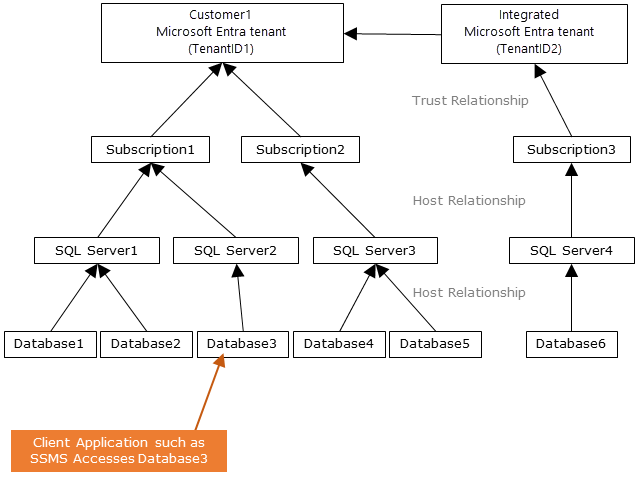
系統管理員結構
使用 Microsoft Entra 驗證時,有兩個 管理員 istrator 帳戶:原始 Azure SQL 資料庫 系統管理員和 Microsoft Entra 系統管理員。 Azure Synapse 適用相同的概念。 只有以 Microsoft Entra 帳戶為基礎的系統管理員才能在用戶資料庫中建立第一個 Microsoft Entra ID 自主資料庫使用者。 Microsoft Entra 系統管理員登入可以是 Microsoft Entra 使用者或 Microsoft Entra 群組。 當系統管理員是群組帳戶時,任何群組成員都可以使用它,為伺服器啟用多個 Microsoft Entra 系統管理員。 以系統管理員身分使用群組帳戶,可讓您集中新增和移除 Microsoft Entra 識別碼中的群組成員,而不需變更 SQL 資料庫 或 Azure Synapse 中的使用者或許可權,藉此增強管理性。 隨時只能設定一個 Microsoft Entra 系統管理員(使用者或群組)。
注意
使用 Azure SQL 的 Microsoft Entra 驗證僅支援 Azure SQL 資源目前所在的單一 Microsoft Entra 租使用者。 此租使用者中的所有 Microsoft Entra 物件都可以設定為允許使用者存取此租使用者中的 Azure SQL。 Microsoft Entra 系統管理員也必須來自 Azure SQL 資源的租使用者。 不支援從不同租使用者存取 Azure SQL 的 Microsoft Entra 多租用戶驗證。
權限
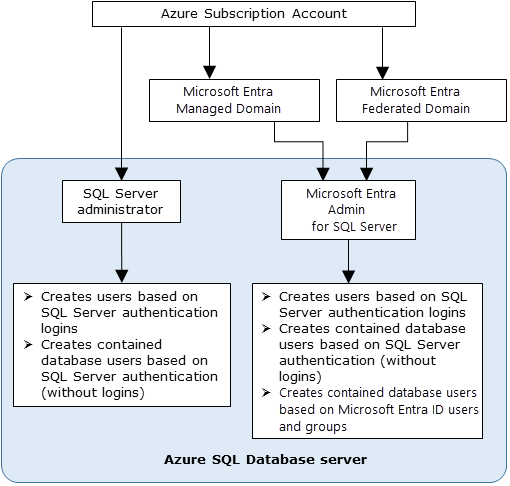
若要建立新的使用者,您必須具有資料庫中的 ALTER ANY USER 權限。 任何資料庫使用者皆可授與 ALTER ANY USER 權限。 ALTER ANY USER 權限的擁有者還包括伺服器系統管理員帳戶、具備資料庫之 CONTROL ON DATABASE 或 ALTER ON DATABASE 權限的資料庫使用者,以及 db_owner 資料庫角色的成員。
若要在 Azure SQL 資料庫、Azure SQL 受控執行個體 或 Azure Synapse 中建立自主資料庫使用者,您必須使用 Microsoft Entra 身分識別連線到資料庫或實例。 若要建立第一個自主資料庫使用者,您必須使用 Microsoft Entra 系統管理員連線到資料庫(誰是資料庫的擁有者)。 這示範於使用 SQL 資料庫 或 Azure Synapse 設定及管理 Microsoft Entra 驗證。 只有在針對 Azure SQL 資料庫、Azure SQL 受控執行個體 或 Azure Synapse 建立 Microsoft Entra 系統管理員時,才能進行 Microsoft Entra 驗證。 如果 Microsoft Entra 系統管理員已從伺服器中移除,則先前在伺服器內建立的現有 Microsoft Entra 使用者無法再使用其 Microsoft Entra 認證連線到資料庫。
Microsoft Entra 功能和限制
您可以為 Azure SQL 資料庫 布建下列 Microsoft Entra ID 成員:
- Microsoft Entra 使用者: Microsoft Entra 租使用者中的任何類型使用者 ,包括內部、外部、來賓和成員。 也支援為與 Microsoft Entra ID 同盟設定的 Active Directory 網域成員,並可設定為無縫單一登錄。
- 應用程式:存在於 Azure 中的應用程式可以使用服務主體或受控識別,直接向 Azure SQL 資料庫 進行驗證。 使用受控識別進行驗證是慣用的,因為它是無密碼的,而且不需要開發人員管理的認證。
- Microsoft Entra 群組,可根據組織成員資格管理適當的使用者和應用程式存取,以簡化整個組織的存取管理。
屬於資料庫角色成員群組的
