適用於雲端的 Defender Apps 如何協助保護您的 Google Cloud Platform (GCP) 環境
Google Cloud Platform 是 IaaS 提供者,可讓您的組織在雲端中裝載和管理其整個工作負載。 除了利用雲端基礎結構的優點外,貴組織最重要的資產可能會暴露在威脅面前。 公開的資產包括具有潛在敏感性資訊的記憶體實例、計算資源,這些資源會操作您一些最重要的應用程式、埠和虛擬專用網,以存取您的組織。
連線 GCP 來 適用於雲端的 Defender Apps 可協助您保護您的資產,並藉由監視系統管理與登入活動、通知可能的暴力密碼破解攻擊、惡意使用特殊許可權用戶帳戶,以及異常刪除 VM 來偵測潛在威脅。
主要威脅
- 濫用雲端資源
- 遭入侵的帳戶和內部威脅
- 數據外洩
- 資源設定錯誤和訪問控制不足
適用於雲端的 Defender 應用程式如何協助保護您的環境
使用內建原則和原則範本控制 GCP
您可以使用下列內建原則範本來偵測並通知您潛在威脅:
| 類型 | 名稱 |
|---|---|
| 內建異常偵測原則 | 匿名 IP 位址的活動 非經常性國家/地區的活動 可疑 IP 位址的活動 不可能的移動 由終止使用者 執行的活動(需要 Microsoft Entra ID 作為 IdP) 多次失敗的登入嘗試 不尋常的系統管理活動 多次 VM 刪除活動 不尋常的多個 VM 建立活動 (預覽) |
| 活動原則範本 | 計算引擎資源的變更 StackDriver 設定的變更 記憶體資源的變更 虛擬專用網的變更 從有風險的 IP 位址登入 |
如需建立原則的詳細資訊,請參閱 建立原則。
自動化治理控制件
除了監視潛在威脅之外,您還可以套用並自動化下列 GCP 治理動作來補救偵測到的威脅:
| 類型 | 動作 |
|---|---|
| 使用者治理 | - 要求使用者將密碼重設為 Google(需要已連線連結的 Google Workspace 實例) - 暫停使用者(需要已連結的 Google Workspace 實例) - 透過 Microsoft Entra ID 通知使用者警示 - 要求使用者再次登入 (透過 Microsoft Entra ID) - 暫停使用者 (透過 Microsoft Entra ID) |
