搭配 Intune 設定及使用 PKCS 憑證
Microsoft Intune 支援使用私鑰和公鑰組 (PKCS) 憑證。 本文會檢閱搭配 Intune 使用 PKCS 憑證所需的專案,包括匯出 PKCS 憑證,然後將其新增至 Intune 裝置組態配置檔。
Microsoft Intune 包含內建設定,可使用 PKCS 憑證來存取和驗證您的組織資源。 憑證會驗證並保護您公司資源的存取,例如 VPN 或 WiFi 網路。 您可以使用 Intune 中的裝置組態設定檔,將這些設定部署到裝置。
如需使用已匯入 PKCS 憑證的資訊,請參閱 匯入的 PFX 憑證。
提示
Windows Enterprise 多重會話遠端桌面支援 PKCS 憑證配置檔。
需求
若要搭配 Intune 使用 PKCS 憑證,您需要下列基礎結構:
Active Directory 網域:
本節中列出的所有伺服器都必須加入您的 Active Directory 網域。如需安裝和設定 #D09F804DC57014B4EA330148513C544EA (AD DS) 的詳細資訊,請參閱 AD DS 設計與規劃。
憑證頒發機構單位:
企業證書頒發機構單位 (CA) 。如需安裝和設定 Active Directory 憑證服務 (AD CS) 的詳細資訊,請參閱 Active Directory 憑證服務逐步指南。
警告
Intune 會要求您使用企業證書頒發機構單位來執行 AD CS (CA) ,而不是獨立 CA。
用戶端:
聯機到企業CA。跟憑證:
從企業 CA 導出的跟證書複本。適用於 Microsoft Intune 的憑證連接器:
如需憑證連接器的相關信息,請參閱:
從企業 CA 匯出跟證書
若要使用 VPN、WiFi 或其他資源來驗證裝置,裝置需要根或中繼 CA 憑證。 下列步驟說明如何從您的企業 CA 取得必要的憑證。
使用命令列:
使用系統管理員帳戶登入跟證書授權單位伺服器。
移至 [開始>執行],然後輸入 Cmd 以開啟命令提示字元。
指定 certutil -ca.cert ca_name.cer 將跟證書匯出為名為 ca_name.cer 的檔案。
在 CA 上設定證書範本
使用具有系統管理許可權的帳戶登入您的企業CA。
開啟 [ 證書頒發機構單位 ] 控制台,以滑鼠右鍵按兩下 [ 證書範本],然後選取 [ 管理]。
尋找 [使用者 ] 證書範本,以滑鼠右鍵按兩下它,然後選擇 [ 複製範本 ] 以開啟 [新範本的屬性]。
注意事項
針對 S/MIME 電子郵件簽署和加密案例,許多系統管理員會使用個別的憑證來簽署和加密。 如果您使用 Microsoft Active Directory 憑證服務,則可以使用 僅限 Exchange 簽章 範本進行 S/MIME 電子郵件簽署憑證,以及 使用 Exchange 使用者 範本進行 S/MIME 加密憑證。 如果您使用第三方證書頒發機構單位,建議您檢閱其設定簽署和加密範本的指引。
在 [ 兼容性] 索 引標籤上:
- 將 證書頒發機構單位 設定為 Windows Server 2008 R2
- 將 憑證收件者 設定為 Windows 7 / Server 2008 R2
在 [ 一般] 索引 標籤上:
- 將 [範本顯示名稱] 設定為對您有意義的名稱。
- 取消核取 [ 在 Active Directory 中發佈憑證]。
警告
根據預設,範本名稱與沒有空格的範本顯示名稱相同。 請記下範本名稱,稍後需要它。
在 [要求處理] 中,選取 [ 允許匯出私鑰]。
注意事項
不同於 SCEP,使用 PKCS 時,憑證私鑰會在安裝憑證連接器的伺服器上產生,而不是在裝置上產生。 證書範本必須允許匯出私鑰,連接器才能匯出 PFX 憑證,並將它傳送至裝置。
當憑證安裝在裝置本身時,私鑰會標示為無法匯出。
在 [密碼編譯] 中,確認 [金鑰大小下限 ] 設定為 2048。
Windows 和 Android 裝置支援使用 4096 位密鑰大小搭配 PKCS 憑證配置檔。 若要使用此金鑰大小,請將 4096 指定為 [金鑰大小下限]。
