建立 Cloud Discovery 原則
您可以建立應用程式探索原則,使其在偵測到新的應用程式時通知您。 適用於雲端的 Defender Apps 也會搜尋 Cloud Discovery 中的所有記錄,以尋找異常狀況。
建立應用程式探索原則
探索原則可讓您設定警示,在您的組織內偵測到新的應用程式時通知您。
在 Microsoft Defender 入口網站的 [Cloud Apps] 下,移至 [原則 -> 原則管理]。 然後選取 [ 陰影 IT] 索引標籤。
選取 [建立原則 ],然後選取 [ 應用程式探索原則]。
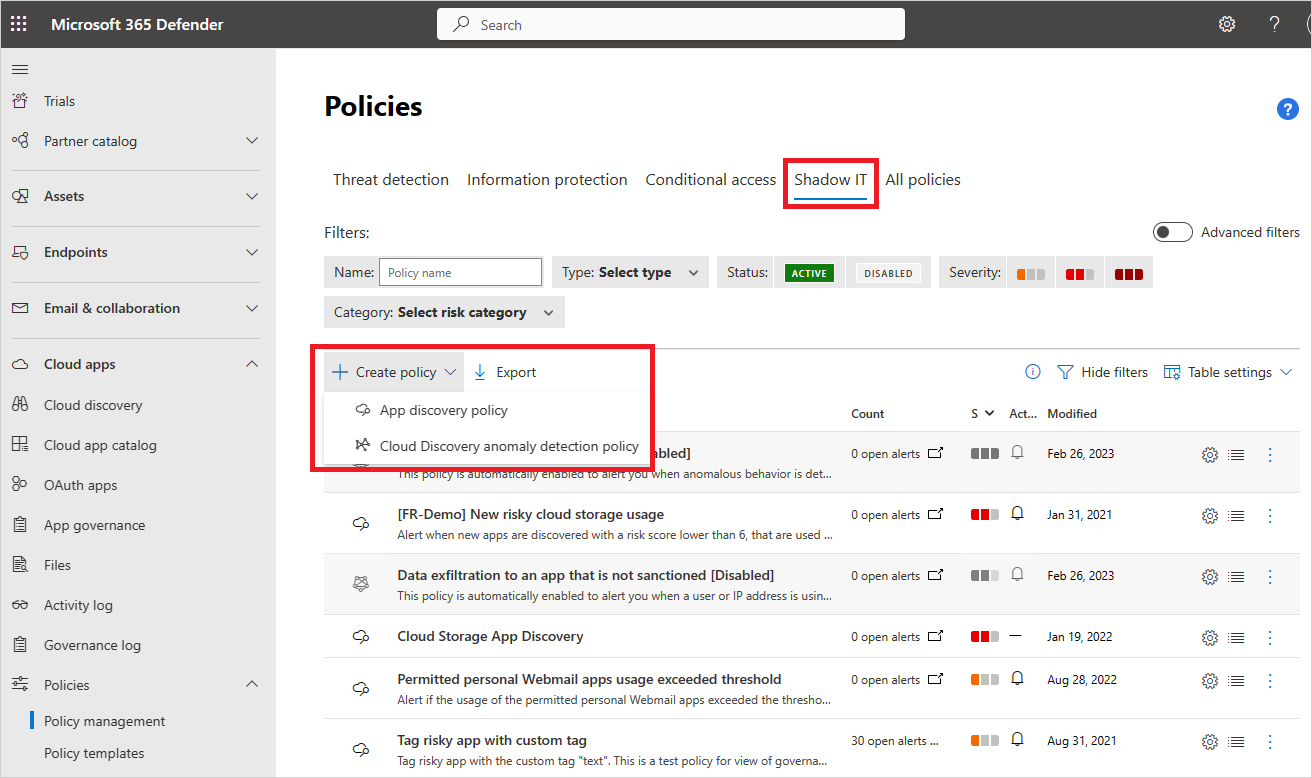
為您的原則提供名稱及描述。 如果您想的話,也可以範本為依據。 有關原則範本的詳細資訊,請參閱<使用原則控制雲端應用程式>。
設定原則的 [嚴重性]。
若要設定有哪些已探索到的應用程式會觸發此原則,請新增篩選。
您可以設定原則敏感度的閾值。 啟用如果下列情況在同一天發生,就觸發原則比對。 您可以設定應用程式每天必須超過的準則來比對原則。 選取下列其中一個準則:
- 每日流量
- 下載的資料
- IP 位址數目
- 交易數目
- 使用者數目
- 上傳的資料
在 [警示] 下設定每日警示限制。 選取警示是否以電子郵件傳送。 然後視需要提供電子郵件位址。
- 選取 [ 儲存警示設定] 作為您組織的 預設值,可讓未來的原則使用設定。
- 如果您有預設的設定,可以選取 [使用組織的預設設定]。
選取在應用程式符合此原則時,要套用的 [治理] 動作。 它可以將原則 標記為已批准、 未經批准、 受監視或自定義標籤。
選取 建立。
注意
- 新建立的探索原則(或具有更新連續報告的原則)會在每個應用程式每連續報告 90 天內觸發一次警示,而不論同一個應用程式是否有現有的警示。 因此,例如,如果您建立原則來探索新的熱門應用程式,它可能會觸發已探索並警示的應用程式的其他警示。
- 快照 報表 中的數據不會在應用程式探索原則中觸發警示。
例如,如果您想要探索雲端環境中具風險的託管應用程式,請依下列方式設定您的原則︰