如需從應用程式補救威脅的詳細資訊,請參閱 治理已連線的應用程式。
實時保護 GCP
檢閱我們的最佳做法,以 保護與外部使用者 共同作業,並 封鎖和保護敏感數據下載至非受控或具風險的裝置。
連線 Google Cloud Platform 適用於雲端的 Microsoft Defender Apps
本節提供使用連接器 API 將 適用於雲端的 Microsoft Defender Apps 連線到現有 Google Cloud Platform (GCP) 帳戶的指示。 此連線可讓您檢視及控制 GCP 的使用。 如需 適用於雲端的 Defender 應用程式如何保護 GCP 的資訊,請參閱保護 GCP。
建議您使用專用專案進行整合,並限制對專案的存取,以維持穩定的整合,並防止刪除/修改安裝程式。
注意
線上 GCP 環境以進行稽核的指示遵循 Google 針對取用匯總記錄的建議 。 整合會利用Google StackDriver,並取用可能會影響帳單的其他資源。 耗用的資源如下:
適用於雲端的 Defender Apps 稽核連線只會匯入 管理員 活動稽核記錄;不會匯入數據存取和系統事件稽核記錄。 如需 GCP 記錄的詳細資訊,請參閱 雲端稽核記錄。
必要條件
整合 GCP 使用者必須具有下列權限:
- IAM 和 管理員 編輯 – 組織層級
- 專案建立和編輯
您可以將 GCP 安全性稽核連線連線至 適用於雲端的 Defender Apps 連線,以深入瞭解及控制 GCP 應用程式使用。
設定Google Cloud Platform
建立專用專案
在您的組織下於 GCP 中建立專用專案,以啟用整合隔離和穩定性
使用整合 GCP 使用者帳戶登入 GCP 入口網站。
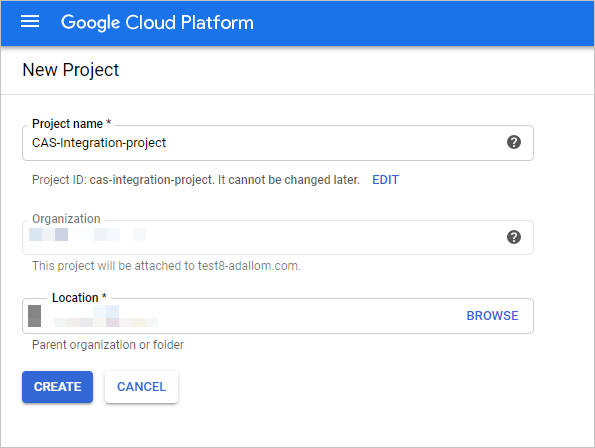
選取 [建立專案 ] 以啟動新的專案。
在 [ 新增專案] 畫面中,為您的專案 命名,然後選取 [ 建立]。
啟用必要的 API
切換至專用專案。
移至 [連結 庫] 索引標籤 。
搜尋並選取 [雲端記錄 API],然後在 [API] 頁面上,選取 [ 啟用]。
搜尋並選取 [Cloud Pub/Sub API],然後在 [API] 頁面上,選取 [ 啟用]。
