何謂 Azure Bastion?
Azure Bastion 是完全受控的 PaaS 服務,您可以佈建該服務,以透過私人 IP 位址安全地連線到虛擬機器。 其直接透過 Azure 入口網站的 TLS,或透過本機電腦上原本安裝的原生 SSH 或 RDP 用戶端,為虛擬機器提供安全且順暢的 RDP/SSH 連線。 透過 Azure Bastion 連線時,您的虛擬機器不需要公用 IP 位址、代理程式或特殊用戶端軟體。
Bastion 可為佈建所在虛擬網路中的所有 VM 提供安全的 RDP 和 SSH 連線。 使用 Azure Bastion 來保護您的虛擬機器免於向外公開 RDP/SSH 連接埠,同時提供使用 RDP/SSH 的安全存取。
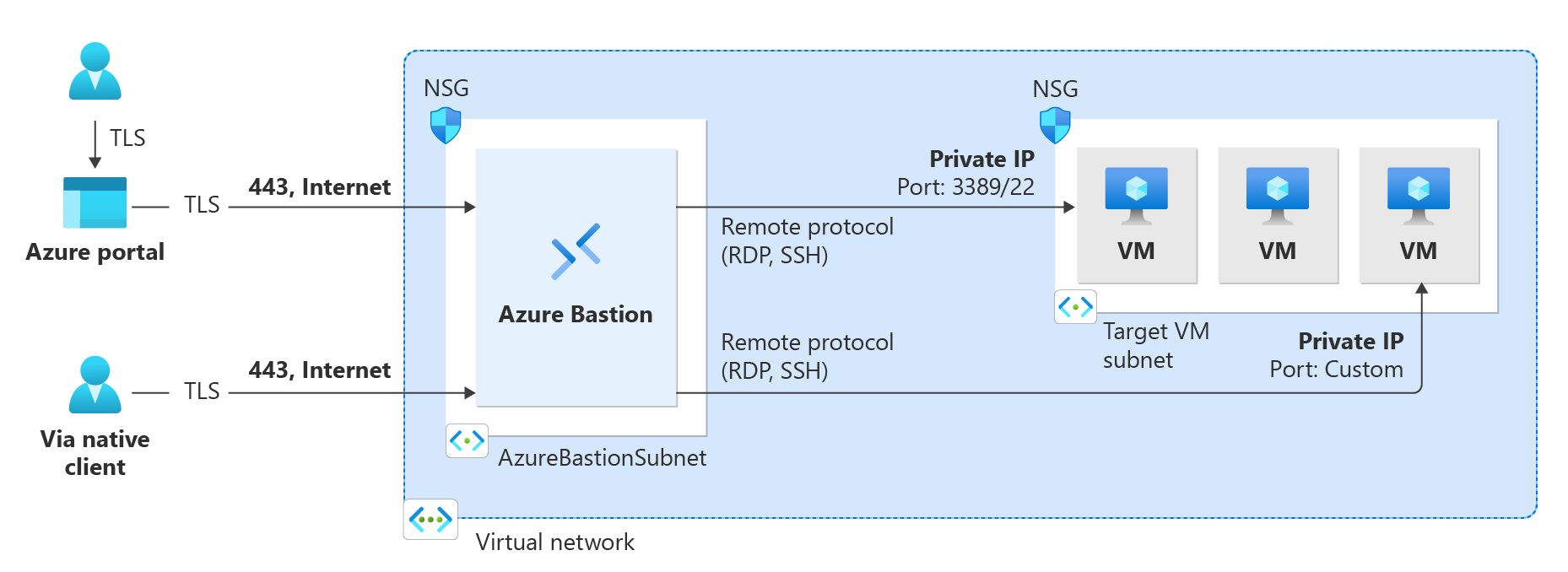
下圖顯示如何透過使用基本或標準 SKU 的 Bastion 部署,連線至虛擬機器。
重點優勢
| 優點 | 描述 |
|---|---|
| 透過 Azure 入口網站使用 RDP 和 SSH | 只要在 Azure 入口網站中按一下無縫體驗,就可以直接進入 RDP 和 SSH 工作階段。 |
| RDP/SSH 透過 TLS 和防火牆周遊的遠端工作階段 | Azure Bastion 使用自動串流到本機裝置的 HTML5 Web 用戶端。 RDP/SSH 工作階段使用連接埠 443 透過 TLS 連線。 這使流量可更安全地周遊防火牆。 Bastion 支援 TLS 1.2。 不支援舊版 TLS。 |
| Azure VM 上不需要公用 IP 位址 | Azure Bastion 使用 VM 上的私人 IP 位址,開啟對 Azure VM 的 RDP/SSH 連線。 您在虛擬機器上不需要公用 IP 位址。 |
| 輕鬆管理網路安全性群組 (NSG) | 您不需要將任何 NSG 套用至 Azure Bastion 子網路。 因為 Azure Bastion 透過私人 IP 來連線至虛擬機器,您可以將 NSG 設定為只允許來自 Azure Bastion 的 RDP/SSH。 每次需要安全地連線至虛擬機器時,就不必再麻煩管理 NSG。 如需 NSG 的詳細資訊,請參閱網路安全性群組。 |
| 不需要在 VM 上另外管理堡壘主機 | Azure Bastion 是 Azure 的完全受控平台 PaaS 服務,內部經過強化,為您提供安全的 RDP/SSH 連線。 |
| 針對連接埠掃描的保護 | 因為您不需向網際網路公開 VM,得以保護 VM 免遭惡意使用者掃描連接埠。 |
| 僅需強化一處 | Azure Bastion 位於虛擬網路的的周邊,所以您不需煩惱要強化虛擬網路中的每一部 VM。 |
| 防範零時差惡意探索 | Azure 平台保持 Azure Bastion 強化並永遠維持更新,以防範零時差惡意探索。 |
SKU
Azure Bastion 提供多個 SKU 層。 下表顯示功能和對應的 SKU。
| 功能 | 開發人員 SKU | 基本 SKU | 標準 SKU |
|---|---|---|---|
| 連線至相同虛擬網路中的目標 VM | Yes | .是 | Yes |
| 連線至對等互連虛擬網路中的目標 VM | No | 是 | 是 |
| 支援並行連線 | No | .是 | Yes |
| 在 Azure Key Vault (AKV) 中存取 Linux VM 私密金鑰 | No | .是 | Yes |
| 使用 SSH 連線至 Linux VM | Yes | 是 | 是 |
