使用 SCEP 在 Intune 中新增合作夥伴證書頒發機構單位
重要事項
為了支援自 2022 年 5 月 10 日起在 KB5014754 中導入和宣告之 SCEP 憑證的強式對應 Windows 需求,我們已變更為新的和更新的 SCEP 憑證 Intune SCEP 憑證發行。 透過這些變更,iOS/iPadOS、macOS 和 Windows 的全新或更新 Intune SCEP 憑證現在會在憑證的 [主體別名] (SAN) 字段中包含下列卷標:URL=tag:microsoft.com,2022-09-14:sid:<value>
強式對應會使用此標記,將憑證從 Entra ID 系結至特定裝置或使用者 SID。 透過這項變更,以及從 Entra ID 對應 SID 的需求:
- 當 Windows 混合式加入裝置在 Entra ID 中具有已從 內部部署的 Active Directory 同步處理的 SID 時,裝置憑證會受到支援。
- 用戶憑證會使用來自 Entra ID 的使用者 SID,從 內部部署的 Active Directory 同步處理。
證書頒發機構單位 (不支援 SAN 中 URL 標籤的 CA) 可能無法發行憑證。 從 KB5014754 安裝更新的 Microsoft Active Directory 憑證服務伺服器支援使用此標籤。 如果您使用第三方 CA,請洽閱您的 CA 提供者,以確保其支援此格式,或如何及何時新增此支援。
如需詳細資訊,請參閱支援提示:在 Microsoft Intune 憑證中實作強式對應 - Microsoft 社群中樞。
使用第三方證書頒發機構單位 (CA) 搭配 Intune。 第三方 CA 可以使用簡單的憑證註冊通訊協定 (SCEP) 來布建具有新憑證或更新憑證的行動裝置,而且可以支援 Windows、iOS/iPadOS、Android 和 macOS 裝置。
使用這項功能有兩個部分:開放原始碼 API 和 Intune 系統管理員工作。
第 1 部分 - 使用開放原始碼 API
Microsoft 已建立 API 來與 Intune 整合。 透過 API,您可以驗證憑證、傳送成功或失敗通知,以及使用 SSL,特別是 SSL 套接字處理站來與 Intune 通訊。
API 可在 Intune SCEP API 公用 GitHub 存放庫上取得,供您下載並用於您的解決方案。 使用此 API 搭配第三方 SCEP 伺服器,在 SCEP 將憑證布建至裝置之前,對 Intune 執行自定義挑戰驗證。
與 Intune SCEP 管理解決方案整合可提供更多有關使用 API、其方法,以及測試您所建置解決方案的詳細數據。
第 2 部分 - Create 應用程式和設定檔
使用 Microsoft Entra 應用程式,您可以將許可權委派給 Intune,以處理來自裝置的 SCEP 要求。 Microsoft Entra 應用程式包含應用程式識別碼和驗證密鑰值,這些值會在開發人員所建立的 API 解決方案內使用。 系統管理員接著會使用 Intune 建立及部署 SCEP 憑證配置檔,並可檢視裝置上部署狀態的報告。