注意
請確定您未選取 [發佈/子精簡版 API]。
建立安全性稽核整合的專用服務帳戶
在 [IAM 與系統管理員] 下,選取 [服務帳戶]。
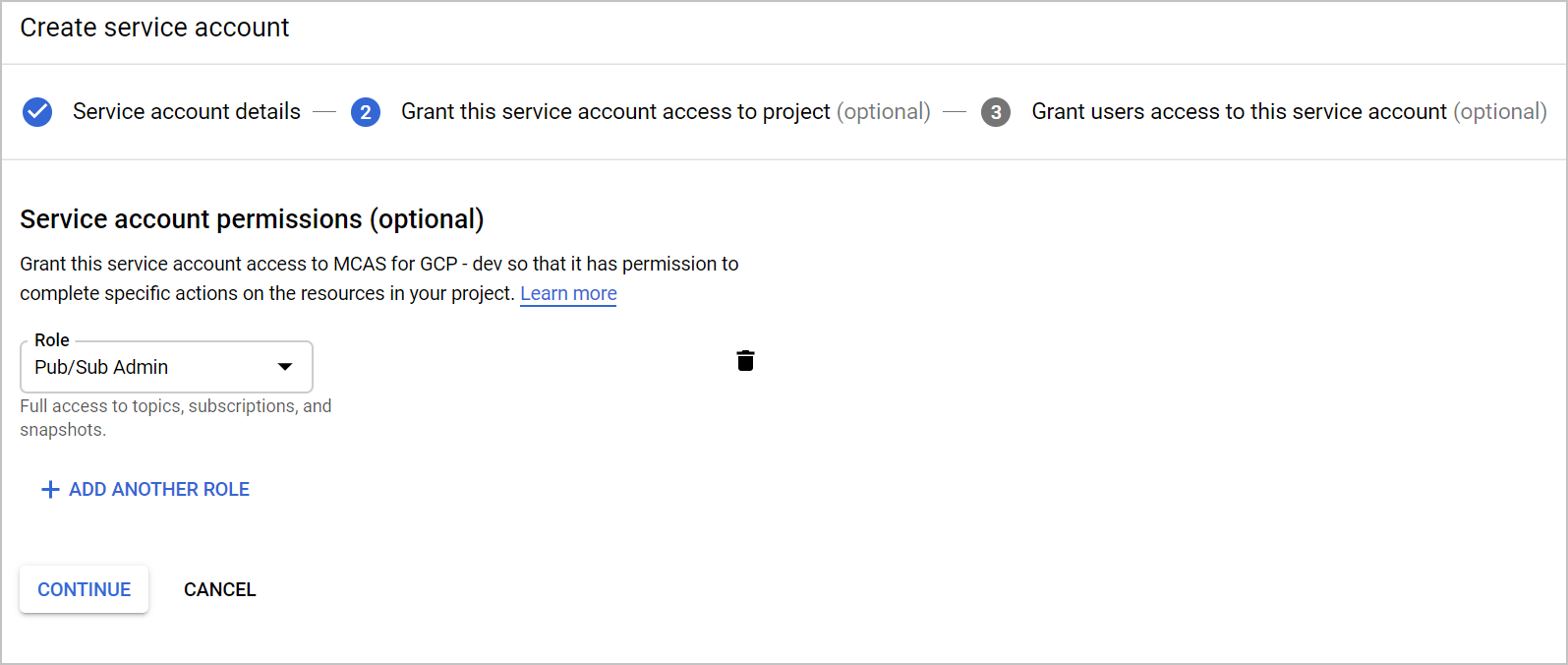
選取 [建立服務帳戶 ] 以建立專用的服務帳戶。
輸入帳戶名稱,然後選取 [ 建立]。
將角色指定為 Pub/Sub 管理員,然後選取 [儲存]。
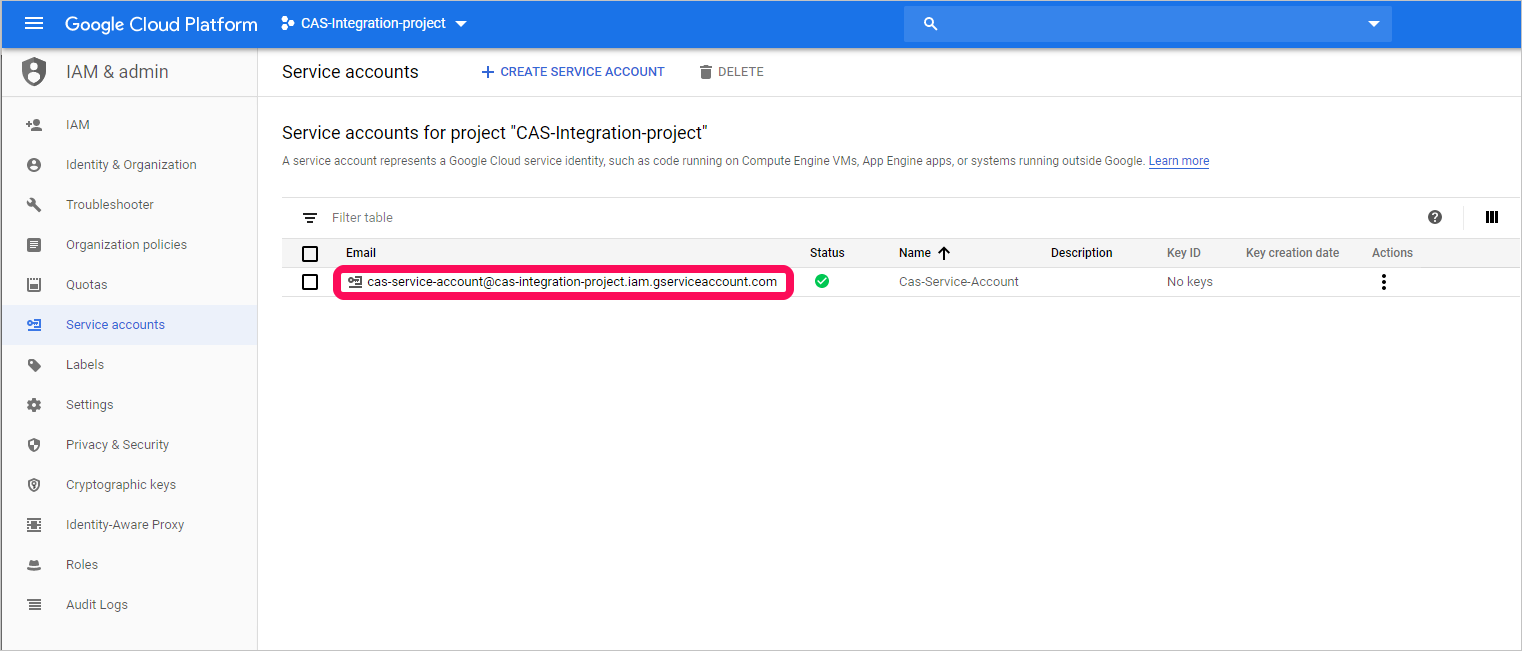
複製 [ 電子郵件 ] 值,稍後您將需要此值。
在 [IAM 和系統管理員] 下,選取 [IAM]。
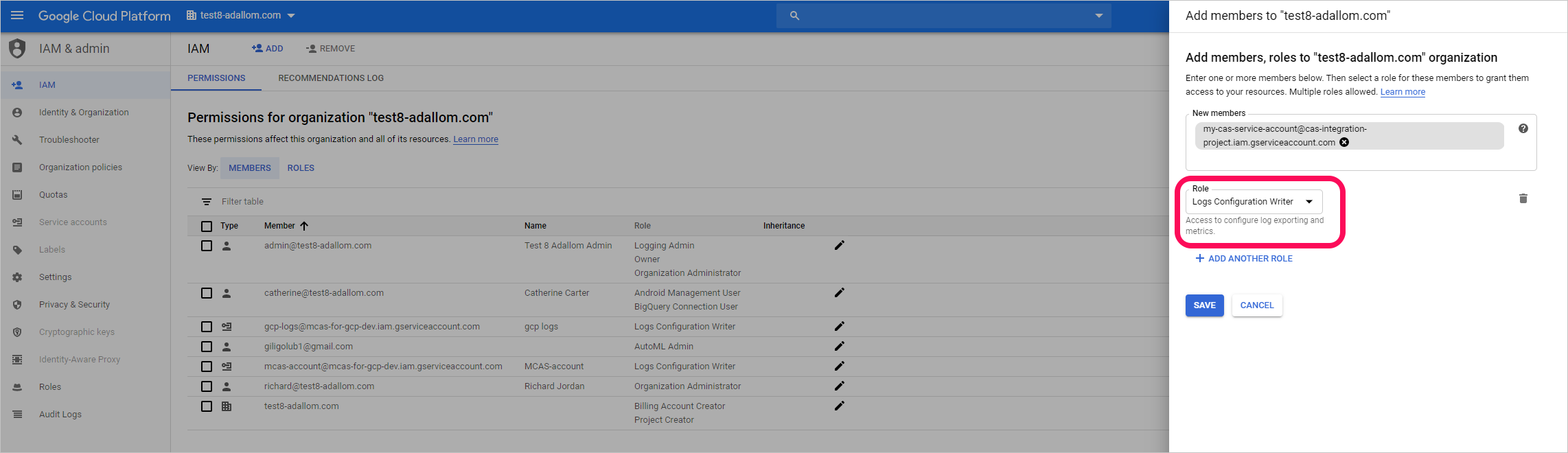
切換至組織層級。
選取 [ADD] (新增)。
在 [新增成員] 方塊中,貼上您稍早複製的電子郵件值。
將角色指定為記錄設定寫入器,然後選取 [儲存]。
建立專用服務帳戶的私密金鑰
切換至專案層級。
在 [IAM 與系統管理員] 下,選取 [服務帳戶]。
開啟專用服務帳戶,然後選取 [編輯]。
選取 [ 建立金鑰]。
