適用於雲端的 Microsoft Defender Apps 中的檔案原則
檔案原則可讓您使用雲端提供者的 API 強制執行各種不同的自動化程式。 設定原則可提供持續的相容性掃描、合法的電子文件探索工作、公開共用敏感性內容的 DLP,以及更多使用案例。 適用於雲端的 Defender 應用程式可以根據 20 個以上的元資料篩選來監視任何檔案類型(例如存取層級、檔案類型)。
如需可套用的檔案篩選清單,請參閱 適用於雲端的 Microsoft Defender Apps 中的檔案篩選。
支援的檔案類型
適用於雲端的 Defender Apps 引擎會從包括 Office、Open Office、壓縮檔、各種 RTF 格式、XML、HTML 等所有通用文件類型中擷取文字來執行內容檢查。
原則
該引擎會合併各原則下的三個層面:
根據預先設定的範本或自訂的運算式進行內容掃描。
內容篩選條件包含使用者角色、檔案中繼資料、共用層級、組織群組整合、共同作業內容,以及額外的可自訂屬性。
控管和補救的自動化動作。
注意
僅保證會套用第一個觸發原則的治理動作。 例如,如果檔案原則已將敏感度標籤套用至檔案,則第二個檔案原則無法將另一個敏感度標籤套用至檔案。
啟用後,原則就會持續掃描您的雲端環境、識別出符合內容和內容篩選的檔案,並套用要求的自動化動作。 這些原則會偵測並修復待用資訊或建立新內容時的任何違規。 您可以使用即時警示或主控台產生的報告來監視原則。
您可以建立的檔案原則範例如下︰
公開共用檔案 - 藉由選取其共用層級為公開的所有檔案,來接收雲端中任何公開共用檔案的警示。
公開共享檔名包含組織的名稱 - 收到包含您組織名稱且公開共用之任何檔案的相關警示。 選取檔案名稱包含貴組織名稱且已公開共用的檔案。
與外部網域共用 - 針對任何與特定外部網域所擁有帳戶共用的檔案接收警示。 例如,與競爭者網域共用的檔案。 選取您要限制共用的外部網域。
隔離上個期間未修改的共用檔案 - 針對近期內無人修改的共用檔案接收警示,以隔離它們或選擇開啟自動化動作。 排除在指定日期範圍內未修改的所有私人檔案。 在 Google Workspace 上,您可以選擇使用原則建立頁面上的 [隔離檔案] 核取方塊來隔離這些檔案。
與未經授權使用者共用 - 針對與您組織中未經授權使用者群組共用的檔案接收通知。 選取未獲授權共用的使用者。
敏感性副檔名 - 針對擁有極可能公開特定副檔名的檔案接收通知。 選取特定的副檔名 (例如 crt,意指憑證) 或檔案名稱,並排除具有私人共用層級的檔案。
注意
您在 適用於雲端的 Defender Apps 中限制為 50 個檔案原則。
建立新的檔案原則
若要建立新的檔案原則,請遵循此程序︰
