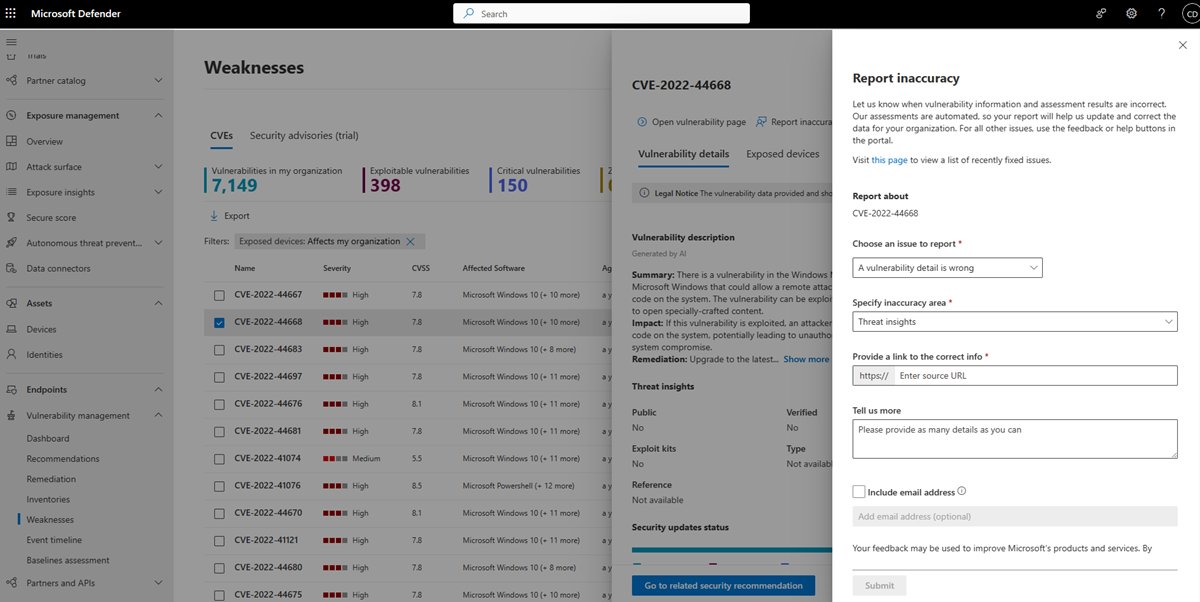
我組織中的弱點
Microsoft Defender 弱點管理 中的 [弱點] 頁面會依其 CVE 標識符列出已知的常見弱點和公開 (CVE) 。
CVE 識別碼是指派給公開揭露的網路安全性弱點的唯一標識碼,會影響軟體、硬體和韌體。 它們為組織提供標準方式來識別和追蹤弱點,並協助他們瞭解、排定優先順序,並解決組織中的這些弱點。 CVA 會在從 https://www.cve.org/存取的公用登錄中追蹤。
Defender 弱點管理會使用端點感測器來掃描和偵測組織中的這些和其他弱點。
適用於:
- Microsoft Defender 弱點管理
- 適用於端點的 Microsoft Defender 方案 2
- Microsoft Defender XDR
- 伺服器方案 1 & 2 的 Microsoft Defender
重要事項
Defender 弱點管理可協助識別應用程式和元件中的Log4j弱點。 深入了解。
提示
您知道您可以免費試用 Microsoft Defender 弱點管理 中的所有功能嗎? 瞭解如何 註冊免費試用版。
弱點概觀頁面
若要存取 [弱點] 頁面,請從 Microsoft Defender 入口網站的 [弱點管理] 導覽功能表中選取 [弱點]
[弱點] 頁面隨即開啟,其中包含裝置公開的 CVE 清單。 您可以檢視嚴重性、常見弱點評分系統 (CVSS) 評等、對應的缺口和威脅深入解析等等。
注意事項
如果沒有指派給弱點的官方 CVE 識別符,弱點名稱會由 Microsoft Defender 弱點管理 指派,而且格式為 TVM-2020-002。
注意事項
您可以從弱點頁面匯出至 CSV 檔案的記錄數目上限為 10,000 筆。
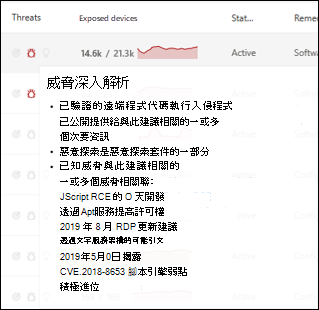
缺口和威脅深入解析
請務必優先處理與持續威脅相關聯的建議。 您可以使用 [ 威脅 ] 資料行中可用的信息,協助您排定弱點的優先順序。 若要查看持續性威脅的弱點,請依下列方式篩選 [ 威脅] 資料 行:
- 相關聯的作用中警示
- 可用的惡意探索
- 已驗證惡意探索
- 此惡意探索是惡意探索套件的一部分
威脅深入解析圖示 ![]() 。如果弱點中有相關聯的惡意探索,則會在 [ 威脅 ] 數據行中反白顯示。
