教學課程:了解如何使用 Azure CLI 管理 Linux 虛擬機器
將資源部署至 Azure 時,您有極大的彈性可決定所要部署的資源類型、資源所在之處,以及如何設定資源。 不過,此種彈性可能會使得組織所擁有的選項超出您的規劃。 當您考慮將資源部署至 Azure 時,可能會思考下列問題:
- 如何符合某些國家/地區中資料主權的法律需求?
- 如何控制成本?
- 如何確保他人不會不慎變更重要系統?
- 如何追蹤資源成本並準確地計費?
本文可解決這些問題。 具體而言,您可以:
- 將使用者指派給角色,並將角色指派給範圍,讓使用者有權限能夠執行預期的動作,但僅止於此。
- 針對訂用帳戶中的資源,套用規定慣例的原則。
- 鎖定系統不可或缺的資源。
- 標記資源,讓您可以依照對組織有意義的價值來追蹤資源。
本文著重於實作治理所要進行的工作。 如需更廣泛的概念討論,請參閱 Azure 中的治理。
必要條件
在 Azure Cloud Shell 中使用 Bash 環境。
如果想要,請安裝 Azure CLI 以執行 CLI 參考命令。
如果您使用的是本機安裝,請使用 az login 命令,透過 Azure CLI 來登入。 請遵循您終端機上顯示的步驟,完成驗證程序。 如需其他登入選項,請參閱使用 Azure CLI 登入。
出現提示時,請在第一次使用時安裝 Azure CLI 擴充功能。 如需擴充功能詳細資訊,請參閱使用 Azure CLI 擴充功能。
執行 az version 以尋找已安裝的版本和相依程式庫。 若要升級至最新版本,請執行 az upgrade。
- 本教學課程需要 2.0.30 版或更新版本的 Azure CLI。 如果您是使用 Azure Cloud Shell,就已安裝最新版本。
了解範圍
在建立任何項目之前,讓我們先檢閱範圍的概念。 Azure 提供四個管理層級:管理群組、訂用帳戶、資源群組和資源。 管理群組是預覽版本。 下圖顯示這些層級的範例。
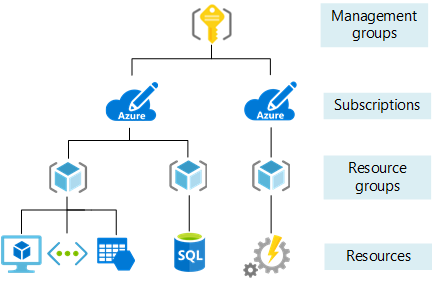
您可以在任何範圍層級套用管理設定。 您所選層級會判斷套用設定的範圍。 較低層級會繼承較高層級中的設定。 當您將設定套用到訂用帳戶時,訂用帳戶中的所有資源群組和資源都會套用該設定。 當您在資源群組上套用設定時,資源群組及其所有資源都會套用該設定。 不過,另一個資源群組沒有該設定。
通常我們會在較高層級套用重要設定,而在較低層級套用專案特定需求。 例如,您可能想要確定組織的所有資源都部署到特定區域。 若要完成這項需求,將原則套用至訂用帳戶,該訂用帳戶會指定允許的位置。 當貴組織中其他使用者新增新的資源群組和資源時,會自動強制執行允許的位置。
在本教學課程中,您會將所有的管理設定套用到資源群,讓您可以在完成後輕易地移除這些設定。
先來建立該資源群組。
az group create --name myResourceGroup --location "East US"
目前資源群組是空的。
Azure 角色型存取控制
您想要確定組織中的使用者具有這些資源的正確存取權等級。 您不想要授與不受限制的存取權給使用者,但是您又必須確定他們可以執行其工作。 Azure 角色型存取控制 (Azure RBAC) 可讓您管理哪些使用者具有權限可以在一個範圍內完成特定動作。
若要建立和移除角色指派,使用者必須具有 Microsoft.Authorization/roleAssignments/* 存取權。 此存取權是透過擁有者或使用者存取系統管理員角色來授與。
為了管理虛擬機器解決方案,有三個資源專屬角色可提供您經常需要的存取權:
相較於將角色指派給個別使用者,使用 Azure Active Directory 群組來含括需要執行類似動作的使用者,通常會較為容易。 然後,將該群組指派給適當的角色。 在本文中,請使用現有的群組來管理虛擬機器,或使用入口網站來建立 Azure Active Directory 群組。
建立新群組或找到現有群組後,請使用 az role assignment create 命令,將新的 Azure Active Directory 群組指派給資源群組的虛擬機器參與者角色。
adgroupId=$(az ad group show --group <your-group-name> --query objectId --output tsv)
az role assignment create --assignee-object-id $adgroupId --role "Virtual Machine Contributor" --resource-group myResourceGroup
如果您收到錯誤,指出 主體 < guid > 不存在於目錄中,則新群組尚未傳播至整個 Azure Active Directory。 請嘗試再次執行命令。
通常您需要針對網路參與者和儲存體帳戶參與者重複進行此程序,以確保已指派使用者來管理已部署的資源。 在本文中,您可以略過這些步驟。
Azure 原則
Azure 原則可協助您確認訂用帳戶中的所有資源均符合公司標準。 您的訂用帳戶已經有數個原則定義。 若要查看可用的原則定義,請使用 az policy definition list 命令:
az policy definition list --query "[].[displayName, policyType, name]" --output table
您會看到現有的原則定義。 原則類型不是內建就是自訂。 查看定義,尋找符合您要指派之條件的定義。 在本文中,您指派的原則要:
- 限制所有資源的位置。
- 限制虛擬機器的 SKU。
- 稽核未使用受控磁碟的虛擬機器。
在下列範例中,您會根據顯示名稱擷取三個原則定義。 您使用 az policy assignment create 命令將這些定義指派給資源群組。 針對某些原則,您要提供參數值來指定允許的值。
# Get policy definitions for allowed locations, allowed SKUs, and auditing VMs that don't use managed disks
locationDefinition=$(az policy definition list --query "[?displayName=='Allowed locations'].name | [0]" --output tsv)
skuDefinition=$(az policy definition list --query "[?displayName=='Allowed virtual machine SKUs'].name | [0]" --output tsv)
auditDefinition=$(az policy definition list --query "[?displayName=='Audit VMs that do not use managed disks'].name | [0]" --output tsv)
# Assign policy for allowed locations
az policy assignment create --name "Set permitted locations" \
--resource-group myResourceGroup \
--policy $locationDefinition \
--params '{
"listOfAllowedLocations": {
"value": [
"eastus",
"eastus2"
]
}
}'
# Assign policy for allowed SKUs
az policy assignment create --name "Set permitted VM SKUs" \
--resource-group myResourceGroup \
--policy $skuDefinition \
--params '{
"listOfAllowedSKUs": {
"value": [
"Standard_DS1_v2",
"Standard_E2s_v2"
]
}
}'
# Assign policy for auditing unmanaged disks
az policy assignment create --name "Audit unmanaged disks" \
--resource-group myResourceGroup \
--policy $auditDefinition
上述範例假設您已知道原則的參數。 如果您需要檢視參數,請使用:
az policy definition show --name $locationDefinition --query parameters
部署虛擬機器
您已指派角色和原則,現在可以開始部署您的解決方案。 預設大小是 Standard_DS1_v2,也就是所允許之 SKU 的其中一個。 如果預設位置中沒有 SSH 金鑰,命令會加以建立。
az vm create --resource-group myResourceGroup --name myVM --image UbuntuLTS --generate-ssh-keys
部署完成之後,您可以套用更多的管理設定至解決方案。
鎖定資源
資源鎖定可避免組織中的使用者不小心刪除或修改重要資源。 不同於角色型存取控制,資源鎖定會對所有使用者和角色套用限制。 您可以將鎖定層級設定為 CanNotDelete 或 ReadOnly。
若要建立或刪除管理鎖定,您必須擁有 Microsoft.Authorization/locks/* 動作的存取權。 在內建角色中,只有 擁有者 和 使用者存取管理員 被授與這些動作的存取權。
若要鎖定虛擬機器和網路安全性群組,請使用 az lock create 命令:
# Add CanNotDelete lock to the VM
az lock create --name LockVM \
--lock-type CanNotDelete \
--resource-group myResourceGroup \
--resource-name myVM \
--resource-type Microsoft.Compute/virtualMachines
# Add CanNotDelete lock to the network security group
az lock create --name LockNSG \
--lock-type CanNotDelete \
--resource-group myResourceGroup \
--resource-name myVMNSG \
--resource-type Microsoft.Network/networkSecurityGroups
若要測試鎖定,請嘗試執行下列命令:
az group delete --name myResourceGroup
您會看到一則錯誤,指出刪除作業因鎖定而無法完成。 只有當您明確移除鎖定後,才能刪除資源群組。 清除資源中會說明該步驟。
標記資源
您可將標籤套用至 Azure 資源,以便以邏輯方式依照類別組織這些資源。 每個標記都是由一個名稱和一個值所組成。 例如,您可以將「環境」名稱和「生產」值套用至生產環境中的所有資源。
若要在資源群組中新增兩個標記,請使用 az group update 命令:
az group update -n myResourceGroup --set tags.Environment=Test tags.Dept=IT
假設您想要新增第三個標記。 對新標記再次執行命令。 新標記會附加至現有標記。
az group update -n myResourceGroup --set tags.Project=Documentation
資源不會從資源群組繼承標記。 目前,您的資源群組具有三個標記,但是資源並沒有任何標記。 若要將所有標記從資源群組套用至其資源,並在資源上保留現有的標記,請使用下列指令碼:
# Get the tags for the resource group
jsontag=$(az group show -n myResourceGroup --query tags)
# Reformat from JSON to space-delimited and equals sign
t=$(echo $jsontag | tr -d '"{},' | sed 's/: /=/g')
# Get the resource IDs for all resources in the resource group
r=$(az resource list -g myResourceGroup --query [].id --output tsv)
# Loop through each resource ID
for resid in $r
do
# Get the tags for this resource
jsonrtag=$(az resource show --id $resid --query tags)
# Reformat from JSON to space-delimited and equals sign
rt=$(echo $jsonrtag | tr -d '"{},' | sed 's/: /=/g')
# Reapply the updated tags to this resource
az resource tag --tags $t$rt --id $resid
done
或者,您可以從資源群組將標記套用至資源,而不保留現有標記:
# Get the tags for the resource group
jsontag=$(az group show -n myResourceGroup --query tags)
# Reformat from JSON to space-delimited and equals sign
t=$(echo $jsontag | tr -d '"{},' | sed 's/: /=/g')
# Get the resource IDs for all resources in the resource group
r=$(az resource list -g myResourceGroup --query [].id --output tsv)
# Loop through each resource ID
for resid in $r
do
# Apply tags from resource group to this resource
az resource tag --tags $t --id $resid
done
若要在單一標記中合併數個值,請使用 JSON 字串。
az group update -n myResourceGroup --set tags.CostCenter='{"Dept":"IT","Environment":"Test"}'
若要移除資源群組上的所有標記,請使用:
az group update -n myResourceGroup --remove tags
若要將標籤套用至虛擬機器,請使用 az resource tag 命令。 資源上的任何現有標記都不會保留。
az resource tag -n myVM \
-g myResourceGroup \
--tags Dept=IT Environment=Test Project=Documentation \
--resource-type "Microsoft.Compute/virtualMachines"
依標籤尋找資源
若要尋找具有某標籤名稱和值的資源,請使用 az resource list 命令:
az resource list --tag Environment=Test --query [].name
傳回的值可用於管理工作,例如停止具有某標籤值的所有虛擬機器。
az vm stop --ids $(az resource list --tag Environment=Test --query "[?type=='Microsoft.Compute/virtualMachines'].id" --output tsv)
依標籤值檢視成本
將標記套用至資源之後,您可以檢視具有這些標記之資源的成本。 成本分析顯示最新的使用方式需要一些時間,因此您可能還看不到成本。 當有成本可顯示時,您可以檢視訂用帳戶中所有資源群組的資源成本。 使用者必須擁有訂用帳戶層級的計費資訊存取權才能查看成本。
若要在入口網站中依標記檢視成本,請選取您的訂用帳戶,然後選取 [成本分析]。
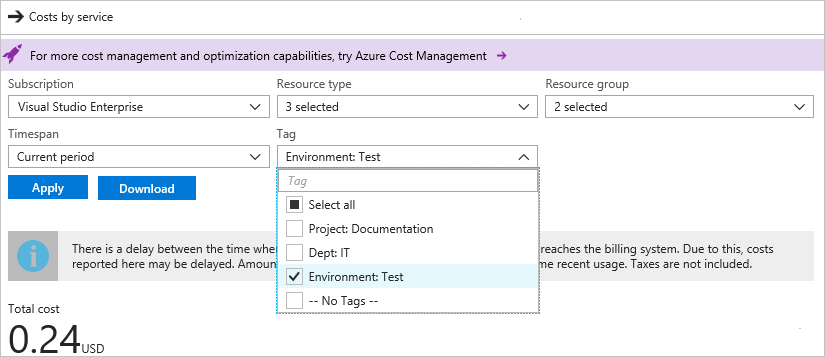
接著,以標記值篩選,選取 [套用]。
您也可以使用 Azure 使用量 API 概觀 ,以程式設計方式檢視成本。
清除資源
您無法刪除已鎖定的網路安全性群組,除非移除鎖定。 若要移除鎖定,請擷取鎖定的識別碼,並將這些識別碼提供給 az lock delete 命令:
vmlock=$(az lock show --name LockVM \
--resource-group myResourceGroup \
--resource-type Microsoft.Compute/virtualMachines \
--resource-name myVM --output tsv --query id)
nsglock=$(az lock show --name LockNSG \
--resource-group myResourceGroup \
--resource-type Microsoft.Network/networkSecurityGroups \
--resource-name myVMNSG --output tsv --query id)
az lock delete --ids $vmlock $nsglock
若不再需要,您可以使用 az group delete 命令來移除資源群組、VM 和所有相關資源。 結束 SSH 工作階段並返回您的 VM,然後將資源刪除,如下所示:
az group delete --name myResourceGroup
後續步驟
您在本教學課程中建立了自訂 VM 映像。 您已了解如何︰
- 將使用者指派給角色
- 套用會強制執行標準的原則
- 使用鎖定保護重要資源
- 標記資源以進行計費和管理
請繼續進行下一個教學課程,以了解如何在虛擬機器上識別變更及管理套件更新。