安全性建議
適用於:
- Microsoft Defender 弱點管理
- 適用於端點的 Microsoft Defender 方案 2
- Microsoft Defender XDR
- 伺服器方案 1 & 2 的 Microsoft Defender
提示
您知道您可以免費試用 Microsoft Defender 弱點管理 中的所有功能嗎? 瞭解如何 註冊免費試用版。
您組織中識別的網路安全性弱點會對應至可採取動作的安全性建議,並依其影響排定優先順序。 優先建議可協助縮短緩和或補救弱點及推動合規性的時間。
每個安全性建議包含可採取動作的補救步驟。 為了協助進行工作管理,也可以使用 Microsoft Intune 和 Microsoft Endpoint Configuration Manager 傳送建議。 當威脅形勢改變時,建議也會隨之變更,因為它會持續從您環境中收集資訊。
提示
若要取得有關新弱點事件的電子郵件,請參閱在 適用於端點的 Microsoft Defender 中設定弱點電子郵件通知
運作方式
組織中的每個裝置都會根據三個重要因素進行評分,以協助客戶在正確的時間專注於正確的專案。
- 威脅:組織裝置和缺口歷程記錄中弱點和惡意探索的特性。 根據這些因素,安全性建議會顯示作用中警示、進行中的威脅活動及其對應威脅分析報告的對應連結。
- 缺口可能性:貴組織的安全性狀態和抵禦威脅的復原能力。
- 商業價值:貴組織的資產、重要流程和智慧財產。
流覽至 [安全性建議] 頁面
使用幾種不同的方式存取 [安全性建議] 頁面:
- Microsoft Defender 入口網站中的弱點管理導覽功能表
- 弱點管理儀錶板中的最高安全性建議
導覽功能表
移至 [弱點管理] 導覽功能表,然後選取 [ 建議]。 此頁面包含組織中所找到威脅和弱點的安全性建議清單。
弱點管理儀錶板中的最高安全性建議
以安全性系統管理員身分在指定的一天中,您可以查看 弱點管理儀錶板 ,以查看您的 暴露程度分數 與裝置的 Microsoft 安全分數並存。 目標是 降低貴 組織暴露於弱點的風險,並 提高 組織的裝置安全性,以更能抵禦網路安全性威脅攻擊。 最上層的安全性建議清單可協助您達成該目標。
最佳安全性建議會根據上一節中所述的重要因素,列出優先的改進機會 - 威脅、遭到入侵的可能性和價值。 選取建議會帶您前往安全性建議頁面,並提供更多詳細數據。
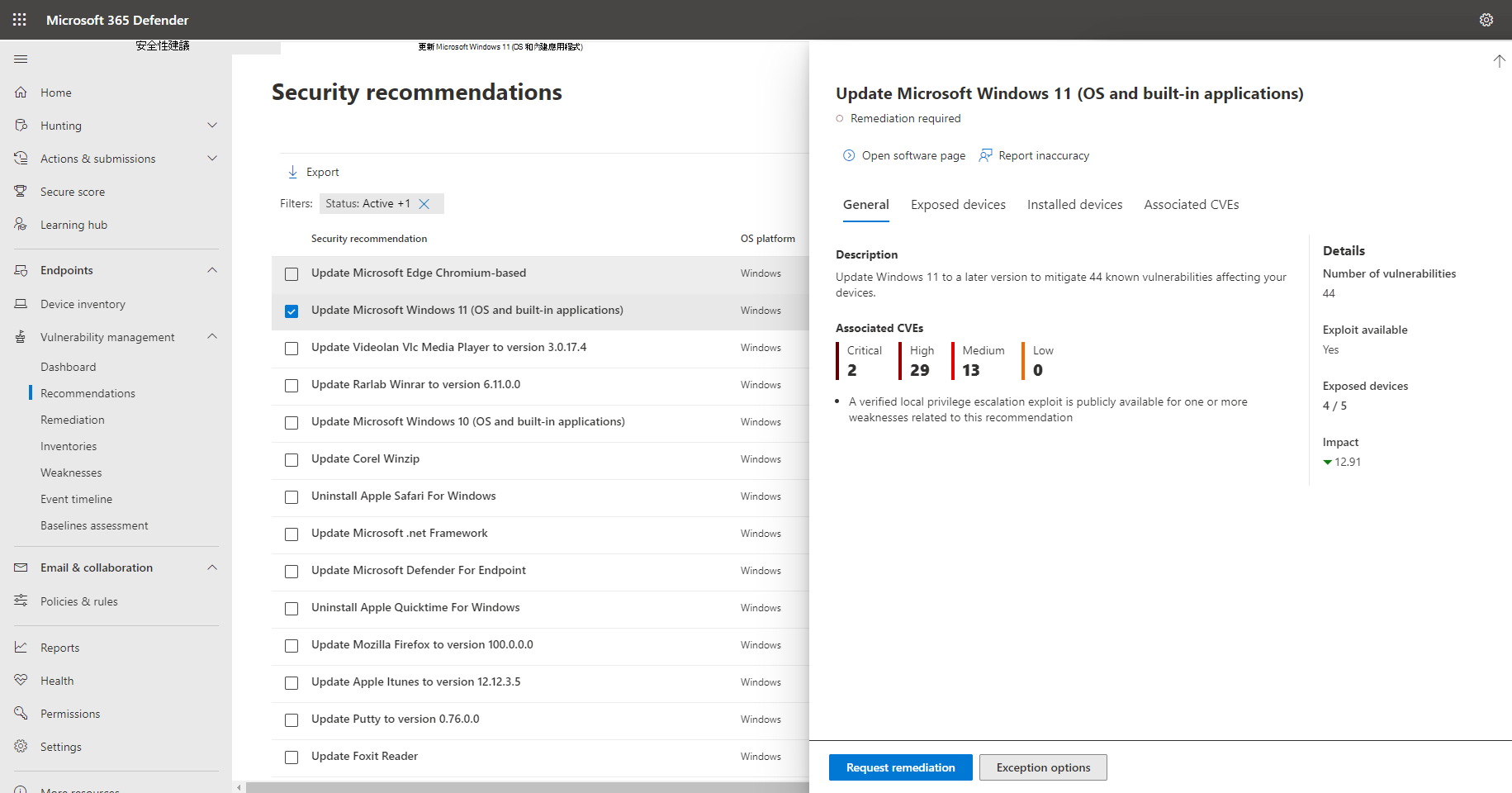
安全性建議概觀