在 Microsoft Defender 入口網站的 [Cloud Apps] 下,移至 [原則 -> 原則管理]。 選取 [資訊保護] 索引標籤。
選取 [建立原則 ],然後選取 [ 檔案原則]。
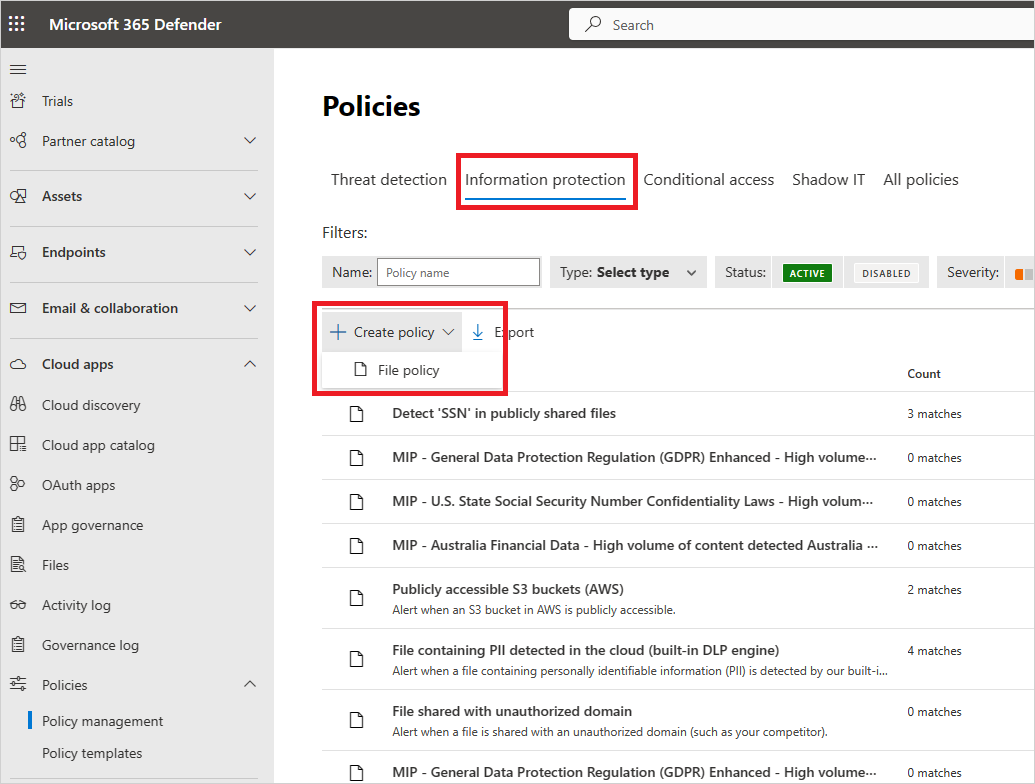
為您的原則命名並描述,如果希望,也可以範本為依據;如需原則範本的詳細資訊,請參閱 Control cloud apps with policies (使用原則控制雲端應用程式)。
設定原則的原則嚴重性。 如果您已設定 Defender for Cloud Apps 針對特定原則重要性層級的原則相符項目向您傳送通知,則此層級會用來決定該原則的相符項目是否觸發通知。
在 [類別] 連結內,將原則連結至最合適的風險類型。 此欄位僅提供資訊,可於稍後協助您依風險類型搜尋特定的原則及警示。 風險可能已根據您選擇用來建立該原則的類別預先選取。 依預設,檔案原則會設為 DLP。
為套用此原則的檔案建立篩選條件,以設定會觸發此原則的探索應用程式。 縮小原則篩選範圍,直到觸及您要處理的一組正確檔案。 請盡量給予限制,以避免誤判。 例如,如果您想要移除公用許可權,請記得新增公用篩選,如果您想要移除外部使用者,請使用 「External」 篩選等等。
注意
使用原則篩選時, Contains 只會搜尋完整單字 ,並以逗號、點、空格或底線分隔。 例如,如果您搜尋 malware 或 virus,會找到 virus_malware_file.exe,但不會找到 malwarevirusfile.exe。 如果您搜尋 malware.exe,則您會在其檔名中找到所有含有惡意代碼或 exe 的檔案,而如果您 搜尋 “malware.exe” (加上引號),則只會找到只包含 “malware.exe” 的檔案。 Equals 僅會搜尋完整字串。例如,如果您搜尋 malware.exe,會找到 malware.exe,但不會找到 malware.exe.txt。
如需檔案原則篩選的詳細資訊,請參閱 適用於雲端的 Microsoft Defender Apps 中的檔案篩選。
在第一個 [套用至篩選] 底下,針對 Box、SharePoint、Dropbox 或 OneDrive,選取排除所選資料夾或選取資料夾的所有檔案,您可以在其中針對應用程式或特定資料夾的所有檔案強制執行檔案原則。 系統已將您重新導向以登入雲端應用程式,然後新增相關的資料夾。
在第二個 [套用到] 篩選下,選取 [所有檔案擁有者]、[所選使用者群組中的檔案擁有者] 或 [除了所選群組之外的所有檔案擁有者]。 然後選取相關的使用者群組,以決定哪些使用者和群組應包含在該原則中。
