使用 Azure 防火牆 原則來定義規則階層
安全性系統管理員必須管理防火牆,並確保跨內部部署和雲端部署的合規性。 關鍵元件是能夠讓應用程式小組彈性地實作 CI/CD 管線,以自動化方式建立防火牆規則。
Azure 防火牆 原則可讓您定義規則階層並強制執行合規性:
- 提供階層式結構,在子應用程式小組原則之上重疊中央基底原則。 基底原則具有較高的優先順序,並在子原則之前執行。
- 使用 Azure 自定義角色定義來防止意外移除基底原則,並提供訂用帳戶或資源群組內規則集合群組的選擇性存取權。
解決方案概觀
此範例的高階步驟如下:
- 在安全性小組資源群組中建立基底防火牆原則。
- 在基底原則中定義IT安全性特定規則。 這會新增一組常見的規則,以允許/拒絕流量。
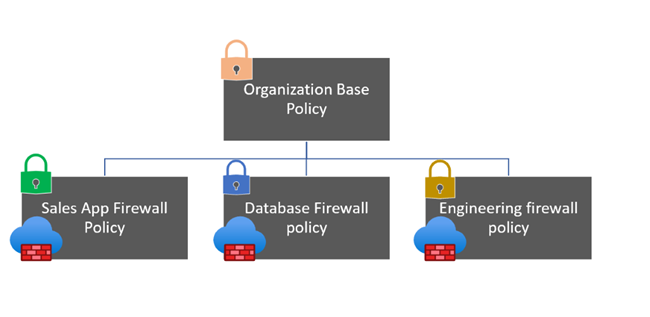
- 建立繼承基底原則的應用程式小組原則。
- 在原則中定義應用程式小組特定的規則。 您也可以從既有的防火牆移轉規則。
- 建立 Microsoft Entra 自定義角色,以提供規則集合群組的精細存取權,並在防火牆原則範圍中新增角色。 在下列範例中,銷售小組成員可以編輯銷售團隊防火牆原則的規則集合群組。 這同樣適用於資料庫和工程小組。
- 將原則與對應的防火牆產生關聯。 Azure 防火牆只能有一個指派的原則。 這需要每個應用程式小組有自己的防火牆。
建立防火牆原則
- 基底防火牆原則。
為每個應用程式小組建立原則:
- 銷售防火牆原則。 銷售防火牆原則會繼承基底防火牆原則。
- 資料庫防火牆原則。 資料庫防火牆原則會繼承基底防火牆原則。
- 工程防火牆原則。 工程防火牆原則也會繼承基底防火牆原則。
建立自定義角色以存取規則集合群組
每個應用程式小組都會定義自定義角色。 角色會定義作業和範圍。 應用程式小組可以編輯其個別應用程式的規則集合群組。
使用下列高階程式來定義自訂角色:
取得訂用帳戶。
Select-AzSubscription -SubscriptionId xxxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx執行下列命令。
Get-AzProviderOperation "Microsoft.Support/*" | FT Operation, Description -AutoSize使用 Get-AzRoleDefinition 命令,以 JSON 格式輸出讀取器角色。
Get-AzRoleDefinition -Name "Reader" | ConvertTo-Json | Out-File C:\CustomRoles\ReaderSupportRole.json在編輯器中開啟ReaderSupportRole.json檔案。
以下是 JSON 輸出。 如需不同屬性的相關信息,請參閱 Azure 自定義角色。
{
"Name": "Reader",
"Id": "acdd72a7-3385-48ef-bd42-f606fba81ae7",
"IsCustom": false,
"Description": "Lets you view everything, but not make any changes.",
"Actions": [
"*/read"
],
"NotActions": [],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": [
"/"
]
}
編輯 JSON 檔案以新增
*/read", "Microsoft.Network/*/read", "Microsoft.Network/firewallPolicies/ruleCollectionGroups/write動作屬性的作業。 請務必在讀取作業之後包含逗號。 此動作可讓使用者建立和更新規則集合群組。
在 AssignableScopes 中,使用下列格式新增您的訂用帳戶標識碼。
/subscriptions/xxxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx您必須新增明確的訂用帳戶標識碼。 否則,您不允許將角色匯入訂用帳戶。
刪除Id 屬性行,並將IsCustom屬性變更為 true。
將此角色中的 [名稱] 和 [描述] 屬性變更為 AZFM 規則集合群組作者和使用者,可以編輯防火牆原則規則集合群組
您的 JSON 檔案應會類似於下列範例:
{
"Name": "AZFM Rule Collection Group Author",
"IsCustom": true,
"Description": "Users in this role can edit Firewall Policy rule collection groups",
"Actions": [
"*/read",
"Microsoft.Network/*/read",
"Microsoft.Network/firewallPolicies/ruleCollectionGroups/write"
],
"NotActions": [
],
"DataActions": [
],
"NotDataActions": [
],
"AssignableScopes": [
"/subscriptions/xxxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx"]
}
若要建立新的自訂角色,請使用 New-AzRoleDefinition 命令並指定 JSON 角色定義檔案。
New-AzRoleDefinition -InputFile "C:\CustomRoles\RuleCollectionGroupRole.json
列出自定義角色
若要列出所有自定義角色,您可以使用 Get-AzRoleDefinition 命令:
Get-AzRoleDefinition | ? {$_.IsCustom -eq $true} | FT Name, IsCustom
您也可以在 Azure 入口網站 中看到自定義角色。 移至您的訂用帳戶,選取 [訪問控制]、[ IAM]、 [角色]。
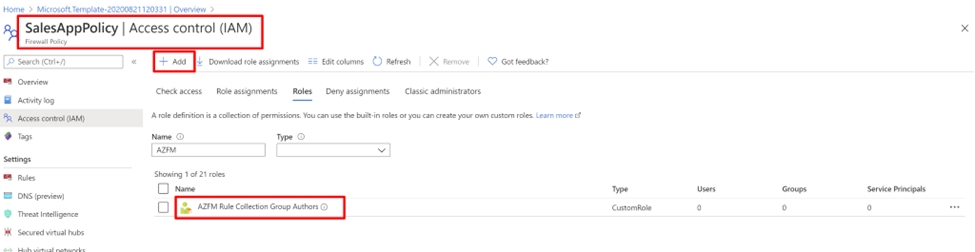

如需詳細資訊,請參閱 教學課程:使用 Azure PowerShell 建立 Azure 自定義角色。
將使用者新增至自定義角色
在入口網站上,您可以將使用者新增至 AZFM 規則集合群組作者角色,並提供防火牆原則的存取權。
- 從入口網站中,選取應用程式小組防火牆原則(例如 SalesAppPolicy)。
- 選取 [存取控制]。
- 選取 [新增角色指派]。
- 將使用者/使用者群組(例如 Sales 小組)新增至角色。
針對其他防火牆原則重複此程式。
摘要
具有自定義角色的防火牆原則現在提供防火牆原則規則集合群組的選擇性存取權。
使用者沒有下列權限:
- 刪除 Azure 防火牆 或防火牆原則。
- 更新防火牆原則階層或 DNS 設定或威脅情報。
- 更新其不是 AZFM 規則集合群組作者群組成員的防火牆原則。
安全性系統管理員可以使用基底原則來強制執行護欄,並封鎖其企業所需的特定類型流量(例如ICMP)。