。如果弱點中有相關聯的惡意探索,則會在 [ 威脅 ] 數據行中反白顯示。
將滑鼠停留在圖示上,會顯示威脅是否為惡意探索套件的一部分,或是連線到特定的進階持續性活動或活動群組。 如果有的話,就會有威脅分析報告的連結,其中包含零時差惡意探索新聞、揭露或相關安全性諮詢。
如果您的組織中發現弱點,則會醒目提示缺口深入解析圖示。 ![]() 。
。
[ 公開的裝置] 資料行會顯示目前公開到弱點的裝置數目。 如果數據行顯示 0,表示您沒有風險。
取得弱點深入解析
如果您從 [弱點] 頁面選取 CVE,飛出視窗面板隨即開啟,其中包含弱點描述、詳細數據和威脅深入解析等詳細資訊。 如果可用,AI 產生的弱點描述會提供弱點的詳細資訊、其影響、建議的補救步驟,以及任何其他資訊。
針對每個 CVE,您可以看到公開的裝置和受影響軟體的清單。
相關安全性建議
使用安全性建議來補救公開裝置中的弱點,並降低資產和組織的風險。 當有安全性建議可用時,您可以選取 [移至相關的安全性建議 ],以取得如何補救弱點的詳細數據。
CVE 的建議通常是透過相關軟體的安全性更新來補救弱點。 不過,某些 CVA 將無法使用安全性更新。 這可能適用於 CVE 的所有相關軟體或只是子集,例如,軟體廠商可能會決定不要修正特定易受攻擊版本的問題。
當安全性更新僅適用於某些相關軟體時,CVE 的 CVE 名稱底下會有「某些可用的更新」標籤。 至少有一個可用的更新之後,您可以選擇移至相關的安全性建議。
如果沒有可用的安全性更新,CVE 的 CVE 名稱底下會有「沒有安全性更新」標籤。 無法選擇移至相關的安全性建議,因為安全性建議頁面中會排除沒有可用安全性更新的軟體。
注意事項
安全性建議只包含具有可用安全性更新的裝置和軟體套件。
要求 CVE 支援
弱點管理目前不支援的軟體 CVE 仍會出現在 [弱點] 頁面中。 因為軟體不受支援,所以只有有限的數據可供使用。 公開的裝置資訊將不適用於具有不支持軟體的 CVE。
若要檢視不支援的軟體清單,請依 [已公開的裝置] 區段中的 [無法使用] 選項來篩選弱點頁面。
您可以要求將支援新增至特定 CVE 的 Defender 弱點管理。 若要要求支援:
- 從 Microsoft Defender 入口網站的 [弱點] 頁面選取 CVE
- 從 [弱點詳細數據] 索引標籤中選取 [ 請支援此 CVE ]
此要求會傳送給 Microsoft,並協助我們排定此 CVE 的優先順序,以及其他系統中的 CVE。
