診斷虛擬機器路由問題
在本文中,您將了解如何藉由檢視對虛擬機器 (VM) 中的網路介面而言有效的路由,對來診斷路由問題。 Azure 會為每個虛擬網路子網路建立數個預設路由。 您可以在路由表中定義路由,並建立該路由表與子網路的關聯,以覆寫 Azure 的預設路由。 您所建立的路由、Azure 的預設路由和任何路由的組合若透過邊界閘道協定 (BGP) 經由 Azure VPN 閘道 (如果您的虛擬網路連線至內部部署網路) 從您的內部部署網路進行傳播,對子網路中的所有網路介面而言都將是有效路由。 如果您不熟悉虛擬網路、網路介面或路由概念,請參閱虛擬網路概觀、網路介面及路由概觀。
案例
您嘗試連線至 VM,但連線失敗。 若要判斷為何無法連線至 VM,您可以使用 Azure 入口網站、PowerShell 或 Azure CLI 來檢視網路介面的有效路由。
下列步驟假設您具有可檢視有效路由的現有 VM。 如果您沒有現有的 VM,請先部署 Linux 或 Windows VM,用以完成本文中的工作。 本文中的範例適用於名為 myVM 的 VM,而該 VM 的網路介面名為 myVMNic1。 VM 和網路介面皆位於名為 myResourceGroup 的資源群組,且位於「美國東部」區域。 請針對您要診斷問題的 VM,適當地變更步驟中的值。
使用 Azure 入口網站進行診斷
在 Azure 入口網站頂端的搜尋方塊中,輸入執行中 VM 的名稱。 當 VM 的名稱出現在搜尋結果中時,請加以選取。
在左側的 [設定] 下,選取 [網路],然後選取其名稱以瀏覽至網路介面資源。
選取左側的 [有效路由]。 對名為 myVMNic1 的網路介面來說,有效的路由如下圖中所示:
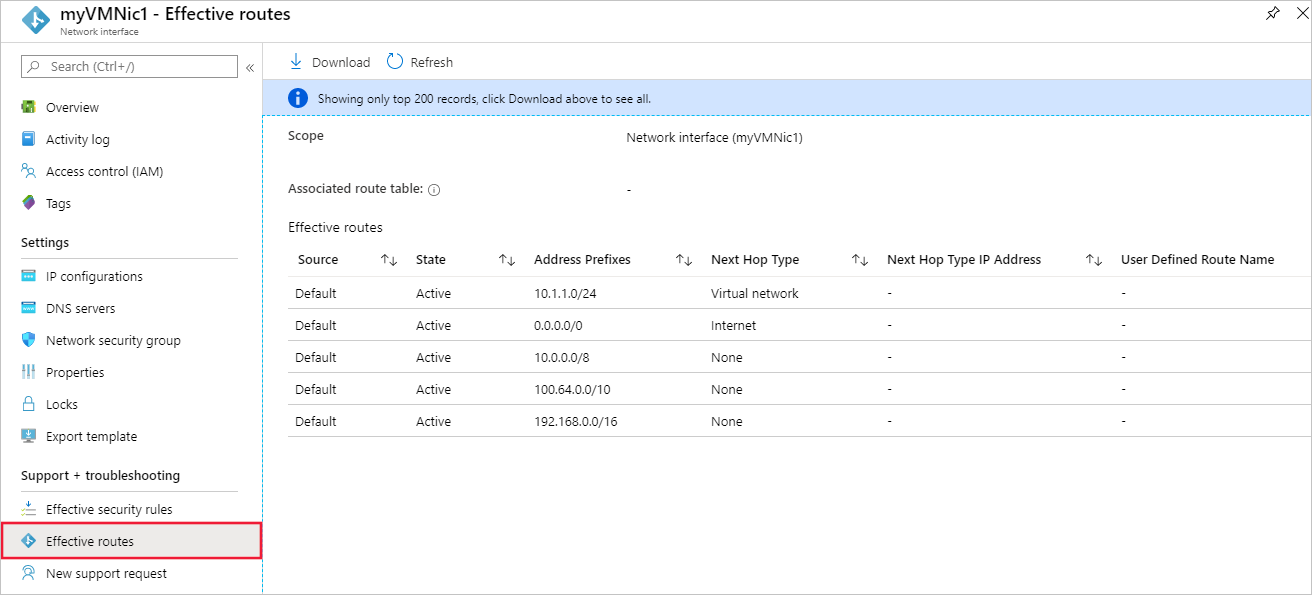
如果有多個網路介面連結至 VM,您可以選取任何網路介面以檢視其有效路由。 因為每個網路介面可以位於不同子網路中,所以每個網路介面可有不同的有效路由。
在上圖顯示的範例中,列出的路由是 Azure 為每個子網路建立的預設路由。 您的清單至少會有這些路由,但也可能會有其他路由,視您為虛擬網路啟用的功能而定,例如,您讓虛擬網路可與其他虛擬網路對等互連,或可透過 Azure VPN 閘道連線至您的內部部署網路。 若要深入了解每個路由,以及您可檢視的其他網路介面路由,請參閱虛擬網路流量路由。 如果您的清單中有大量路由,您可以選取 [下載] 來下載含有路由清單的 .csv 檔案,試著簡化作業。
雖然您在前幾個步驟中是透過 VM 來檢視有效路由,但您也可以透過下列途徑來檢視有效路由:
使用 PowerShell 進行診斷
注意
建議您使用 Azure Az PowerShell 模組來與 Azure 互動。 請參閱安裝 Azure PowerShell 以開始使用。 若要了解如何移轉至 Az PowerShell 模組,請參閱將 Azure PowerShell 從 AzureRM 移轉至 Az。
您可以執行 Azure Cloud Shell 中採用的命令,或從您的電腦執行 PowerShell。 Azure Cloud Shell 是免費的互動式殼層。 它具有預先安裝和設定的共用 Azure 工具,可與您的帳戶搭配使用。 若是從電腦執行 PowerShell,則需要 Azure PowerShell 模組 1.0.0 版或更新版本。 請在您的電腦上執行 Get-Module -ListAvailable Az,以尋找已安裝的版本。 如果您需要升級,請參閱安裝 Azure PowerShell 模組。 如果您在本機執行 PowerShell,則還需要執行 Connect-AzAccount 以使用具有必要權限的帳戶登入 Azure。