在 [建立私鑰] 畫面中,選取 [JSON],然後選取 [建立]。
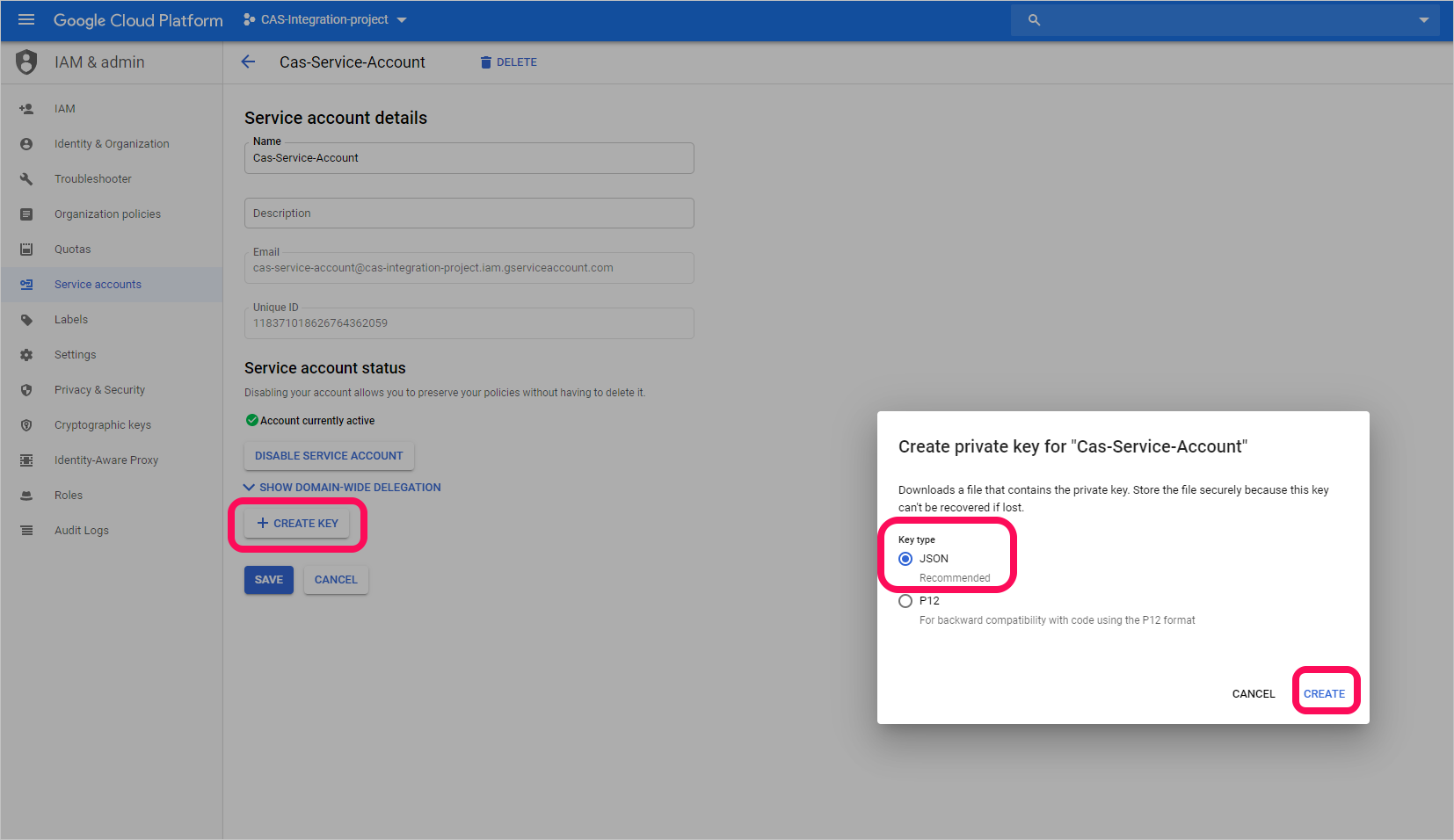
注意
您稍後需要下載到裝置的 JSON 檔案。
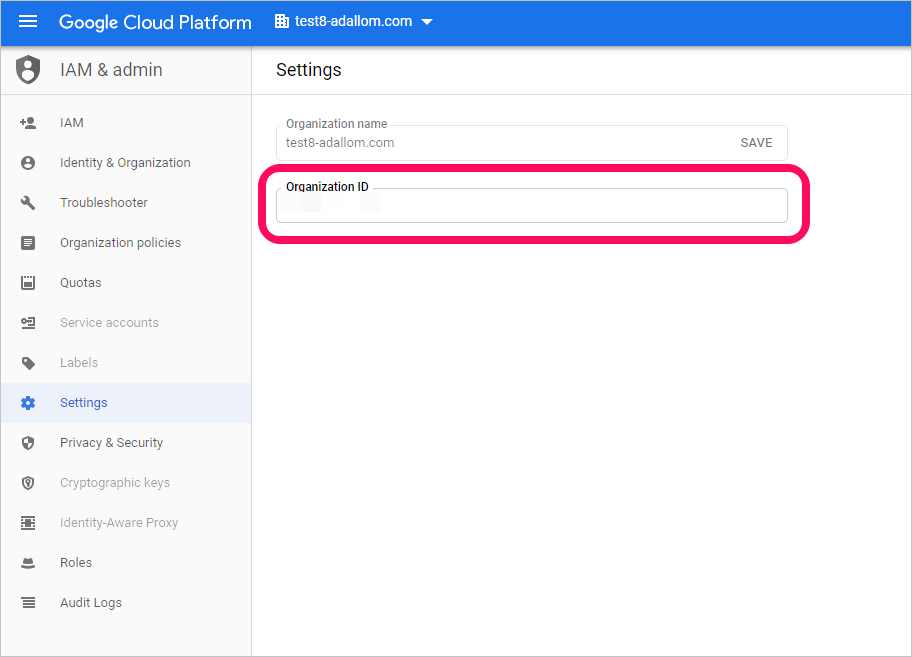
擷取您的組織標識碼
記下您的 組織識別碼,稍後您將需要此標識碼。 如需詳細資訊,請參閱 取得您的組織標識符。
連線 Google Cloud Platform 稽核至 適用於雲端的 Defender Apps
此程序說明如何新增 GCP 連線詳細數據,以將 Google Cloud Platform 稽核連線至 適用於雲端的 Defender Apps。
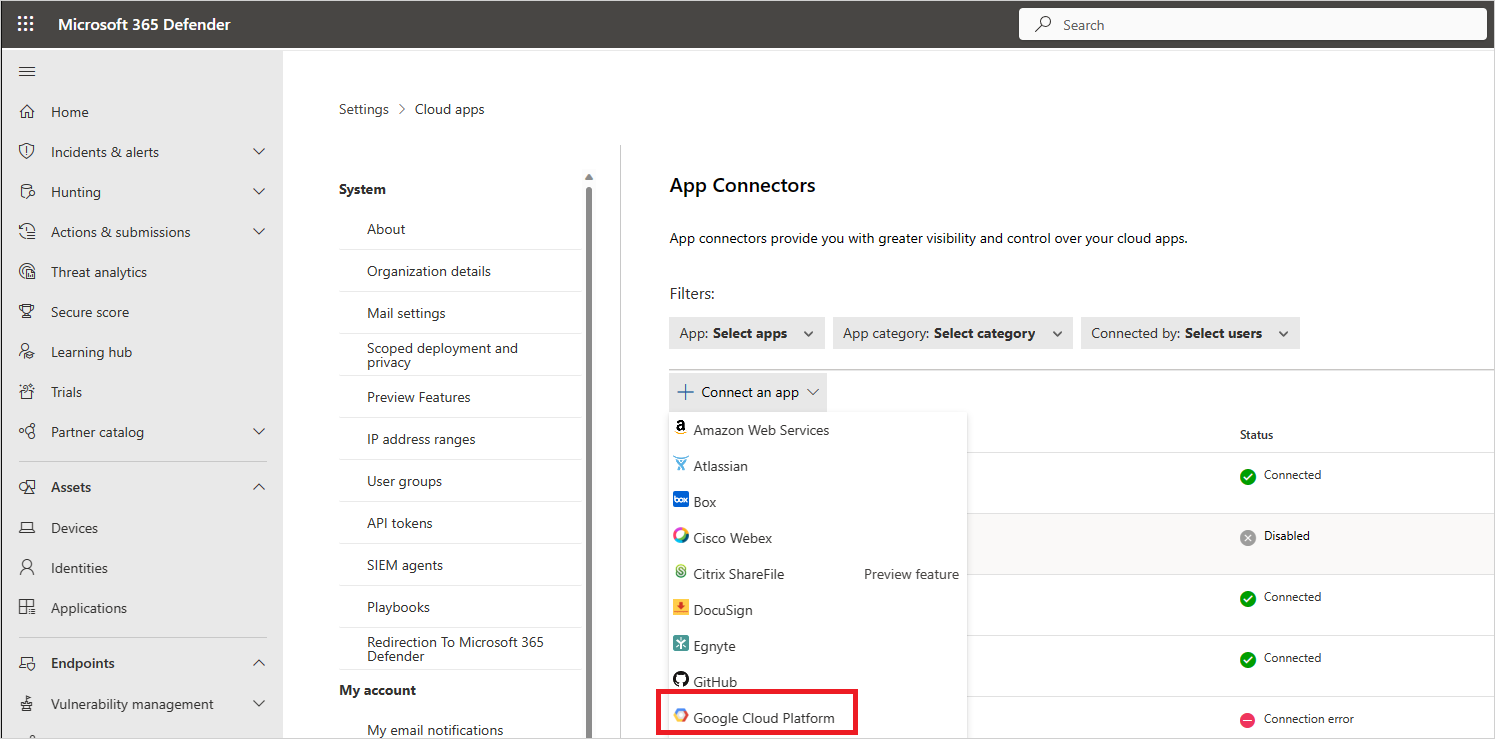
在 Microsoft Defender 入口網站中,選取 [設定]。 然後選擇 [ 雲端應用程式]。 在 [連線 應用程式] 底下,選取 [應用程式 連線 者]。
在 [應用程式連線程式] 頁面中,若要提供 GCP 連接器認證,請執行下列其中一項:
