針對 Azure Load Balancer 輸出連線問題進行疑難排解
了解 Azure Load Balancer 中輸出連線的疑難排解指引。 這包括了解來源網路位址轉換 (SNAT),而且會影響連線、在 VM 上使用個別公用 IP,以及設計應用程式以提升連線效率,以避免 SNAT 連接埠耗盡。 客戶經歷的大部分輸出連線問題,都是因為 SNAT 連接埠耗盡且連線逾時,導致封包遭到丟棄。
若要深入了解 SNAT 連接埠,請參閱輸出連線的來源網路位址轉譯。
了解您的 SNAT 連接埠使用量
依照包含計量、警示和資源健康情況的 Standard Load Balancer 診斷的指示,監視您現有負載平衡器的 SNAT 連接埠使用量和配置。 監視以確認或判斷 SNAT 耗盡的風險。 如果您無法了解輸出連線行為,請使用 IP 堆疊統計資料 (netstat) 或收集封包擷取。 您可以在您執行個體的客體 OS 中執行這些封包擷取,或使用網路監看員來進行封包擷取。 在大部分情況下,Azure 建議使用 NAT 閘道進行輸出連線,以降低 SNAT 耗盡的風險。 如果您的服務重複對相同目的地起始 TCP 或 UDP 輸出連線,強烈建議您使用 NAT 閘道。
為您的 Azure 部署進行輸出連線的最佳化
為您的 Azure 部署進行輸出連線的最佳化,是很重要的。 最佳化可以避免或減輕輸出連線的問題。
部署 NAT 閘道以進行輸出網際網路連線
Azure NAT 閘道是具有高度復原性且可調整的 Azure 服務,可讓您從虛擬網路對網際網路進行輸出連線。 NAT 閘道使用 SNAT 連接埠的獨特方法,有助於解決常見的 SNAT 耗盡和連線問題。 如需 Azure NAT 閘道的詳細資訊,請參閱什麼是 Azure NAT 閘道?。
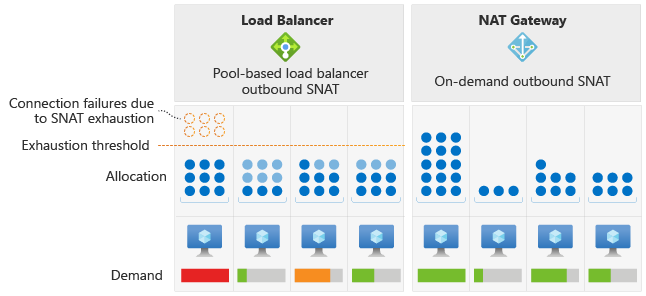
NAT 閘道如何降低 SNAT 連接埠耗盡的風險?
Azure Load Balancer 會將固定數量的 SNAT 連接埠配置給後端集區中的每個虛擬機器執行個體。 這種配置方法可能會導致 SNAT 耗盡,尤其是在不平均的流量模式導致特定虛擬機器傳送較大量的傳出連線時。 不同於負載平衡器,NAT 閘道會在子網路內的所有 VM 執行個體間動態配置 SNAT 連接埠。
NAT 閘道會使可用的 SNAT 連接埠可供子網路中的每個執行個體存取。 此動態配置可讓 VM 執行個體從可用的連接埠集區中所需的 SNAT 連接埠數目進行新連線。 動態配置可降低 SNAT 耗盡的風險。
連接埠選取和重複使用行為。
NAT 閘道會從可用的連接埠集區中隨機選取連接埠。 如果沒有可用的連接埠,則只要沒有相同目的地公用 IP 和連接埠的現有連線,就會重複使用 SNAT 連接埠。 NAT 閘道的這個連接埠選取和重複使用行為,可降低發生連線逾時的可能性。
若要深入了解 SNAT 和連接埠如何用於 NAT 閘道,請參閱 SNAT 基本概念。 在某些情況下,您無法使用 NAT 閘道進行輸出連線。 如需 NAT 閘道限制的詳細資訊,請參閱 NAT 閘道限制。
如果您無法使用 NAT 閘道進行輸出連線,請參閱本文所述的其他移轉選項。
設定負載平衡器輸出規則,將每個 VM 的 SNAT 連接埠數目最大化
如果您在使用公用 Standard Load Balancer 時遇到 SNAT 耗盡的狀況或連線失敗,請確定您使用的是具有手動連接埠配置的輸出規則。 否則,您可能會依賴負載平衡器的預設輸出存取。 預設輸出存取會自動設定保守數目的連接埠,視後端集區中的執行個體數目而定。 預設輸出存取並非啟用輸出連線的建議方法。 後端集區進行調整時,如果需要重新配置連接埠,您的連線可能會受到影響。
若要深入了解預設輸出存取和預設連接埠配置,請參閱輸出連線的來源網路位址轉譯。