請使用 Get-AzEffectiveRouteTable 取得網路介面的有效路由。 下列範例可取得對名為 myVMNic1 (位於 myResourceGroup 的資源群組中) 的網路介面有效的路由:
Get-AzEffectiveRouteTable `
-NetworkInterfaceName myVMNic1 `
-ResourceGroupName myResourceGroup `
| Format-Table
若要了解輸出中傳回的資訊,請參閱路由概觀。 只有在 VM 處於執行狀態時,才會傳回輸出。 若有多個網路介面連結至 VM,您可以檢視每個網路介面的有效路由。 因為每個網路介面可以位於不同子網路中,所以每個網路介面可有不同的有效路由。 如果仍有通訊問題,請參閱其他診斷和考量。
如果您不知道網路介面的名稱,但知道該網路介面所附加至的 VM 名稱,則下列命令會針對所有附加至 VM 的網路介面,傳回其識別碼:
$VM = Get-AzVM -Name myVM `
-ResourceGroupName myResourceGroup
$VM.NetworkProfile
您會收到類似於下列範例的輸出:
NetworkInterfaces
-----------------
{/subscriptions/<ID>/resourceGroups/myResourceGroup/providers/Microsoft.Network/networkInterfaces/myVMNic1
在上述輸出中,網路介面名稱是 myVMNic1。
使用 Azure CLI 進行診斷
您可以遵循 Azure Cloud Shell 的用法,執行此命令,或從您的電腦上執行 CLI。 本文需要 Azure CLI 2.0.32 版或更新的版本。 執行 az --version 以尋找安裝的版本。 如果您需要安裝或升級,請參閱安裝 Azure CLI。 如果您在本機執行 Azure CLI,還需要執行 az login 並使用具有必要權限的帳戶登入 Azure。
使用 az network nic show-effective-route-table 取得網路介面的有效路由。 下列範例可取得對名為 myVMNic1 (位於 myResourceGroup 的資源群組中) 的網路介面有效的路由:
az network nic show-effective-route-table \
--name myVMNic1 \
--resource-group myResourceGroup
若要了解輸出中傳回的資訊,請參閱路由概觀。 只有在 VM 處於執行狀態時,才會傳回輸出。 若有多個網路介面連結至 VM,您可以檢視每個網路介面的有效路由。 因為每個網路介面可以位於不同子網路中,所以每個網路介面可有不同的有效路由。 如果仍有通訊問題,請參閱其他診斷和考量。
如果您不知道網路介面的名稱,但知道該網路介面所附加至的 VM 名稱,則下列命令會針對所有附加至 VM 的網路介面,傳回其識別碼:
az vm show \
--name myVM \
--resource-group myResourceGroup
解決問題
要解決路由問題通常需要:
- 新增自訂路由以覆寫 Azure 的其中一個預設路由。 了解如何新增自訂屬性。
- 變更或移除可能導致路由至不當位置的自訂路由。 了解如何變更或刪除自訂路由。
- 確定您已定義的任何自訂路由所屬的路由表已與網路介面所在的子網路相關聯。 了解如何建立路由表與子網路的關聯。
