網路安全性群組如何篩選網路流量
您可以使用 Azure 網路安全性群組在 Azure 虛擬網路中篩選進出 Azure 資源的網路流量。 網路安全性群組包含安全性規則,用來允許或拒絕進出多種 Azure 資源類型的輸入和輸出網路流量。 針對每個規則,您可以指定來源與目的地、連接埠和通訊協定。
您可以將數個 Azure 服務中的資源部署到 Azure 虛擬網路。 如需完整清單,請參閱可以部署至虛擬網路的服務。 您可以將零個或一個網路安全性群組關聯至每個虛擬網路子網路,以及虛擬機器中的網路介面。 您可以將相同的網路安全性群組關聯至所需數量的子網路和網路介面。
下圖以不同案例說明網路安全性群組可如何部署,以 允許網路流量透過 TCP 連接埠 80 來進出網際網路:
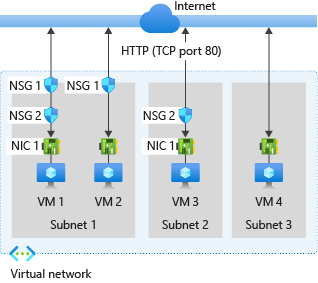
請參考上圖及下列文字,以了解 Azure 如何處理網路安全性群組的輸入和輸出規則:
輸入流量
針對輸入流量,Azure 會先處理子網路的相關聯網路安全性群組中的規則 (如果有的話),然後再處理網路介面的相關聯網路安全性群組中的規則 (如果有的話)。 此流程也包含子網路內部流量。
VM1:處理 NSG1 中的安全性規則,因為與 Subnet1 相關聯,而且 VM1 位於 Subnet1 中。 除非您已建立允許連接埠 80 輸入的規則,否則 DenyAllInbound 預設安全性規則會拒絕流量。 此封鎖的流量接著不會由 NSG2 評估,因為它與網路介面相關聯。 不過,如果 NSG1 在其安全性規則中允許連接埠 80,則 NSG2 會處理流量。 若要允許從連接埠 80 到虛擬機器,NSG1 和 NSG2 都必須有規則來允許從網際網路到連接埠 80。
VM2:在 NSG1 中的規則會進行處理,因為VM2 也位於 Subnet1 中。 由於 VM2 沒有與其網路介面相關聯的網路安全性群組,因此接收允許通過 NSG1 的所有流量,或拒絕 NSG1 拒絕的所有流量。 如果網路安全性群組與子網路相關聯,則相同子網路中的所有資源會一起接收或拒絕流量。
VM3:由於沒有網路安全性群組與 Subnet2 相關聯,所以允許流量進入子網路並由 NSG2 處理,因為 NSG2 與連結至 VM3 的網路介面相關聯。
VM4:流量被封鎖進入 VM4,因為網路安全性群組未與 Subnet3 或虛擬機器中的網路介面相關聯。 如果沒有任何網路安全性群組與子網路和網路介面相關聯,則所有網路流量都會透過子網路和網路介面被封鎖。
輸出流量
針對輸出流量,Azure 會先處理網路介面的相關聯網路安全性群組中的規則 (如果有的話),然後再處理子網路的相關聯網路安全性群組中的規則 (如果有的話)。 此流程也包含子網路內部流量。
VM1:NSG2 中的安全性規則會進行處理。 除非您建立安全性規則,拒絕輸出到網際網路的連接埠 80,否則 NSG1 和 NSG2 中的 AllowInternetOutbound 預設安全性規則都會允許流量。 如果 NSG2 在其安全性規則中拒絕連接埠 80,則會拒絕流量,而 NSG1 永遠不會評估該流量。 若要拒絕流量從連接埠 80 輸出虛擬機器,其中一個網路安全性群組或兩個網路安全性群組必須有規則來拒絕將流量流向網際網路的連接埠 80。
VM2:所有流量都通過網路介面傳送到子網路,因為連結至 VM2 的網路介面沒有相關聯的網路安全性群組。 處理 NSG1 中的規則。
VM3:如果 NSG2 在其安全性規則中拒絕連接埠 80,則會拒絕流量。 如果 NSG2 未拒絕連接埠 80,NSG2 中的 AllowInternetOutbound 預設安全性規則會允許流量,因為沒有與 Subnet2 相關聯的網路安全性群組。
VM4:所有網路流量會允許從 VM4 輸出,因為網路安全性群組未與連結至虛擬機器的網路介面或 Subnet3 相關聯。
子網路內部流量
請務必注意,在 NSG 中與子網路相關聯的安全性規則可能會影響其內部 VM 之間的連線能力。 根據預設,相同子網路中的虛擬機器可以根據允許子網路內部流量的預設 NSG 規則進行通訊。 如果您將規則新增至 NSG1,以拒絕所有輸入和輸出流量,VM1 和 VM2 將無法彼此通訊。
藉由檢視網路介面的有效安全性規則,您就可以輕鬆地檢視網路介面中套用的彙總規則。 您也可以使用 Azure 網路監看員中的 IP 流量驗證功能,來判斷是否允許網路介面的雙向通訊。 您可以使用 IP 流量驗證,來判斷是否允許或拒絕通訊。 此外,使用 IP 流量驗證,來呈現負責允許或拒絕流量的網路安全性規則身分識別。
注意
網路安全性群組會與子網路或部署在傳統部署模型中的虛擬機器和雲端服務相關聯,以及與 Resource Manager 部署模型中的子網路或網路介面相關聯。 若要深入了解 Azure 部署模型,請參閱了解 Azure 部署模型。
提示
除非您有特殊原因要這麼做,否則我們建議您讓網路安全性群組與子網路或網路介面的其中一個建立關聯,而非同時與這兩者建立關聯。 因為如果與子網路相關聯的網路安全性群組中,以及與網路介面相關聯的網路安全性群組中都存在規則,則這兩個規則可能會發生衝突,您可能會遇到需要進行疑難排解的非預期通訊問題。
下一步
若要了解虛擬網路中可部署哪些 Azure 資源,並使這些資源與網路安全性群組產生關聯,請參閱 Azure 服務的虛擬網路整合。
如果您從未建立過網路安全性群組,可以完成快速教學課程,以取得一些建立體驗。
如果您熟悉網路安全性群組,並且有管理需求,請參閱管理網路安全性群組。
如果您有通訊問題,因而需要對網路安全性群組進行疑難排解,請參閱診斷虛擬機器網路流量篩選問題。
了解如何啟用網路安全性群組流量記錄,分析進出與網路安全性群組相關聯資源的網路流量。