設定原則篩選以探索託管服務類別中風險分數為 1 的服務,表示這些服務有高風險。
設定閾值,以對在底部找到的某個應用程式觸發警示。 例如,只有在超過 100 位環境中的使用者使用應用程式,而且他們從服務中下載了一定的資料量時,才發出警示。 此外,您可以設定想要接收的每日警示限制。
Cloud Discovery 異常偵測
適用於雲端的 Defender Apps 會搜尋 Cloud Discovery 中的所有記錄,以尋找異常狀況。 例如,有位使用者之前從未使用過 Dropbox,但突然上傳了 600 GB 的資料,或者特定應用程式出現了比平常多很多的交易量。 根據預設,會啟用異常偵測原則。 不需要設定新的原則,異常偵測就會執行。 但您可以在預設原則中,微調您希望收到相關警示的異常類型。
在 Microsoft Defender 入口網站的 [Cloud Apps] 下,移至 [原則 -> 原則管理]。 然後選取 [ 陰影 IT] 索引標籤。
選取 [建立原則 ],然後選取 [ Cloud Discovery 異常偵測原則]。
為您的原則提供名稱及描述。 如果您想的話,也可以範本為依據。如需原則範本的詳細資訊,請參閱使用原則控制雲端應用程式。
若要設定探索到的應用程式觸發此原則,請選取 [ 新增篩選]。
篩選會從下拉式清單中選擇。 若要新增篩選,請選取 [新增篩選]。 若要移除篩選,請選取 『X』。
在 [套用至] 下選擇此原則要套用 [所有連續報告] 或 [特定連續報告]。 選取原則要套用至使用者、IP 位址,或兩者皆是。
在 [只對下列日期以後發生的可疑活動引發警示] 下選取發生異常活動的日期,來觸發警示。
在 [警示] 下設定每日警示限制。 選取警示是否以電子郵件傳送。 然後視需要提供電子郵件位址。
- 選取 [ 儲存警示設定] 作為您組織的 預設值,可讓未來的原則使用設定。
- 如果您有預設的設定,可以選取 [使用組織的預設設定]。
選取 建立。

相關影片
下一步
如果您遇到任何問題,我們會在這裡提供説明。 若要取得產品問題的協助或支援,請 開啟支援票證。