在其他地方檢視 CVE) 項目的常見弱點和暴露 (
儀錶板中最易受攻擊的軟體
- 移至 Defender 弱點管理儀錶板 ,並向下捲動至 最易受攻擊的軟體 小工具。 您會看到在每個軟體中找到的弱點數目,以及威脅資訊和一段時間的裝置暴露程度高階檢視。
- 選取您想要調查的軟體。
- 選取 [ 探索到的弱點] 索引標籤 。
- 選取您想要調查的弱點,以開啟包含 CVE 詳細數據的飛出視窗面板。
探索裝置頁面中的弱點
在裝置頁面中檢視相關的弱點資訊。
- 從 Microsoft Defender 入口網站的 [資產] 導覽功能表中選取 [裝置]。
- 在 [ 裝置清查 ] 頁面中,選取您要調查的裝置名稱。
- 選 取 [開啟裝置頁面] ,然後從裝置頁面選 取 [探索 到的弱點]。
- 選取您想要調查的弱點,以開啟包含 CVE 詳細數據的飛出視窗面板。
CVE 偵測邏輯
類似於軟體辨識項,我們會顯示我們在裝置上套用的偵測邏輯,以指出其易受攻擊。
若要查看偵測邏輯:
- 從 [裝置清查] 頁面選取裝置。
- 選 取 [開啟裝置頁面] ,然後從裝置頁面選 取 [探索 到的弱點]。
- 選取您想要調查的弱點。
飛出視窗隨即開啟, 而 [偵測邏輯] 區 段會顯示偵測邏輯和來源。
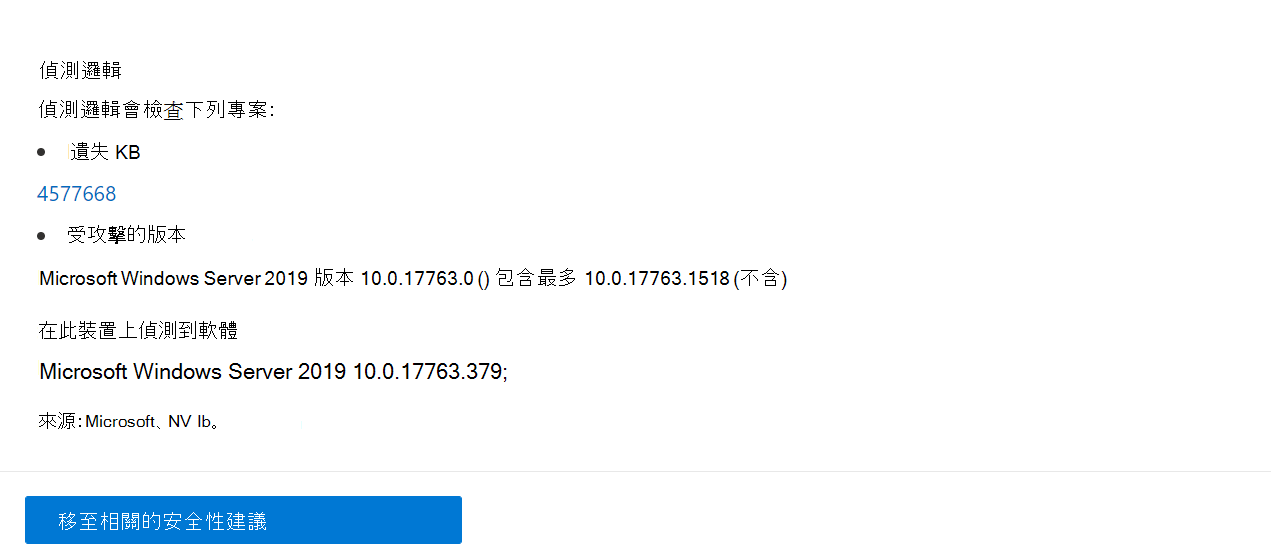
「OS 功能」類別也會顯示在相關案例中。 此時,如果啟用特定 OS 元件,CVE 會影響執行易受攻擊 OS 的裝置。 例如,如果 Windows Server 2019 或 Windows Server 2022 的 DNS 元件有弱點,我們只會將此 CVE 附加至在其 OS 中啟用 DNS 功能的 Windows Server 2019 和 Windows Server 2022 裝置。
報表不精確
當您看到任何模糊、不正確或不完整的資訊時,請回報誤判。 您也可以報告已補救的安全性建議。
- 在 [弱點] 頁面上開啟 CVE。
- 選取 [報告不精確] ,飛出視窗窗格隨即開啟。
- 從飛出視窗窗格中,選擇要報告的問題。
- 填入所要求的不精確詳細數據。 這會根據您回報的問題而有所不同。
- 選取 [提交]。 您的意見反應會立即傳送給 Microsoft Defender 弱點管理 專家。
相關文章
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應