注意
建議您連線 Google Workspace 實例,以取得統一的使用者管理和控管。 即使您未使用任何 Google Workspace 產品,而且 GCP 使用者是透過 Google Workspace 使用者管理系統管理,也是建議的。
針對新的連接器
選取 [+連線 應用程式,後面接著Google Cloud Platform。
在下一個視窗中,提供連接器的名稱,然後選取 [ 下一步]。
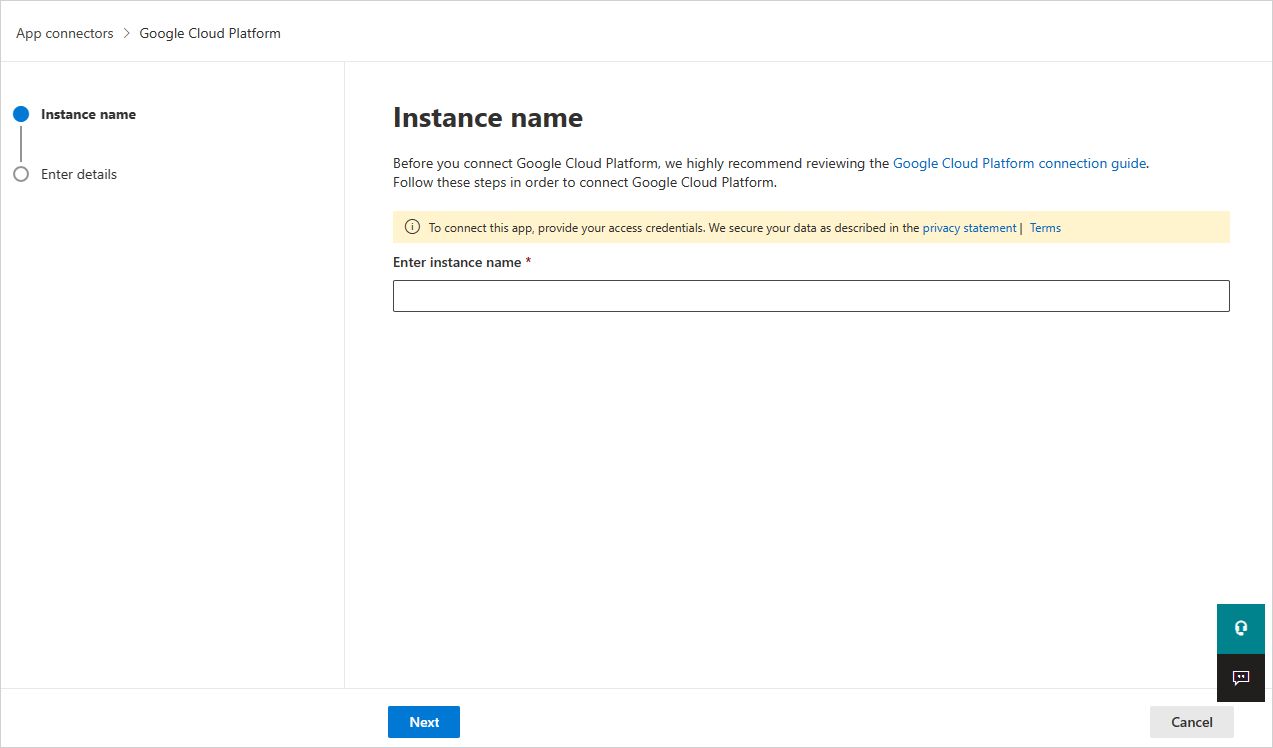
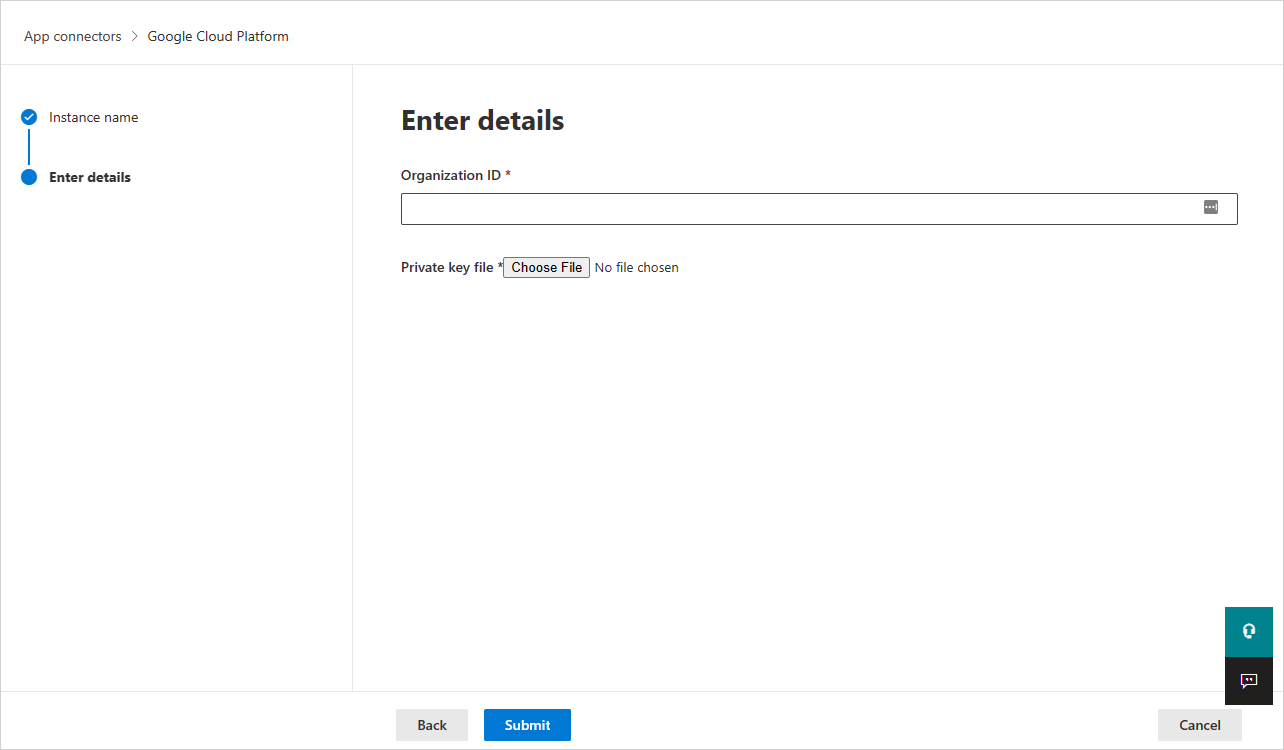
在 [ 輸入詳細數據] 頁面中,執行下列動作,然後選取 [ 提交]。
- 在 [ 組織標識符 ] 方塊中,輸入您稍早記下的組織。
- 在 [ 私鑰檔案 ] 方塊中,流覽至您稍早下載的 JSON 檔案。
針對現有的連接器
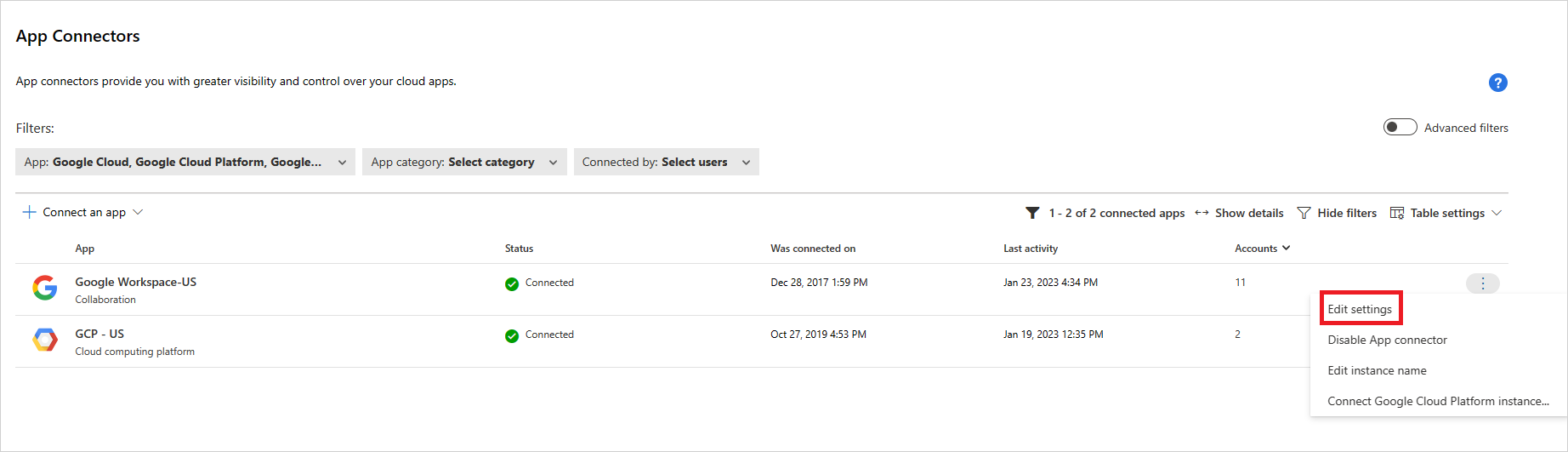
在連接器清單中,於 GCP 連接器出現的數據列上,選取 [ 編輯設定]。