本文從系統管理員的觀點提供這項功能的概觀,包括建立 Microsoft Entra 應用程式。
概觀
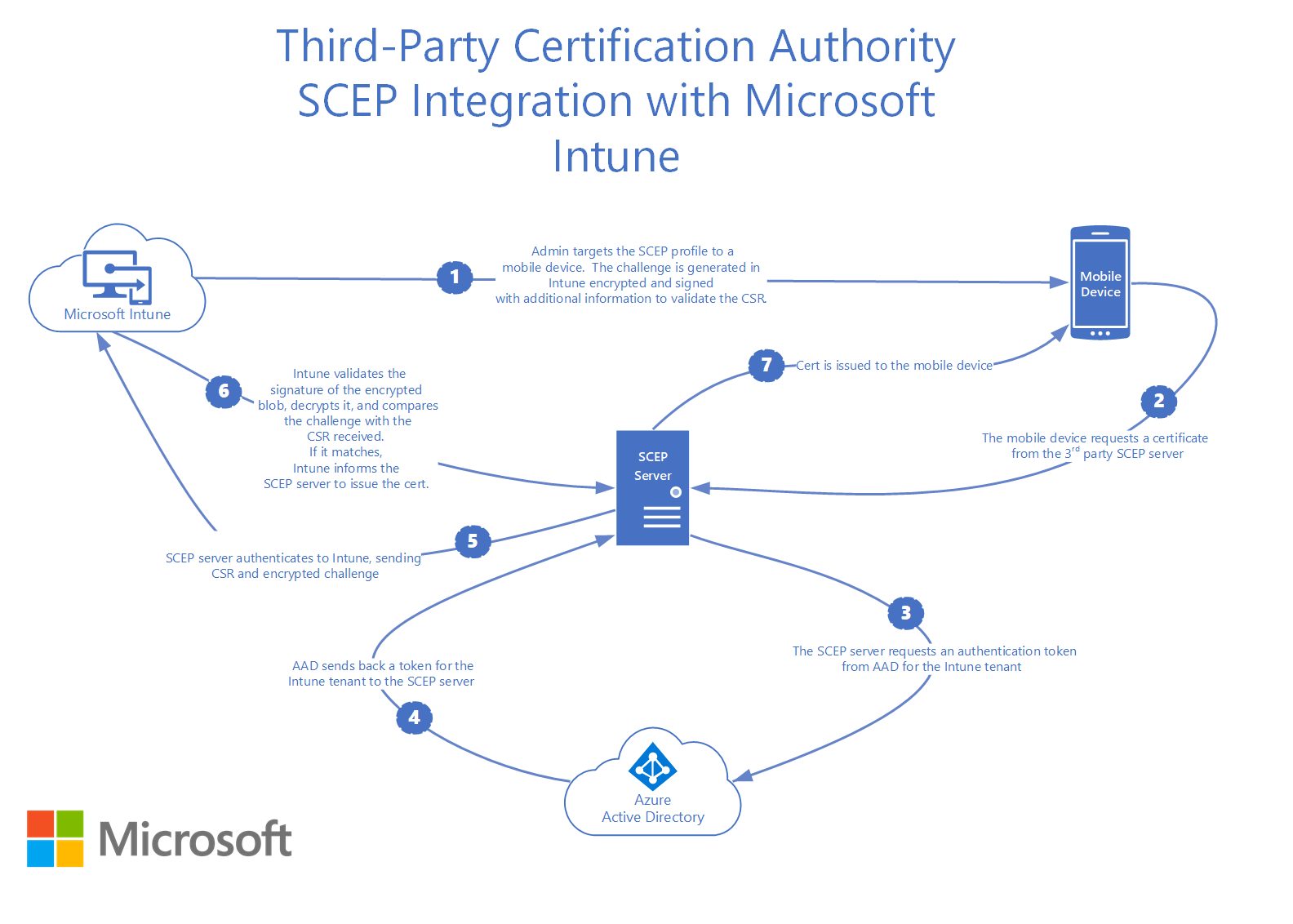
下列步驟提供在 Intune 中針對憑證使用 SCEP 的概觀:
- 在 Intune 中,系統管理員會建立 SCEP 憑證配置檔,然後將配置檔的目標設為使用者或裝置。
- 裝置會簽入以 Intune。
- Intune 會建立唯一的SCEP挑戰。 它也會新增其他完整性檢查資訊,例如預期的主體和 SAN 應該是什麼。
- Intune 加密並簽署挑戰和完整性檢查資訊,然後使用SCEP要求將此資訊傳送至裝置。
- 裝置會根據從 Intune 推送的SCEP憑證配置檔,在裝置上產生 (CSR) 和公開/私鑰組的憑證簽署要求。
- CSR 和加密/已簽署的挑戰會傳送至第三方 SCEP 伺服器端點。
- SCEP 伺服器會將 CSR 和挑戰傳送至 Intune。 然後 Intune 驗證簽章、解密承載,並將 CSR 與完整性檢查資訊進行比較。
- Intune 傳回 SCEP 伺服器的回應,並指出挑戰驗證是否成功。
- 如果成功驗證挑戰,則 SCEP 伺服器會將憑證簽發給裝置。
下圖顯示第三方 SCEP 與 Intune 整合的詳細流程:
設定第三方 CA 整合
驗證第三方證書頒發機構單位
在整合第三方證書頒發機構單位與 Intune 之前,請確認您使用的 CA 支援 Intune。 本文中 (的第三方 CA 合作夥伴) 包含清單。 如需詳細資訊,您也可以查看證書頒發機構單位的指引。 CA 可能包含其實作特定的安裝指示。
注意事項
若要支援下列裝置,當您設定 SCEP 憑證配置檔的 SCEP 伺服器 URL 時,CA 必須支援使用 HTTPS URL:
- Android 裝置系統管理員
- Android Enterprise 裝置擁有者
- Android Enterprise 公司擁有的工作配置檔
- Android Enterprise 個人擁有的工作配置檔
授權 CA 與 Intune 之間的通訊
若要允許第三方 SCEP 伺服器使用 Intune 執行自定義挑戰驗證,請在 Microsoft Entra ID 中建立應用程式。 此應用程式提供委派許可權給 Intune,以驗證 SCEP 要求。
請確定您具有註冊 Microsoft Entra 應用程式所需的許可權。 請參閱 Microsoft Entra 檔中的必要許可權。
在 Microsoft Entra ID 中 Create 應用程式
在 Azure 入口網站 中,移至 [Microsoft Entra ID>][應用程式註冊],然後選取 [新增註冊]。
在 [ 註冊應用程式] 頁面上,指定下列詳細數據:
- 在 [ 名稱] 區段中,輸入有意義的應用程式名稱。
- 在 [ 支持的帳戶類型] 區段中,選取 [任何組織目錄中的帳戶]。