注意事項
針對 Windows 裝置,只有軟體 金鑰儲存提供者 (KSP) 才支援 4096 位金鑰記憶體。 下列項目不支援儲存此大小的金鑰:
- 硬體 TPM (信賴平臺模組) 。 因應措施是使用軟體 KSP 來儲存金鑰。
- Windows Hello 企業版。 目前沒有 Windows Hello 企業版的因應措施。
在 [ 主體名稱] 中,選擇 [在要求中提供]。
在 [擴充功能] 中,確認您在 [應用程式原則] 下看到 [加密檔案系統]、[安全 Email] 和 [用戶端驗證]。
重要事項
針對 iOS/iPadOS 證書範本,請移至 [ 延伸 模組] 索引標籤,更新 [金鑰使用方式],並確認未選取 [簽章是原始證明 ]。
在 [安全性] 中:
- (必要) :為您安裝適用於 Microsoft Intune 的憑證連接器的伺服器新增電腦帳戶。 允許此帳戶 的讀 取和 註冊 許可權。
- (選擇性但建議的) :選取 [網域使用者] 群組,然後選取 [移除],從此範本上允許的群組或使用者名稱清單中移除 [網域使用者] 群組。 檢閱 群組或用戶名稱 中的其他專案,以取得環境的許可權和適用性。
選 取 [套用>確定] 以儲存證書範本。 關閉證書 範本主控台。
在 [證書頒發機構單位] 控制台中,以滑鼠右鍵按兩下 [要發出的證書範>本] [新增>證書範本]。 選擇您在先前步驟中建立的範本。 選取 [確定]。
若要讓伺服器管理已註冊裝置和用戶的憑證,請使用下列步驟:
- 以滑鼠右鍵按兩下 [證書頒發機構單位],選擇 [ 屬性]。
- 在 [安全性] 索引標籤上,新增您執行連接器之伺服器的電腦帳戶。
- 授 與發行和管理憑證 和 要求憑證 允許計算機帳戶的許可權。
註銷企業 CA。
下載、安裝及設定適用於 Microsoft Intune的憑證連接器
如需指引,請參閱安裝和設定適用於 Microsoft Intune 的憑證連接器。
建立受信任的憑證配置檔
選取並移至 [ 裝置>設定>建立]。
輸入下列內容:
- 平台:選擇將接收此配置檔之裝置的平臺。
- Android 裝置系統管理員
- Android Enterprise:
- 完全受控
- 專用
- Corporate-Owned 工作配置檔
- Personally-Owned 工作配置檔
- iOS/iPadOS
- macOS
- Windows 10/11
- 配置檔:選取 [信任的憑證]。 或者,選取 [範本信任的>憑證]。
- 平台:選擇將接收此配置檔之裝置的平臺。
選取 [建立]。
在 [基本資訊] 中,輸入下列內容:
- 名稱:輸入設定檔的描述性名稱。 為您的配置檔命名,以便稍後輕鬆地識別它們。 例如,良好的配置檔名稱是 整個公司的受信任憑證配置檔。
- 描述:輸入設定檔的描述。 這是選擇性設定,但建議進行。
選取[下一步]。
在 [ 組態設定] 中,針對您先前導出的根 CA 憑證指定.cer檔。
注意事項
視您在 步驟 3 中選擇的平臺而定,您也可以選擇憑證的 目的地存放 區。
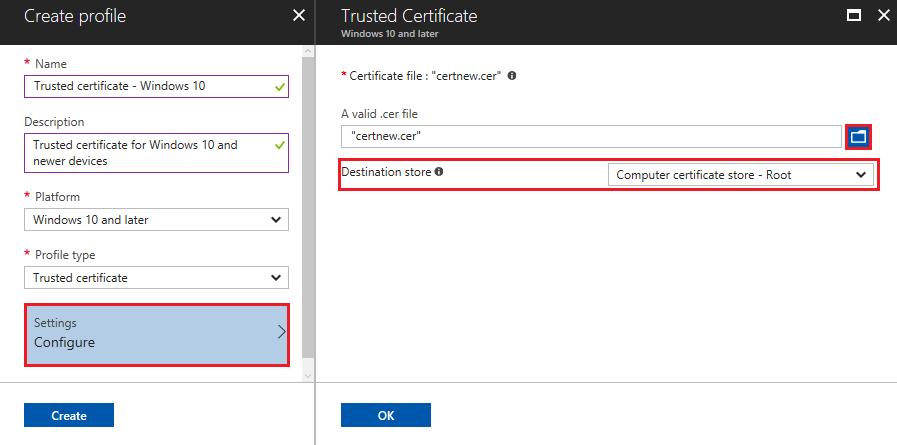
選取 [下一步]。
在 [ 指派] 中,選取要指派配置檔的使用者或裝置群組 () 。 如需更細微的詳細資訊,請參閱在 Microsoft Intune 中建立篩選,並選取 [編輯篩選] 加以套用。
規劃將此憑證配置檔部署到接收 PKCS 憑證配置檔的相同群組,以及接收組態配置檔的相同群組,例如使用憑證的 Wi-Fi 配置檔。 如需指派設定檔的詳細資訊,請參閱指派使用者和裝置設定檔。
選取[下一步]。
(僅適用於 Windows 10/11) 在適用性規則中,指定適用性規則以精簡此配置檔的指派。 您可以選擇根據 OS 版本或裝置版本來指派或不指派設定檔。
如需詳細資訊,請參閱在 Microsoft Intune 中建立裝置配置檔中的適用性規則。