檢視建議、找到的弱點數目、相關元件、威脅深入解析、公開的裝置數目、狀態、補救類型、補救活動、在實作建議后對您的曝光分數的影響,以及裝置的安全分數,以及相關聯的標籤。
[ 已公開的裝置 ] 圖形的色彩會隨著趨勢變更而變更。 如果公開的裝置數目增加,色彩會變更為紅色。 如果公開的裝置數目減少,圖表的色彩將會變更為綠色。
注意事項
弱點管理會顯示最多 30 天前 使用的裝置。 這與 適用於端點的 Microsoft Defender 的其餘部分不同,如果裝置未使用超過 7 天,則處於「非作用中」狀態。
圖示
實用的圖示也會快速提醒您注意:
 可能的作用中警示
可能的作用中警示 相關聯的公用惡意探索
相關聯的公用惡意探索 建議深入解析
建議深入解析
影響
影響數據行會顯示在實作建議后,對您的曝光分數和裝置安全分數的潛在影響。 您應該優先處理會降低暴露程度分數的專案,並提高裝置的安全分數。
暴露程度分數的潛在降低會顯示為:
 。 曝光分數較低表示裝置較不容易遭受惡意探索。 由於暴露分數是以各種因素的組合為基礎,包括新的補救或新探索到的弱點,因此實際的分數降低可能較低。
。 曝光分數較低表示裝置較不容易遭受惡意探索。 由於暴露分數是以各種因素的組合為基礎,包括新的補救或新探索到的弱點,因此實際的分數降低可能較低。裝置安全分數的預計增加會顯示為:
 。 裝置的安全分數越高,表示您的端點在防範網路安全性攻擊時更具復原能力。
。 裝置的安全分數越高,表示您的端點在防範網路安全性攻擊時更具復原能力。
探索安全性建議選項
選取您想要調查或處理的安全性建議。
從飛出視窗中,您可以選擇下列任何選項:
開啟軟體頁面 - 開啟軟體頁面,以取得更多有關軟體及其散發方式的內容。 此資訊會包括威脅內容、相關建議、找到的弱點、暴露的裝置數量、找到的弱點、已安裝軟體的裝置名稱和詳細資料,以及版本發佈。
補救選項 - 提交補救要求以在 Microsoft Intune 中開啟票證,讓 IT 系統管理員取貨並尋址。 在 補救 頁面中追蹤補救活動。
例外狀況選項 - 如果您還無法補救問題,請提交例外狀況、提供理由,以及設定例外狀況持續時間。
注意事項
在裝置上進行軟體變更時,通常需要 2 小時的時間,數據才會反映在安全性入口網站中。 不過,有時可能需要較長的時間。 設定變更可能需要 4 到 24 小時才能反映。
調查裝置暴露或影響的變更
如果公開的裝置數目大幅增加,或對貴組織暴露程度分數和裝置安全分數的影響大幅增加,則該安全性建議值得調查。
- 選取 [建議] 和 [ 開啟軟體] 頁面