在 [ 輸入詳細數據] 頁面中,執行下列動作,然後選取 [ 提交]。
- 在 [ 組織標識符 ] 方塊中,輸入您稍早記下的組織。
- 在 [ 私鑰檔案 ] 方塊中,流覽至您稍早下載的 JSON 檔案。

在 Microsoft Defender 入口網站中,選取 [設定]。 然後選擇 [ 雲端應用程式]。 在 連線 的應用程式下,選取 [應用程式 連線 者]。 請確定已連線的應用程式 連線 or 的狀態已 連線。
注意
適用於雲端的 Defender Apps 會使用整合專案中的整合服務帳戶,建立匯總的導出接收(組織層級)、Pub/Sub 主題和 Pub/Sub 訂用帳戶。
匯總導出接收可用來匯總 GCP 組織之間的記錄,而建立的 Pub/Sub 主題會當做目的地使用。 適用於雲端的 Defender Apps 會透過建立的 Pub/Sub 訂用帳戶訂閱來訂閱本主題,以擷取 GCP 組織中的系統管理活動記錄。
如果您在連線應用程式時發生任何問題,請參閱針對應用程式 連線 器進行疑難解答。
下一步
如果您遇到任何問題,我們會在這裡提供説明。 若要取得產品問題的協助或支援,請 開啟支援票證。