在 [檢閱 + 建立] 中,檢閱您的設定。 當您選取 [建立] 時,系統會儲存您的變更,然後指派設定檔。 原則也會顯示在設定檔清單中。
建立 PKCS 憑證配置檔
重要事項
Microsoft Intune 於 2024 年 8 月 30 日終止對可存取 Google 行動服務 (GMS) 之裝置上的 Android 裝置系統管理員管理支援。 在該日期之後,裝置註冊、技術支援、錯誤修正和安全性修正將無法使用。 如果您目前使用裝置系統管理員管理,建議您在支持結束之前,先切換至 Intune 中的另一個 Android 管理選項。 如需詳細資訊,請參閱 終止 GMS 裝置上的 Android 裝置系統管理員支援。
選取並移至 [ 裝置>設定>建立]。
輸入下列內容:
- 平台:選擇裝置的平臺。 選項包括:
- Android 裝置系統管理員
- Android Enterprise:
- 完全受控
- 專用
- Corporate-Owned 工作配置檔
- Personally-Owned 工作配置檔
- iOS/iPadOS
- macOS
- Windows 10/11
- 配置檔:選取 [PKCS 憑證]。 或者,選取 [範本>PKCS 憑證]。
注意事項
在具有 Android Enterprise 設定檔的裝置上,使用 PKCS 憑證設定檔安裝的憑證不會顯示在裝置上。 若要確認憑證部署成功,請在 Intune 系統管理中心檢查配置檔的狀態。
- 平台:選擇裝置的平臺。 選項包括:
選取 [建立]。
在 [基本資訊] 中,輸入下列內容:
- 名稱:輸入設定檔的描述性名稱。 為您的配置檔命名,以便稍後輕鬆地識別它們。 例如,良好的配置檔名稱是 整家公司的 PKCS 配置檔。
- 描述:輸入設定檔的描述。 這是選擇性設定,但建議進行。
選取[下一步]。
在 [組態設定] 中,視您選擇的平臺而定,您可以設定的設定會不同。 選取您的平臺以取得詳細設定:
- Android 裝置系統管理員
- Android Enterprise
- iOS/iPadOS
- Windows 10/11
設定 平台 詳細資料 更新閾值 (%) - 全部
建議為 20% 憑證有效期間 - 全部
如果您未變更證書範本,此選項可能會設定為一年。
使用5天或最多24個月的有效期間。 當有效期間小於五天時,憑證極有可能進入接近到期或過期狀態,這可能會導致裝置上的 MDM 代理程式在安裝憑證之前拒絕該憑證。金鑰儲存提供者 (KSP) - Windows 10/11
針對 Windows,選取要在裝置上儲存金鑰的位置。 證書頒發機構單位 - 全部
顯示企業 CA 的 FQDN) (內部完整功能變數名稱。 證書頒發機構單位名稱 - 全部
清單 您的企業 CA 名稱,例如 “Contoso Certification Authority”。 證書範本名稱 - 全部
清單 證書範本的名稱。 憑證類型 - Android Enterprise (公司擁有和 Personally-Owned 工作配置檔)
- iOS
- macOS
- Windows 10/11
選取類型: - 用戶 憑證可以在憑證的主體和主體別名中包含使用者和裝置屬性 (SAN) 。
- 裝置 憑證只能在憑證的主體和SAN中包含裝置屬性。 針對無用戶裝置等案例使用裝置,例如 kiosk 或其他共用裝置。
此選取範圍會影響主體名稱格式。
主體名稱格式 - 全部
如需如何設定主體名稱格式的詳細資訊,請參閱本文稍後的 主體名稱格式 。
針對下列平臺,主體名稱格式取決於憑證類型:- Android Enterprise (工作配置檔)
- iOS
- macOS
- Windows 10/11
主體替代名稱 - 全部
針對 [屬性],選 取 [用戶主體名稱 (UPN) ,除非另有需要,否則請設定對應的 [值],然後選取 [ 新增]。
您可以針對這兩種憑證類型的 SAN 使用變數或靜態文字。 不需要使用變數。
如需詳細資訊,請參閱本文稍後的 主體名稱格式 。擴充金鑰使用方式 - Android 裝置系統管理員