db_ownerMicrosoft Entra 用戶無法對 Azure SQL 資料庫 和 Azure Synapse 使用 CREATE DATABASE SCOPED CREDENTIAL 語法。 您將會看到下列錯誤:SQL Error [2760] [S0001]: The specified schema name 'user@mydomain.com' either doesn't exist or you do not have permission to use it.若要減輕 CREATE DATABASE SCOPED CREDENTIAL 問題,請直接新增個別的 Microsoft Entra 使用者
db_owner角色。當 Microsoft Entra 主體執行時,不支援這些系統函式並傳回 NULL 值:
SUSER_ID()SUSER_NAME(<ID>)SUSER_SNAME(<SID>)SUSER_ID(<name>)SUSER_SID(<name>)
Azure SQL 資料庫 不會為已登入的使用者建立隱含使用者,做為 Microsoft Entra 群組成員資格的一部分。 因此,需要指派擁有權的各種作業將會失敗,即使 Microsoft Entra 群組會新增為具有這些許可權的角色成員也一樣。
例如,使用者透過具有db_ddladmin角色的 Microsoft Entra 群組登入資料庫,將無法執行 CREATE SCHEMA、ALTER SCHEMA 和其他物件建立語句,而不需明確定義架構(例如數據表、檢視或類型)。 若要解決此問題,您必須為該使用者建立 Microsoft Entra 使用者,或必須變更 Microsoft Entra 群組,將DEFAULT_SCHEMA指派給 dbo。
SQL 受控執行個體
microsoft Entra 伺服器主體(登入)和用戶支援 SQL 受管理執行個體。
SQL 受管理執行個體 不支持將對應至 Microsoft Entra 群組的 Microsoft Entra 登入設定為資料庫擁有者。
- 擴充功能是當群組新增為
dbcreator伺服器角色的一部分時,此群組中的使用者可以連線至 SQL 受控執行個體並建立新的資料庫,但將無法存取資料庫。 這是因為新的資料庫擁有者是 SA,而不是 Microsoft Entra 使用者。 如果將個別使用者新增至dbcreator伺服器角色,則不會顯示這個問題。
- 擴充功能是當群組新增為
Microsoft Entra 登入支援 SQL Agent 管理和作業執行。
資料庫備份和還原作業可由 Microsoft Entra 伺服器主體執行(登入)。
支援稽核與 Microsoft Entra 伺服器主體(登入)和驗證事件相關的所有語句。
Microsoft Entra 伺服器主體 (logins) 的專用系統管理員連線,這是支持系統管理員伺服器角色的成員。
- 透過 SQLCMD 公用程式和 SQL Server Management Studio 支援。
登入觸發程式支援來自 Microsoft Entra 伺服器主體 (logins) 的登入事件。
Service Broker 和 DB 郵件可以使用 Microsoft Entra 伺服器主體進行設定(登入)。
使用 Microsoft Entra 身分識別進行連線
Microsoft Entra 驗證支援使用 Microsoft Entra 身分識別連線到資料庫的下列方法:
- Microsoft Entra 密碼
- 已與 Microsoft Entra 整合
- 具有多重要素驗證的 Microsoft Entra Universal
- 使用應用程式權杖驗證
Microsoft Entra 伺服器主體支援下列驗證方法(登入):
- Microsoft Entra 密碼
- 已與 Microsoft Entra 整合
- 具有多重要素驗證的 Microsoft Entra Universal
其他考量
- 若要增強管理性,建議您以系統管理員身分佈建專用的 Microsoft Entra 群組。
- 您隨時只能為 SQL 資料庫 或 Azure Synapse 中的伺服器設定一個 Microsoft Entra 系統管理員(使用者或群組)。
- 新增 SQL 受管理執行個體 的 Microsoft Entra 伺服器主體 (logins) 可讓您建立可新增至角色的
sysadmin多個 Microsoft Entra 伺服器主體 (logins)。