| 使用 RDP 連線至 Windows VM | Yes | 是 | 是 |
| 使用 RDP 連線至 Linux VM | No | 無 | Yes |
| 使用 SSH 連線至 Windows VM | No | 無 | 是 |
| 指定自訂輸入連接埠 | No | 無 | 是 |
| 使用 Azure CLI 連線至 VM | No | 無 | 是 |
| 主機調整 | No | 無 | 是 |
| 上傳或下載檔案 | No | 無 | 是 |
| Kerberos 驗證 | No | 是 | 是 |
| 可共用連結 | No | 無 | 是 |
| 透過 IP 位址連線到 VM | No | 無 | 是 |
| VM 音訊輸入 | Yes | .是 | Yes |
| 停用複製/貼上 (Web 型用戶端) | No | 無 | Yes |
如需 SKU 的詳細資訊,包括如何升級 SKU 以及新開發人員 SKU (目前為預覽版) 的相關資訊,請參閱組態設定一文。
架構
本節適用於所有 SKU 層,但開發人員 SKU 除外,其部署方式有所不同。 Azure Bastion 會部署至虛擬網路,並支援虛擬網路對等互連。 具體而言,Azure Bastion 會管理本機或對等互連虛擬網路中所建立 VM 的 RDP/SSH 連線能力。
RDP 和 SSH 是連接到 Azure 中運行的工作負載的一些基本方法。 透過網際網路公開 RDP/SSH 連接埠並非預期,而且會視為重大威脅。 這通常是由於協定弱點造成的。 為了抑制這項威脅表面,您可以在周邊網路的公用端部署堡壘主機 (也稱為「跳板伺服器」)。 堡壘主機伺服器是設計及設定來防禦攻擊。 堡壘伺服器也會提供與位於堡壘後方 (以及進一步的網路內) 工作負載的 RDP 和 SSH 連線。
根據預設,新的 Bastion 部署目前不支援區域備援。 先前部署的堡壘可能是區域備援,或可能不是。 例外狀況是南韓中部和東南亞的 Bastion 部署,這些部署確實支援區域備援。
此圖顯示了 Azure Bastion 部署的結構。 此圖表不適用於開發人員 SKU。 在此圖表中:
- Bastion 主機部署在包含至少 /26 前置詞之 AzureBastionSubnet 子網路的虛擬網路中。
- 使用者使用任何 HTML5 瀏覽器連線到 Azure 入口網站。
- 使用者選取要連線的虛擬機器。
- 只要按一下,RDP/SSH 工作階段就會在瀏覽器中開啟。
- Azure VM 上不需公用 IP。
主機調整
Azure Bastion 支援手動主機調整。 您可以設定主機執行個體數目 (縮放單位),以便管理 Azure Bastion 可以支援的並行 RDP/SSH 連線數目。 增加主機執行個體數目可讓 Azure Bastion 管理更多並行工作階段。 減少執行個體數目會減少並行支援的工作階段數目。 Azure Bastion 最多可支援 50 個主機執行個體。 此功能僅適用於 Azure Bastion Standard SKU。
如需詳細資訊,請參閱組態設定一文。
定價
Azure Bastion 定價是根據 SKU 和執行個體 (縮放單位),加上資料傳輸費率的每小時價格組合。 無論輸出資料使用量為何,每小時價格都是從部署 Bastion 的那一刻開始計費。 如需最新的價格資訊,請參閱 Azure Bastion 價格頁面。
新功能
訂閱 RSS 摘要,並在 Azure 更新頁面上檢視最新的 Azure Bastion 功能更新。
Bastion 常見問題集
如需常見問題,請參閱 Bastion 常見問題。