- Android Enterprise (裝置擁有者、 公司擁有和 Personally-Owned 工作配置檔)
- Windows 10/11
憑證通常需要 客戶端驗證 ,用戶或裝置才能向伺服器進行驗證。 允許所有應用程式存取私鑰 - macOS
設定為 [啟用 ] 可讓針對相關聯 mac 裝置設定的應用程式存取 PKCS 憑證的私鑰。
如需此設定的詳細資訊,請參閱 Apple 開發人員檔中的 AllowAllAppsAccess the Certificate Payload 一節的組態 配置文件參考 。跟證書 - Android 裝置系統管理員
- Android Enterprise (裝置擁有者、 公司擁有和 Personally-Owned 工作配置檔)
選取先前指派的根 CA 憑證配置檔。 此步驟僅適用於完全受控、專用和 Corporate-Owned 工作配置檔的Android Enterprise裝置配置檔。
在 [應用程式] 中,設定 憑證存取 以管理如何將憑證存取權授與應用程式。 從下列項目中選擇:
- 應用程式需要使用者核准 (預設) – 用戶必須核准所有應用程式使用憑證。
- 針對特定應用程式以無訊息方式授與 (需要使用者核准其他應用程式) – 使用此選項,選取 [ 新增應用程式],然後選取一或多個應用程式以無訊息方式使用憑證,而不需要用戶互動。
選取 [下一步]。
在 [ 指派] 中,選取將接收配置檔的使用者或群組。 規劃將此憑證配置檔部署到接收受信任憑證配置檔的相同群組,以及接收組態配置檔的相同群組,例如使用憑證的 Wi-Fi 配置檔。 如需指派設定檔的詳細資訊,請參閱指派使用者和裝置設定檔。
選取[下一步]。
在 [檢閱 + 建立] 中,檢閱您的設定。 當您選取 [建立] 時,系統會儲存您的變更,然後指派設定檔。 原則也會顯示在設定檔清單中。
主體名稱格式
當您為下列平臺建立 PKCS 憑證配置檔時,主體名稱格式的選項取決於您選取的 [憑證類型][ 使用者 ] 或 [ 裝置]。
平臺:
- Android Enterprise (公司擁有和 Personally-Owned 工作配置檔)
- iOS
- macOS
- Windows 10/11
注意事項
從 Android 12 開始,Android 不再支援針對 個人擁有的工作設定檔 裝置使用下列硬體識別碼:
- 序號
- Imei
- 大臡
在主體名稱或 SAN 中依賴這些變數的個人擁有工作配置檔裝置的 Intune 憑證設定檔,在向 Intune 註冊裝置時,將無法在執行 Android 12 或更新版本的裝置上布建憑證。 只要 Intune 先前已取得裝置硬體識別碼,在升級至 Android 12 之前註冊的裝置仍然可以收到憑證。
如需 Android 12 引進的這項變更和其他變更的詳細資訊,請參閱 Android Day Zero Support for Microsoft Endpoint Manager 部落格文章。
用戶憑證類型
主體名稱格式的格式選項包含兩個變數:一般名稱 (CN) 和 Email (E) 。 Email (E) 通常會使用 {{EmailAddress}} 變數來設定。 例如:E={{EmailAddress}}一般名稱 (CN) 可以設定為下列任何變數:
CN={{UserName}}:使用者的用戶名稱,例如 Jane Doe。
CN={{UserPrincipalName}}:使用者的用戶主體名稱,例如 janedoe@contoso.com。
CN={{AAD_Device_ID}}:當您在 Microsoft Entra ID 中註冊裝置時指派的標識符。 此標識碼通常用來向 Microsoft Entra ID 進行驗證。
CN={{DeviceId}}:在 Intune 中註冊裝置時指派的標識符。
CN={{SERIALNUMBER}}: (SN 的唯一序號) 通常由製造商用來識別裝置。
CN={{IMEINumber}}: 國際行動設備識別 (IMEI) 用來識別行動電話的唯一號碼。