- 新增 SQL 受管理執行個體 的 Microsoft Entra 伺服器主體 (logins) 可讓您建立可新增至角色的
- 只有伺服器的 Microsoft Entra 系統管理員一開始可以使用 Microsoft Entra 帳戶連線到伺服器或受控實例。 Microsoft Entra 系統管理員可以設定後續的 Microsoft Entra 資料庫使用者。
- 不支援屬於 2048 個以上 Microsoft Entra 安全組成員的 Microsoft Entra 使用者和服務主體(Microsoft Entra 應用程式)在 SQL 資料庫、SQL 受管理執行個體 或 Azure Synapse 中登入資料庫。
- 建議將連接逾時設定為 30 秒。
- SQL Server 2016 Management Studio 和 SQL Server Data Tools for Visual Studio 2015 (版本 14.0.60311.1April 2016 或更新版本)支援 Microsoft Entra 驗證。 (.NET Framework Data Provider for SqlServer 支援 Microsoft Entra 驗證;至少為 .NET Framework 4.6 版)。 因此,這些工具和數據層應用程式的最新版本(DAC 和 BACPAC)可以使用 Microsoft Entra 驗證。
- 從 15.0.1 版開始,sqlcmd 公用程式和 bcp 公用程式支援使用多重要素驗證的 Active Directory 互動式驗證。
- SQL Server Data Tools for Visual Studio 2015 至少需要 2016 年 4 月版本的 Data Tools (版本 14.0.60311.1)。 目前,SSDT 物件總管 中不會顯示 Microsoft Entra 使用者。 解決方法是在 sys.database_principals 中檢視使用者。
- Microsoft JDBC Driver 6.0 for SQL Server 支援 Microsoft Entra 驗證。 此外,請參閱 設定連接屬性。
- PolyBase 無法使用 Microsoft Entra 驗證進行驗證。
- 使用 [Azure 入口網站 匯入資料庫和導出資料庫] 刀鋒視窗,支援 Azure SQL 資料庫 和 Azure Synapse 的 Microsoft Entra 驗證。 PowerShell 命令也支援使用 Microsoft Entra 驗證匯入和匯出。
- 使用 CLI 支援 SQL 資料庫、SQL 受管理執行個體 和 Azure Synapse 的 Microsoft Entra 驗證。 如需詳細資訊,請參閱使用 SQL 資料庫 或 Azure Synapse 和 SQL Server 設定和管理 Microsoft Entra 驗證 - az sql server。
下一步
- 若要瞭解如何建立及填入 Microsoft Entra 租使用者,然後使用 Azure SQL 資料庫、Azure SQL 受控執行個體 或 Azure Synapse 進行設定及管理,請參閱使用 SQL 資料庫、SQL 受管理執行個體 或 Azure Synapse 設定和管理 Microsoft Entra 驗證。
- 如需搭配 SQL 受管理執行個體 使用 Microsoft Entra 伺服器主體 (logins) 的教學課程,請參閱搭配 SQL 受管理執行個體 的 Microsoft Entra 伺服器主體 (logins)
- 如需 SQL Database 中登入、使用者、資料庫角色和權限的概觀,請參閱登入、使用者、資料庫角色和權限。
- 如需資料庫主體的詳細資訊,請參閱主體。
- 如需資料庫角色的詳細資訊,請參閱資料庫角色。
- 如需為 SQL 受管理執行個體 建立 Microsoft Entra 伺服器主體 (logins) 的語法,請參閱 CREATE LOGIN。
- 如需 SQL Database 中防火牆規則的詳細資訊,請參閱 SQL Database 防火牆規則。
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應