若要增加每個 VM 可用的 SNAT 連接埠數目,請在負載平衡器上設定具有手動連接埠配置的輸出規則。 例如,如果您知道後端集區中最多會有 10 個 VM,即可為每個 VM 配置最多 6,400 個 SNAT 連接埠,而不是預設的 1,024 個。 如果您需要更多 SNAT 連接埠,可以為輸出連線新增多個前端 IP 位址,使可用的 SNAT 連接埠數目倍增。 在新增更多前端 IP 位址之前,請務必先了解 SNAT 連接埠耗盡的原因。
如需詳細指引,請參閱本文稍後的設計您的應用程式以有效率地使用連線。 若要為輸出連線新增更多 IP 位址,請為每個新 IP 建立前端 IP 設定。 設定輸出規則時,您可以為後端集區選取多個前端 IP 設定。 建議對輸入和輸出連線使用不同的 IP 位址。 不同的 IP 位址可隔離流量,以利進行監視和疑難排解。
在 VM 上設定個別的公用 IP
對於較小的部署,您可以考慮為 VM 指派公用 IP。 如果將公用 IP 指派給 VM,則該公用 IP 提供的所有連接埠都可供 VM 使用。 不同於負載平衡器或 NAT 閘道,連接埠僅可供與 IP 位址相關聯的單一 VM 存取。
強烈建議您考慮改用 NAT 閘道,因為指派個別公用 IP 位址並非可調整的解決方案。
注意
如果您需要將 Azure 虛擬網路連線到 Azure PaaS 服務 (例如 Azure 儲存體、Azure SQL、Azure Cosmos DB) 或其他可用的 Azure 服務,您可以利用 Azure Private Link 來徹底迴避 SNAT。 Azure Private Link 會透過 Azure 骨幹網路 (而非透過網際網路傳送) 將來自虛擬網路的流量傳送至 Azure 服務。
Private Link 是私人存取 Azure 託管服務的服務端點所建議的選項。 若要深入了解 Private Link 與服務端點之間的差異,請參閱比較私人端點和服務端點。
設計有連線效率的應用程式
在設計應用程式時,請確定應用程式可有效率地使用連線。 連線效率可降低或消除在已部署的應用程式中耗盡 SNAT 連接埠的可能性。
將應用程式修改成重複使用連線
建議您將應用程式設定為重複使用連線,而不是為每個要求產生個別且不可部分完成的 TCP 連線。 連線重複使用會產生效能更高的 TCP 交易,且對於 HTTP/1.1 之類的通訊協定格外重要 (因為依預設會重複使用連線)。 這種重複使用適用於以 HTTP 作為傳輸方式的其他通訊協定,例如 REST。
將應用程式修改成使用連線共用
您可以在應用程式中採用連線共用配置,此時要求會在內部分配到一組固定的連線,並盡可能地重複使用。 此配置會限制使用中的 SNAT 連接埠數目,而建立較可預測的環境。
這個配置可在單一連線阻斷某個作業的回應時,藉由允許多個作業同時進行,來增加要求輸送量。
連線共用可能已存在於您用來開發應用程式的架構中,或是您應用程式的組態設定中。 您可以將連線共用與連線重複使用搭配使用。 這樣,您的多個要求就會將數目固定且可預測的連接埠取用至相同的目的地 IP 位址和連接埠。
這些要求會因為系統有效率地使用 TCP 交易來降低延遲和資源使用量而受益。 UDP 交易也可受益。 管理 UDP 流程數目可避免發生耗盡的狀況,並管理 SNAT 連接埠使用量。
將應用程式修改成使用較不積極的重試邏輯
當 SNAT 連接埠耗盡或發生應用程式失敗時,不含衰減和降速邏輯的積極或暴力重試會造成耗盡的情況發生或持續存在。 您可以使用較不積極的重試邏輯,以降低對 SNAT 連接埠的需求。
根據設定的閒置逾時,如果重試頻率太高,連線可能沒有足夠的時間可關閉並釋出 SNAT 連接埠以供重複使用。
使用 Keepalive 來重設輸出閒置逾時
負載平衡器輸出規則依預設會有 4 分鐘的閒置逾時,且最高可調整為 100 分鐘。 您也可以使用 TCP 存留來重新整理閒置流程,並在必要時重設此閒置逾時。 使用 TCP 存留時,在連線的一端加以啟用即已足夠。
例如,只在伺服器端啟用便足以重設流程的閒置計時器,且不需要在兩端都起始 TCP 存留。 應用程式層也有類似概念,包括資料庫用戶端-伺服器組態。 請檢查伺服器端,了解應用程式的特定存留有哪些選項。
下一步
如需 SNAT 連接埠耗盡、輸出連線選項和預設輸出存取的詳細資訊,請參閱: