使用 PowerShell 建立具有站對站 VPN 連線的 VNet
本文說明如何使用 PowerShell 來建立從內部部署網路到 VNet 的站對站 VPN 閘道連線。 本文中的步驟適用於 Resource Manager 部署模型。 您也可從下列清單中選取不同的選項,以使用不同的部署工具或部署模型來建立此組態:
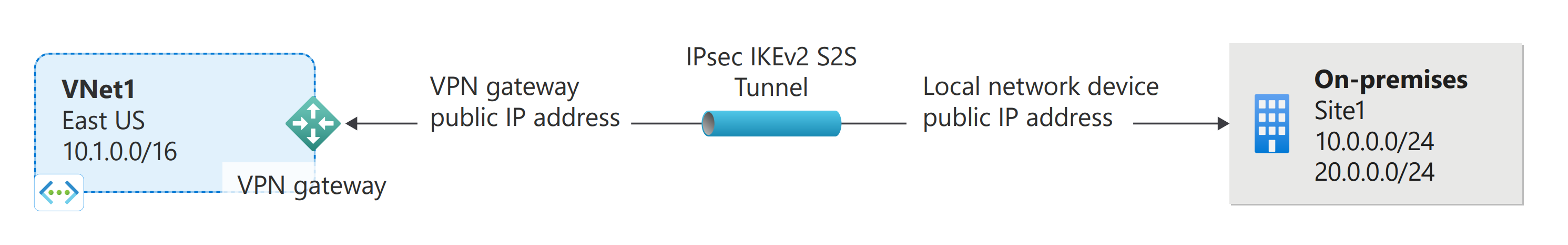
站對站 VPN 閘道連線可用來透過 IPsec/IKE (IKEv1 或 IKEv2) VPN 通道,將內部部署網路連線到 Azure 虛擬網路。 此類型的連線需要位於內部部署的 VPN 裝置,且您已對該裝置指派對外開放的公用 IP 位址。 如需 VPN 閘道的詳細資訊,請參閱關於 VPN 閘道。
開始之前
在開始設定之前,請確認您已符合下列條件:
- 確定您有相容的 VPN 裝置以及能夠對其進行設定的人員。 如需相容 VPN 裝置和裝置組態的詳細資訊,請參閱關於 VPN 裝置。
- 確認您的 VPN 裝置有對外開放的公用 IPv4 位址。
- 如果您不熟悉位於內部部署網路設定的 IP 位址範圍,您需要與能夠提供那些詳細資料的人協調。 當您建立此組態時,您必須指定 IP 位址範圍的首碼,以供 Azure 路由傳送至您的內部部署位置。 內部部署網路的子網路皆不得與您所要連線的虛擬網路子網路重疊。
Azure PowerShell
本文使用 PowerShell Cmdlet。 若要執行 Cmdlet,您可以使用 Azure Cloud Shell。 Cloud Shell 是免費的互動式殼層,可讓您用來執行本文中的步驟。 它具有預先安裝和設定的共用 Azure 工具,可與您的帳戶搭配使用。
若要開啟 Cloud Shell,只要選取程式碼區塊右上角的 [開啟 Cloudshell] 即可。 您也可以移至 https://shell.azure.com/powershell,在個別的瀏覽器索引標籤上開啟 Cloud Shell。 選取 [複製] 以複製程式碼區塊、將它們貼上到 Cloud Shell 中,然後選取 Enter 鍵以執行它們。
您也可以在本機電腦上安裝並執行 Azure PowerShell Cmdlet。 PowerShell Cmdlet 會經常更新。 如果您尚未安裝最新版本,指示中指定的值可能會失敗。 若要尋找電腦上安裝的 Azure PowerShell 版本,請使用 Get-Module -ListAvailable Az Cmdlet。 若要安裝或更新,請參閱安裝 Azure PowerShell 模組。
範例值
本文的範例使用下列值。 您可以使用這些值來建立測試環境,或參考這些值,進一步了解本文中的範例。
#Example values
VnetName = VNet1
ResourceGroup = TestRG1
Location = East US
AddressSpace = 10.1.0.0/16
SubnetName = Frontend
Subnet = 10.1.0.0/24
GatewaySubnet = 10.1.255.0/27
LocalNetworkGatewayName = Site1
LNG Public IP = <On-premises VPN device IP address>
Local Address Prefixes = 10.0.0.0/24, 20.0.0.0/24
Gateway Name = VNet1GW
PublicIP = VNet1GWPIP
Gateway IP Config = gwipconfig1
VPNType = RouteBased
GatewayType = Vpn
ConnectionName = VNet1toSite1
1.建立虛擬網路和閘道器子網路
如果您還沒有虛擬網路,請建立一個。 在建立虛擬網路時,請確定您指定的位址空間沒有與您在內部部署網路上所擁有的任何位址空間重疊。
注意
為了讓此 VNet 連線到內部部署位置,您需要與內部部署網路系統管理員協調,以切割出此虛擬網路專用的 IP 位址範圍。 如果 VPN 連線的兩端存在重複的位址範圍,流量就不會如預期的方式進行路由。 此外,如果您想要將此 VNet 連線到另一個 VNet,則位址空間不能與其他 VNet 重疊。 因此,請謹慎規劃您的網路組態。
關於閘道子網路
虛擬網路閘道會使用稱為閘道子網路的特定子網路。 閘道子網路是您設定虛擬網路時,所指定虛擬網路 IP 位址範圍的一部分。 其包含虛擬網路閘道資源和服務所使用的 IP 位址。 子網路必須命名為 'GatewaySubnet' 才可供 Azure 部署閘道資源。 您無法指定不同的子網路來作為閘道資源的部署目的地。 如果您沒有名為 'GatewaySubnet' 的子網路,當您建立 VPN 閘道時,它將會失敗。
當您建立閘道子網路時,您可指定子網路包含的 IP 位址數目。 所需的 IP 位址數目取決於您想要建立的 VPN 閘道組態。 有些組態需要的 IP 位址比其他組態多。 我們建議您建立使用 /27 或/28 的閘道子網路。
如果您看到錯誤指出位址空間與子網路重疊,或子網路未包含在虛擬網路的位址空間內,請檢查您的 VNet 位址範圍。 您為虛擬網路所建立的位址範圍中可能沒有足夠的可用 IP 位址。 例如,如果您的預設子網路包含整個位址範圍,則沒有剩餘任何 IP 位址可供建立其他子網路。 您可以調整現有位址空間內的子網路以釋出 IP 位址,也可以指定其他位址範圍並於該處建立閘道子網路。
重要
使用閘道子網路時,請避免將網路安全性群組 (NSG) 與閘道子網路產生關聯。 將網路安全性群組與此子網路產生關聯,可能會導致您的虛擬網路閘道 (VPN 與 ExpressRoute 閘道) 如預期停止運作。 如需有關網路安全性群組的詳細資訊,請參閱什麼是網路安全性群組?。
建立虛擬網路和閘道器子網路
此範例會建立虛擬網路和閘道子網路。 如果您已經有虛擬網路,並需要對它新增閘道子網路,請參閱將閘道子網路新增至您已建立的虛擬網路。
建立資源群組:
New-AzResourceGroup -Name TestRG1 -Location 'East US'
建立虛擬網路。
設定變數。
$subnet1 = New-AzVirtualNetworkSubnetConfig -Name 'GatewaySubnet' -AddressPrefix 10.1.255.0/27 $subnet2 = New-AzVirtualNetworkSubnetConfig -Name 'Frontend' -AddressPrefix 10.1.0.0/24建立 VNet。
New-AzVirtualNetwork -Name VNet1 -ResourceGroupName TestRG1 ` -Location 'East US' -AddressPrefix 10.1.0.0/16 -Subnet $subnet1, $subnet2
將閘道器子網路加入至您已建立的虛擬網路
如果您已經有虛擬網路,但需要新增閘道子網路,請使用本節中的步驟。
設定變數。
$vnet = Get-AzVirtualNetwork -ResourceGroupName TestRG1 -Name VNet1建立閘道子網路。
Add-AzVirtualNetworkSubnetConfig -Name 'GatewaySubnet' -AddressPrefix 10.1.255.0/27 -VirtualNetwork $vnet設定組態。
Set-AzVirtualNetwork -VirtualNetwork $vnet
2.建立區域網路閘道
區域網路閘道 (LNG) 通常是指您的內部部署位置。 它與虛擬網路閘道不同。 請賦予網站可供 Azure 參考的名稱,然後指定您想要與其建立連線之內部部署 VPN 裝置的 IP 位址。 也請指定 IP 位址首碼,以供系統透過 VPN 閘道路由至 VPN 裝置。 您指定的位址首碼是位於內部部署網路上的首碼。 如果您的內部部署網路有所變更,您可以輕鬆地更新首碼。
選取下列其中一個範例。 範例中使用的值為:
- GatewayIPAddress 是內部部署 VPN 裝置的 IP 位址。
- AddressPrefix 是您的內部部署位址空間。
單一位址首碼範例
New-AzLocalNetworkGateway -Name Site1 -ResourceGroupName TestRG1 `
-Location 'East US' -GatewayIpAddress '23.99.221.164' -AddressPrefix '10.0.0.0/24'
多個位址首碼範例
New-AzLocalNetworkGateway -Name Site1 -ResourceGroupName TestRG1 `
-Location 'East US' -GatewayIpAddress '23.99.221.164' -AddressPrefix @('20.0.0.0/24','10.0.0.0/24')
3.要求公用 IP 位址
VPN 閘道必須具有公用 IP 位址。 您會先要求 IP 位址資源,然後在建立虛擬網路閘道時參考它。 建立 VPN 閘道時,系統會將 IP 位址動態指派給此資源。 公用 IP 位址只會在刪除或重新建立閘道時變更。 它不會因為重新調整、重設或 VPN 閘道的其他內部維護/升級而變更。
要求虛擬網路 VPN 閘道的公用 IP 位址。
$gwpip= New-AzPublicIpAddress -Name VNet1GWPIP -ResourceGroupName TestRG1 -Location 'East US' -AllocationMethod Static -Sku Standard
4.建立閘道器 IP 位址組態
閘道設定定義要使用的子網路 ('GatewaySubnet') 和公用 IP 位址。 使用下列範例來建立閘道組態:
$vnet = Get-AzVirtualNetwork -Name VNet1 -ResourceGroupName TestRG1
$subnet = Get-AzVirtualNetworkSubnetConfig -Name 'GatewaySubnet' -VirtualNetwork $vnet
$gwipconfig = New-AzVirtualNetworkGatewayIpConfig -Name gwipconfig1 -SubnetId $subnet.Id -PublicIpAddressId $gwpip.Id
5.建立 VPN 閘道
建立虛擬網路 VPN 閘道。 建立閘道通常可能需要 45 分鐘或更久,視選取的閘道 SKU 而定。 範例中會使用下列值:
- 網站間組態的 -GatewayType 是 Vpn。 閘道器類型永遠是您實作的組態的特定類型。 例如,其他閘道器組態可能需要 -GatewayType ExpressRoute。
- -VpnType 可以是 RouteBased (在某些文件中稱為動態閘道器),或 PolicyBased (在某些文件中稱為靜態閘道器)。 如需 VPN 閘道類型的詳細資訊,請參閱關於 VPN 閘道。
- 選取您想要使用的閘道 SKU。 某些 SKU 有組態限制。 如需詳細資訊,請參閱閘道 SKU。 如果您在建立有關 -GatewaySku 的 VPN 閘道時發生錯誤,請確認您已安裝最新版的 PowerShell Cmdlet。
New-AzVirtualNetworkGateway -Name VNet1GW -ResourceGroupName TestRG1 `
-Location 'East US' -IpConfigurations $gwipconfig -GatewayType Vpn `
-VpnType RouteBased -GatewaySku VpnGw2
6.設定 VPN 裝置
內部部署網路的站對站連線需要 VPN 裝置。 在此步驟中,設定 VPN 裝置。 設定 VPN 裝置時,您需要下列項目:
共用金鑰。 這個共同金鑰與您建立站對站 VPN 連線時指定的共用金鑰相同。 在我們的範例中,我們會使用基本的共用金鑰。 我們建議您產生更複雜的金鑰以供使用。
虛擬網路閘道的公用 IP 位址。 您可以使用 Azure 入口網站、PowerShell 或 CLI 來檢視公用 IP 位址。 若要使用 PowerShell 尋找虛擬網路閘道的公用 IP 位址,請使用下列範例。 在此範例中,VNet1GWPIP 是您在先前步驟中所建立公用 IP 位址資源的名稱。
Get-AzPublicIpAddress -Name VNet1GWPIP -ResourceGroupName TestRG1
若要下載 VPN 裝置組態指令碼:
根據您所擁有的 VPN 裝置,您或許可以下載 VPN 裝置設定指令碼。 如需詳細資訊,請參閱下載 VPN 裝置組態指令碼。
請參閱下列連結以取得其他組態資訊︰
如需有關相容的 VPN 裝置資訊,請參閱 VPN 裝置。
請在設定 VPN 裝置之前,檢查您要使用的 VPN 裝置是否有任何已知裝置相容性問題。
如需裝置組態設定的連結,請參閱已經驗證的 VPN 裝置。 會以最佳方式來提供裝置組態連結。 最好一律洽詢您的裝置製造商以取得最新的組態資訊。 該清單會顯示已完成測試的版本。 如果您的 OS 不在清單中,版本仍然可能相容。 請洽詢您的裝置製造商,以驗證您 VPN 裝置的 OS 版本相容。