- 選取 [ 事件時程表] 索引標籤 ,以檢視與該軟體相關的所有影響性事件,例如新的弱點或新的公用惡意探索。 深入瞭解事件時間軸
- 決定如何解決增加或貴組織暴露的問題,例如提交補救要求
裝置上的建議
若要查看適用於裝置的安全性建議清單,您可以:
注意事項
如果您已在適用於端點的 Defender 中啟用 IoT 整合 Microsoft Defender,則出現在 [IoT 裝置] 索引標籤上的 [企業 IoT 裝置] 建議會顯示在 [安全性建議] 頁面上。 如需詳細資訊,請參閱 使用適用於端點的Defender啟用企業IoT安全性。
要求補救
弱點管理補救功能會透過補救要求工作流程,橋接安全性與IT系統管理員之間的差距。 例如,安全性系統管理員可以要求IT系統管理員補救從 [ 安全性建議 ] 頁面到 Intune 的弱點。 深入瞭解補救選項
如何要求補救
選取您想要要求補救的安全性建議,然後選取 [ 補救選項]。 填寫表單,然後選取 [提交要求]。 移至 [ 補救] 頁面以檢視補救要求的狀態。 深入瞭解如何要求補救
例外狀況的檔案
當建議目前不相關時,作為補救要求的替代方案,您可以建立建議的例外狀況。 深入瞭解例外狀況
僅具有「例外狀況處理」權限的使用者才可以新增例外狀況。 深入瞭解 RBAC 角色。
當例外狀況是針對建議所建立時,則此建議已不再有效。 建議狀態會變更為裝置群組) (的完整例外 狀況或 部分例外 狀況。
如何建立例外狀況
選取您想要為其建立例外狀況的安全性建議,然後選取 [ 例外狀況選項]。
![顯示 [例外狀況選項] 的按鈕在安全性建議飛出視窗中的位置。](../../media/defender-vulnerability-management/tvm-exception-options.png?view=o365-worldwide)
填寫表單並提交。 若要檢視目前和過去) (所有例外狀況,請流覽至 [威脅 & 弱點管理] 功能表下的 [補救] 頁面,然後選取 [例外狀況] 索引卷標。深入瞭解如何建立例外狀況
報表不精確
當您看到任何模糊、不正確、不完整或已補救的安全性建議資訊時,您可以回報誤判。
開啟 [安全性] 建議。
選取您想要報告的安全性建議旁邊的三個點,然後選取 [報告不準確]。
從飛出視窗窗格中,從下拉功能表中選取 [不準確] 類別、填入您的電子郵件位址,以及有關不準確的詳細數據。
選取 [提交]。 您的意見反應會立即傳送給弱點管理專家。
相關文章
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應