- 針對 [重新導向 URI],保留 Web 的預設值,然後指定第三方 SCEP 伺服器的登入 URL。
選取 [註冊 ] 以建立應用程式,並開啟新應用程式的 [概觀] 頁面。
在 [應用程式 概觀] 頁面上,複製 [應用程式 (用戶端) 標識 符] 值,並加以記錄以供稍後使用。 您稍後將需要此值。
在應用程式的瀏覽窗格中,移至 [管理] 底下的 [憑證 & 秘密]。 選取新增用戶端密碼按鈕。 在 [描述] 中輸入值,選取 [ 到期] 的任何選項,然後選擇 [ 新增 ] 以產生客戶端密碼的 值 。
重要事項
離開此頁面之前,請複製客戶端密碼的值並加以記錄,以供稍後搭配第三方 CA 實作使用。 這個值不會再顯示。 請務必檢閱第三方 CA 的指引,以了解他們想要如何設定應用程式識別碼、驗證密鑰和租使用者標識碼。
記錄您的 租用戶標識碼。 租用戶標識碼是 @ 登入您帳戶之後的網域文字。 例如,如果您的帳戶是 admin@name.onmicrosoft.com,則您的租使用者標識 碼會 name.onmicrosoft.com。
在應用程式的瀏覽窗格中,移至 [管理] 底下的 [API 權 限]。 您將新增兩個不同的應用程式權限:
選 取 [新增許可權]:
- 在 [要求 API 許可權] 頁面上,選取 [Intune],然後選取 [應用程式許可權]。
- 選取 scep_challenge_provider ( SCEP 挑戰驗證) 複選框。
- 選取 [新增許可權 ] 以儲存此設定。
再次選 取 [新增許可權] 。
- 在 [ 要求 API 許可權 ] 頁面上,選取 [ Microsoft Graph>應用程式許可權]。
- 展開 [應用程式 ],然後選取 [ Application.Read.All ] ([讀取所有應用程式) ] 複選框。
- 選取 [新增許可權 ] 以儲存此設定。
保留在 [API 許可權] 頁面上,然後選取 [為<您的租>使用者授與系統管理員同意],然後選取 [是]。
Microsoft Entra ID 中的應用程式註冊程式已完成。
設定及部署 SCEP 憑證配置檔
身為系統管理員,請建立以使用者或裝置為目標的SCEP憑證配置檔。 然後,指派配置檔。
拿掉憑證
當您取消註冊或抹除裝置時,會移除憑證。 憑證不會被撤銷。
第三方證書頒發機構單位合作夥伴
下列第三方證書頒發機構單位支援 Intune:
- Cogito 群組
- DigiCert
- EasyScep
- EJBCA
- 委託
- EverTrust
- GlobalSign
- HID 全域
- IDnomic
- Keyfactor 命令
- KeyTalk
- Keytos
- Nexus 憑證管理員
- SCEPman
- Sectigo
- SecureW2
- Splashtop
- Venafi
如果您是第三方 CA,想要將產品與 Intune 整合,請檢閱 API 指引:
另請參閱
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應