選取 [內容檢查方法]。 您可選取 [內建 DLP] 或 [資料分類服務]。 建議您使用 [資料分類服務]。
啟用內容檢查後,您就可以選擇使用預設運算式或尋找其他自訂運算式。
此外,您也可以指定規則運算式,從結果中排除檔案。 如果您想要從原則中排除內部分類關鍵字標準,這個選項會非常實用。
您可以決定設定要至少比對到多少次內容違規數,才將該檔案視為違規。 例如,如果您想要收到在內容中找到至少 10 個信用卡號碼之檔案的警示,您可以選擇 10。
當內容與選取的運算式相符時,違規文字會以「X」字元取代。 根據預設,違規部分會被屏蔽並呈現在內容中,該部分的前後 100 個字元會顯示出來。 運算式內容中的數字會以「#」字元取代,而且絕不會儲存在 Defender for Cloud Apps 中。 您可以選取 [將違規的最後 4 個字元取消遮罩] 選項,將違規本身的最後 4 個字元取消遮罩。 您必須設定規則運算式要搜尋的資料類型:內容、中繼資料和/或檔案名稱。 根據預設,它會搜尋內容和中繼資料。
選擇偵測到相符專案時,您想要 適用於雲端的 Defender 應用程式採取的治理動作。
建立原則之後,您可以篩選 [檔案原則 類型] 來檢視它。 您可以隨時編輯原則、校正其篩選或變更自動化動作。 原則建立後便會自動啟用,並開始掃描您的雲端檔案。 在設定治理動作時務必特別小心,否則可能會導致檔案存取權限無法回復的損失。 建議使用多個搜尋欄位,以便將篩選條件精簡為可確切代表要套用原則的檔案。 篩選範圍越窄越好。 如需指引,您可以使用篩選條件旁的 [編輯和預覽結果 ] 按鈕。
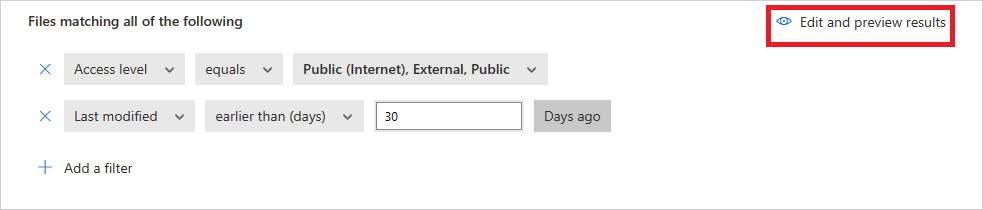
若要檢視檔案原則相符專案,可疑違反原則的檔案,請移至原則 ->原則管理。 使用頂端的 [類型] 篩選器,將結果篩選為僅顯示檔案原則。 如需每個原則相符項目的詳細資訊,請在 [ 計數 ] 數據行底下,選取原則的 相符 項目數目。 或者,針對原則選取數據列結尾的三個點,然後選擇 [ 檢視所有相符專案]。 這會開啟 [ 檔案原則] 報告。 選取 [ 立即 比對] 索引卷標,以查看目前符合原則的檔案。 選取 [歷程記錄] 索引標籤,以查看最多六個月符合原則的檔案記錄。
檔案原則最佳做法
請避免在生產環境中重設檔案原則 (使用 重設結果並再次 套用動作] 複選框),除非這是絕對必要的,因為這樣做會起始原則所涵蓋檔案的完整掃描,這可能會對其效能產生負面影響。
將捲標套用至特定父資料夾 及其 子資料夾中的檔案時,請使用 [ 套用至 ->Selected 資料夾 ] 選項。 然後新增每個父資料夾。