如需 VPN 裝置組態的概觀,請參閱 VPN 裝置組態概觀。
如需編輯裝置組態範例的相關資訊,請參閱編輯範例。
如需密碼編譯需求,請參閱關於密碼編譯需求和 Azure VPN 閘道。
如需 IPsec/IKE 參數的詳細資訊,請參閱關於 VPN 裝置和站對站 VPN 閘道連線的 IPsec/IKE 參數。 除了您完成設定所需的其他參數資訊之外,此連結還會顯示 IKE 版本、Diffie-hellman 群組、驗證方法、加密和雜湊演算法、SA 存留期、PFS 和 DPD 的相關資訊。
如需 IPsec/IKE 原則設定步驟,請參閱設定 S2S VPN 或 VNet 對 VNet 連線的 IPsec/IKE 原則。
若要連線多個以原則為基礎的 VPN 裝置,請參閱使用 PowerShell 將 Azure VPN 閘道連線至多個內部部署以原則為基礎的 VPN 裝置。
7.建立 VPN 連線
接下來,在虛擬網路閘道與 VPN 裝置之間建立網站間 VPN 連線。 請務必將值取代為您自己的值。 共用的金鑰必須符合您用於 VPN 裝置設定的值。 請注意,網站間的「-ConnectionType」為 IPsec。
設定變數。
$gateway1 = Get-AzVirtualNetworkGateway -Name VNet1GW -ResourceGroupName TestRG1 $local = Get-AzLocalNetworkGateway -Name Site1 -ResourceGroupName TestRG1建立連線。
New-AzVirtualNetworkGatewayConnection -Name VNet1toSite1 -ResourceGroupName TestRG1 ` -Location 'East US' -VirtualNetworkGateway1 $gateway1 -LocalNetworkGateway2 $local ` -ConnectionType IPsec -SharedKey 'abc123'
過一會兒,連接將會建立。
8.驗證 VPN 連線
VPN 連線有幾種不同的驗證方式。
您可以使用 'Get-AzVirtualNetworkGatewayConnection' Cmdlet,並在搭配或不搭配 '-Debug' 的情況下驗證連線是否成功。
請使用下列 Cmdlet 範例,並將值設定為與您狀況相符的值。 出現提示時,請選取 [A] 以執行 [全部]。 在範例中,'-Name' 是指您想要測試之連線的名稱。
Get-AzVirtualNetworkGatewayConnection -Name VNet1toSite1 -ResourceGroupName TestRG1完成 Cmdlet 之後,請檢視值。 在下列範例中,連接狀態會顯示為 [已連接],且您可以看見輸入和輸出位元組。
"connectionStatus": "Connected", "ingressBytesTransferred": 33509044, "egressBytesTransferred": 4142431
連線至虛擬機器
您可以建立 VM 的遠端桌面連線,以連線至已部署至虛擬網路的 VM。 一開始確認您可以連線至 VM 的最佳方法是使用其私人 IP 位址 (而不是電腦名稱) 進行連線。 這樣一來,您會測試以查看您是否可以連線,而不是否已正確設定名稱解析。
找出私人 IP 位址。 在 Azure 入口網站中或使用 PowerShell 查看 VM 的屬性,即可找到 VM 的私人 IP 位址。
Azure 入口網站:在 Azure 入口網站中尋找您的 VM。 檢視 VM 的屬性。 系統會列出私人 IP 位址。
PowerShell:使用範例來檢視資源群組中的 VM 和私人 IP 位址清單。 使用此範例前,您不需要加以修改。