CN={{OnPrem_Distinguished_Name}}:以逗號分隔的相對辨別名稱序列,例如 CN=Jane Doe,OU=UserAccounts,DC=corp,DC=contoso,DC=com。
若要使用 {{OnPrem_Distinguished_Name}} 變數,請務必使用 Microsoft Entra Connect 同步處理 onpremisesdistinguishedname 使用者屬性至您的 Microsoft Entra ID。
CN={{onPremisesSamAccountName}}: 系統管理員可以使用 Microsoft Entra Connect 將 samAccountName 属性從 Active Directory 同步至 Microsoft Entra ID 至名為 onPremisesSamAccountName 的屬性。 Intune 可以將該變數取代為憑證主體中憑證發行要求的一部分。 samAccountName 屬性是用來支援舊版 Windows (Windows 2000) 用戶端和伺服器的使用者登入名稱。 使用者登入名稱格式為: DomainName\testUser,或僅 限 testUser。
若要使用 {{onPremisesSamAccountName}} 變數,請務必使用 Microsoft Entra Connect 將 onPremisesSamAccountName 使用者屬性同步至您的 Microsoft Entra ID。
下列 [ 裝置憑證類型 ] 區段中所列的所有裝置變數,也可以在用戶憑證主體名稱中使用。
藉由使用其中一或多個變數和靜態文字字串的組合,您可以建立自定義主體名稱格式,例如: CN={{UserName}},E={{EmailAddress}},OU=Mobile,O=Finance Group,L=Redmond,ST=Washington,C=US
該範例包含使用 CN 和 E 變數的主體名稱格式,以及組織單位、組織、位置、狀態和國家 / 地區值的字串。 CertStrToName 函 式描述此函式及其支援的字串。
沒有使用者關聯的裝置不支援用戶屬性,例如註冊為 Android Enterprise 專用的裝置。 例如,在主旨或 SAN 中使用 CN={{UserPrincipalName}} 的配置檔,在裝置上沒有使用者時,無法取得用戶主體名稱。
裝置憑證類型
主體名稱格式的格式選項包括下列變數:- {{AAD_Device_ID}}
- {{DeviceId}} - 這是 Intune 裝置標識符
- {{Device_Serial}}
- {{Device_IMEI}}
- {{SerialNumber}}
- {{IMEINumber}}
- {{AzureADDeviceId}}
- {{WiFiMacAddress}}
- {{IMEI}}
- {{DeviceName}}
- {{FullyQualifiedDomainName}} (僅適用於 Windows 和已加入網域的裝置)
- {{MEID}}
您可以在文字框中指定這些變數,後面接著變數的文字。 例如,名為 Device1 之裝置的一般名稱可以新增為 CN={{DeviceName}}Device1。
重要事項
- 當您指定變數時,請將變數名稱括在大括弧 { } 中,如範例中所示,以避免發生錯誤。
- 裝置憑證 主體 或 SAN 中使用的裝置屬性,例如 IMEI、 SerialNumber 和 FullyQualifiedDomainName,是可由具有裝置存取權的人員詐騙的屬性。
- 裝置必須支持憑證配置檔中指定的所有變數,該配置檔才能安裝在該裝置上。 例如,如果在SCEP配置檔的主體名稱中使用 {{IMEI}} ,並指派給沒有 IMEI 編號的裝置,配置檔將無法安裝。
後續步驟
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應