- 確定您已部署的裝置 (例如 Azure VPN 閘道或網路虛擬設備) 是可執行的。 使用網路監看員的 VPN 診斷功能判斷 Azure VPN 閘道是否有任何問題。
如果仍有通訊問題,請參閱考量和其他診斷。
考量
對通訊問題進行疑難排解時,請考量以下幾點︰
- 路由所依據的是您所定義的路由、邊界閘道協定 (BGP) 和系統路由之間的最長首碼比對 (LPM)。 如果有多個路由有相同的 LPM 相符項,則會根據路由來源,以路由概觀中所列的順序選取路由。 有有效路由時,您將只會看到所有可用的路由中符合 LPM 的有效路由。 了解如何評估網路介面的路由,有助於對可能會影響 VM 通訊的特定路由進行疑難排解。
- 如果您已定義網路虛擬設備 (NVA) 的自訂路由,並以 VirtualAppliance 作為下一個躍點類型,請確定接收流量的 NVA 已啟用 IP 轉送,否則封包會被捨棄。 深入了解如何啟用網路介面的 IP 轉送。 此外,作業系統或 NVA 內的應用程式也必須能夠轉送網路流量,而進行相關設定。
- 如果您已建立 0.0.0.0/0 的路由,則所有輸出網際網路流量都會路由至您所指定的下一個躍點,例如 NVA 或 VPN 閘道。 我們通常將建立此類路由的作業稱為強制通道。 使用 RDP 或 SSH 通訊協定從網際網路連至 VM 的遠端連線可能無法以此路由執行,這取決於下一個躍點處理流量的方式。 符合下列其中一個條件時,可以啟用強制通道︰
- 透過下一個躍點類型的 VPN 閘道建立路由,而使用站對站 VPN 時。 深入了解如何設定強制通道。
- 如果在使用站對站 VPN 或 ExpressRoute 線路時透過 BGP 經由虛擬網路閘道通告了 0.0.0.0/0 (預設路由)。 深入了解如何搭配使用 BGP 與站對站 VPN 或 ExpressRoute。
- 若要讓虛擬網路對等互連流量正常運作,對等互連虛擬網路的首碼範圍必須要有下一個躍點類型為 VNet 對等互連的系統路由。 如果沒有此類路由,且虛擬網路對等互連連結已連線︰
- 請在等候數秒後重試。 這是新建立的對等互連連結,有時候需要較長的時間才能將路由傳播到子網路中的所有網路介面。 若要深入了解虛擬網路對等互連,請參閱虛擬網路對等互連概觀和管理虛擬網路對等互連。
- 網路安全性群組規則可能會影響通訊。 如需詳細資訊,請參閱診斷虛擬機器網路流量篩選問題。
- 雖然 Azure 會為每個 Azure 網路介面指派預設路由,但如果您有多個網路介面連結至 VM,則在 VM 的作業系統內只會為主要網路介面指派預設路由 (0.0.0.0/0) 或閘道。 了解如何為連結至 Windows 或 Linux VM 的次要網路介面建立預設路由。 深入瞭解主要和輔助網路介面。
其他診斷
- 若要執行快速測試,針對以某位置為目標的流量判斷其下一個躍點類型,請使用 Azure 網路監看員的下一個躍點功能。 下一個躍點會指出以指定位置為目標的流量所使用的下一個躍點類型。
- 如果沒有任何會造成 VM 網路通訊失敗的路由,則問題可能是由執行於 VM 作業系統內的防火牆軟體所致
- 如果您要使用強制通道透過 VPN 閘道或 NVA 將流量傳至內部部署裝置,您可能無法從網際網路連線至 VM,視您為裝置設定路由的方式而定。 請確認您為裝置設定的路由會將流量路由至 VM 的公用或私人 IP 位址。
- 使用網路監看員的連線疑難排解功能,判斷輸出通訊問題的路由、篩選和 OS 內部原因。
下一步
- 了解路由表和路由的所有工作、屬性和設定。
- 了解所有的下一個躍點類型、系統路由和 Azure 選取路由的方式。