$VMs = Get-AzVM $Nics = Get-AzNetworkInterface | Where-Object VirtualMachine -ne $null foreach ($Nic in $Nics) { $VM = $VMs | Where-Object -Property Id -eq $Nic.VirtualMachine.Id $Prv = $Nic.IpConfigurations | Select-Object -ExpandProperty PrivateIpAddress $Alloc = $Nic.IpConfigurations | Select-Object -ExpandProperty PrivateIpAllocationMethod Write-Output "$($VM.Name): $Prv,$Alloc" }
確認您已連線至虛擬網路。
在工作列上的搜尋方塊中輸入「RDP」或「遠端桌面連線」以開啟 [遠端桌面連線]。 然後選取 [遠端桌面連線]。 您也可以在 PowerShell 中使用
mstsc命令,開啟 [遠端桌面連線]。在 [遠端桌面連線] 中,輸入 VM 的私人 IP 位址。 您可以選取 [顯示選項],調整其他設定,然後進行連線。
如果您無法透過 VPN 連線與 VM 連線,請檢查下列幾點:
- 確認您的 VPN 連線成功。
- 確認您正連線至 VM 的私人 IP 位址。
- 如果您可以使用私人 IP 位址 (而非電腦名稱) 來連線至 VM,請確認您已正確設定 DNS。 如需 VM 的名稱解析運作方式的詳細資訊,請參閱 VM 的名稱解析 (部分機器翻譯)。
如需 RDP 連線的詳細資訊,請參閱對 VM 的遠端桌面連線進行疑難排解。
修改區域網路閘道的 IP 位址首碼
如果您要路由傳送到內部部署位置的 IP 位址首碼變更,您可以修改區域網路閘道。 使用這些範例時,請將值修改為符合您的環境。
若要新增其他位址首碼:
設定 LocalNetworkGateway 的變數。
$local = Get-AzLocalNetworkGateway -Name Site1 -ResourceGroupName TestRG1修改首碼。 您指定的值會覆寫先前的值。
Set-AzLocalNetworkGateway -LocalNetworkGateway $local ` -AddressPrefix @('10.101.0.0/24','10.101.1.0/24','10.101.2.0/24')
若要移除位址首碼:
省略您不再需要的首碼。 此範例中不再需要首碼 10.101.2.0/24 (來自先前的範例),因此我們將更新區域網路閘道,並排除該首碼。
設定 LocalNetworkGateway 的變數。
$local = Get-AzLocalNetworkGateway -Name Site1 -ResourceGroupName TestRG1使用更新的首碼設定閘道。
Set-AzLocalNetworkGateway -LocalNetworkGateway $local ` -AddressPrefix @('10.101.0.0/24','10.101.1.0/24')
修改區域網路閘道的閘道 IP 位址
如果您想要連線的 VPN 裝置已變更其公用 IP 位址,您需要修改區域網路閘道,以反映該變更。 修改此值時,您也可以同時修改位址首碼。 務必使用區域網路閘道的現有名稱,以便覆寫目前的設定。 如果您使用不同的名稱,您會建立新的區域網路閘道,而不是覆寫現有閘道。
New-AzLocalNetworkGateway -Name Site1 `
-Location "East US" -AddressPrefix @('10.101.0.0/24','10.101.1.0/24') `
-GatewayIpAddress "5.4.3.2" -ResourceGroupName TestRG1
刪除閘道連線
如果您不知道連線的名稱,可以使用 'Get-AzVirtualNetworkGatewayConnection' Cmdlet 來尋找。
Remove-AzVirtualNetworkGatewayConnection -Name VNet1toSite1 `
-ResourceGroupName TestRG1
下一步
- 一旦完成您的連接,就可以將虛擬機器加入您的虛擬網路。 如需詳細資訊,請參閱虛擬機器。
- 如需 BGP 的相關資訊,請參閱 BGP 概觀和如何設定 BGP。
- 如需使用 Azure Resource Manager 範本建立站對站 VPN 連線的相關資訊,請參閱建立站對站 VPN 連線 (部分機器翻譯)。
- 如需使用 Azure Resource Manager 範本建立 vnet 對 vnet VPN 連線的相關資訊,請參閱部署 HB 異地複寫。