僅將卷標套用至特定資料夾中的檔案時(不包括任何子資料夾),請使用檔案原則篩選具有 Equals 運算子的父資料夾。
使用窄篩選準則時,檔案原則會更快(相較於寬準則)。
將相同服務的數個檔案原則(例如 SharePoint、OneDrive、Box 等)合併至單一原則。
啟用檔案監視時(從 [設定] 頁面,請建立至少一個檔案原則。 當沒有任何檔案原則存在,或連續七天停用檔案監視時,就會自動存取檔案監視。
檔案原則參考
本節提供原則的參考詳細資訊,並說明每種原則類型和您可以針對每項原則設定的欄位。
[檔案原則] 是一種 API 型原則,可讓您將 20 多項檔案中繼資料篩選 (包括擁有者和共用層級) 與內容檢查結果納入考量,藉此控制雲端中的組織內容。 您可以根據原則結果,套用治理動作。 內容檢查引擎可以透過第三方 DLP 引擎和反惡意程式碼解決方案來擴充。
每個原則皆由下列部分組成:
檔案篩選 - 讓您可以根據中繼資料建立細微條件。
內容檢查 - 讓您可以根據 DLP 引擎結果縮小原則。 您可以納入自訂運算式或預設運算式。 也可以設定排除項目,以及選擇相符項目數。 您也可以使用匿名為使用者名稱加上遮罩。
動作 - 此原則提供一組可在找到違規時自動套用的治理動作。 這些動作分成共同作業動作、安全性動作和調查動作。
延伸模組 - 您可透過協力廠商引擎來執行內容檢查,以取得改善的 DLP 或反惡意程式碼功能。
檔案查詢
為更簡化調查,您現在可以建立自訂的查詢,並儲存以供日後使用。
在 [ 檔案] 頁面中,使用先前所述的篩選條件,視需要向下切入您的應用程式。
建置好查詢之後,請選取篩選上方的 [ 另存新檔] 按鈕。
在 [ 儲存查詢] 彈出視窗中,為您的查詢命名。
日後若要再次使用這項查詢,請在 [查詢] 下向下捲動至 [儲存查詢],並選取您的查詢。
檢視檔案原則結果
您可以移至原則中心以檢閱檔案原則違規。
在 Microsoft Defender 入口網站的 [Cloud Apps] 下,移至 [原則 -> 原則管理],然後選取 [信息保護] 索引標籤。
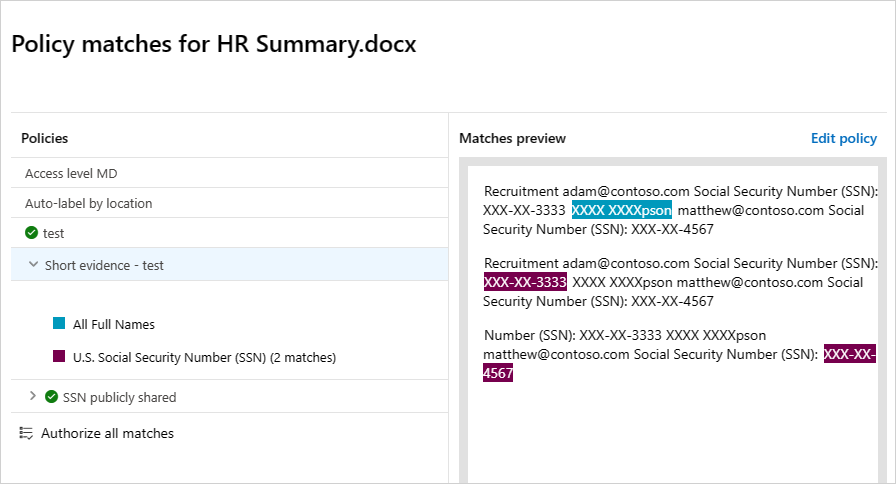
針對每個檔案原則,您可以選取 相符專案來查看檔案原則違規。
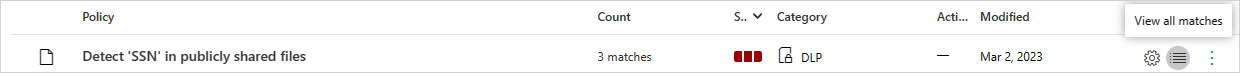
您可以選取檔案本身以取得檔案的相關資訊。
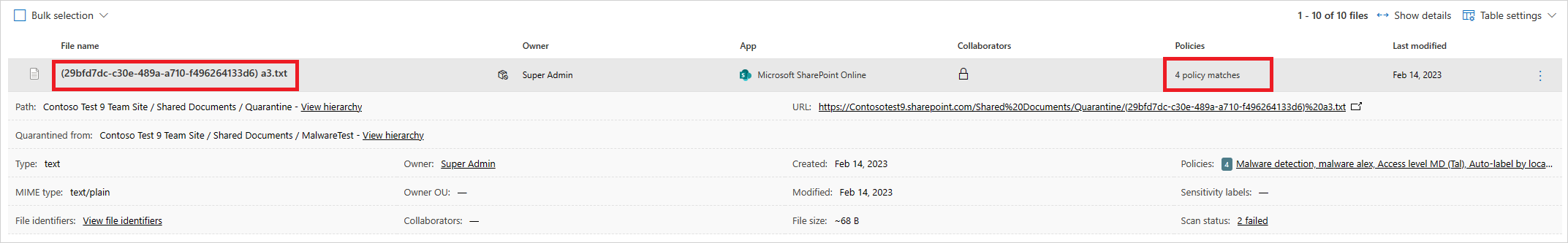
例如,您可以選取 [共同作業者 ] 來查看誰可以存取此檔案,而且您可以選取 [相符專案 ] 以查看 [社會安全號碼]。
相關影片
下一步
如果您遇到任何問題,我們會在這裡提供説明。 若要取得產品問題的協助或支援,請 開啟支援票證。